漏洞概要
关注数(24)
关注此漏洞
漏洞标题:163邮箱126邮箱任意文件下载漏洞
相关厂商:网易
提交时间:2011-11-09 21:45
修复时间:2011-12-09 21:46
公开时间:2011-12-09 21:46
漏洞类型:任意文件遍历/下载
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2011-11-09: 细节已通知厂商并且等待厂商处理中
2011-11-10: 厂商已经确认,细节仅向厂商公开
2011-11-20: 细节向核心白帽子及相关领域专家公开
2011-11-30: 细节向普通白帽子公开
2011-12-10: 细节向实习白帽子公开
2011-12-09: 细节向公众公开
简要描述:
163邮箱和126邮箱在实现上存在缺陷,利用80sec发布的xml解析漏洞可以读取服务器上任意文件,包括服务器配置文件和敏感的数据库文件,结合上下文逻辑可能可以获得更高权限。
详细说明:
163的服务器在接受和传递参数时使用的是xml的格式进行数据传递,但是根据80sec的安全公告,如果服务端在处理xml数据时格式不对就会导致安全漏洞,使用应用上下文的权限来获取任意文件内容,结合逻辑可能可以得到更多的权限
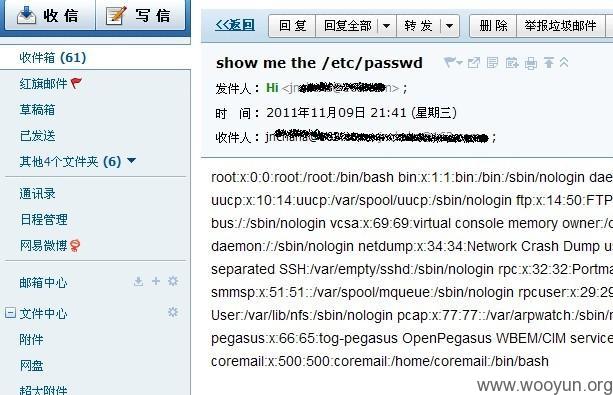
漏洞证明:
神奇的代码哦,就是简单的在xml头部附加我们的恶意就可以了
修复方案:
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2011-11-10 10:56
厂商回复:
感谢80sec,尽快修复。
最新状态:
暂无



