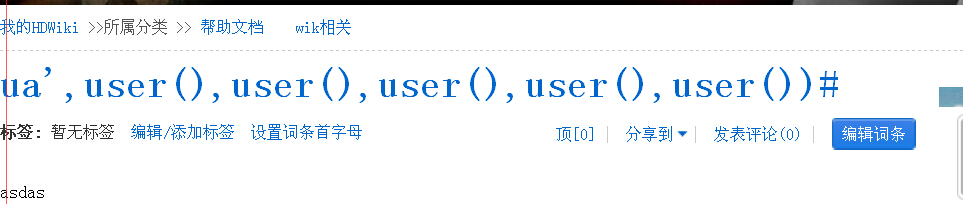
在control/doc.php中
省略一点.......
$_ENV['doc']->edit_doc($doc,"1", $increase_edition)
跟这函数
带入到了insert当中
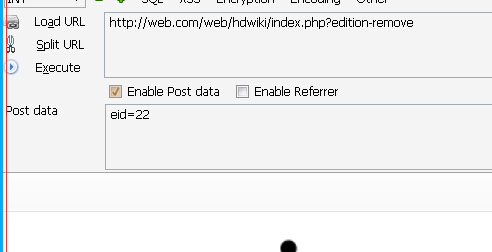
在control/edition.php
remove_edition($eids, $did)
跟一下这函数。
$query=$this->db->query("SELECT * FROM ".DB_TABLEPRE."edition WHERE eid IN ($eid)");
这里查询出来 出库。
$sql.="('edition','".$edition['title']."','".addslashes(serialize($edition))."','$file','".$this->base->user['uid']."','".$this->base->user['username']."','".$this->base->time."'),"
在这里addslashes(serialize($edition)像这些的addslashes都转义了
但是 $edition['title'] 这里出库的标题没过滤。
然后带入到了insert当中, 造成了注入。