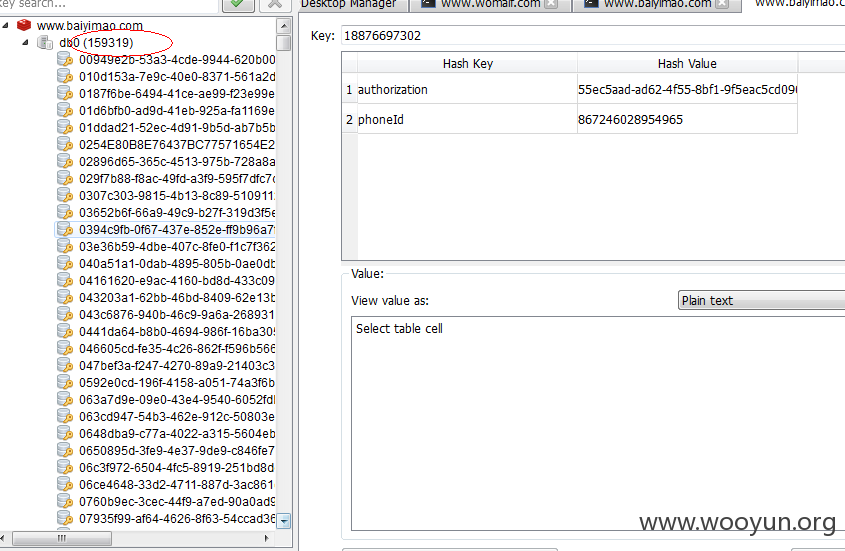
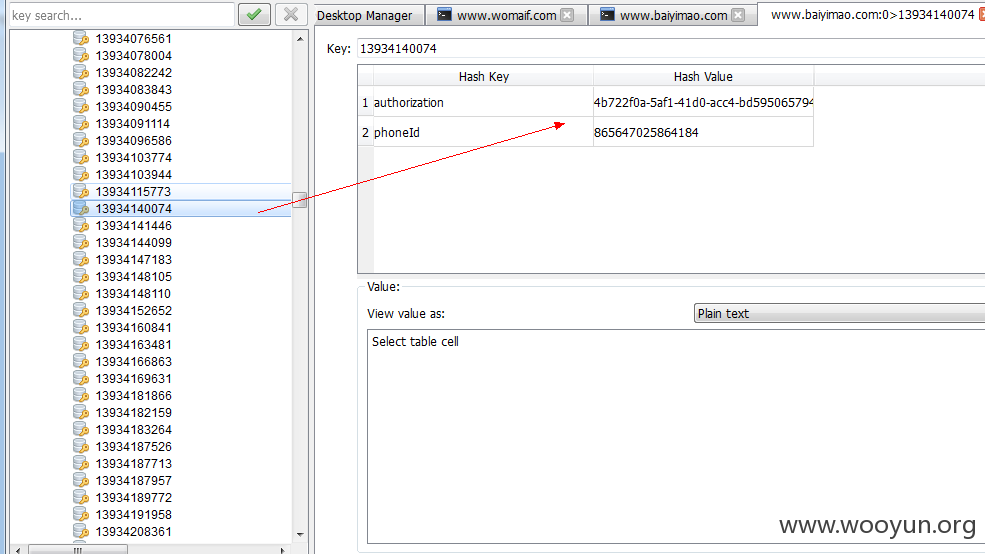
深圳佰亿猫金融服务有限公司成立于2015年,注册资本1000万元人民币,在职员工100余名,为中小企业和个人投资者提供高效,安全,便捷的 P2P理财服务,管理团队成员均来自银行,法律,风控,互联网资深专业人士,拥有国内外从业相关经验,公司与合作的金融机构严格为投资者把控风 险。树立独特竞争优势,实现全民理财梦想
“佰亿猫”携手平安保险,为公司平台的个人投资者投保个人账户资金安全保险,最大限度保障投资者的资金安全,为投资者争取更多的权益和保障
www.baiyimao.com:0>config get *
配置信息,应该是WINDOWS 服务器。
www.baiyimao.com:0>info
服务器INFO信息