WooYun: PHPCMS V9 一个为所欲为的漏洞
可以参考这篇文章,这这篇文章的作者爆了这样一个点
厂商同学直接忽略了,但是却自己修复了(不评论),修复为
修复得很不仔细,看来厂商真的觉得这不是个洞。好啊,那么肯定就会有其它点了,既然不重视这个点,我们来看\api\get_menu.php:
其中的getcache的两个参量是可控的。并且没有过滤反斜杠。构造合适的访问链接可以访问到cache文件夹中的配置文件,并读取内容。
那么如果这样的链接会督导什么内容呢?
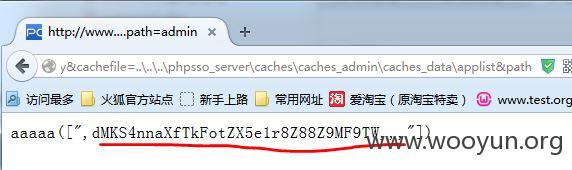
不过这里厂商又会忽略的。那么我们看看authkey怎么用
在\phpsso_server\phpcms\modules\phpsso\index.php中含有如下函数:
里面有数据库的操作,应该是用于密码更改的。我们来构造一个data数据,加密前:
利用上面的authkey以及cms自带的加解密函数即可进行加密。在这里,我们除了可以修改密码,还可以进行注入



