通杀v9所有版本(有条件).
swfupload上传页面输出了 MD5(auth_key+sess_id), phpcms\modules\attachment\functions\global.func.php:initupload函数
可以看到函数返回的数据中有$sess_id 、$swf_auth_key这两个值,并且$swf_auth_key=MD5(auth_key+$sess_id).
模板phpcms\modules\attachment\templates\swfupload.tpl.php调用initupload函数输出了上边的内容:
利用点:PHPCMS文件下载功能加密了文件路径,使用的加密密钥为MD5(auth_key+User-Agent),通过修改浏览器UA为上边获取到的$sess_id,就能共用一个加密密钥,从而使PHPCMS能够解密我们构造的数据,这样就能下载任意文件啦。
phpcms\modules\content\down.php:
利用方式:
第一步获取$sess_id 和 $swf_auth_key:
注册用户登录后,在线投稿(需要后台开启),上传图片右键源码:
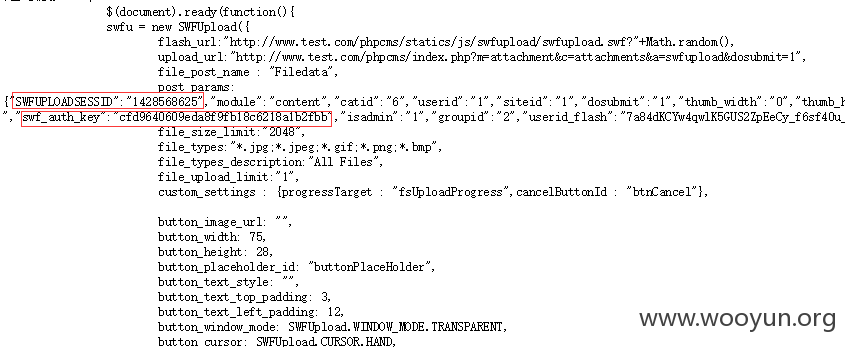
得到SWFUPLOADSESSID、swf_auth_key这两个值记录下来后边会用到。
第二部构造参数提交:
文件下载url:index.php?m=content&c=down&a=download&a_k=构造的参数,使用上一步得到的$swf_auth_key加密数据:
将路径拆为两部分绕过检查。下载会检查ip,提交的时候xff要与之对应。
通过读取配置文件,得到auth_key之后就能SQL注入了。
phpcms\modules\member\classes\foreground.class.php: