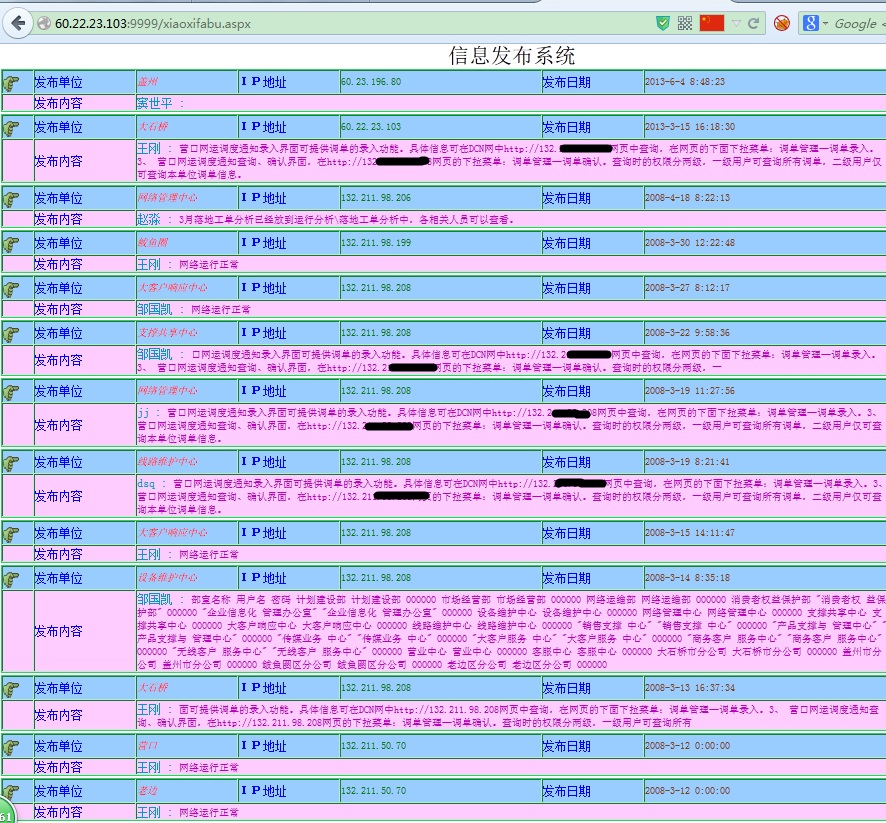
http://60.22.23.103:9999
存在各种问题
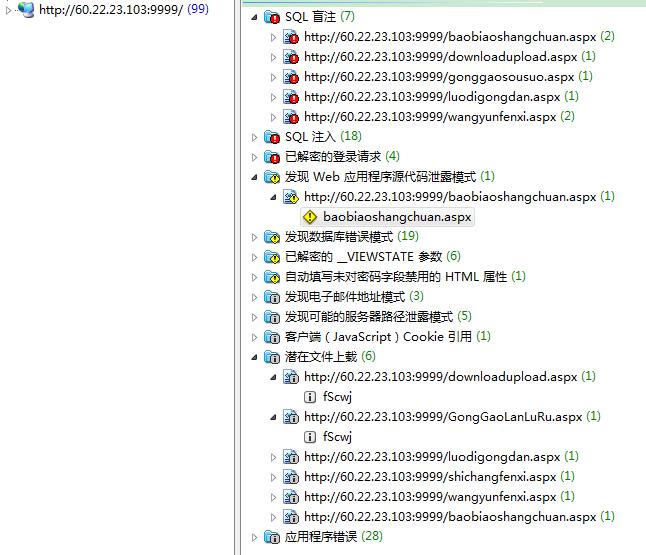
一、存在SQL注入。这个……不太懂,没有进一步测试。
http://60.22.23.103:9999/ChangePassword.aspx
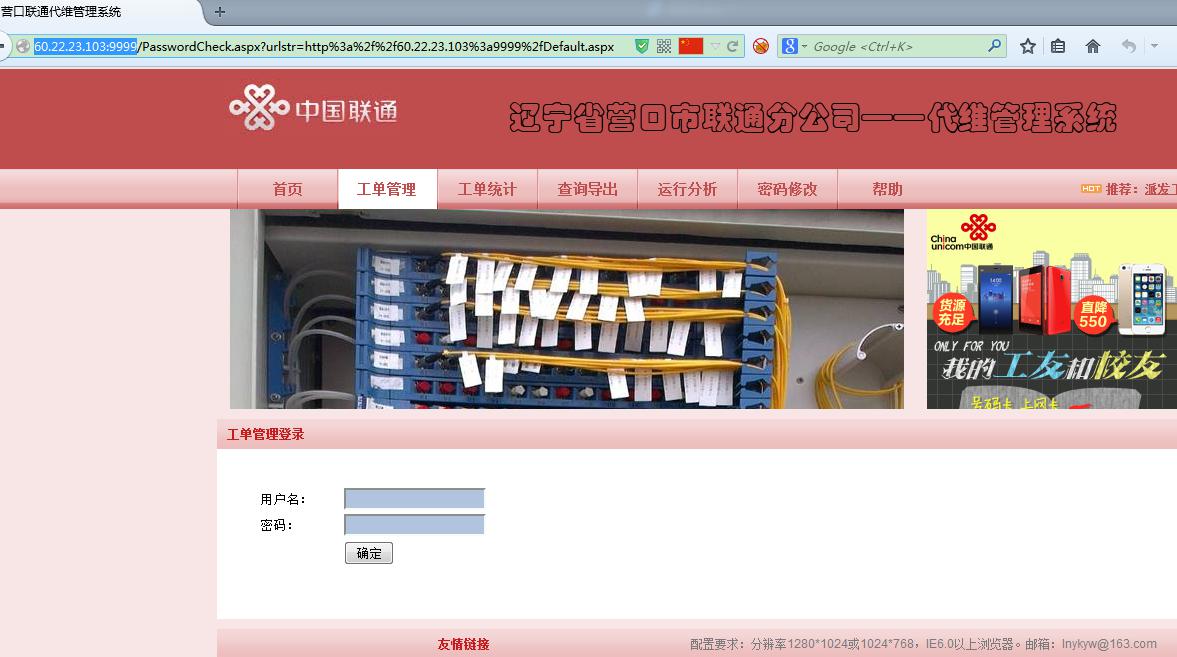
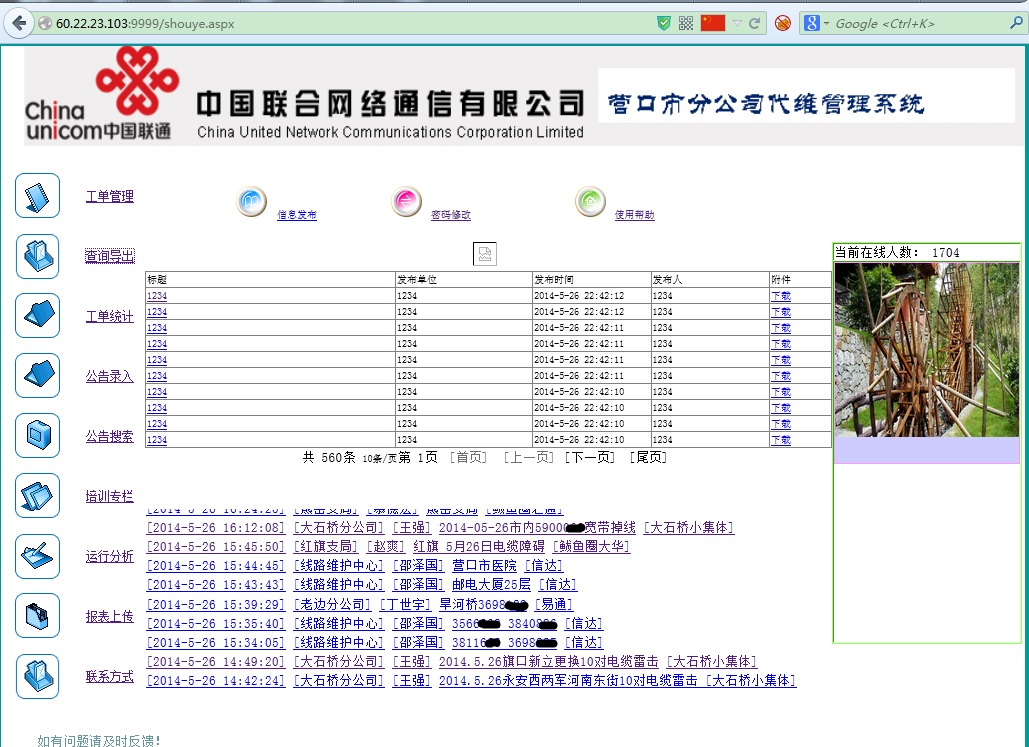
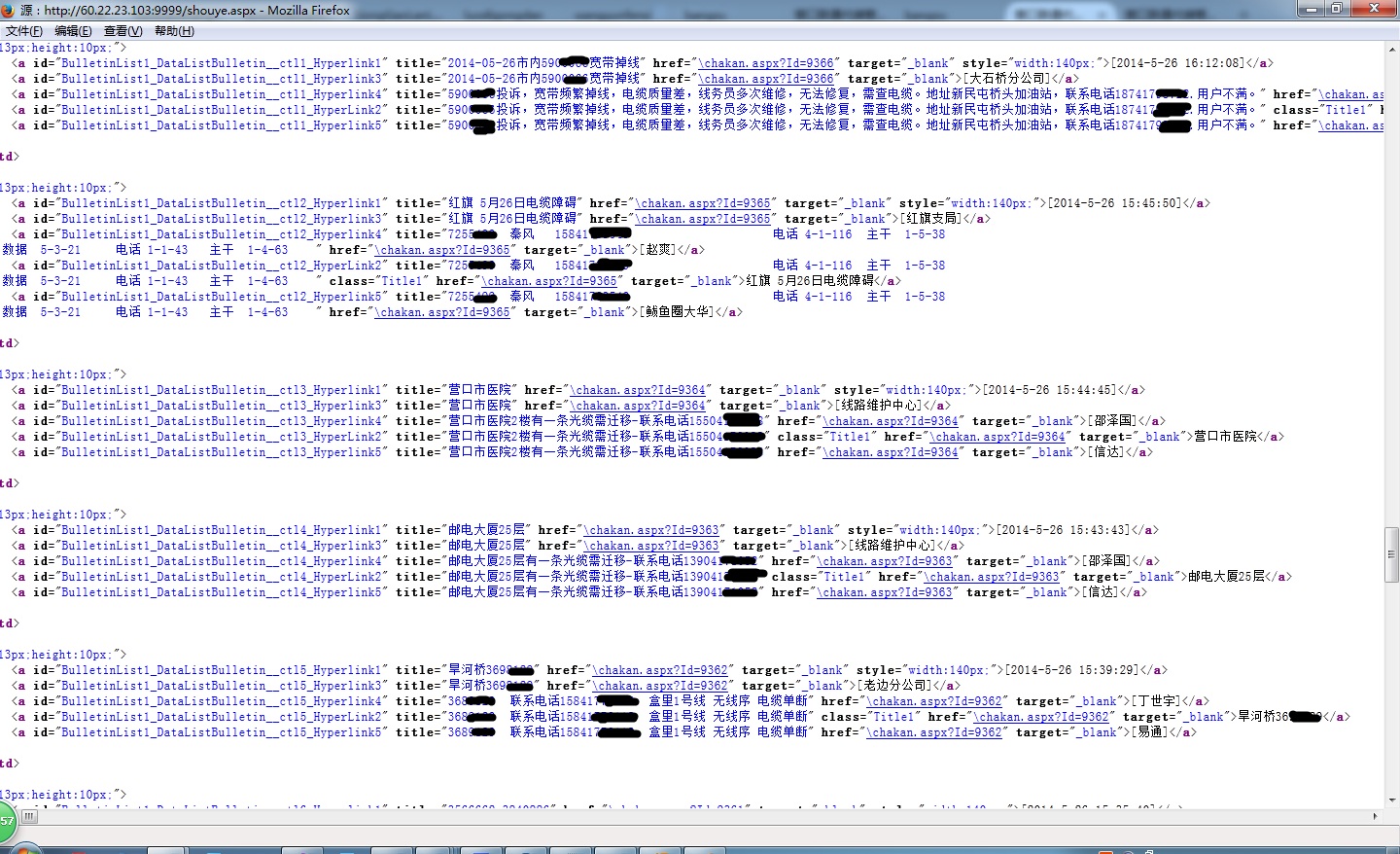
二、可以绕过登陆界面看到“代维管理系统”首页,可以正常显示系统首页信息,而且有敏感信息泄露。
http://60.22.23.103:9999/shouye.aspx
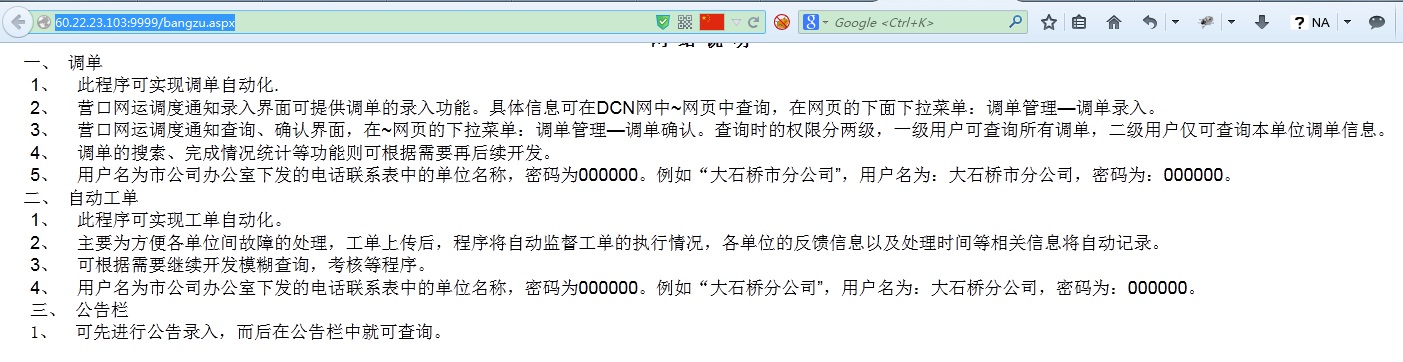
主页上“使用帮助”中有默认登陆账号和密码。我登陆时显示“您无权登陆此系统。”,也许是因为我的不是联通宽带,也许密码已经改了。没验证。
三、存在文件上传页面,可以正常上传文件(绝没上传木马)
http://60.22.23.103:9999/baobiaoshangchuan.aspx
http://60.22.23.103:9999/downloadupload.aspx
http://60.22.23.103:9999/GongGaoLanLuRu.aspx
http://60.22.23.103:9999/luodigongdan.aspx
http://60.22.23.103:9999/shichangfenxi.aspx
http://60.22.23.103:9999/wangyunfenxi.aspx
四、在页面http://60.22.23.103:9999/GongGaoLanLuRu.aspx上传txt文件后直接跳到“信息发布系统”界面,显示以前发布信息,其中有各个单位的账号和默认密码。