漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0107603
漏洞标题:慧聪网信息发布过滤不严导致任意js执行可进行恶意跳转/弹窗(需从搜索引擎进入)
相关厂商:慧聪网
漏洞作者: 路人甲
提交时间:2015-04-24 15:31
修复时间:2015-06-08 17:36
公开时间:2015-06-08 17:36
漏洞类型:内容安全
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-04-24: 细节已通知厂商并且等待厂商处理中
2015-04-24: 厂商已经确认,细节仅向厂商公开
2015-05-04: 细节向核心白帽子及相关领域专家公开
2015-05-14: 细节向普通白帽子公开
2015-05-24: 细节向实习白帽子公开
2015-06-08: 细节向公众公开
简要描述:
慧聪网信息发布过滤不严导致用户发布的内容中可插入加密代码,导致任意js执行,可进行恶意跳转、弹窗等js代码能实现的操作。
详细说明:
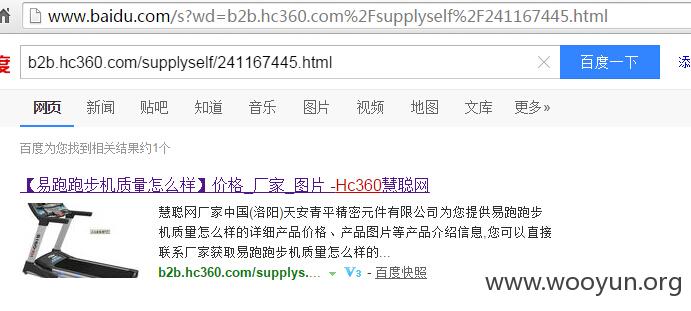
例如慧聪网站用户发布信息的页面:b2b.hc360.com/supplyself/241167445.html
正常打开,不会发现有任何问题,但是用搜索引擎打开,就会发现端倪:
http://www.baidu.com/s?wd=b2b.hc360.com%2Fsupplyself%2F241167445.html
点击快照后,先打开慧聪网站页面,还没打开完全呢,发现跳转了!经过一系列跳转后,最终跳转到天猫页面!
为什么会挑砖呢?仔细来看一下用户发布的内容有什么神秘代码:
view-source:http://b2b.hc360.com/supplyself/241167445.html
打开后发现,代码中含有这样一段:
一大串数字,是什么东东呢?加密了的js代码,解密后是这样子的:
也就是说通过百度等搜索引擎进入页面,就会自动跳转到指定的url。
跳转到天猫并不可怕,可怕的是这段js代码是用户自定义的,也就是说,改成其他js代码同样也能执行!这样强大的js还有什么不能完成的呢?什么弹窗、替换代码、钓鱼……都不在话下!
好端端的慧聪网成了广告泛滥的平台了~给正常用户得造成多大困扰,给慧聪自身造成多大损失!?
漏洞证明:
页面:b2b.hc360.com/supplyself/241167445.html
打开后发现,代码中含有这样一段:
一大串数字,是什么东东呢?加密了的js代码,解密后是这样子的:
也就是说通过百度等搜索引擎进入页面,就会自动跳转到指定的url。
修复方案:
用户发信息加强过滤
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2015-04-24 17:34
厂商回复:
谢谢您
最新状态:
暂无