系统:在线对账系统http://duizhang.haidilao.com/
这个就比较重要了吧。
然后呢,发现还是比较严格的:
看起来很严格,爆破是不可能了,但是,防不胜防啊。
发现一个地址。
http://duizhang.haidilao.com/log.aspx
打开一看,越权查看,还是好多信息的。
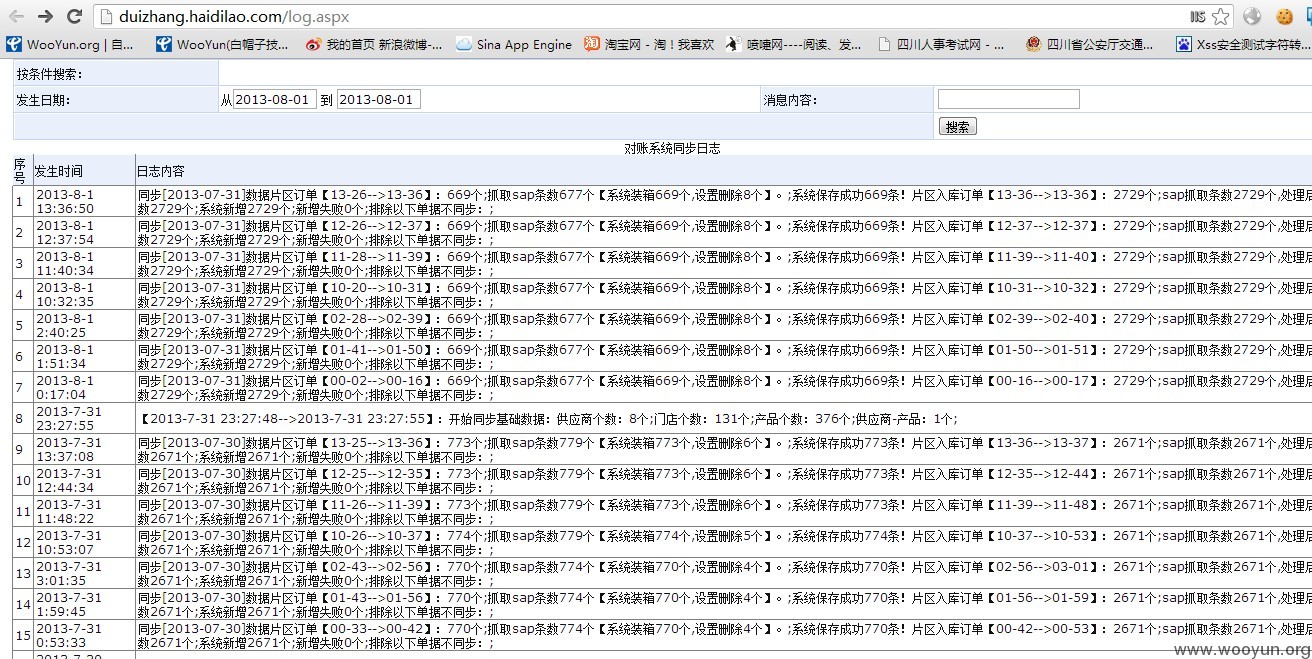
然后呢,随便在搜索处加个单引号就报错了。
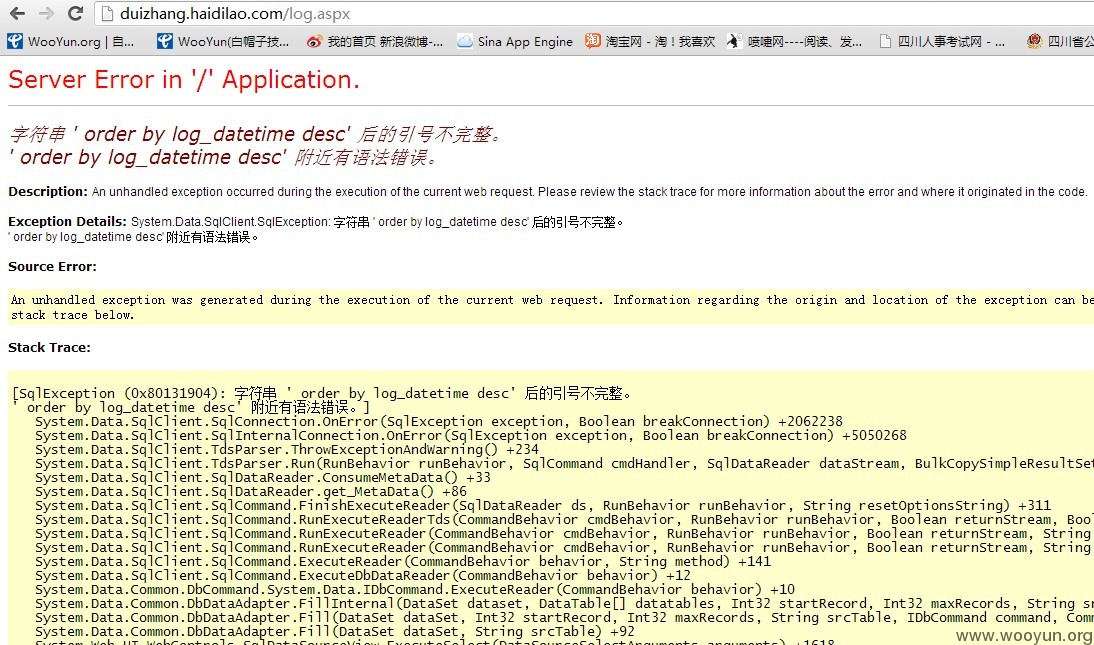
然后呢,果断抓包。
post注射看看。
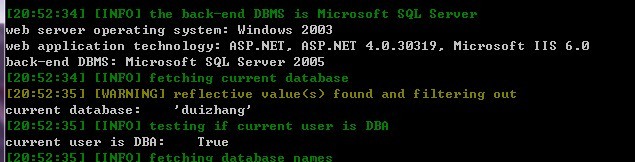
发现权限挺高的,DBA。注射速度也是一流的。
注射出很多弱口令啊,这下继续渗透你们就能摸准你们的习惯了。
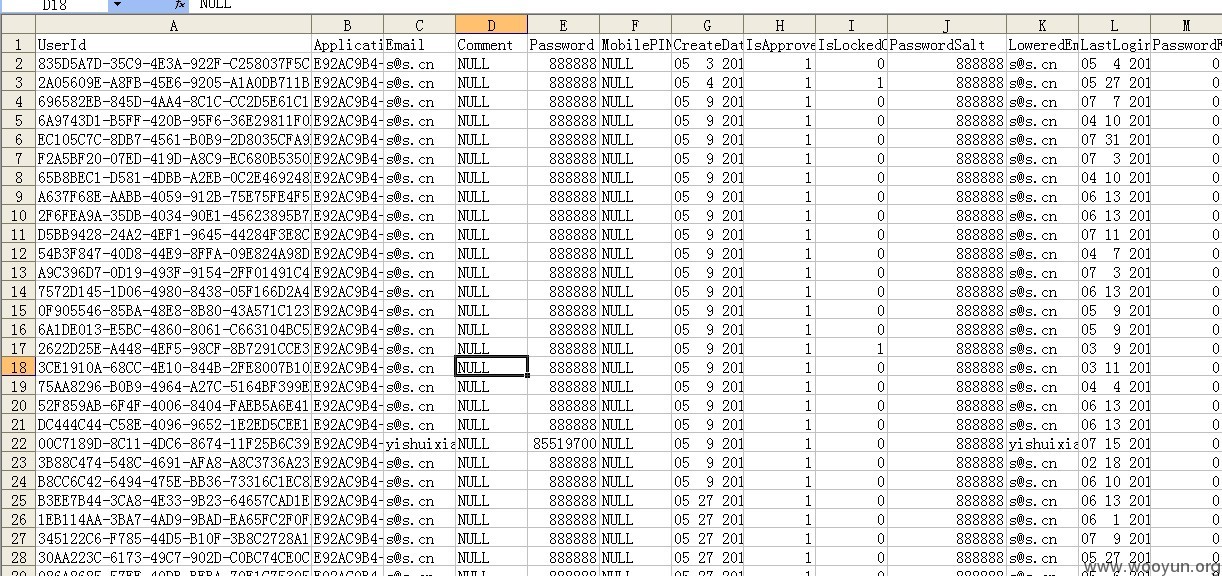
然后进入系统:
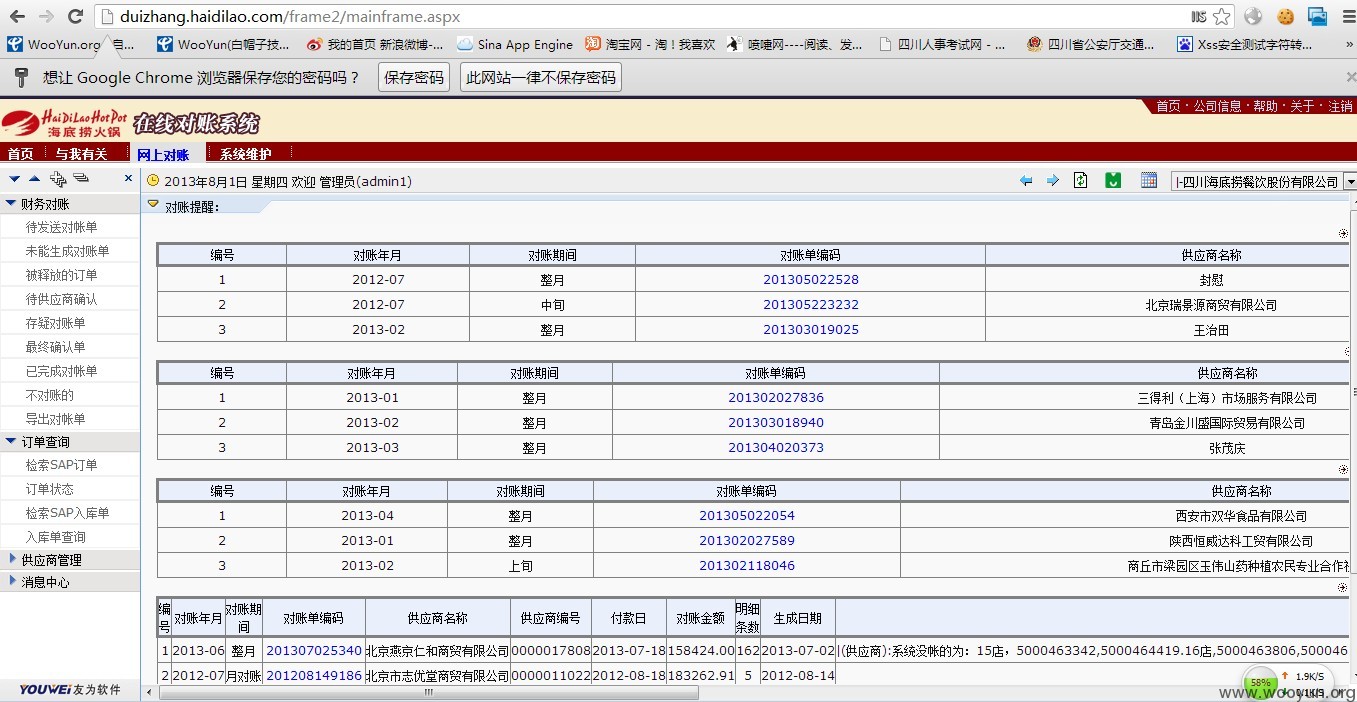
然后,好多信息啊,卧槽
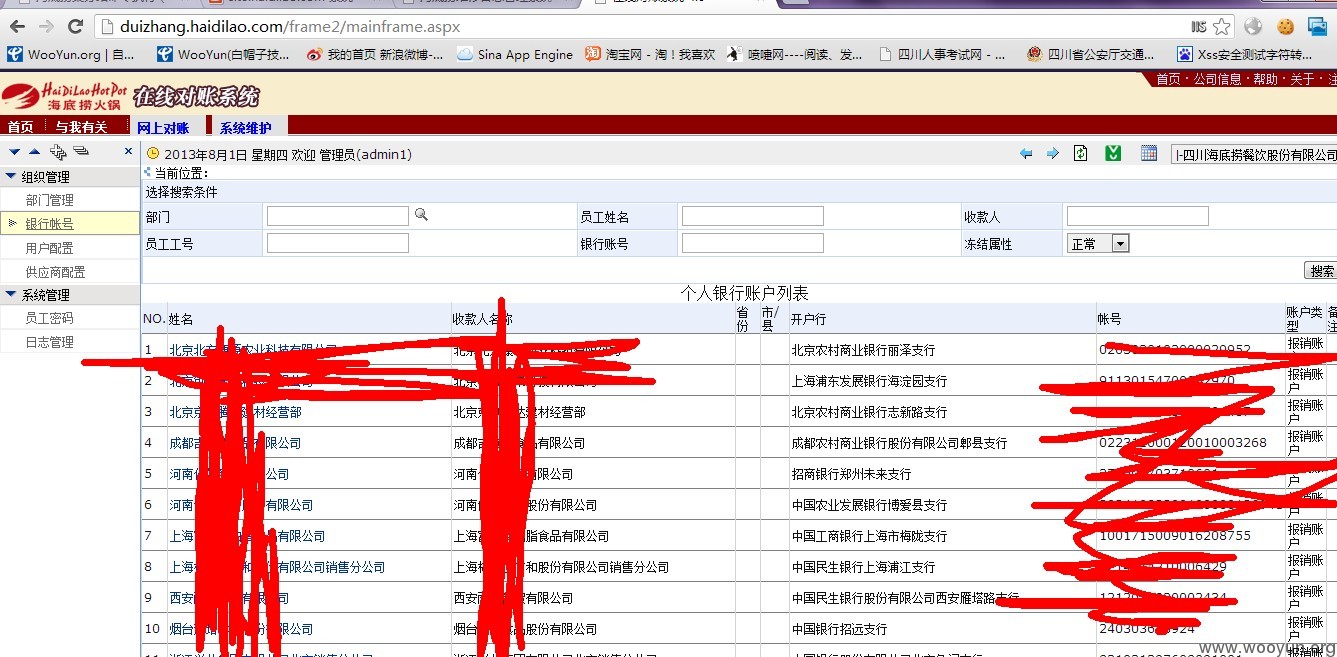
over。








