漏洞概要
关注数(24)
关注此漏洞
漏洞标题:腾讯云WAF安全防护存在一处XSS
相关厂商:腾讯
提交时间:2014-12-26 10:20
修复时间:2015-02-09 10:22
公开时间:2015-02-09 10:22
漏洞类型:xss跨站脚本攻击
危害等级:低
自评Rank:2
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2014-12-26: 细节已通知厂商并且等待厂商处理中
2014-12-26: 厂商已经确认,细节仅向厂商公开
2015-01-05: 细节向核心白帽子及相关领域专家公开
2015-01-15: 细节向普通白帽子公开
2015-01-25: 细节向实习白帽子公开
2015-02-09: 细节向公众公开
简要描述:
攻击者通过攻击对方所在的腾讯云服务,可以在提交数据中构造XSS,当网站管理员登陆腾讯云后台,查看攻击攻击详情时可看到xss攻击效果
详细说明:
攻击者通过攻击对方所在的腾讯云服务,可以在提交数据中构造XSS,当网站管理员登陆腾讯云后台,查看攻击攻击详情时可看到xss攻击效果.
攻击者构造iframe可实现自动加载xss代码,弹出提示
漏洞证明:
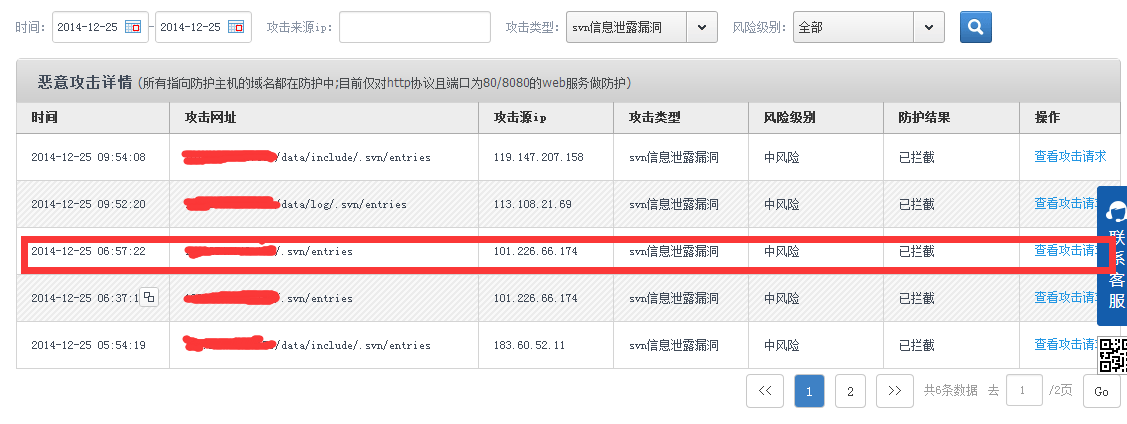
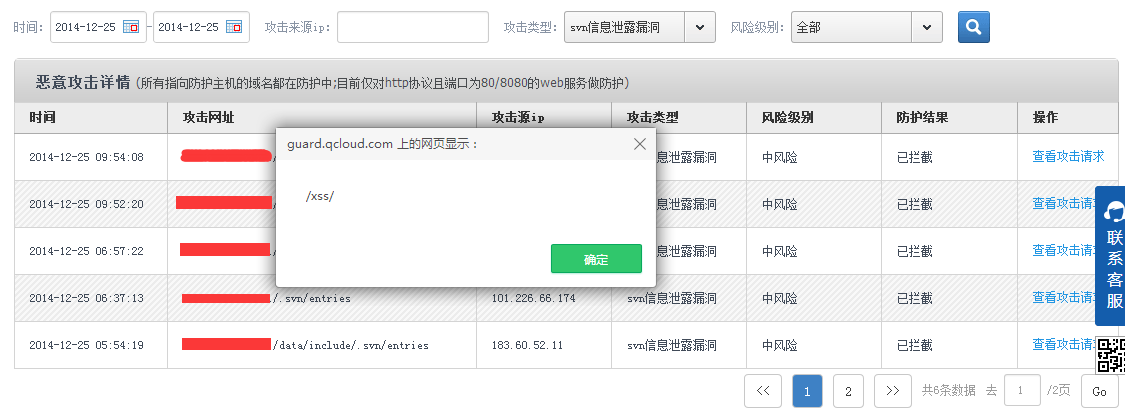
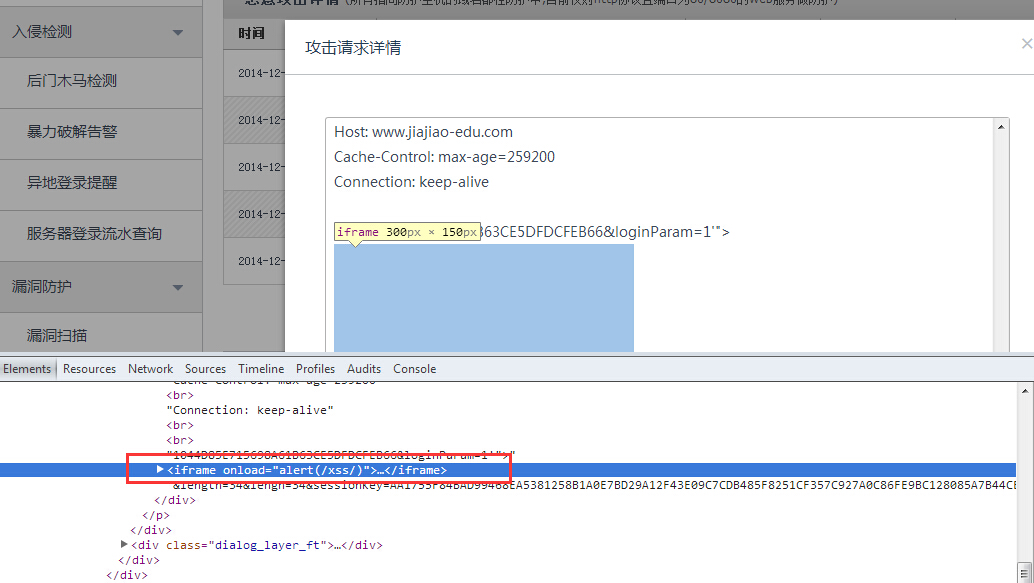
返回的请求json数据如下
由于当天的测试数据第二天才能在后台显示,所以未进入深入测试.
修复方案:
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2014-12-26 11:21
厂商回复:
非常感谢您的报告,问题已着手处理,感谢大家对腾讯业务安全的关注。如果您有任何疑问,欢迎反馈,我们会有专人跟进处理。
最新状态:
暂无





