2处代码设计问题.
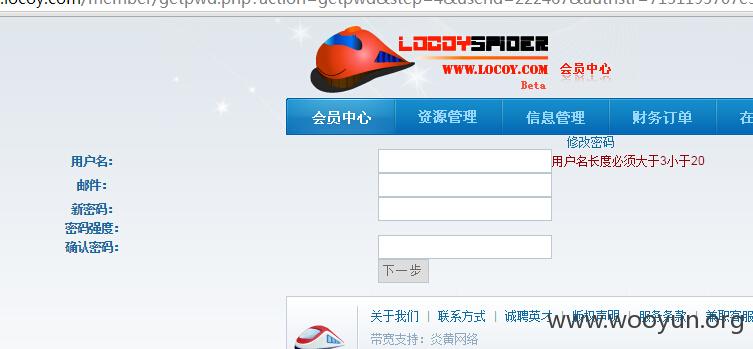
1:任意用户密码修改 位置http://www.locoy.com/member/getpwd.php
首先注册用户.然后选择找回密码. 填入正确的用户名和此用户的注册邮箱. 系统发找回密码的URL链接至用户邮箱.
类似:http://www.locoy.com/member/getpwd.php?action=getpwd&step=4&userid=[用户ID]&authstr=[32位加密码]
此时直接发包修改POST 参数. 即可对任意用户密码进行重置.
详情见http post包. 修改POST包后.直接发包即可修改成功.
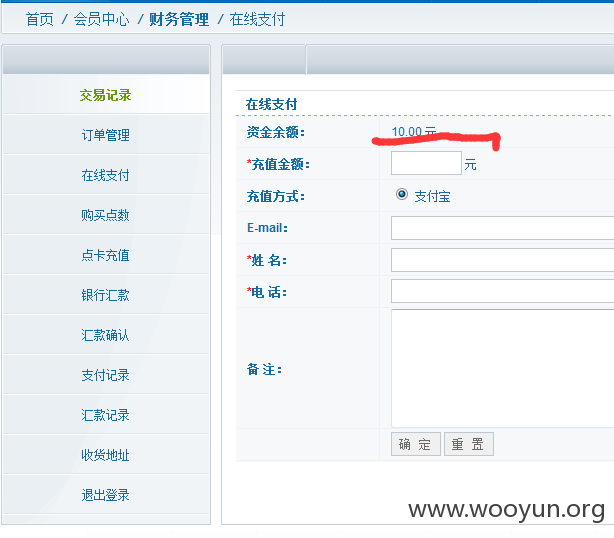
2:新注册用户可以任意修改用户账号余额漏洞.
注册发包时: 新增一处parameter 即 memberinfo[amount]=10 新注册用户注册后就有了10元的余额.可以直接在商城购买最新版火车头软件.
根据第一个任意密码修改漏洞,可以在bbs.locoy.com 里面找到几个管理员的账号 ,重置他们的密码.即可登录discuz 3.2 后台.
然后getwebshell....主站和BBS在同一服务器上.然后就没有然后了....