漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-066606
漏洞标题:据说斗鱼TV鱼丸能换人民币?那就XSS吸光观众鱼丸!
相关厂商:douyu.tv
漏洞作者: N1ghtBird
提交时间:2014-07-03 00:41
修复时间:2014-07-03 22:08
公开时间:2014-07-03 22:08
漏洞类型:xss跨站脚本攻击
危害等级:高
自评Rank:10
漏洞状态:厂商已经修复
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 help@wooyun.org
Tags标签: 无
漏洞详情
披露状态:
2014-07-03: 细节已通知厂商并且等待厂商处理中
2014-07-03: 厂商已经确认,细节仅向厂商公开
2014-07-03: 厂商已经修复漏洞并主动公开,细节向公众公开
简要描述:
刚看见斗鱼在做活动,观众送鱼丸主播领现金。
那就猥琐的吸光观众的鱼丸吧~
详细说明:
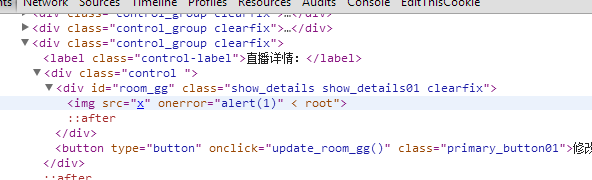
富文本编辑器的XSS过滤没有考虑到浏览器的容错特性。
在某些现代浏览器内非规范标签是可行的。
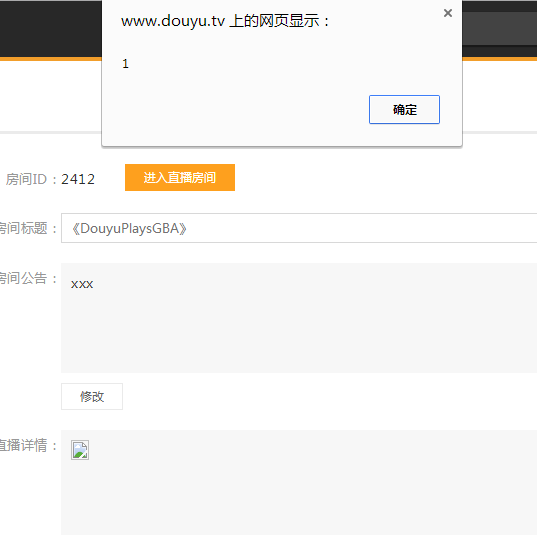
所以,构造以下代码(CHROME)。
成功执行。
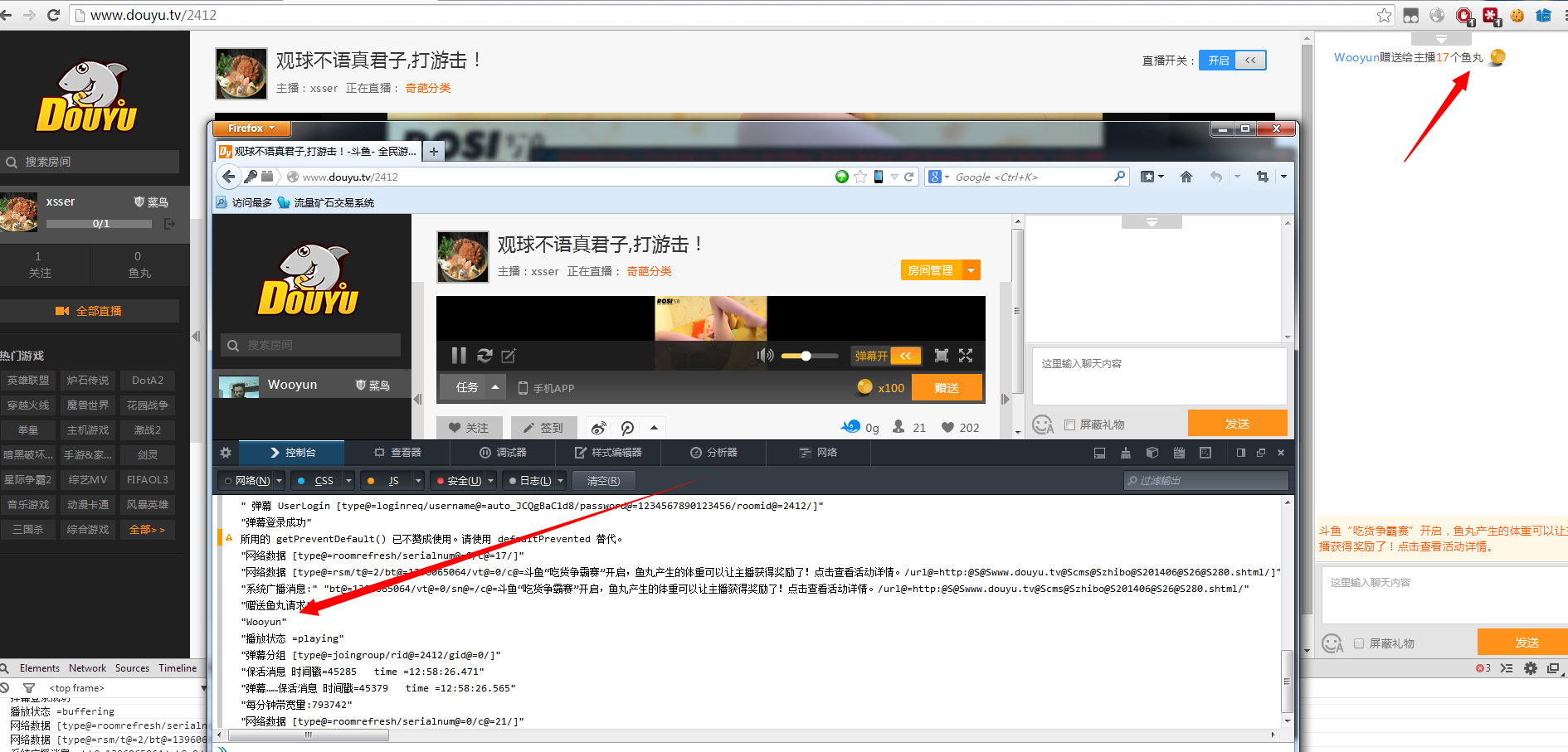
那么如何猥琐的刷鱼丸/刷人民币呢?
开个直播间,设置个诱惑的标题配合封面图再加上我们的猥琐代码比如这样:
搞定~
漏洞证明:
修复方案:
过...滤....
版权声明:转载请注明来源 N1ghtBird@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2014-07-03 00:47
厂商回复:
此bug已于前两天修复!谢谢!
最新状态:
2014-07-03:此bug已于前两天修复!谢谢!