1.首先进入这里,魅族的密码重置模块
https://member.meizu.com/forgetpwd
2.然后我们需要获取的是四种功能模块的包,分别是发送验证码,验证验证码是否正确的,以及获取令牌和重置密码的,这里我都获取好了,接下来我们直接用
发送验证码:
验证验证码是否正确:
获取令牌:
重置密码:
OK,准备齐全了,下面就给大家做现场的表演
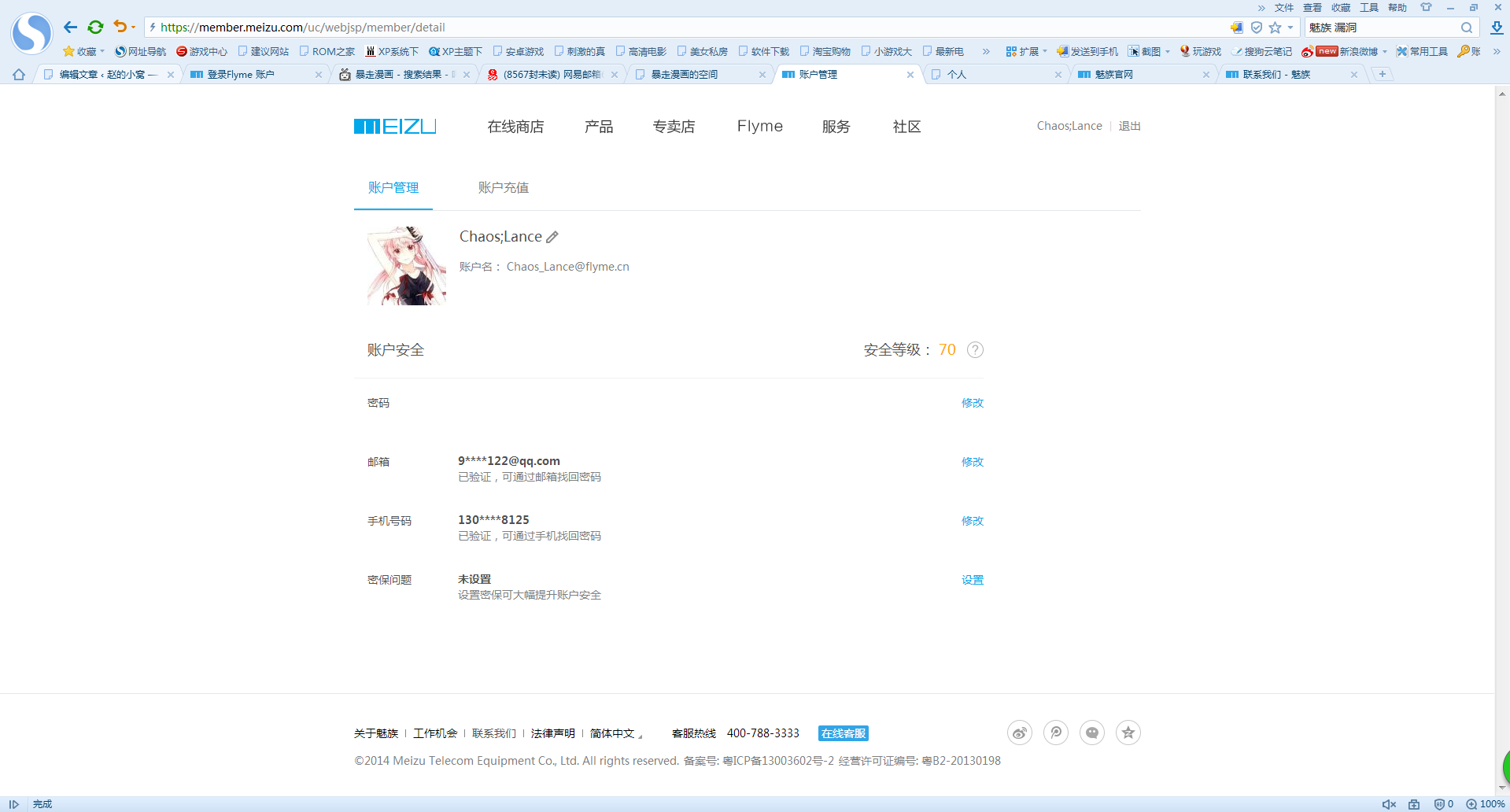
1.首先我的目标账号是我朋友LANCE的账号(在这里特别感谢他允许我使用他的账号来测试)130××××××××
2.同样的我们进入那个账号查找页面,然后这样把账号填进去,进到这个页面
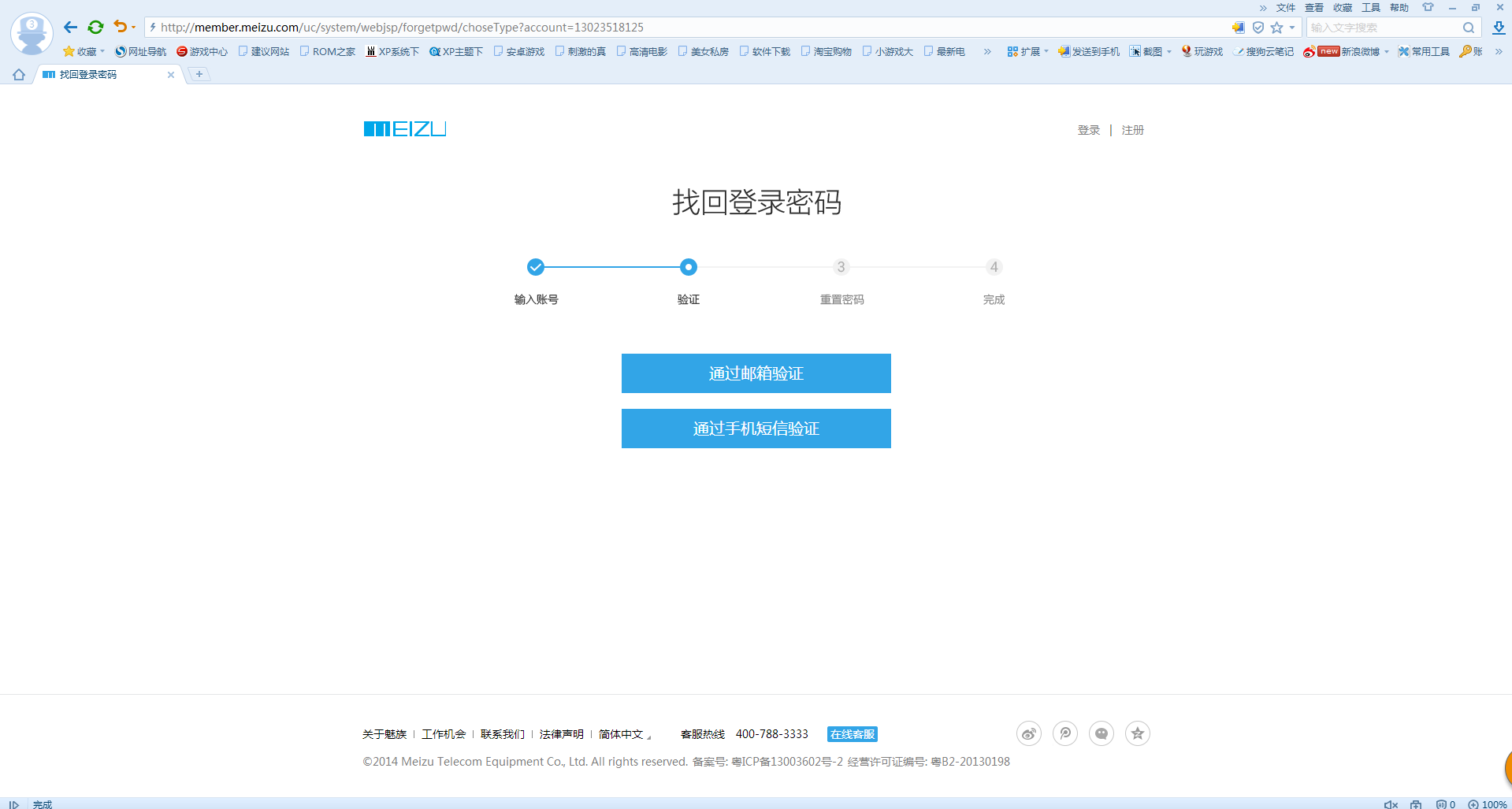
3.这时我们回到抓包那里,把COOKIE干出来
这里我们需要的是这一段
4.再拿出我们之前抓的找回密码那个包,我们替换些信息进去
注意,我这里替换的是COOKIE以及下面的账号那里,邮箱你要填上自己的
然后,就发送出去吧
5.然后我们的邮箱里收到了这封东西
130×××××××,您好:
感谢您使用Flyme服务。
您正在进行Flyme找回密码操作,请在30分钟内将此验证码:991344 输入验证码输入框,以完成验证。
此致
Flyme 项目组
把上面的验证码记下,我们继续玩
6.然后这里,我们来验证一下是否正确,同样的记住替换COOKIE和信息
验证验证码是否正确:
返回是错误的,但不要在意,我们继续走
7.这时,我们来获取令牌了,记得把该替换的东西都替换了
返回的是这些
我们需要的是value
8.然后,最后,我们替换好该替换的东西,重置密码吧!
OK,我们看到的,返回的是200和true,就是说我们成功的重置了密码
9.登陆试试